What is cyber risk?
Cyber risk is the probability of exposure or potential loss resulting from a cyber attack or data breach. Typically, this type of risk encompasses damage and destruction of data, monetary loss, theft of intellectual data, productivity loss and reputational damage. When thinking about cyber risk, it’s important to first consider the vectors that can be used to breach sensitive assets and the various devices and apps at risk of being attacked within a network. This requires assessing an organization’s attack surface to determine where the critical IT assets are within a network. An attack surface assessment will also show how assets are related to each other and where the compromise of one asset essentially compromises another asset or significantly impairs the performance of another asset.

The knowledge gained from understanding an organization’s attack surface not only ensures a more accurate cyber risk calculation, it also provides security teams with detailed information about how to mitigate cyber risk.
Why is calculating cyber risk important?
Translating cyber risk into monetary units such as francs, euros, dollars, or other currencies can help organizations understand what their risk means in financial terms so they can make better decisions around managing it. With a more concrete understanding of cyber risk, security executives can demonstrate whether their efforts to lower risk throughout the organization are working and that security investments are paying off. It also allows decision makers to easily trace financial risks to the underlying assets and vulnerabilities so the risk can be quickly remediated. Most importantly, calculating risk can help security teams align their cyber program with the goals of business stakeholders, such as CFOs and board members, and convey risk in terms that are tied to business outcomes in a language everyone understands.
Different methods to calculate cyber risk
Organizations can use a variety of methods to calculate cyber risk, some of which are described below.
With a manual approach, like FAIR, qualitative human input, instead of actual operational data, is used to derive risk calculations. But this subjectiveness leads to a gap between the numbers reported and the truth around cyber risk. The manual-intensive process of such an approach also makes it challenging to frequently perform risk assessments. As a result, security leaders might find themselves making risk management decisions using outdated information.
An automated approach, like Cyber Risk Quantification, utilizes machine learning and AI to continuously analyze operational data in order to quantify cyber risk. The key benefit to this is that the risk calculation changes in real-time as new threats and vulnerabilities emerge, as security threats are mitigated, or as other changes happen in the enterprise environment. As a result, your risk calculation is more accurate and up-to-date.
Some organizations use a custom process that moves data from their tools into a centralized data lake, which is then analyzed with excel or via business intelligence (BI) tools to calculate cyber risk. Unfortunately, Do-It-Yourself (DIY) projects for calculating cyber risk are difficult to implement primarily due to lack of funding in data engineering, machine learning, and other experts needed to implement such a system.
How to calculate cyber risk?
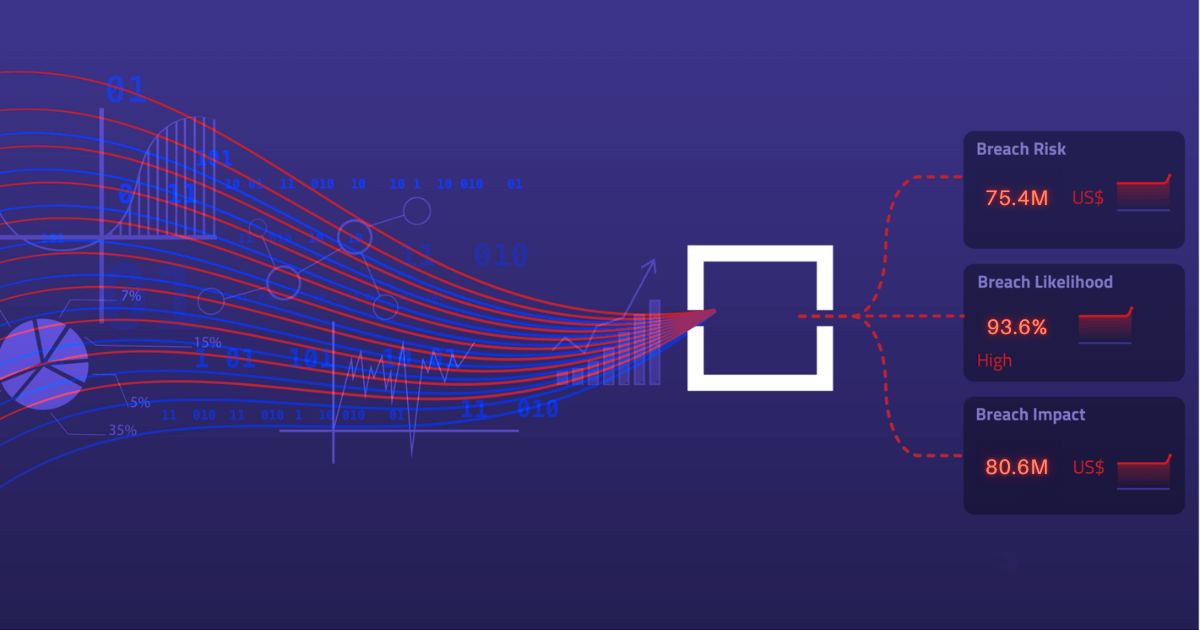
Calculating cyber risk is best done using an asset-centric approach. This requires a precise inventory of all IT assets – including systems, applications, devices, data, business processes, and users – and an understanding of two factors: breach impact and breach likelihood.
