Analyst Report
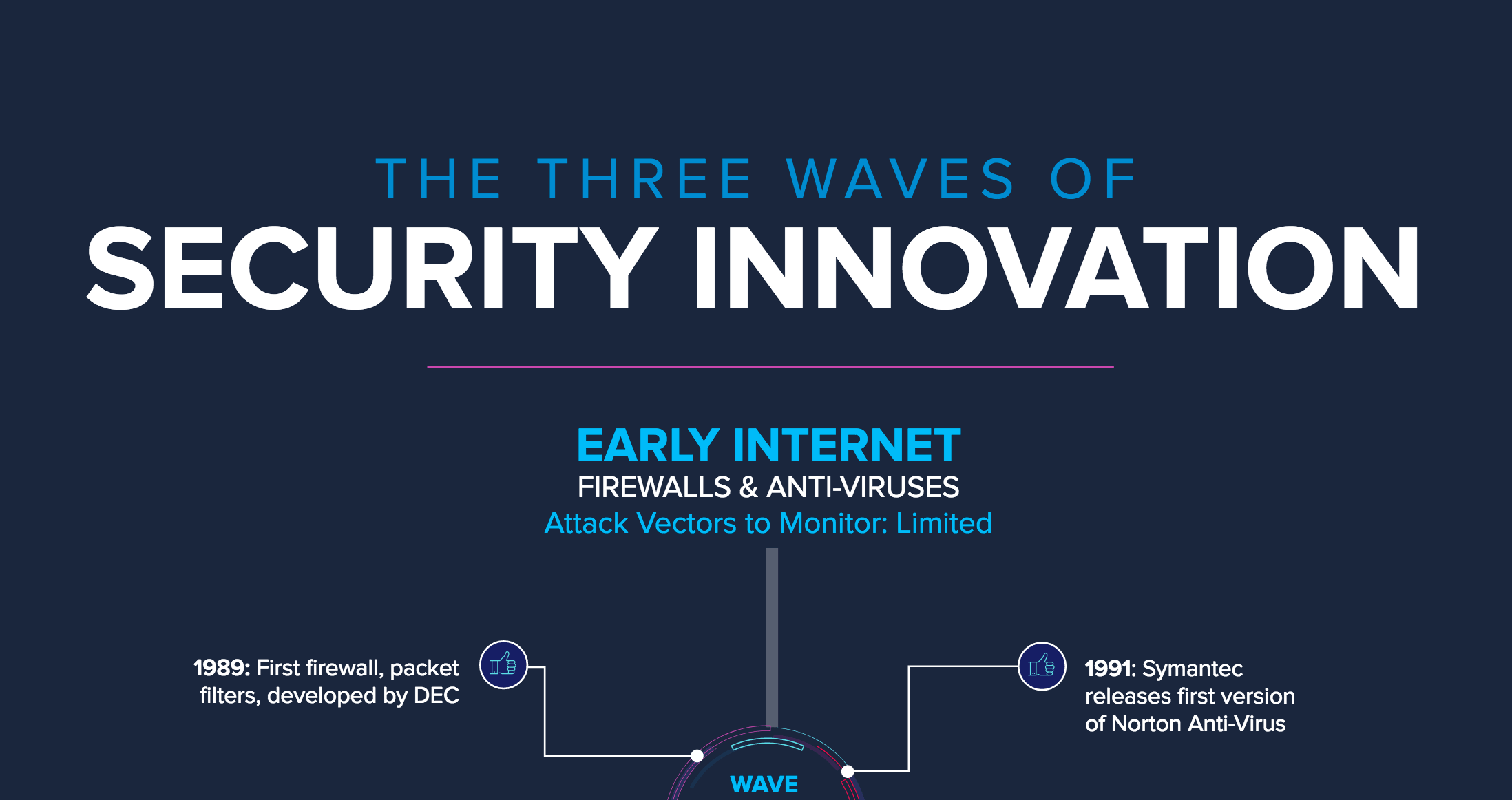
Gartner® on Moving Beyond Patch Management for a Smarter Approach to Reducing Exposure

Analyst Report
What AI-powered CRQ Means for the Future of Cyber Risk Quantification

Webinar
AI in Cybersecurity: Where CISOs are Investing and Cutting

Webinar
Introducing Next-Gen CRQ with scenarios and risk remediation guidance
Infographic
20 Proven Cyber Risk Tactics That Actually Work
Webinar
Vulnerability to Exposure Management: Smarter Risk Prioritization

Webinar
Live Demo: 5 Reasons to Unify Application Risk Findings and How Balbix does it

