

November 17, 2021
Even with dozens of cybersecurity tools and mountains of data, are you still struggling to quantify your cyber risk?
If you answered yes, you are not alone. In fact, my experience suggests you are in the majority. In my conversations with CISOs over the years, they repeatedly tell me that when it comes to metrics, there isn’t a silver bullet. Instead, security leaders usually choose a maturity model against which they benchmark their technology, people and processes. They measure ‘performance’ based on maturity and use the model as a way to justify budget requests and allocations over a multi-year plan.
Yet, there still remains a need to quantify cyber risk, both for managing down (accessing the performance of the security team) and reporting up (demonstrating performance to the rest of the leadership team and often, the board of directors). To get an understanding of how that is being done, my colleagues spoke to a dozen security leaders earlier this month. The answer was consistent, they use operational metrics. For example, when it comes to software vulnerabilities, they all measure two things:
As these are useful to measure progress day-to-day, it’s not surprising that these are being used for managing team performance. For organizations using these vulnerability metrics, I recently wrote about how automation can help security leaders improve CVE remediation, which will in turn improve their performance using the metrics above.
Of course, besides MTTP and # of vulnerabilities, there are other metrics that security teams use in their board communication. These too are usually detection metrics, for example, detection rates for malware incidents, phishing attempts and other security events.
But when it comes to reporting up, these are vanity metrics. Operational metrics do not tie to any measurement that executives or board directors care about. Patch-based metrics are a poor proxy for estimating the overall cyber risk of an organization, and limit leadership’s ability to make good decisions.
In light of this, what was surprising in our quick survey was that MTTP and other patch-based metrics are what security leaders are relying on to report risk to leadership and the board. The CFO, CEO and board members of an organization typically care about two things: how an infosec program protects profit and how it enables revenue. Using operational metrics like MTTP or looking at maturity against a specific framework does not enable them to understand the risk to profit and revenue in dollars.
Some security leaders do publish risk score cards, and while this is better than nothing, they usually only cover a small portion of the enterprise. Their process can also be problematic. They often build scorecards by aggregating all of their organization’s security data into a data lake and doing some proprietary and ad hoc risk scoring there. This poses several problems. First, there are multiple data lakes that don’t talk to each other and may calculate conflicting cyber risk scores. Second, the process of creating the model is expensive, and hard to develop and maintain. And third, the results are usually not statistically sound, and ultimately do not help CFO, CEO and board understand the degree of risk to profit and revenue in dollars. These issues also apply to most organizations’ processes for rendering their GRC metrics.
Instead, cyber risk quantification must take into account exposure, threats, security controls and business criticality. Risk must also cover the vast majority, if not all the attack surface, otherwise it will be misleading and lull security teams into a false sense of security. Finally, it is important that the risk value is explainable (i.e., the factors driving risk can be known) and be actionable.
The chart below shows how organizations can mature cyber risk quantification from delivering operational outcomes to delivering more business outcomes (plug: Balbix allows our customers to measure and report on all of these metrics).
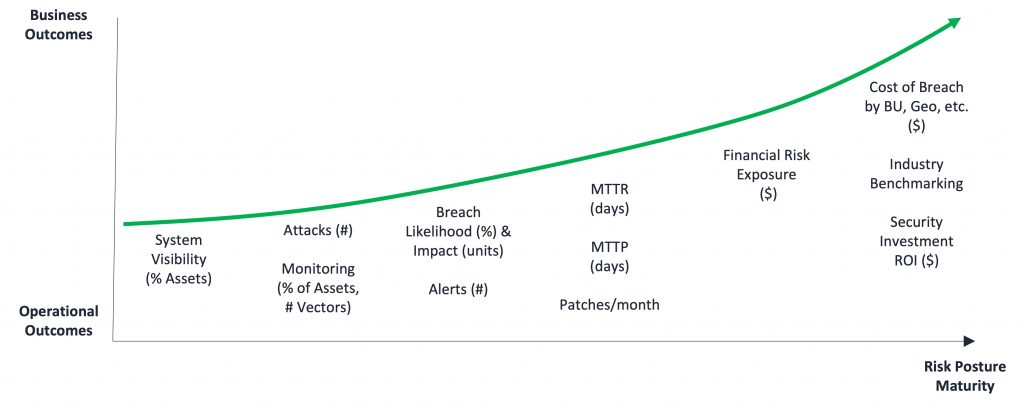
For security leaders, it is critical that cyber risk is quantified in monetary terms so that their CFO, CEO and board can appreciate the amount of risk in business terms. Calculating breach risk in monetary terms provides a common language that organizations – from security engineers and IT admins to the CISO, CFO and CIO – can use to prioritize projects and spending, and track the effectiveness of their overall cybersecurity program.
