November 11, 2021
Balbix is in the business of helping organizations automate their security posture so they can reduce their attack surface and decrease the likelihood and impact of a breach. Automating CVE remediation plays a central role in achieving these outcomes, in fact, CVE reduction often rises to the attention of organizations’ executive leadership team and board of directors.
Cybersecurity more generally is increasingly a board-level issue. Gartner predicts that, “by 2025, 40% of boards of directors will have a dedicated cybersecurity committee overseen by a qualified board member.” CVE remediations specifically come to the attention of executives and board members on two regular occasions.
The first is a “drop everything” moment: a breach based on a software vulnerability hits newspaper headlines and leadership wants to know what their risk is. Does the organization use that software? Where is it present? Is the required patch applied? What is the risk to the business of any unpatched instances?
The second interaction with leadership is equally important but could be characterized as, well, boring by comparison. Leadership wants regular updates on the organization’s security posture and whether the security team is reducing the organization’s risk over time. For the security team, this is the daily activity of burning down their CVE backlog. It comes with increasing scrutiny and ever tighter SLAs. For example, the Biden administration announced that it is requiring civilian agencies to fix hundreds of CVEs, and that those published in 2021 be fixed within 2 weeks.
Automating CVE remediation helps in both cases. It allows security teams to work faster: either to respond to a high profile situation or to meet ever shrinking SLAs. As important, automation provides security teams with the business context for decision making when it comes to prioritizing their work and making the biggest impact on reducing their organization’s cyber risk. Let’s take a look at the two situations above in more detail to see how.
“CVE-XXXX-XXXX” is in the headlines and needs to be urgently resolved. Responding is a two-step process: understanding the level of risk and then remediating as necessary. For most organizations, this is really time consuming. For example, before working with Balbix to automate their processes, a large technology company used to take several weeks to pull together a list of all the assets that needed to be patched whenever a headline-worthy CVE emerged. Similarly, after remediating the vulnerability, it took them several more weeks to be able to compile a list confirming that patches had been both downloaded and installed. These timelines are not uncommon. Fortunately, with the help of automation, the technology company was able to bring the time required to assess their environment and report on remediation down to minutes.
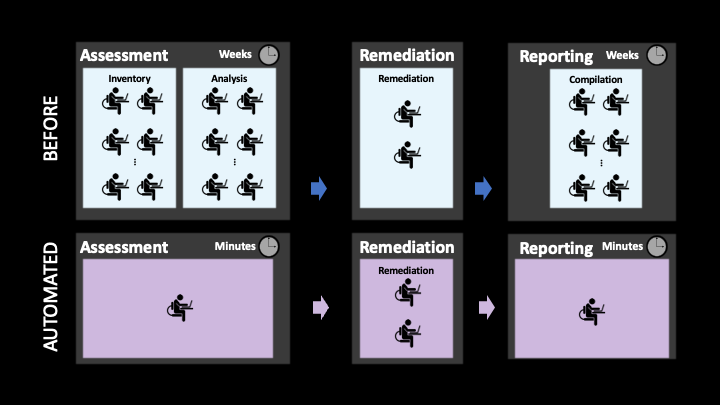
Let’s look at the individual steps involved and see how automation can help with CVE remediation and with reporting to the board.
Unfortunately most security teams don’t have access to a good inventory of their assets. They likely rely on their vulnerability management software which may, or may not, sync with their CMDB. What we have found in practice is that asset databases are wildly out of date. In one recent case, we were able to determine that the asset database the company was using was 10x the size of the actual number of assets deployed in the organization. The security team was spending a lot of time chasing ghosts.
Instead, Balbix ingests data from existing vulnerability scanners, CMDB and other tools like EPP/EDR, cloud infrastructure and security applications and then uses machine learning and other advanced analytics to correlate these data sources and deduplicate assets in the resulting database.
Another important difference in the asset inventory (as well as for the software and risk information we’ll look at below) is that Balbix is constantly being updated. Updates aren’t dependent on intermittent vulnerability scans. Having an accurate view is important for the security team to do the remediation. It also means that they can provide their leadership with access to a dashboard(s) with confidence that it will provide a complete and up-to-date overview of their progress.
The next step is to determine if affected software is deployed on these assets. The good news is that vulnerability management tools provide high fidelity information about assets where their agents are deployed. Unfortunately, there is less fidelity on assets where an agent hasn’t been deployed but the asset has been scanned, and almost no software information on assets that aren’t in the vulnerability management application’s inventory due to failed scans or other reasons. To fill the void, the technology company I mentioned earlier, ran scripts to gather all the inventory information they needed and then correlated that information with data from their asset systems.
