Comprehensive SBOM for Your Environment
Discover and identify all vulnerable open-source and third-party libraries in real-time
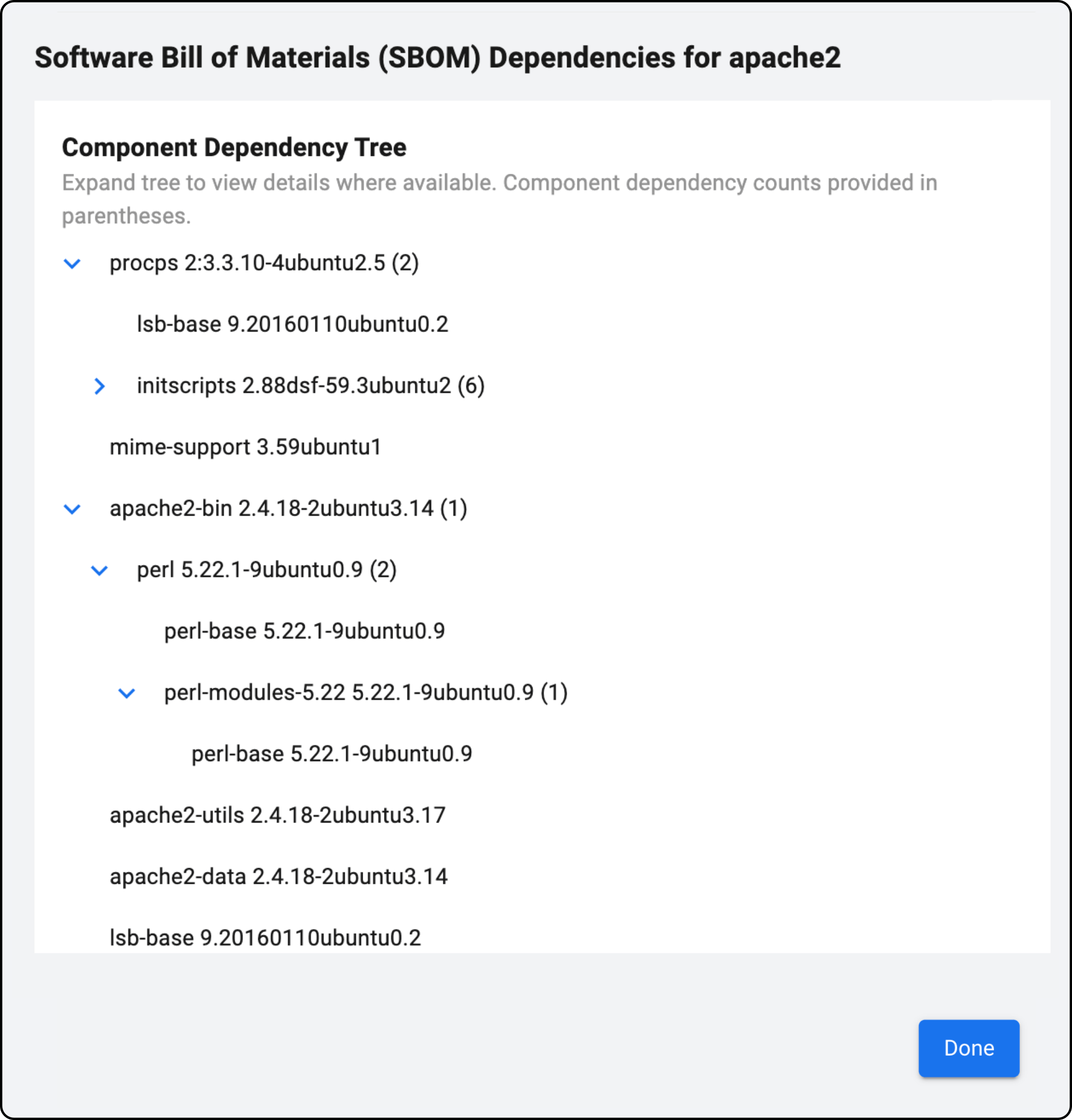
Detect all software components on your virtual and physical machines, including open-source and third-party libraries.
Leverage AI to detect vulnerable software libraries without waiting for lengthy scans to complete, which takes weeks.
