Balbix for the Telecom Industry
Reduce cyber risk to your critical infrastructure and data
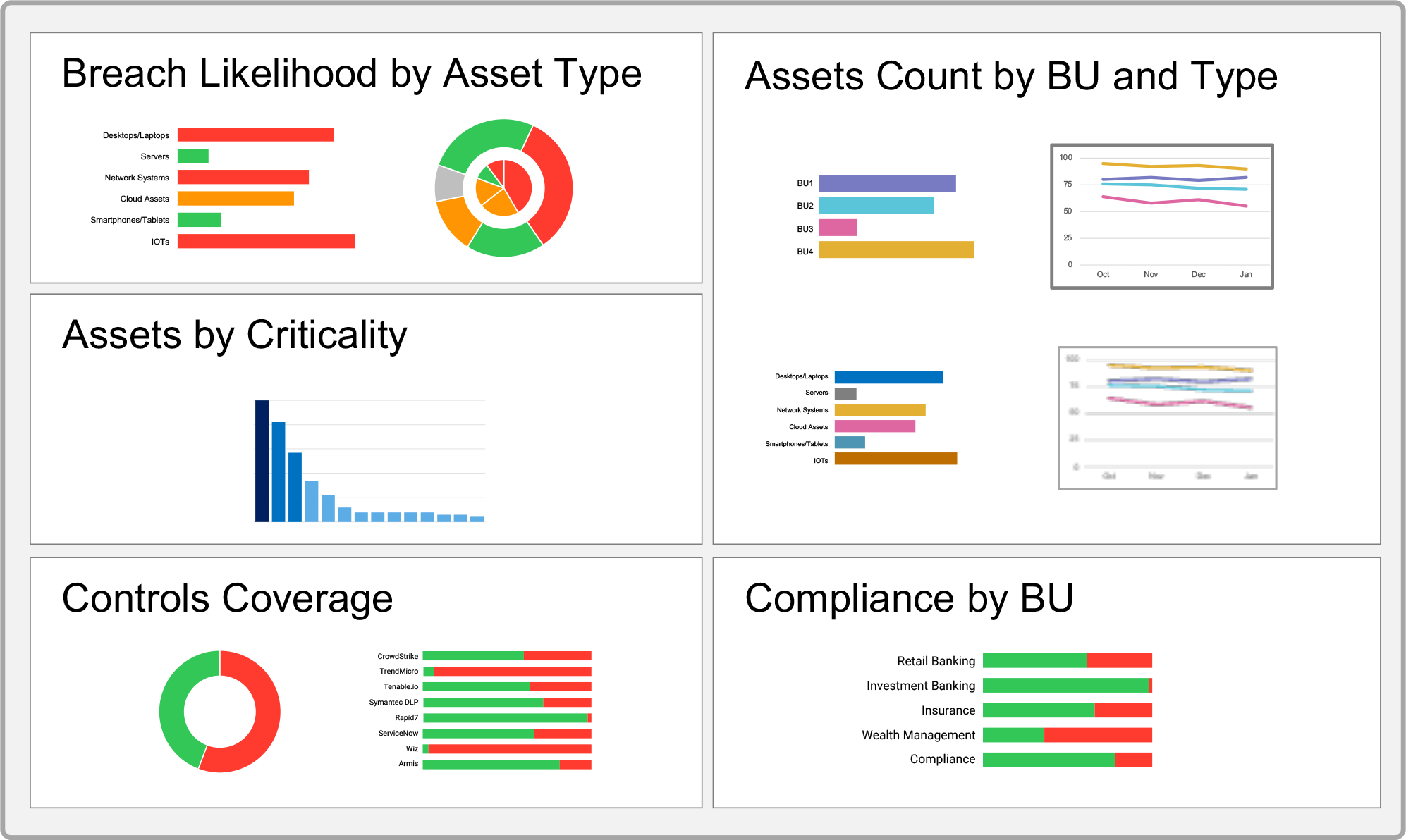
Consolidate legacy and modern infrastructure assets and applications on a single dashboard, along with their vulnerabilities, misconfigurations, threats, and controls.