Webinar
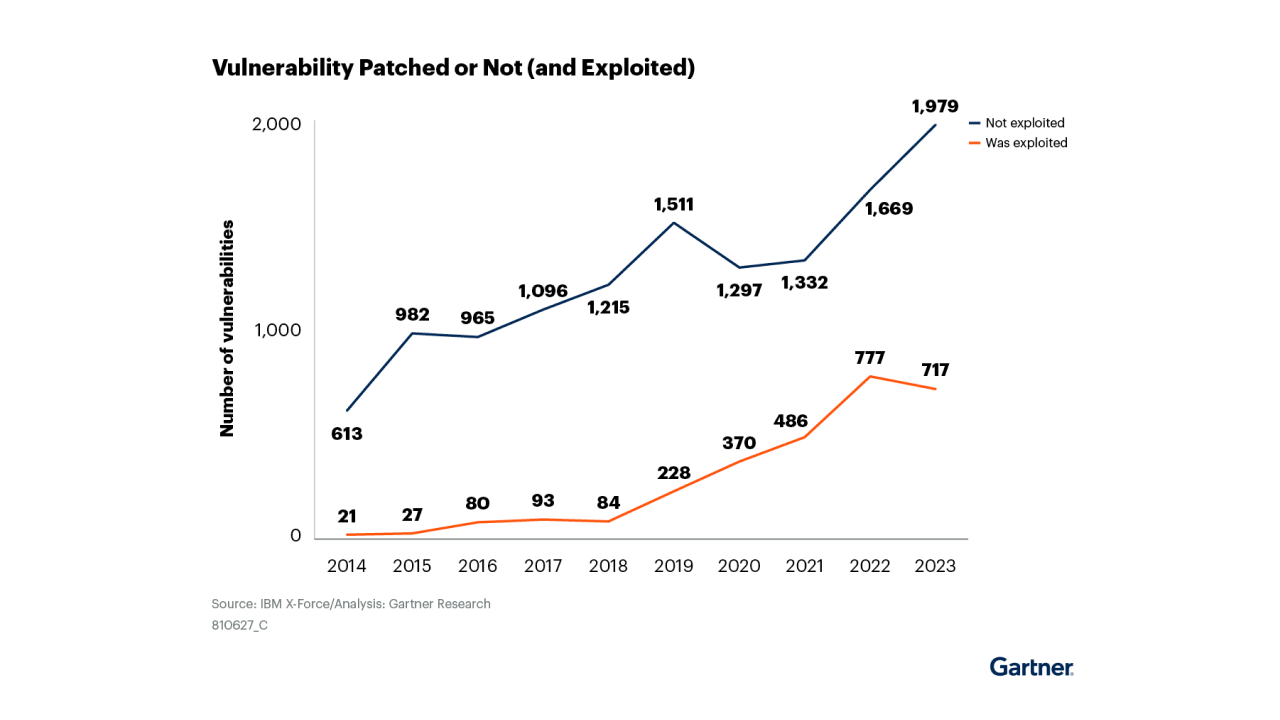
20 Years of Exposure and Vulnerability Management: What Really Works
eBook
The CISO's Playbook for Effective Boardroom Presentations
Webinar
Finally, AI Fuel for Vulnerability Management Teams

Video
Leveraging AI to Burn Down Your Cyber Risk Exposures
Webinar
CISO in the Boardroom: Mock Presentation + 3 Tips for Success
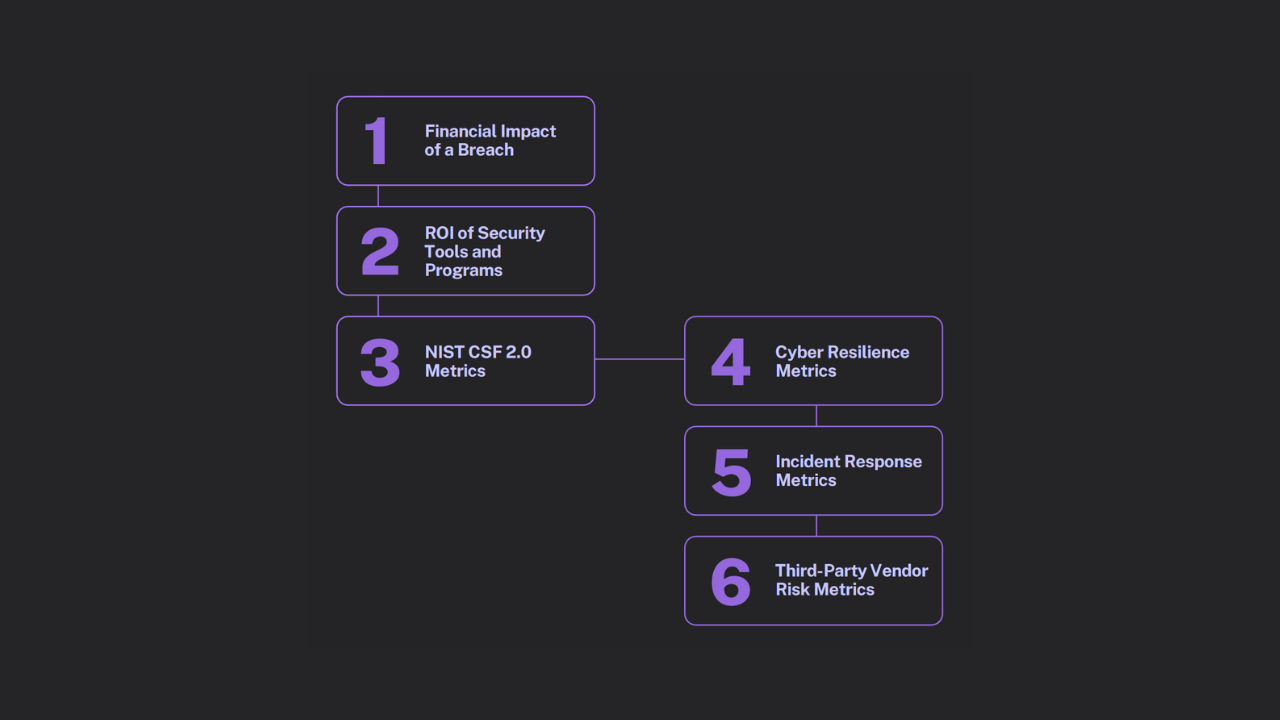
eBook
Discover 6 Cybersecurity Metrics That Capture Your Board’s Attention and Unlock Budget

