What Are CVSS Base Scores?
CVSS Base Scores are a key element of the Common Vulnerability Scoring System (CVSS), providing a standardized measure of a vulnerability’s severity. These scores quantify the inherent traits of a vulnerability, such as how easily it can be exploited and its potential impact. CVSS Base Scores remain constant over time, making them crucial for consistent risk assessment and prioritization in vulnerability management.
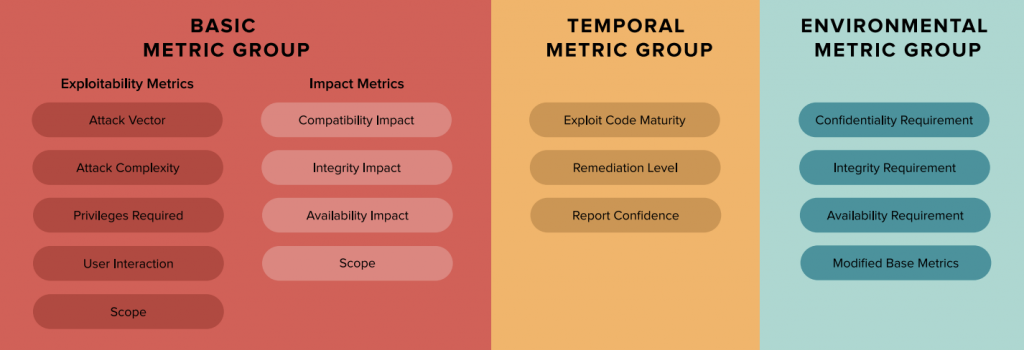
The CVSS framework includes three metric groups: Base, Temporal, and Environmental. The Base Metrics evaluate the intrinsic properties of a vulnerability, while Temporal Metrics adjust the score based on factors like patch availability or exploit maturity. Environmental Metrics further refine the score to reflect an organization’s specific environment and security needs, making CVSS a versatile tool for risk prioritization.
How are CVSS Base Scores Calculated?
CVSS Base Scores are determined by evaluating a vulnerability’s exploitability, impact on Confidentiality, Integrity, and Availability (CIA Triad), and scope of effect. Factors like Attack Vector, Privileges Required, and potential system-wide impact are assessed to generate a severity score between 0 and 10.
When looking up a CVSS score for a vulnerability in a third-party system like NIST’s National Vulnerability Database, the reported score is almost always the CVSS Base Score. Public severity rankings, such as those listed in NIST’s National Vulnerability Database (NVD), refer exclusively to Base CVSS scores. These factors are categorized into three sub-groupings:
Exploitability Metrics
Exploitability metrics in CVSS Base Scores evaluate how easily a vulnerability can be exploited. These metrics include:
- Attack Vector (AV): Assesses the level of access required for exploitation, from remote Network (N) access to Physical (P) access. The Attack Vector metric is scored in one of four levels:
- Network (N): Vulnerabilities with this rating are remotely exploitable, from one or more hops away, up to and including remote exploitation over the Internet.
- Adjacent (A): A vulnerability with this rating requires network adjacency for exploitation. The attack must be launched from the same physical or logical network.
- Local (L): Vulnerabilities with this rating are not exploitable over a network. The attacker must access the system locally or remotely (via a protocol like SSH or RDP) or use social engineering or other techniques to trick an unsuspecting user into helping initiate the exploit.
- Physical (P): In this type of attack, the adversary must physically interact with the target system.
- Attack Complexity (AC) measures the difficulty of exploitation, with Low (L) requiring no special conditions and High (H) needing specific preconditions. This metric indicates conditions beyond the attacker’s control that must exist in order to exploit the vulnerability. Most commonly, this refers to either required user interaction or specific configurations of the target system. The Attack Complexity metric is scored as either Low or High:
- Low (L): There are no specific pre-conditions required for exploitation.
- High (H): Conditions beyond the attacker’s control must exist for a successful attack. For this type of attack, the attacker must complete a number of preparatory steps to get access. This might include gathering reconnaissance data, overcoming mitigations, or becoming a man-in-the-middle.
- Privileges Required (PR): Indicates the level of privileges needed by the attacker, ranging from None (N) to High (H).
- None (N): No privilege or special access is required to conduct the attack.
- Low (L): The attacker requires basic “user” level privileges to leverage the exploit.
- High (H): Administrative or similar access privileges are required for a successful attack.
- User Interaction (UI): Determines whether user involvement is necessary. User Interaction is a yes/no metric:
- None (N): No user interaction is required.
- Required (R): A user must complete some steps for the exploit to succeed. For example, a user might be required to install some software.
Impact Metrics
Impact Metrics in CVSS Base Scores are critical for assessing the potential consequences of a successful exploitation of a vulnerability in the security of a system. These metrics focus on the well-known CIA Triad—Confidentiality, Integrity, and Availability—which are fundamental principles in information security:
- Confidentiality (C):
This metric measures the extent to which unauthorized access to data could occur due to a vulnerability. If confidentiality is compromised, sensitive information may be exposed to unauthorized parties. Confidentiality has three metric values:
- High (H): The attacker has full access to all resources in the impacted system, including highly sensitive information such as encryption keys.