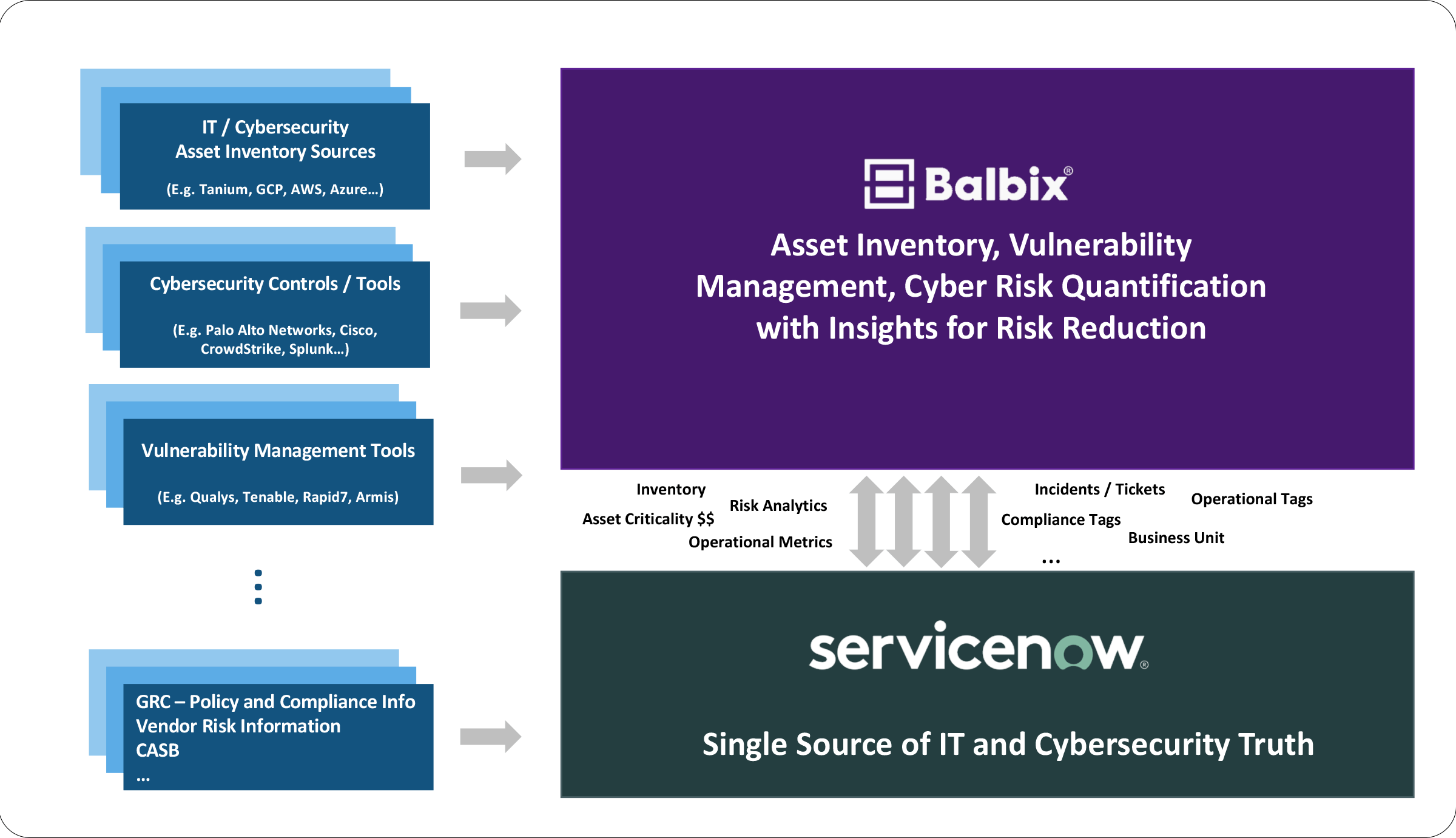
Integrate with CMDBs, such as ServiceNow, to ensure assets and applications, such as their locations, owners, and IP addresses, are kept up-to-date for IT workflows.