eBook
9 Attack Surface Metrics to Slash Your Risk Exposure Starting Today
eBook
Master 5 Key Metrics to Ensure Compliance and Reduce Regulatory Risk
Webinar
AI-Era Cyber Risks: Ponemon and Balbix Insights
eBook
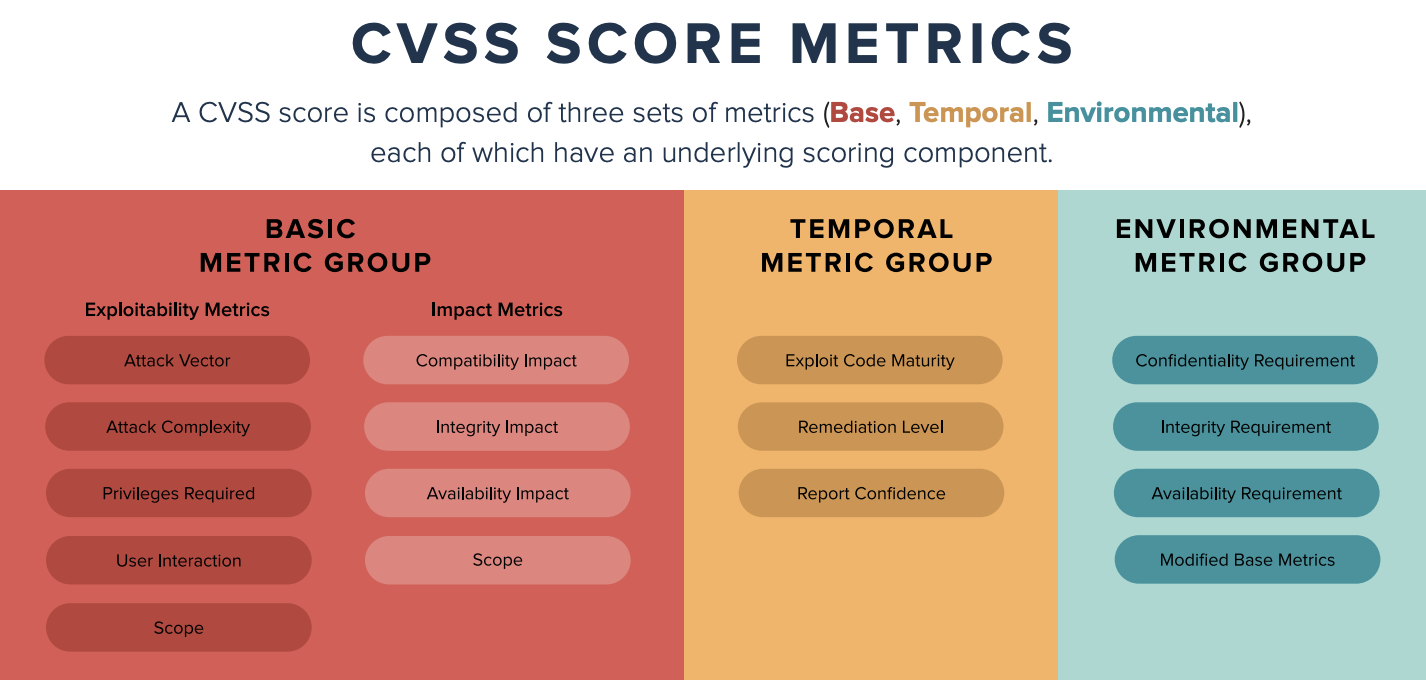
From CVSS to AI: The Evolution to 4th Generation Vulnerability Prioritization
Webinar
Outmaneuvering High Cyber Insurance Premiums With Balbix