- Low (L): The attacker has partial access to information and no control over what they can access.
- None (N): No data is accessible to unauthorized users due to the exploit.
- Integrity (I):
Integrity refers to the trustworthiness and accuracy of data. This metric evaluates the possibility of data being tampered with or altered by an attacker. A loss of integrity could mean that critical data is changed, inserted, or deleted, leading to incorrect information being stored or displayed. Integrity has three metric values:- None (N): There is no loss of the integrity of any information.
- Low (L): A limited amount of information might be tampered with or modified, but the protected system has no serious impact.
- High (H): The attacker can modify any or all information on the target system, resulting in a complete loss of integrity.
- Availability (A):
Availability measures the impact of a vulnerability on the accessibility of the system or its data, such as when a system crashes or goes through a DDOS attack. A compromise in availability means that users may be unable to access the system or its services as needed. Availability has one of three metric values:- None (N): There is no loss of availability.
- Low (L): Availability might be intermittently limited, or a successful attack might negatively impact performance.
- High (H): There is a complete loss of availability of the impacted system or information.
Scope (S) Metrics
Scope metrics in CVSS Base Scores evaluate whether a vulnerability’s exploitation can affect systems beyond its immediate environment.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

According to FIRST, “a security authority is a mechanism (e.g., an application, an operating system, firmware, a sandbox environment) that defines and enforces access control in terms of how certain subjects/actors (e.g., human users, processes) can access certain restricted objects/resources (e.g., files, CPU, memory) in a controlled manner. All the subjects and objects under the jurisdiction of a single security authority are considered to be under one security scope. If a vulnerability in a vulnerable component can affect a component which is in a different security scope than the vulnerable component, a Scope change occurs.“
This metric determines if a vulnerability, when exploited, impacts only the local security authority or if it has broader implications:
- Unchanged (U): The vulnerability’s impact remains confined to the original security boundary, affecting only the local system or component.
- Changed (C): The vulnerability’s exploitation extends beyond the local system, potentially compromising other components or systems within a different security boundary.
Quick Note: CVSS v3 included a revised scoring system for impact metrics, adding a “Scope” metric to evaluate the broader impact, and introduced temporal and environmental metrics for a more comprehensive assessment. These improvements help provide a more accurate and context-aware vulnerability evaluation.
How has CVSS Base Scoring changed from 2.0 to 3.0 to 4.0?
CVSS Base Scoring has changed substantially with each update. CVSS 2.0 featured simpler, less detailed base metrics, lacking Scope, User Interaction, and Privileges Required. CVSS 3.0 expanded the framework by introducing these metrics and refining existing ones for improved accuracy. CVSS 4.0 further enhances clarity and granularity, making vulnerability assessments more precise and relevant to modern security challenges.
| Aspect | CVSS 2.0 | CVSS 3.0 | CVSS 4.0 |
| Scope Metric | Not included | Introduced | Further refined for more granularity |
| User Interaction (UI) | Not included | Introduced | Refined for clarity |
| Privileges Required (PR) | Not included | Introduced | Maintained with possible refinements |
| Attack Vector (AV) | Network, Adjacent, Local | Added Physical access option | Maintained with improved definitions |
| Attack Complexity (AC) | Low, Medium, High | Simplified to Low, High | Further refinement for clarity |
| Confidentiality, Integrity, Availability (CIA Triad) | Basic (None, Partial, Complete) | More granular (None, Low, High) | Maintained with potential enhancements |
The Role of CVSS Base Scores in Risk Assessment
CVSS Base Scores play a crucial role in the risk assessment and prioritization process, serving as a foundational metric for evaluating the severity of vulnerabilities. These scores quantify a vulnerability’s inherent characteristics, such as its exploitability and impact, offering a standardized baseline that organizations can use to assess potential threats to their systems.
Security teams can prioritize vulnerabilities based on their inherent characteristics using CVSS Base scores. However, a comprehensive risk assessment should also consider the broader context provided by temporal and environmental scores.