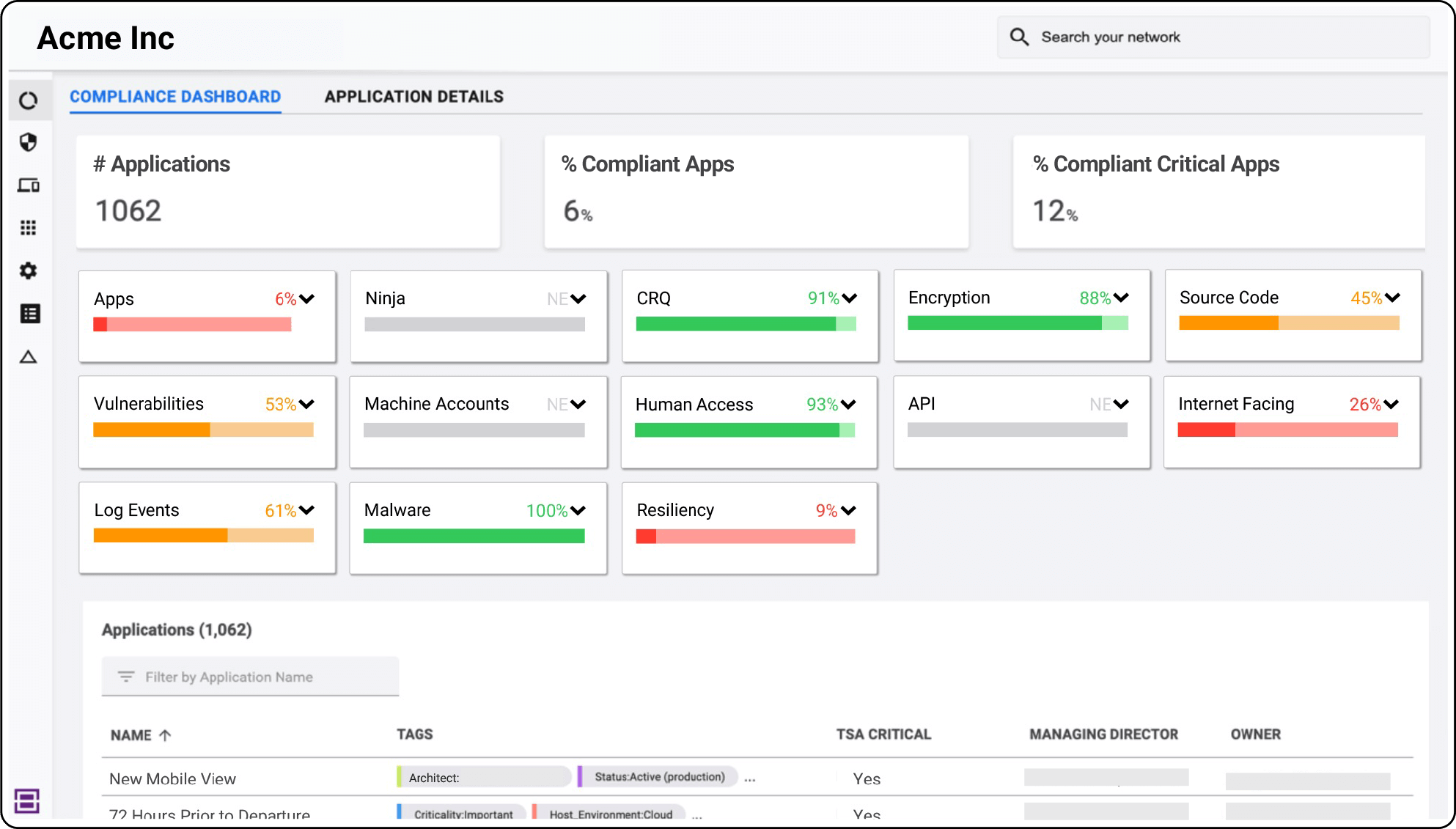
Deliver an SBOM including open-source and third-party libraries associated with software as required by The National Telecommunications and Information Administration (NTIA).