eBook
How to Reduce Cyber Insurance Premiums: 3 Actionable Checklists
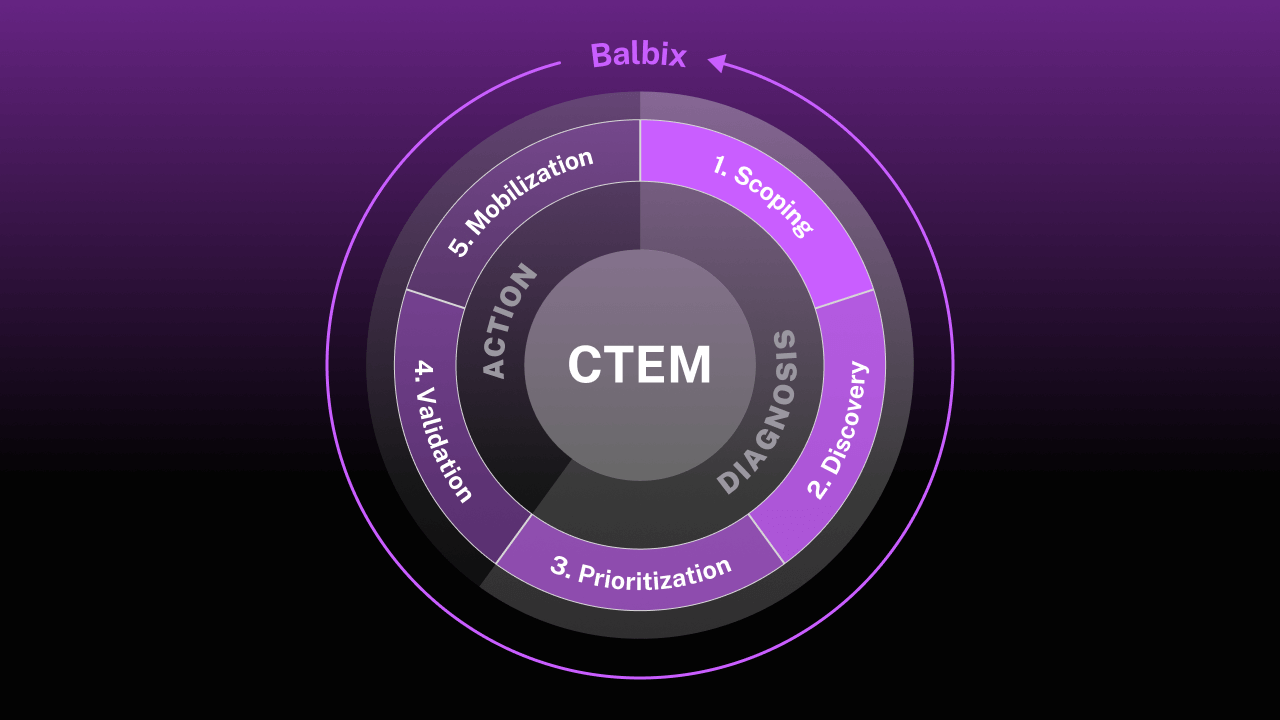
Guide
A Security Professional’s Guide to Continuous Threat Exposure Management
Webinar
Gamify DBIR Findings for Faster Vulnerability Remediation

eBook
The Ultimate Guide to Vulnerability Management Metrics

eBook
Post DBIR 2024: 7 Ways to Reduce Your Cyber Risk
Guide
CISO’s Presentation on the DORA Cybersecurity Regulations

eBook
NIS2: Everything You Need to Know to Stay Compliant

Webinar
CRQ Success Stories: From Skepticism to Advocacy
Webinar
DORA: Practical Insights on How to Achieve Cyber "Resilience"
Guide
The 11 Ways We Sabotage Our Own Vulnerability Management

Webinar
Logical Advice for CISOs on the SEC Cybersecurity Regulations

Webinar
Uncommon Wisdom: Lessons from Two Decades of Cyber Risk Quantification

Guide
3 slides for CISOs to summarize the 2023 SEC Cybersecurity Changes

eBook
A CISO's Guide to the SEC’s Cybersecurity Regulation

Webinar
Master the SEC's Latest Cybersecurity Regulation: 5 Questions Answered

Case Study
US Utility Co. Improves Asset Visibility, Speeds up Patching, and Reduces Breach Risk with Balbix

White Paper
Using Balbix to Secure Higher Education from Ransomware Threats

Analyst Report
Balbix honoured with 2023 ‘Distinguished Vendor’ award from TAG Cyber

Video
Partner Insights: Risk Quantification Strategy for the Fortune 500

Analyst Report
Automating Cybersecurity Posture Assessment

Video
Effective Cyber Risk Quantification Through Automation

eBook
Risk-Based Vulnerability Management: The CISO Executive Guide

eBook
Truths About the State of Cybersecurity Posture Management

Case Study
Par Pacific Uses Balbix for Quarterly Board Reporting and To Cut Mean Time to Patch in Half

Case Study
The Master Group Improves Asset Visibility, Reduces Risk and Speeds Up Patching with Balbix
Case Study
Fortune 100 Company Speeds Up Discovery and Reporting of Log4j Vulnerabilities

Case Study
Financial Institution Prioritizes Cyber Risks, Remediates Vulnerabilities Faster

