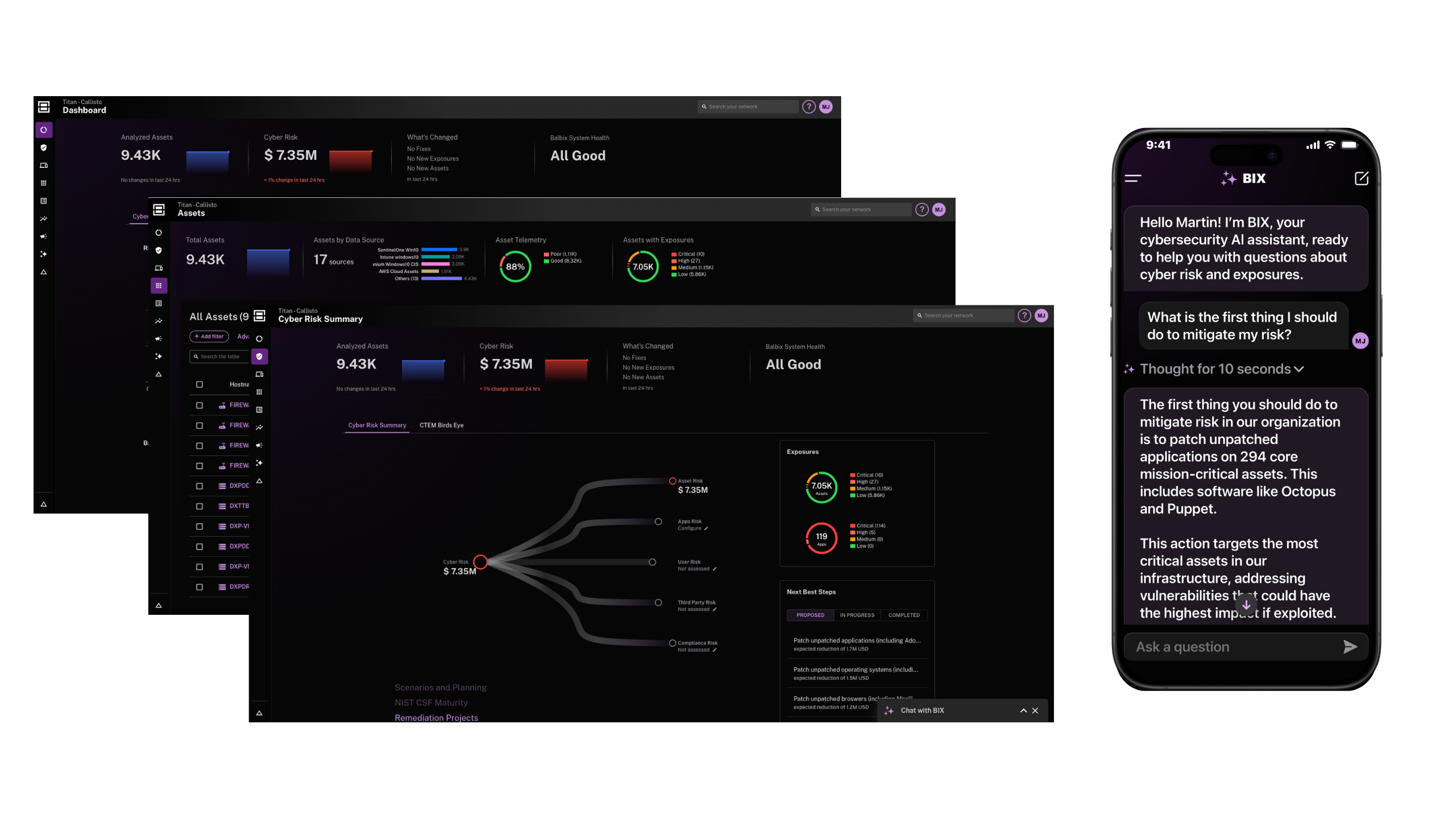
April 25, 2025
Webinar Recap: How AI is Revolutionizing Cybersecurity in Healthcare
January 27, 2025
Is Your Vulnerability Management Strategy Doing More Harm than Good?