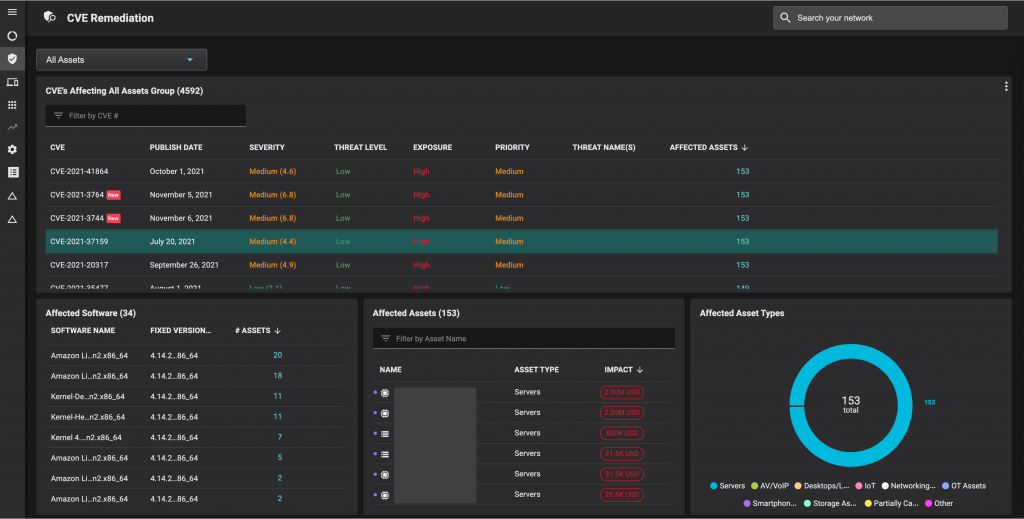
In contrast, Balbix continuously updates information about the software deployed on assets, and not just the OS but other IT, business and security applications. One example, illustrated in the image below, is for CVE 2021-37159 that affects the Linux kernel. Balbix automatically provides the list of affected software, on-premises and in the cloud. Balbix also lists the 153 assets where the software is deployed, all servers in this case.
Knowing where potentially unpatched software resides, security analysts then have to determine what the risk is in each case. Traditional vulnerability management takes into account external factors such CVSS scores and threat levels. However, their ability to assign risk based on an individual organization’s business context is limited to applying tags. For example, they can add a tag if the asset contains sensitive information or is accessible over the Internet, or they can add a criticality label (‘very high’, etc.).
Balbix prioritizes risk automatically based on five factors. The first two are severity and threats. Two more are asset exposure, whether an asset is accessible over the Internet, and business criticality. These are determined automatically using analytics, and business criticality can also be measured in monetary terms. Being able to speak in financial terms allows the security team to discuss the risk of a CVE with the CFO and the board in the common language of dollars and cents. And last, but not least, Balbix also provides a list of security controls for any asset. This can be critical: if the EDR tool indicates that ransomware has been deployed on XYZ devices, the analyst can prioritize fixing the assets where backup and recovery software is not in place.
For each instance where a vulnerability needs to be remediated, analysts must determine which patch to deploy. Traditional vulnerability management tools provide a list of potential patches, say five, or will list the most recent patch. That may leave the analyst having to figure out the best patch to use. Instead, Balbix suggests the best patch by looking at all applicable patches and determining which patch maximizes risk reduction while minimizing the effort required to patch.
Balbix then indicates whether there are impediments to deploying the patch by bringing in context about the asset. For example, suppose an asset owner is solving an application issue related to Java, and that applying the patch means risking downtime or spending a ton of time testing to make sure there is no downtime. If the asset owner knows they have backup in place, they may not have to test as rigorously. They can also factor in the underlying risk – in terms of breach vs downtime – in order to determine how much to test.
Balbix also shows when the software has been updated. This is important as the patch hasn’t truly been applied until a reboot or update has occurred.
Many of the same principles and processes used to respond to an active exploit also pertain to the day-to-day work of a vulnerability management program. The security team needs to be confident their asset and software inventory is accurate, and that they are not chasing ghosts.
Again, Balbix provides the list of exposed software versions and assets, and then correlates them. In the example below, Balbix identifies affected browser versions, in this case Firefox. You can see that six assets have Firefox 71.0 deployed.
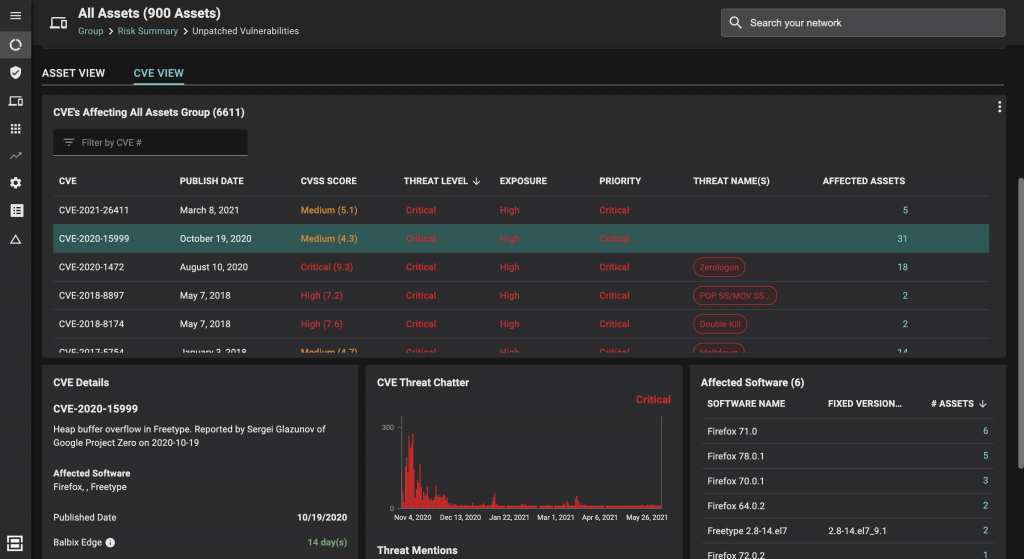
Balbix also makes searching for CVEs easy. Unlike other vendors that require the security team to develop search expertise, for example by learning a structured query language, Balbix allows you to easily search for, and filter, CVEs based on a broad range of attributes. These attributes are constantly being updated for each asset including specific asset categories and software vendors. The image below shows another example using search parameters for SLA compliance, CVSS scores, threat levels and patch SLA times; a subset of Balbix’s search capabilities.