Case Study
Oerlikon Reduces Patch Time and Improves Management-Level Cyber Risk Visibility
Case Study
Greenhill Measures Their Cybersecurity Program ROI With Balbix

eBook
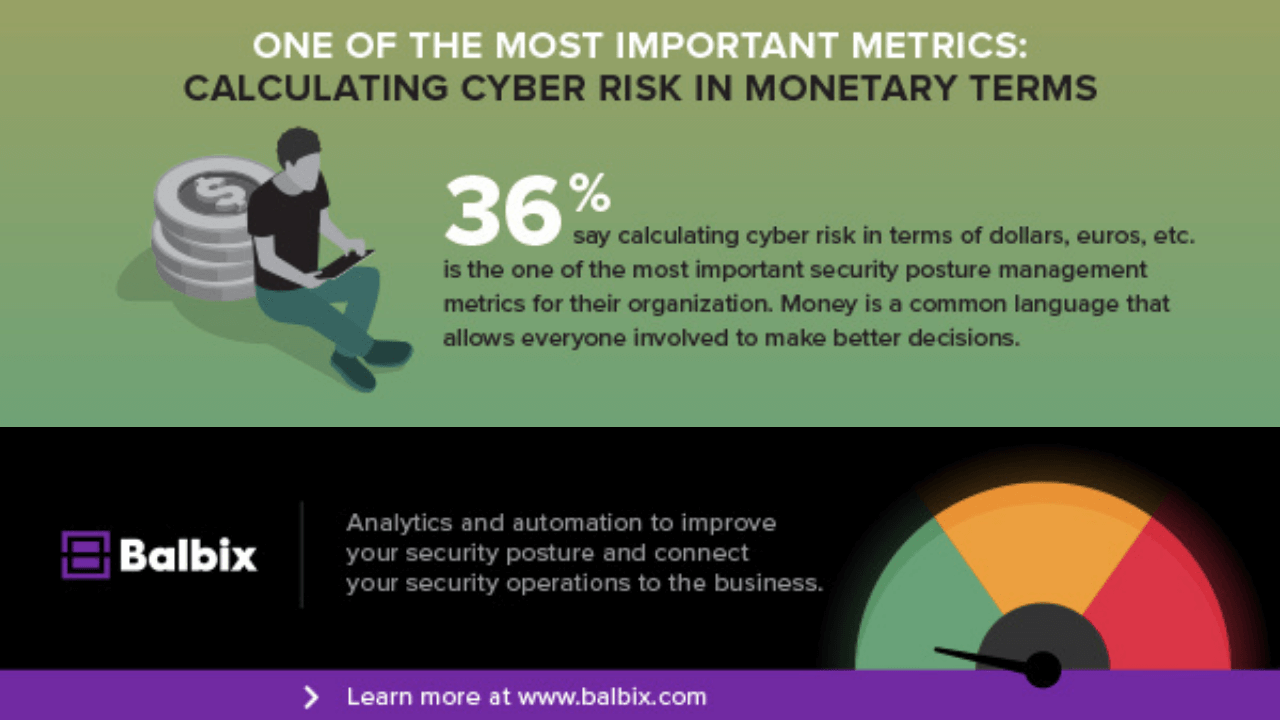
A CISO Guide to Calculating Breach Risk in Monetary Terms
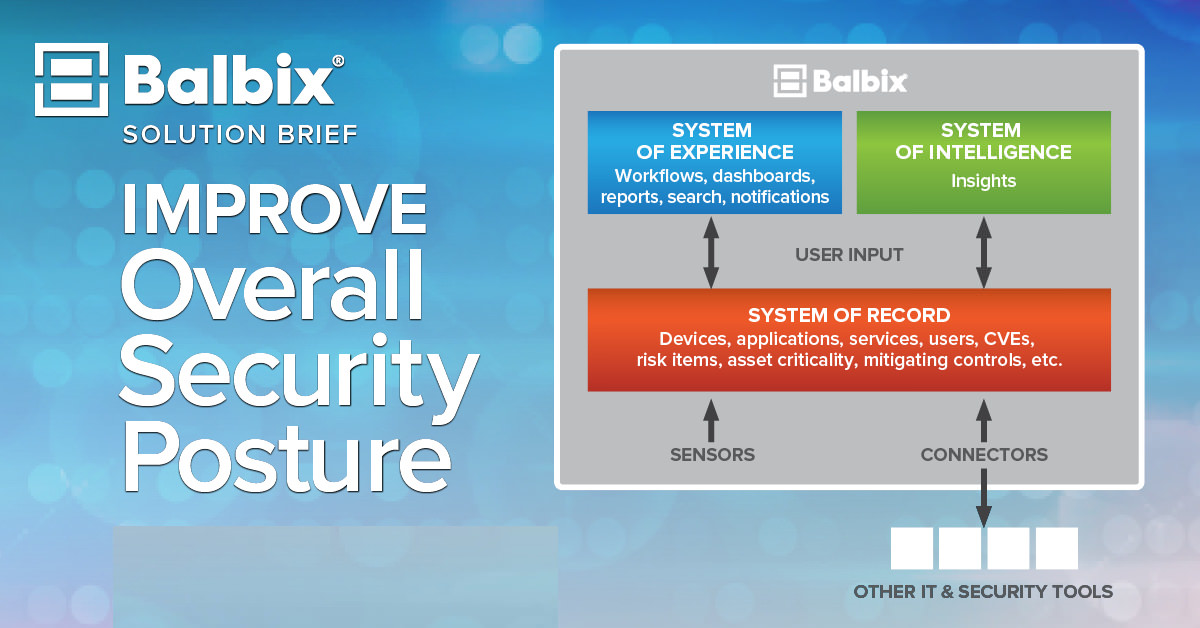
Solution Brief
Automated Cyber Risk Quantification Using the Balbix Platform