November 11, 2024
Four New Balbix Capabilities You’ll Love!
Stay up to date with us
Get insights on cyber risk management, vulnerability prioritization and board reports

August 27, 2024
Seeing the Unseen: How Generative AI Elevates Situational Awareness in Cybersecurity

August 22, 2024
CAASM: Dead-End Approach or Worthwhile Journey?
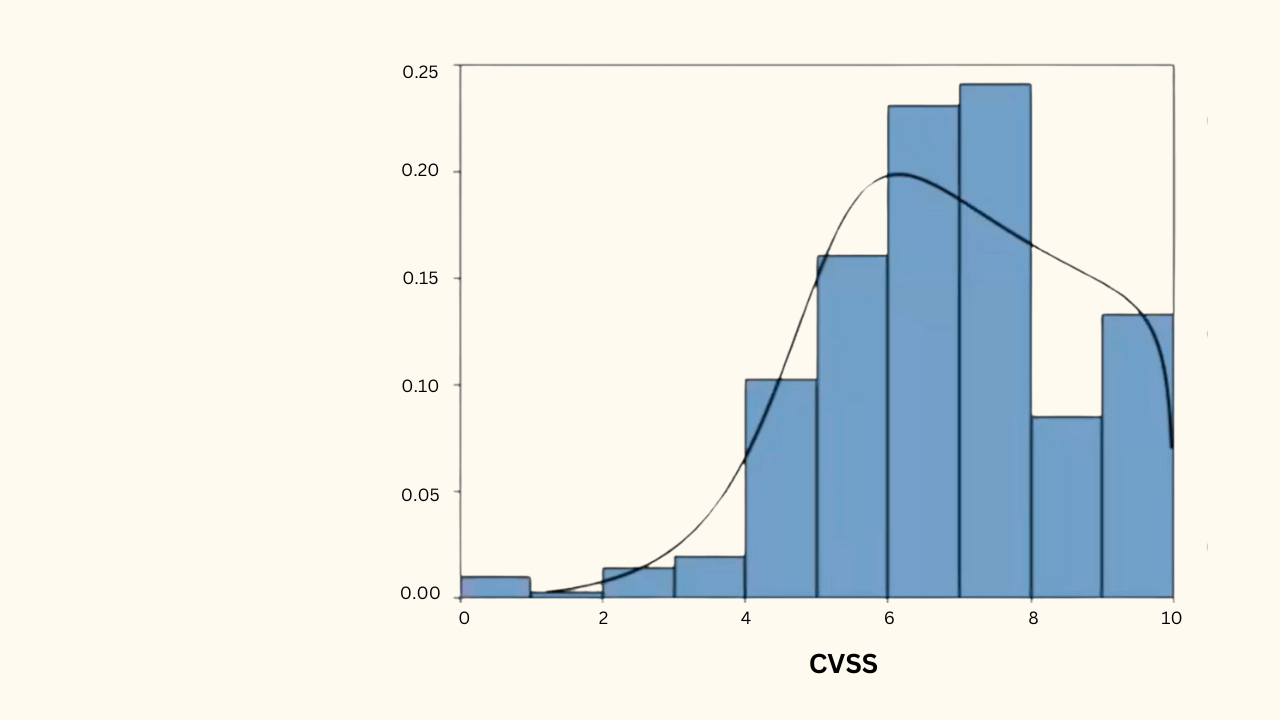
June 10, 2024