Key Aspects of CVSS Base Scores in Risk Assessment:
- Baseline for Vulnerability Evaluation:
CVSS Base Scores provide a consistent method for evaluating vulnerabilities, allowing security teams to compare and prioritize threats based on their intrinsic severity. This baseline score helps organizations quickly identify which vulnerabilities might pose the most significant risk if addressed. - Prioritization of Vulnerabilities:
Using CVSS Base Scores, security teams can prioritize vulnerabilities according to their inherent characteristics, such as the ease of exploitation and the potential impact on confidentiality, integrity, and availability (CIA Triad). This prioritization is critical for allocating resources efficiently, ensuring that the most severe vulnerabilities are remediated first. - Limitations of Base Scores:
While CVSS Base Scores are valuable, they do not account for Temporal and Environmental Factors, which can significantly influence the actual risk posed by a vulnerability. Temporal factors, such as the availability of patches or the presence of exploit code, can change the urgency of addressing a vulnerability. Environmental factors, such as the specific configuration and usage of the affected system within an organization, also affect the actual risk. - Comprehensive Risk Assessment:
For a more accurate and actionable risk assessment, it’s essential to consider the broader context provided by Temporal and Environmental Metrics. These additional metrics adjust the Base Score to reflect real-world conditions, helping organizations better understand the threat level. Incorporating these factors into the risk assessment process ensures that vulnerabilities are prioritized based on their inherent characteristics, relevance, and impact within the specific organizational environment. - Integration with Advanced Risk Management Tools:
To fully leverage CVSS Base Scores in risk assessment, organizations should integrate them with advanced risk management and exposure management tools. These tools can automatically adjust base scores using Temporal and Environmental Metrics, providing a more nuanced view of the risk landscape. This integration allows for a more proactive approach to vulnerability management, enabling security teams to focus on the most pressing threats.
Best Practices for Using CVSS Base Scores in Exposure Management
To maximize the effectiveness of CVSS Base Scores in your exposure management strategy, follow these best practices:
- Integrate CVSS Scores with Exposure Management Tools:
Utilize exposure management platforms, such as Balbix, to enhance the utility of CVSS Base Scores. These tools allow you to correlate CVSS scores with your business context, asset criticality, and other risk factors. By integrating CVSS scores with exposure management solutions, you can prioritize remediation efforts based on vulnerabilities’ specific impact on your organization, ensuring that resources are allocated where they are needed most. - Incorporate Temporal and Environmental Factors:
CVSS Base Scores provide a foundational assessment of vulnerability severity but do not capture the complete risk picture. To avoid underestimating or overestimating a vulnerability’s impact, it’s crucial to account for Temporal Metrics (such as the availability of patches or exploit code) and Environmental Metrics (which consider the unique aspects of your organization’s infrastructure and security posture). Adjusting the base score with these factors enables a more accurate and context-specific risk assessment. - Implement Continuous Monitoring and Reassessment:
Vulnerabilities are dynamic; risk levels can change as new information emerges or your environment evolves. Regularly updating and reassessing CVSS scores is vital for accurately understanding your exposure. Continuous monitoring ensures you capture changes in the threat landscape, such as discovering new exploits or releasing patches, allowing you to adjust your risk priorities in real-time. - Prioritize Based on Business Impact:
Not all vulnerabilities pose the same level of threat to your organization. Prioritize vulnerabilities not only by their CVSS Base Scores but also by their potential impact on your business operations. High CVSS scores should be cross-referenced with the criticality of the affected systems to ensure that vulnerabilities with the most significant potential business impact are addressed first. - Automate Where Possible:
Automation can enhance the efficiency of your vulnerability management process. Use automated tools to regularly pull in the latest CVSS data, apply temporal and environmental adjustments, and trigger remediation workflows based on your organization’s risk tolerance. Automation helps ensure that your vulnerability management efforts are both consistent and scalable. - Communicate Risk in Business Terms:
When using CVSS scores to communicate risk to non-technical stakeholders, translate the technical metrics into business impact. Explain how specific vulnerabilities could affect operations, revenue, or customer trust. This approach ensures that executives and decision-makers understand the urgency and importance of addressing particular vulnerabilities.
Operationalizing CVSS Scores
To effectively operationalize CVSS scores in your vulnerability management program, it’s crucial to go beyond just the Base Metrics. While Base Scores generally assess a vulnerability’s potential severity, they don’t fully answer the critical question: “Can this damage my company?” To achieve a more accurate and actionable risk assessment and ensure that CVSS scores are not misleading, you must incorporate Temporal and Environmental Metrics.
- Temporal Metrics adjust the score based on factors like the availability of patches or known exploits, reflecting the current state of the vulnerability.
- Environmental Metrics customize the score to your organization’s specific context, considering the unique aspects of your infrastructure, security controls, and business impact.
By accounting for these additional factors, you ensure that CVSS scores are tailored to your organization’s specific risks, enabling more informed decision-making and effective prioritization in your vulnerability management efforts.
Frequently Asked Questions
- What is the CVSS scoring range?
-
CVSS base scores range from 0 to 10, with 0 indicating no impact or exploitability and 10 representing the most severe vulnerabilities. This scoring scale helps prioritize vulnerabilities by assessing their exploitability and potential impact on the affected system, providing a standardized measure of their severity.
- What is a CVSS base score of 10?
-
A CVSS score of 10 indicates that a vulnerability is considered one of the most severe.
- What is the CIA triad?
-
The CIA Triad stands for Confidentiality, Integrity, and Availability. Confidentiality ensures that information is accessible only to authorized users. Integrity maintains the accuracy and completeness of data. Availability ensures that information and resources are accessible when needed. These three principles are fundamental for evaluating the impact of vulnerabilities and securing information systems.