Video
Using Automation to Kick Your Cybersecurity Program Into High Gear

Video
Discussion with Mike Britton on ABCs of Good Cybersecurity Program
Video
Daniel Gisler, CISO of Oerlikon Group on Balbix

Video
Panel Discussion: Rethinking Cybersecurity for the Age of Infinite Attack Surfaces

Analyst Report
TAG Cyber Security Quarterly Report for Q2 2021

Analyst Report
2021 Technology Innovation Leader Report - Frost & Sullivan

eBook
CISOs: 5 Board Presentation Mistakes to Avoid at All Costs
Presentation
Essential Slides for Your 2024 CISO Board Presentation

Presentation
The Ultimate Guide for New CISOs: Your First Board Presentation Template

eBook
Elevate Your Cooking (and Your Security Posture) Cookbook
Case Study
US Telecommunications Giant Saves Millions with Balbix

Product Sheet
Breach Risk Minimization for Under-Resourced Teams
Solution Brief
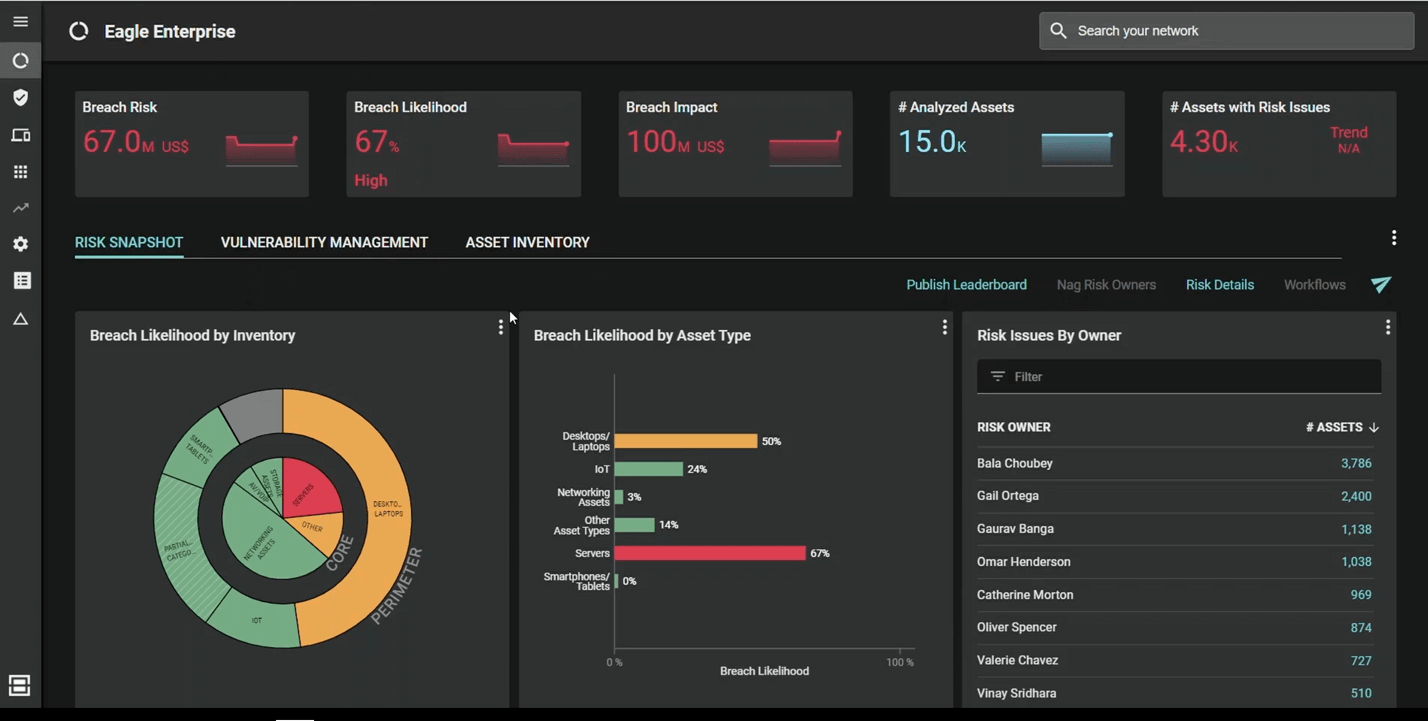
Assessing and Reporting on Enterprise Breach Risk

Video
On-Demand Webinar: Proving Security is Not Just a Cost Center
Analyst Report
2020 State of Enterprise Security Posture Report

eBook
3 Essential Tools for CISOs to Assess and Report on Breach Risk

eBook
Why You Need to Consolidate Cybersecurity Tools

Guide
Ultimate Guide to Risk-Based Vulnerability Management
Guide
Ultimate Guide to Cyber Risk Reporting to the Board of Directors