Is CVSS Alone Failing Us? Insights From Our Webinar With Verizon

May 13, 2024
RSAC 2024 Recap: The Art of the Possible with AI & Cyber Risk Management
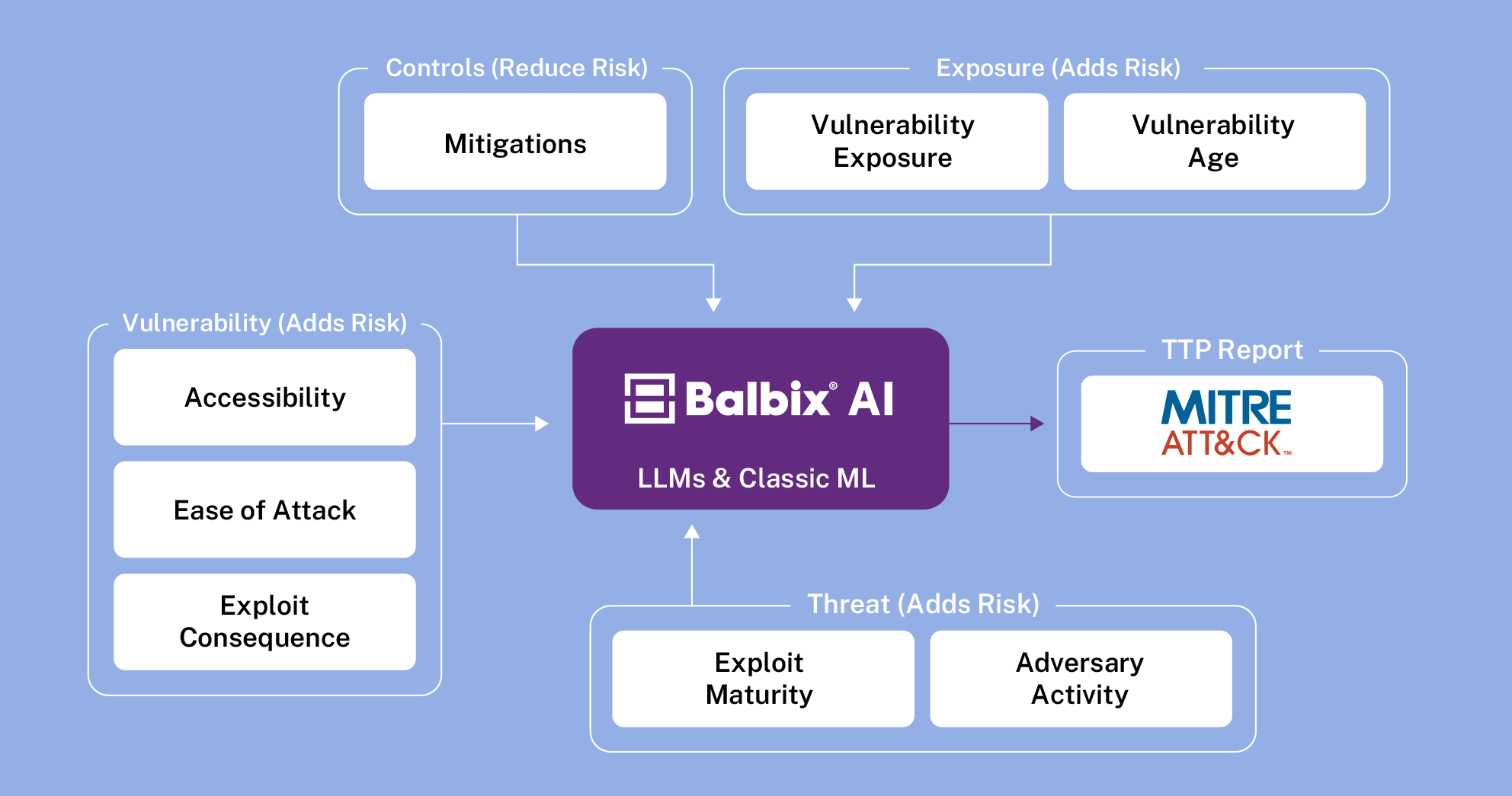
April 2, 2024
Prioritizing Cyber Risk: Get a leg up with AI

December 3, 2023
Flying Blind: Is your Vulnerability Management program working?
November 1, 2023
Cybersecurity Demands a Singular Understanding of Cyber Risk
October 26, 2023