Traditional vulnerability management just isn’t enough. Discover why Continuous Threat Exposure Management (CTEM) is rapidly becoming a must-have strategy for CISOs.
In this CTEM Executive Guide, you’ll learn:
- Methods for improving overall cybersecurity resilience by continuously discovering and managing exposures beyond CVEs.
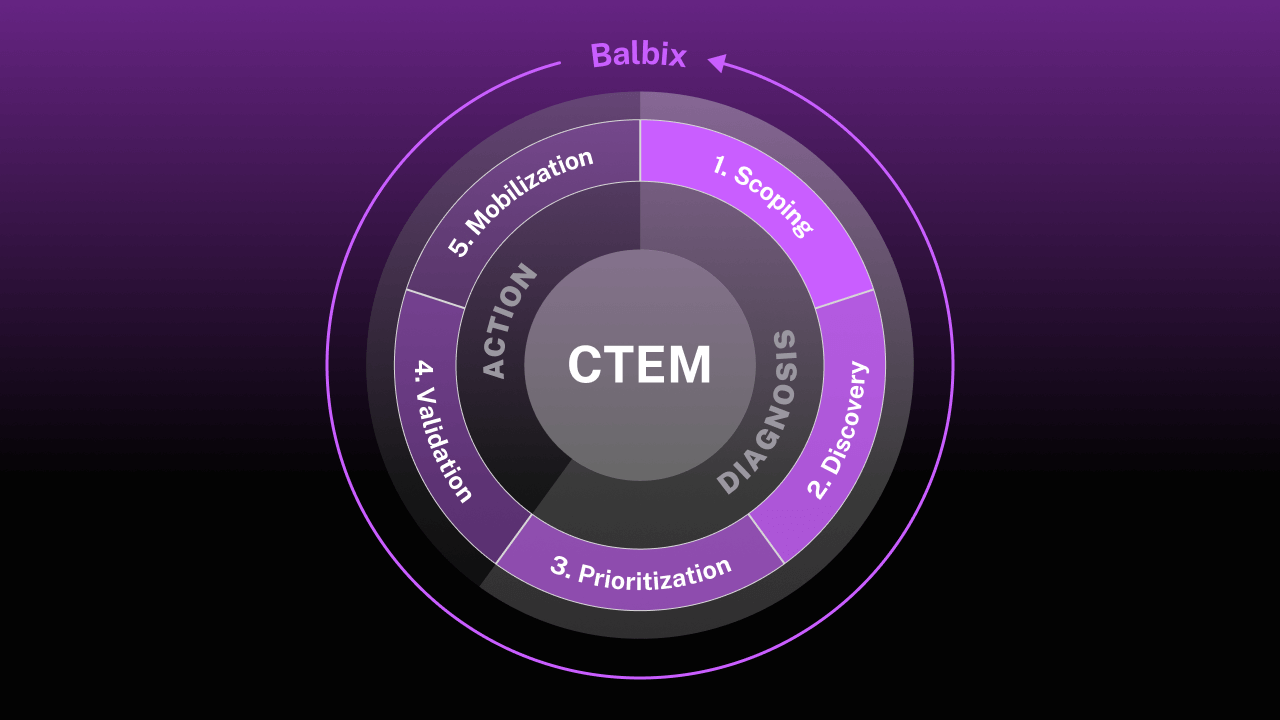
- An overview of the five-step CTEM process, from scoping your attack surface to mobilizing teams for faster exposure mitigation.
A detailed migration checklist to help you shift from traditional vulnerability management to exposure management..