Video
On-Demand Webinar: Leading in a Down Economy: IT & Infosec Efficiency

eBook
"Tired of Adulting" Fun Book for Cybersecurity Pros

White Paper
CISO Guide: 5 Steps to Improve Cyber Resilience

eBook
The Terrible, Horrible, No Good, Very Bad Truth About Vulnerability Management

eBook
3 Keys to Having an InfoSec Team That Loves Their Job

eBook
New CISO Essentials Series: 4 Factors to Focus on in Your First 4 Months

eBook
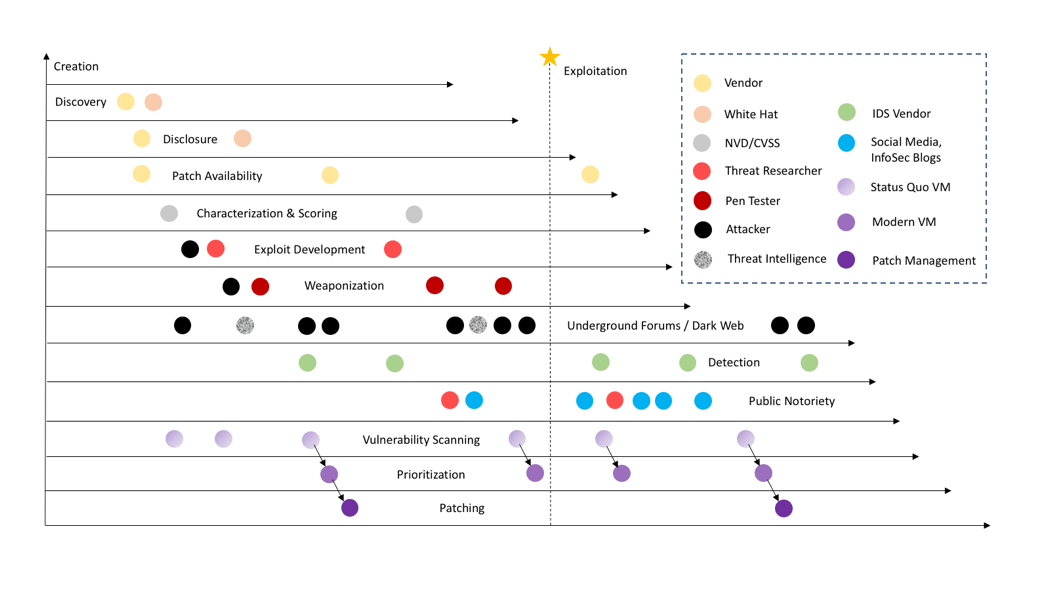
Most Common Cybersecurity Attack Vectors and Breach Methods
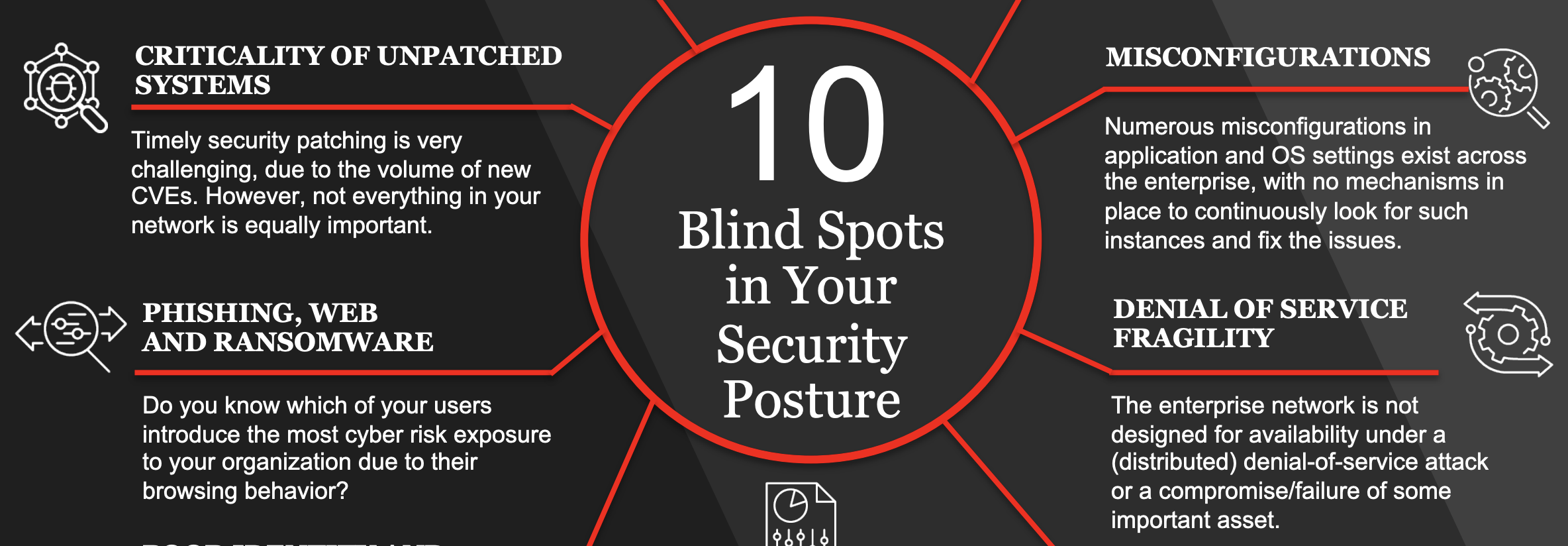
Infographic
10 Blindspots in Your Security Posture (infographic)

eBook
Cyber-Risk Reporting to the Board: 3 Success Factors

eBook
4 Problems with Your Cybersecurity Posture and How to Fix Them

Guide
What CISOs say about the state of cybersecurity

eBook
Visibility: Cybersecurity’s Missing Link and Success Factor

eBook
How to Gain 100x Visibility Into Your Cybersecurity Posture

Analyst Report
Frost & Sullivan: AI-Based Security Industry Guide, 2019

eBook
6 Essential Pillars for Comprehensive Prioritization

eBook
The Best-Kept Secret of the Most Effective CISOs

Analyst Report
Frost & Sullivan: Next Generation Cybersecurity

Guide
Top 6 Vulnerability Management Mistakes to Avoid
Video
Geekin Out: Calculating Breach Likelihood with PGMs