Most security leaders are on the journey to quantifying risk in monetary terms. The recently completed 2021 Gartner Cyber Risk Quantification benchmarking study provides a useful reference point about the sophistication of organizations’ CRQ methodologies today.
According to the Gartner study, 80 percent of organizations provide estimates of likelihood and impact in terms of ordinal scales. However, a risk score that is denominated as high/medium/low or on a scale of 1-10 is not very useful for decision making. For example, senior stakeholders will not be able to appreciate that a score of 7 out of 10 corresponds to a high likelihood of a data breach with a $25 million price tag.
On the other hand, only 20 percent of organizations in the Gartner study said they are using statistical modeling techniques to generate risk exposure probabilities, and even fewer, four percent, are using machine learning techniques using big data to determine real-time risk. But, as I mentioned, this is the direction organizations want to go: 43 percent and 25 percent of respondents say they are looking to use these methodologies, respectively. This is exactly what Balbix does.
Unfortunately, most organizations continue to struggle with measuring cyber risk due to their reliance on complicated manual processes and dozens of isolated IT, security and business tools.
In August, we announced the availability of our Automated Cyber Risk Quantification solution. Balbix’s new offering allows organizations to produce a single, comprehensive view of their cyber risk in dollars (or other currencies) so they can prioritize and fix security vulnerabilities faster and reduce breach risk.
As Rhonda Gass, Chief Information Officer at Stanley Black & Decker noted at the time of our announcement, “Balbix is an industry-leading platform that consolidates cyber risks into a single reportable model. This technology is enabling us to scorecard our risk remediation performance and gain continuous visibility into open security issues.”
One of the benefits of Balbix’s approach is that it converts raw data into executive views of cyber risk. Gone are the days of security leaders lamenting that they have, “mountains of data, but no insights.” Balbix brings all stakeholders together on the same page using the common language of money (Dollars, Euros, Pounds, etc.).
Risk is defined as the probability of a loss event occurring in a given unit of time (likelihood) multiplied by the expected magnitude of loss resulting from that loss event (impact). Cyber risk is the expected loss resulting from a cyberattack or data breach.

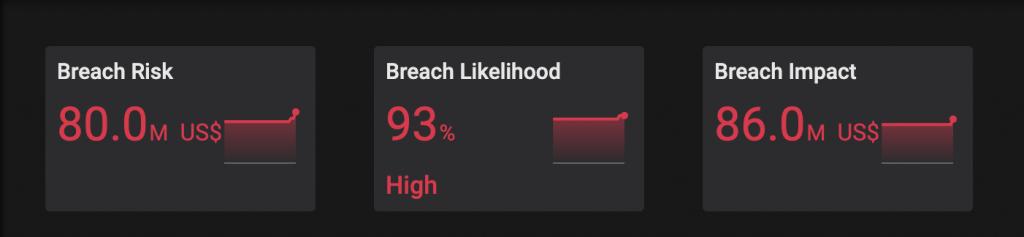
Balbix calculates the overall breach likelihood of an asset as a weighted sum of breach likelihood from individual attack vectors. Breach impact is calculated through a combination of Balbix’s advanced analytics and the first hand knowledge of the security team. The example below shows an organization with a breach risk of $80 million, which is equal to a breach likelihood of 93 percent multiplied by a potential company-wide breach impact of $86 million.