Breach likelihood is the probability that an asset will be breached. Calculating it requires accounting for vulnerability severity, threat level, exposure due to usage and security controls. The risk calculation should also understand the business significance of each asset as it is an important variable in determining the second factor – breach impact. For example, your breach impact is significantly higher for core servers containing sensitive data than for personal laptops that are signed into your guest network. While assessing business criticality of an asset, you need to consider both inherent (e.g., asset category, business unit) and contextual properties of the asset (e.g., roles, applications, user privilege, and interaction with other assets).
Risk is defined as the probability of a loss event (likelihood) multiplied by the magnitude of loss resulting from that loss event (impact). To accurately calculate cyber risk, this must be computed for every asset in your organization.

Challenges to calculating risk
It can be challenging for organizations to calculate cyber risk due to:
Lack of proper data
Your organization may have dozens of tools that generate data; however, it is difficult and time-consuming to sift through this data to find indicators of risk. Moreover, organizations continue to struggle with gaps in asset inventory, restricting security leaders from accurately assessing their cyber risks and vulnerabilities and understanding the effectiveness of their security tools. Without proper data, organizations don’t have a way to analyze the types of attacks, their frequency and the severity of their impact.
Lack of a unified risk model
It can be difficult to unify your data into a common risk model. Many organizations lack a solution that can seamlessly ingest data from their existing cybersecurity, IT, and relevant business tools to help them understand every aspect of their cybersecurity posture and build a unified cyber risk model.
Lack of visibility
New vulnerabilities and threats emerge at a very rapid rate, making it difficult to quickly identify, prioritize and remediate risk items. The objective of cyber security is to stay ahead of the adversary, but a lack of real-time information makes it difficult for security teams to streamline processes that protect the organization from threats. Without automatic and continuous visibility of the attack surface and emerging security issues, organizations have difficulty remediating risk quickly and effectively.
Benefits to calculating risk
Calculating cyber risk helps security teams:
- Communicate cyber risk to senior executives, board members and business risk owners in a common language that everyone understands – monetary terms, like dollars.
- Demonstrate the value of their cybersecurity program and provide the ROI for future security investments.
- Work with senior executives to determine acceptable levels of risk.
- Prioritize the mitigation of cyber security risks based on their potential business impact.
Calculating cyber risk with Balbix
One meaningful way to calculate cyber risk is by using specialized machine learning and automation to quantify both the likelihood and the impact of a potential breach. With Balbix’s Cyber Risk Quantification solution, security leaders can unify all of their cyber security data into a single comprehensive cyber risk quantification model. In doing so, everyone – from security analysts to the board – is provided with a continuous and real-time view of cyber risk in dollars. Additionally, Balbix produces risk calculations that are traceable to the underlying risk issues and assets, and empowers security leaders with necessary guidance and actionable steps to reduce cyber risk. CISOs can also slice and dice their network in dozens of ways and report on cyber risk by a line of business, by site, by the business owner, by type, etc.
Frequently Asked Questions
- What is cyber risk?
-
Cyber risk is the level of risk-posed to an organization in the event of a cyber attack or data breach. Typically, this type of risk encompasses damage and destruction of data, monetary loss, theft of intellectual data, productivity loss and reputational damage.
- Why is calculating cyber risk important?
-
Calculating cyber risk enables organizations to embrace their cyber security posture through a financial lens, providing them with a better understanding of their network environment. With this information, they are able to make informed security investments and implement the controls necessary to minimize the risk of a cyber attack or data breach.
- How can you calculate cyber risk?
-
Calculating cyber risk is best done using an asset-centric approach, which requires an accurate inventory of all IT assets and an understanding of two key factors: breach impact and breach likelihood. This is expressed in a risk equation where the probability of a loss event (likelihood) is multiplied by the magnitude of loss resulting from that loss event (impact). To accurately calculate cyber risk, this must be computed for every asset in your organization.
- What are the benefits to calculating cyber risk?
-
- Improved communication between security and leadership teams around risk posture and risk management.
- Better decision making around risk mitigation efforts based on financial impact.
- Improved understanding of the security environment and which risks pose the greatest threat to an organization.
- Ability to demonstrate the value of security programs and provide the ROI for security investments.