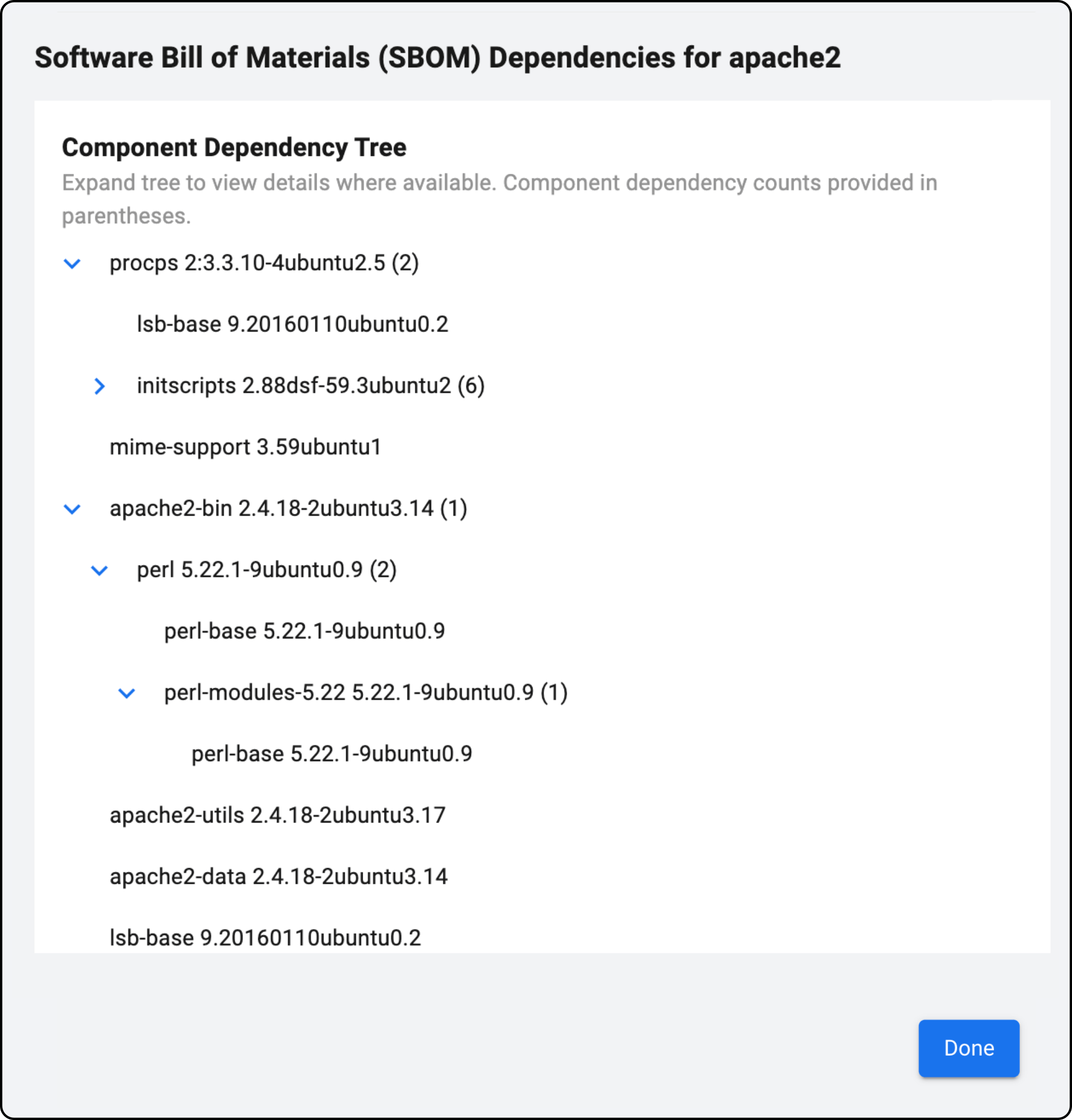
SBOMs include version numbers, vendors, and associated CVEs for every component, making it easier for security teams to discover risks.
Use severity, threats/exploits, external exposure, security controls, and business impact to prioritize vulnerabilities. Add CISA KEV intelligence for improved prioritization.