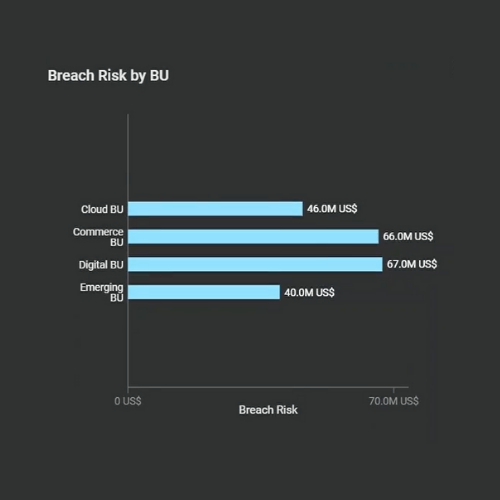
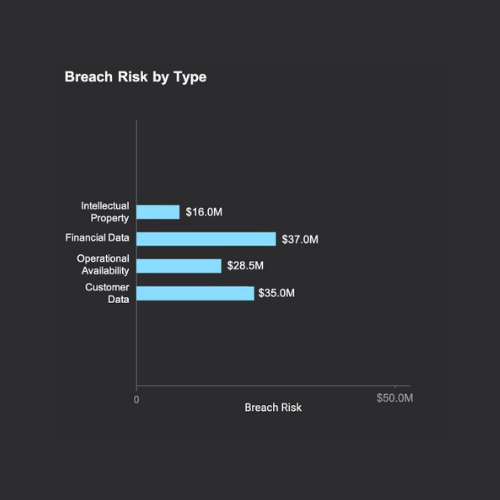
With the breach risk in hand for each asset, risk can then be grouped into categories that align to the needs of the business. For example, breach risk broken out by business unit and by business impact (see images below). The more detailed level of visibility allows business owners to understand their cyber risk and work with the security team to manage it appropriately.
Better Decisions
Being able to measure and monitor breach risk is a big step for most organizations. However, it is not the final step. Hard risk metrics denominated in monetary terms enable everyone involved to make better decisions faster, and mitigate vulnerabilities and security issues faster.
These thoughts are echoed by Jon Oltsik, Senior Principal Analyst and Fellow at ESG: “The Infosec industry has struggled for a long time to quantify the security posture of their organizations in clear cyber risk terms denominated in Dollars (or Euros, Pounds, Yen, etc.). As a result, the right decisions don’t get made, leaving the enterprise vulnerable to attack and compromise. Balbix’s innovative offering has the promise of changing this equation.”
A less obvious, and somewhat self-interested, function of cyber risk quantification is that it also allows security leaders to demonstrate the value of the cybersecurity program.
Generally speaking, quantifying risk in monetary terms allows security leaders to quantify the cyber risk of the organization and demonstrate improvements over time. More specifically, security leaders are also now able to show ROI. As I mentioned at the outset, security leaders typically justify their investments and budgets by aligning them to a maturity model. Now, having quantified cyber risk, they can make clear business cases with monetary justification for their investments, for example, that spending $200,000 on an identity and access management (IAM) solution will reduce password and credential risk by $2 million.
Ultimately, the objective of cybersecurity is to stay a few steps ahead of the adversary. Being able to quantify cyber-risk enables organizations to streamline how security teams achieve the outcomes described above. Hard risk metrics denominated in monetary terms with clear action items enables everyone involved to make better decisions, faster. The net of this is organizations are able to identify, prioritize and mitigate vulnerabilities and security issues faster.
Read our whitepaper, Automated Cyber Risk Quantification Using the Balbix Platform, to learn more about how Balbix automates cyber risk quantification.