Video
Larry Ponemon: The Challenging State of VM Today

Solution Brief
Cyber-Risk Reporting for Your Board of Directors

Video
Webinar: Quantifying Cybersecurity Posture for the Board of Directors

eBook
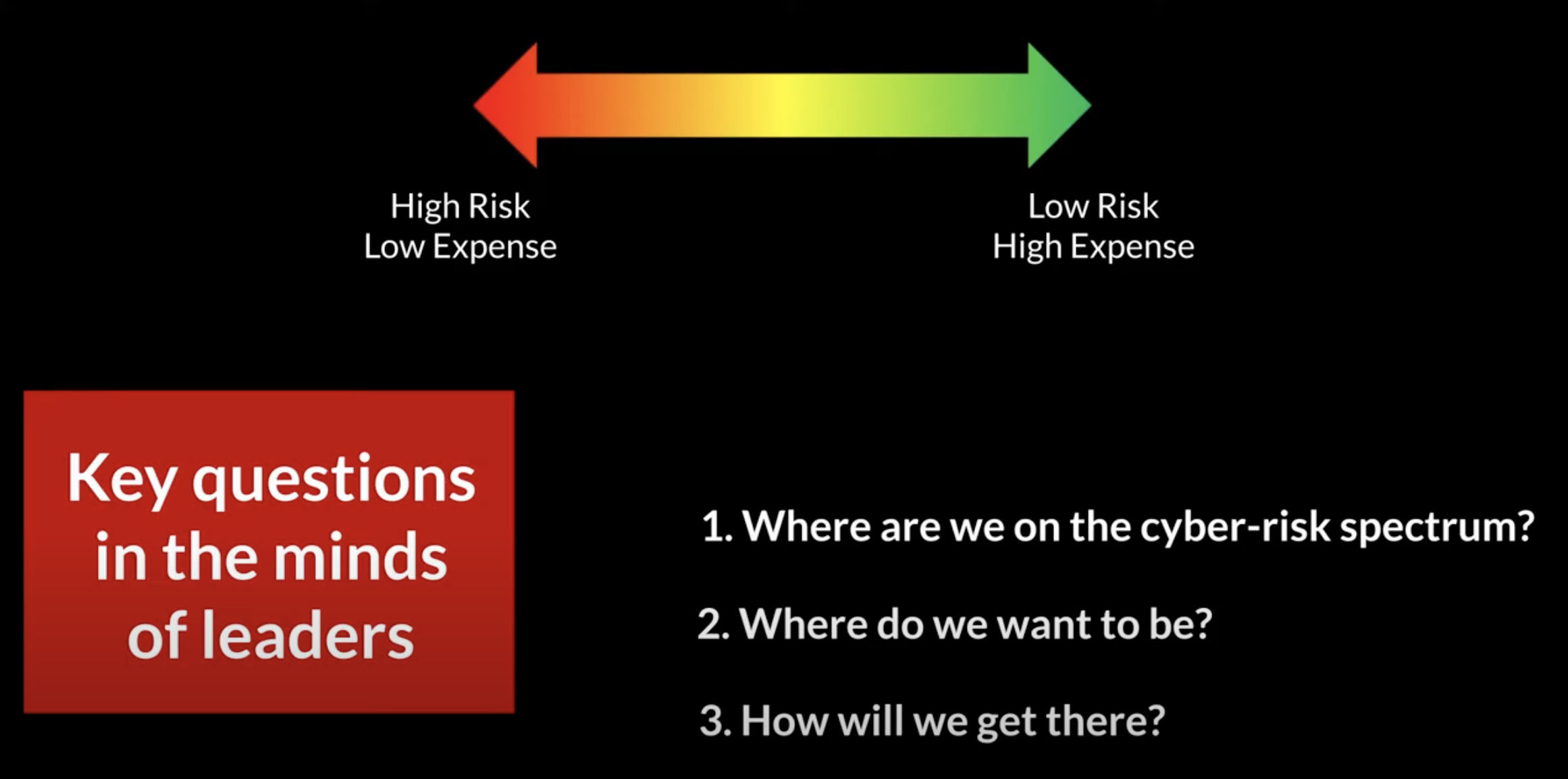
Getting Started on Transforming Your Security Posture

Analyst Report
EMA Report for Threat Detection and Breach Resolution

eBook
How to Implement Risk-Based Vulnerability Management

eBook
8 Must Have Features for Risk-Based Vulnerability Management

eBook
Tackling the Toughest Cybersecurity Challenges Using AI

Guide