
June 10, 2024
In a recent webinar with Verizon, we discussed how organizations measure and prioritize their vulnerabilities. We reviewed insights from Verizon’s 2024 Data Breach Investigations Report, and double-clicked on data to answer several other key questions, such as:
Is the Common Vulnerability Scoring System (CVSS) sufficient for prioritization?
Does Exploit Prediction Scoring Systems (EPSS) with CVSS help or hurt prioritization?
Are there any shortcomings of CVSS by design? How can organizations better prioritize vulnerabilities?
Let’s dive in.
First, good news: CVSS is not entirely failing us. However, its limitations become more apparent as the scope and scale of vulnerabilities increase. CVSS excels at rating the severity of vulnerabilities based on their attributes; however, it does not assess the likelihood of exploitation, which is a critical factor, as not all vulnerabilities rated as severe are exploited at the same rate, if at all.
The static nature of CVSS scores also challenges keeping pace with how quickly vulnerabilities can inflict damage and evolve, complicating organizations’ auditing and record-keeping. This ineffective prioritization makes it difficult for organizations to effectively address a significantly large number of vulnerabilities.
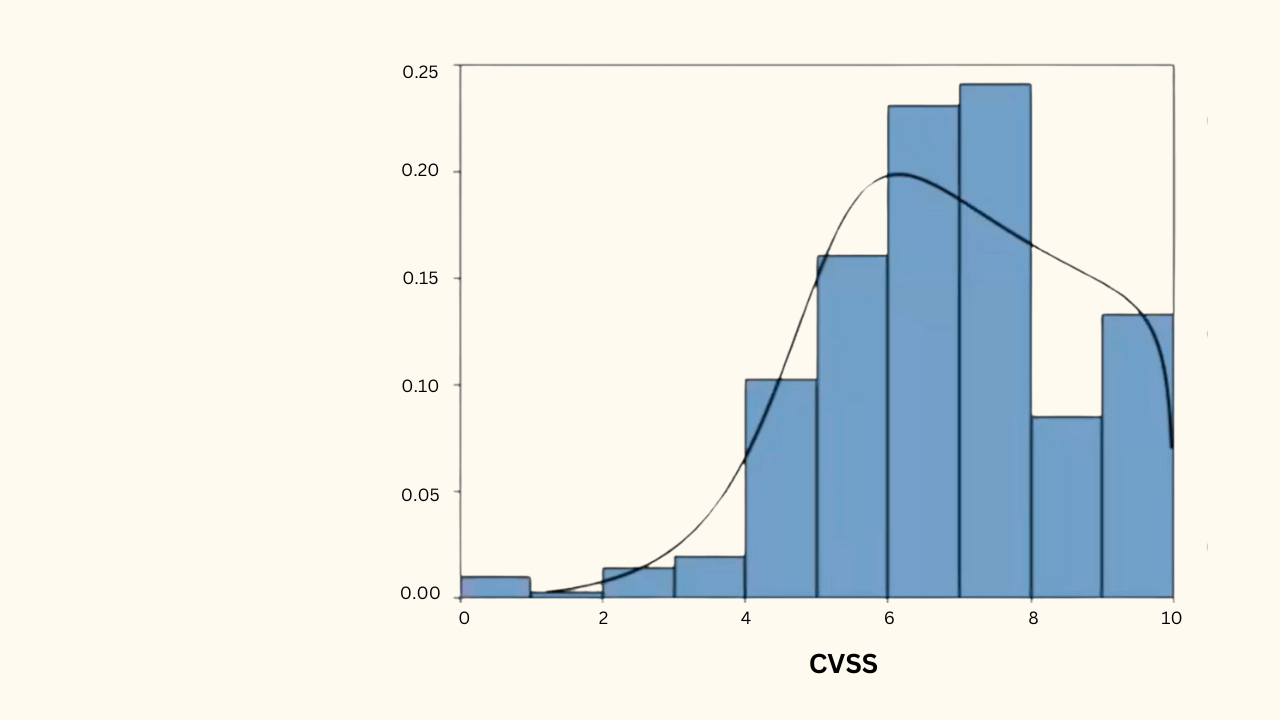
To put this into perspective on the CVSS scale, about 90% of vulnerabilities score above 4.5, and about 50% score above 7.0, Thus, it is impractical for organizations to address all high-scoring vulnerabilities with CVSS alone.
EPSS (Exploit Prediction Scoring System) focuses on the intent and likelihood of exploitation. Using EPSS with the CVSS, organizations can prioritize vulnerabilities by severity and risk of exploitation in the wild.
EPSS provides cyber threat intelligence and forecasts the likelihood that a software vulnerability will be exploited based on historical exploit data. It supplements the CVSS, which rates the severity of vulnerabilities based on their attributes but doesn’t assess exploitation likelihood. Using EPSS in conjunction with CVSS, organizations can prioritize vulnerabilities by severity and risk of exploitation in the wild.
For example, if there are 600 current vulnerabilities listed on CISA KEV, roughly 300 will have a CVSS score of 7.0 or higher. For a large enterprise organization, that will represent around 80,000 vulnerability instances amongst 10,000 assets, which is still a significant problem to surmount.
However, with EPSS, depending on the vulnerabilities, you can prioritize the vulnerability remediations that will have the most considerable impact on the organization’s risk. In the webinar, we estimated that only about 10% of the 300 7.0+ CVSS vulnerabilities hold the most significant result, so you’re now facing only 8,000 highest-priority vulnerability instances within a large organization.
As mentioned in a previous article on our DBIR findings, don’t wait for a vulnerability to appear on CISA KEV to be remediated. There’s a significant gap between adversary scanning times for vulnerabilities reported by CISA KEV, which is five days, and 68 days for non-CISA KEV vulnerabilities. Using a system that incorporates several models better equips larger enterprises with the tools their teams need to prioritize the highest-risk vulnerabilities within their organization.
By adopting a risk-based approach that considers both threat and impact, data shows that remediation of just 0.1% of vulnerability instances can significantly reduce risk.
With a multi-pronged approach, you can collect threat intelligence through numerous sources and determine their overall risk from those multiple models. Then, organizations have comprehensive visibility into their external and internal risk landscape and can prioritize their vulnerability management activities based on the potential business impact.
This webinar’s two keystones are that risk is the true north star and security is a shared responsibility. The sheer volume and increasing speed of cybersecurity risks challenge the traditional, conservative approach to vulnerability prioritization. Organizations should focus on the intent and likelihood of cyber threats through cyber risk platforms such as Balbix to provide a path forward for effective prioritization in vulnerability management.
In addition, CVSS has limitations, particularly in not assessing the likelihood of a vulnerability being exploited. With EPSS and CVSS combined, organizations can more effectively prioritize vulnerabilities but can benefit by incorporating additional factors such as asset exposure and business impact. With this approach, enterprises can significantly reduce their risk by focusing on the vulnerabilities that pose the most immediate threat, regardless of their presence on CISA KEV.
Discover how Balbix can transform your approach to vulnerability management, making your cybersecurity efforts more dynamic and resilient against emerging threats. Let’s schedule a demo to show you Balbix in action and discuss how we can tailor our solutions to your needs.
You can watch the full webinar on-demand now to learn more about the takeaways above.