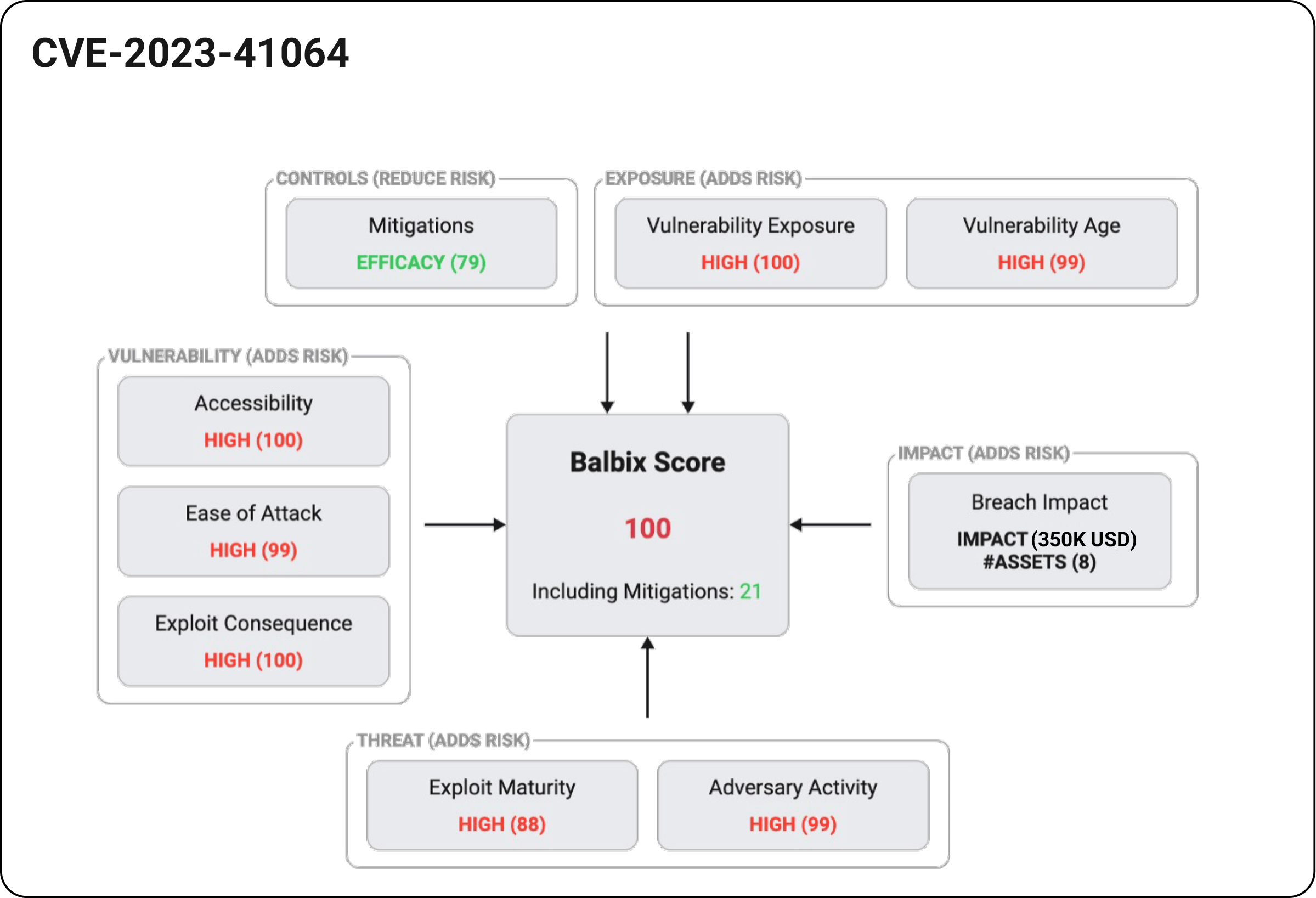
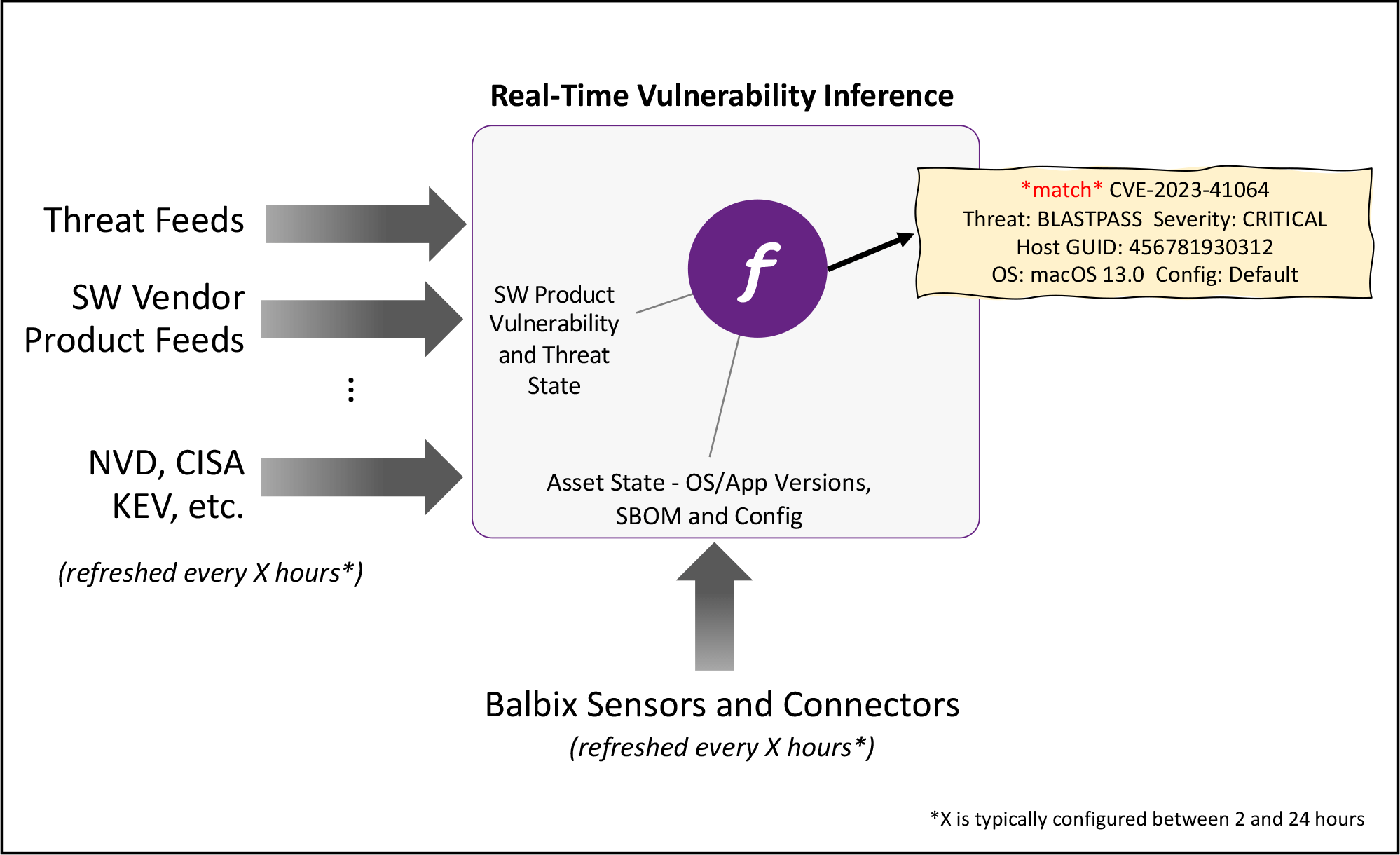
Infer vulnerabilities as soon as they are made public rather than wait for periodic scans to complete. With this approach, organizations can reduce the risk of critical vulnerabilities going unnoticed.
“Balbix was able to find Log4j instances, including Log4j embedded in over 1000 separate application versions across more than 60,000 assets, including 450 application versions on approximately 5000 critical assets”
Fortune 50, Teleco, CISO
Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.