Prioritize vulnerabilities by combining SBOM with their CVE data and service information (ports, services, etc.), asset exposure, and business impact to assess risk.

Map open-source vulnerabilities to assets and their owners to ensure critical vulnerabilities like Log4j can be quickly remediated by creating tickets with the required context.
Gain visibility into complex vulnerabilities such as Log4j and Spring4Shell. Identify, prioritize, and remediate assets with these vulnerable software components.

IT and security teams can export their SBOM inventory to popular configuration management database (CMDB) tools.
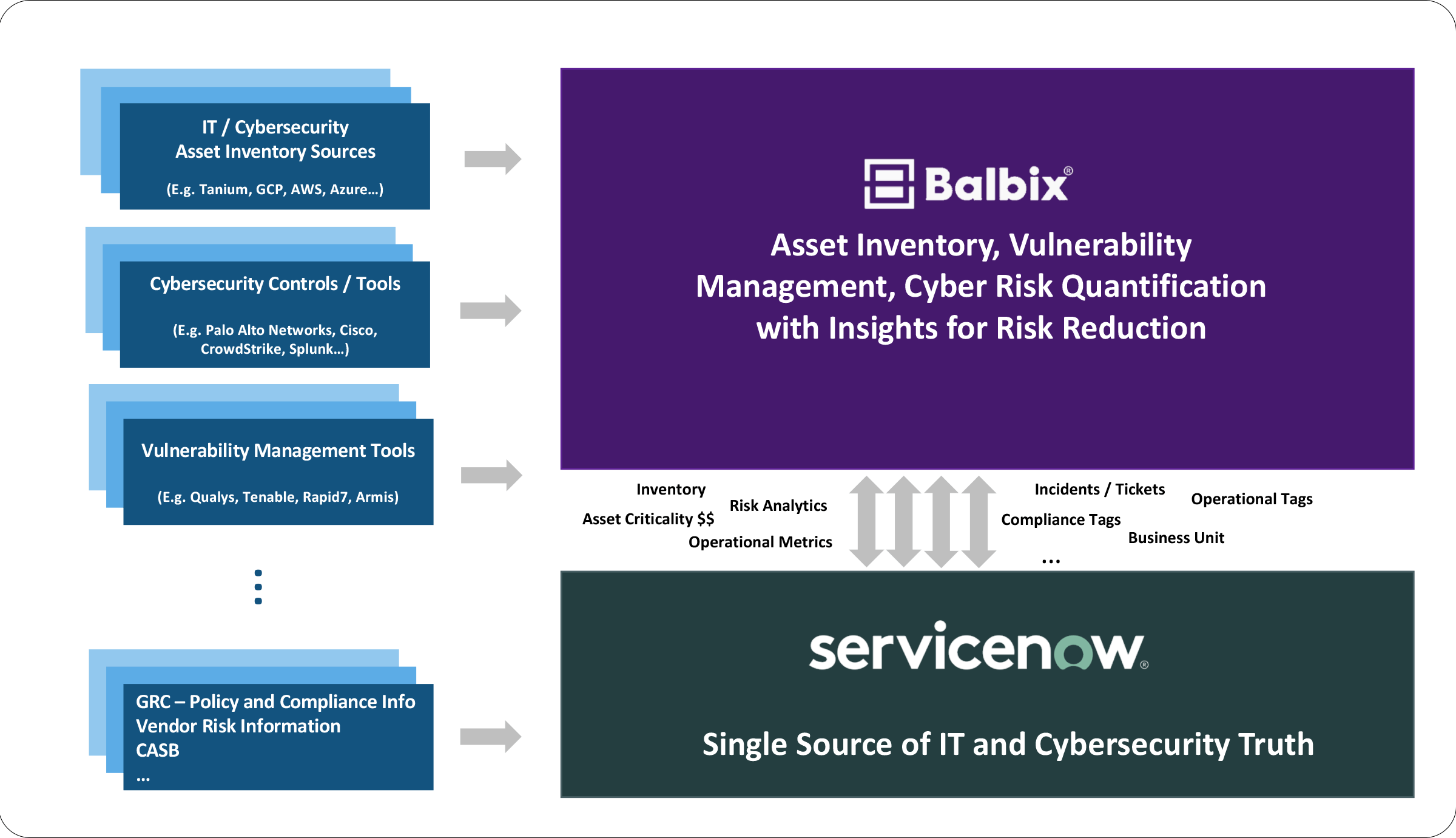
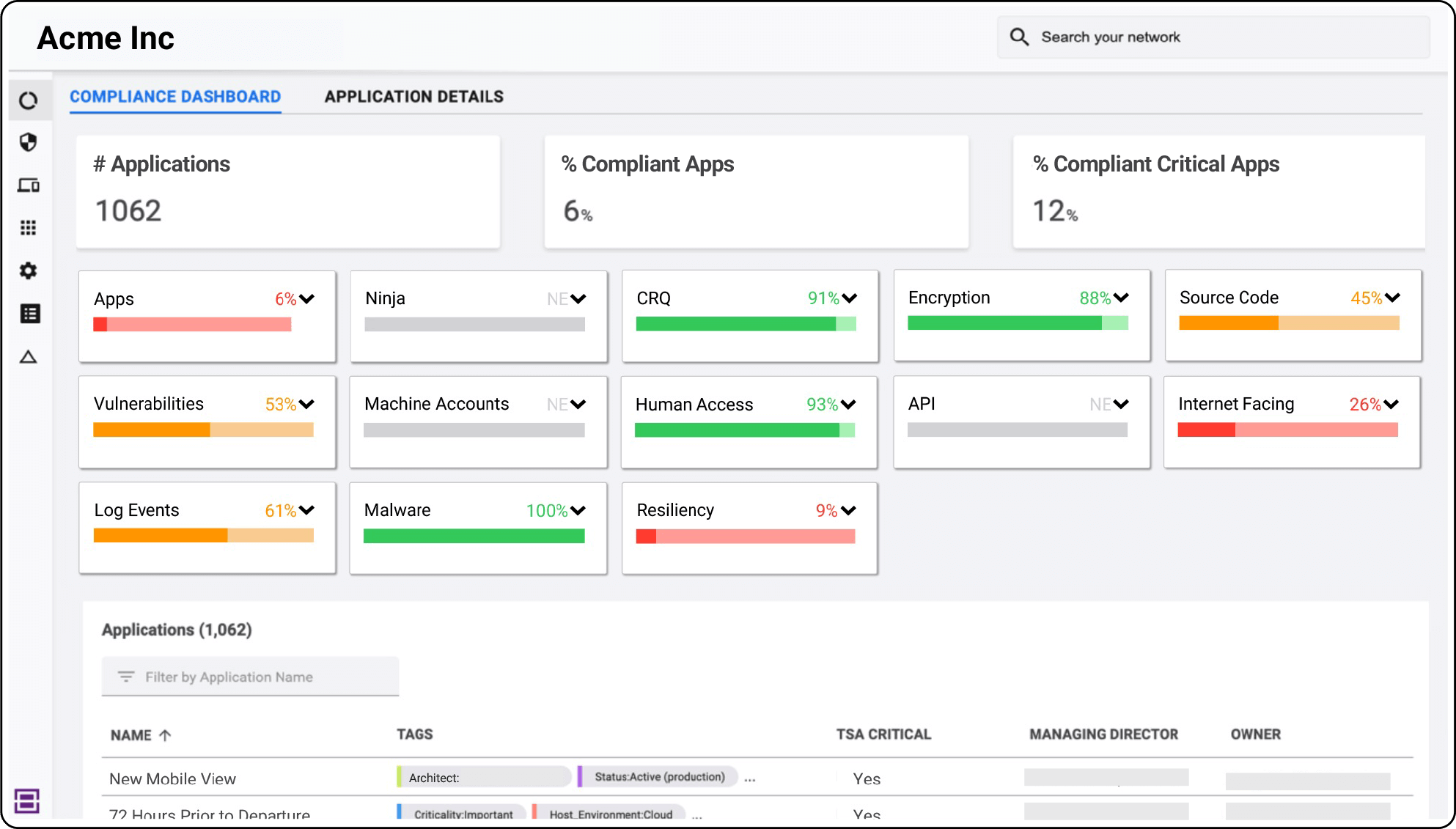
With comprehensive visibility into software components and their associated vulnerabilities, threats, controls, and business contexts, security teams can deliver compliance reports faster.



Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.