What is a Cybersecurity Risk Assessment?
A Cyber Risk Assessment is a systematic process that identifies, analyzes, and evaluates potential cyber risks across an organization’s networks, devices, applications, and users. It provides crucial insights into your exposure to threats, enabling you to prioritize remediation efforts and strengthen your cybersecurity posture against potential attacks.
A cybersecurity risk assessment is vital for protecting digital assets against cyber threats. A well-executed cyber risk assessment enables you to identify, control, and mitigate various cyber risks while highlighting gaps in your cybersecurity program that need attention to enhance your overall security posture.
Why Perform a Cybersecurity Risk Assessment?
Today’s rapidly evolving attack surface—driven by new assets, applications, cloud services, microservices, and APIs—presents significant challenges for security teams. They must contend with various cyber risks, including software vulnerabilities, system misconfigurations, inadequate controls, outdated software, and emerging threats. This dynamic environment makes it difficult for organizations to understand their digital assets and associated risks fully.
Additionally, regulations from the SEC, DORA, NIS2 and other global bodies require CISOs to fully understand their material risks, disclose how they manage them, and demonstrate cybersecurity resilience and maturity.
CISOs must also present to the board to justify programs and validate costs while quickly addressing regulatory demands. Meanwhile, practitioners face the daunting task of prioritizing risks for effective remediation amidst largely manual processes, multiple tools, and limited budgets and resources.
The Role of Cyber Risk Assessments in Exposure Management
Exposure management aims to determine exposures and understand the broader context of these risks—how likely they will be exploited and their potential impact on your organization.
A Cyber Risk Assessment is essential in exposure management. It offers a systematic approach to identifying, evaluating, and mitigating potential exposures that could compromise an organization’s assets.
By focusing on understanding the broader context of these risks—such as their likelihood of being exploited and their potential impact—a cyber risk assessment provides a clear picture of the vulnerabilities within your assets, networks, and users. This process enables organizations to prioritize which exposures require immediate attention and allocate resources efficiently, ensuring a more robust defense against potential threats.
Learn more about exposure management.
Benefits of Performing a Cyber Risk Assessment
With vulnerabilities and exposures increasing at an unprecedented rate, conducting a cyber risk assessment is essential for any organization committed to staying secure. An assessment enhances your ability to proactively detect, contain, and recover from security incidents by providing clear visibility into your asset inventory, vulnerabilities, and overall attack surface.
Moreover, documenting the controls and processes you have in place allows for a more organized and effective response to potential threats. Calculating the likelihood and impact of various threats enables your organization to manage and respond to risks proactively.
Additionally, a cyber risk assessment can help you meet regulatory compliance standards, ensuring that your organization meets legal and industry requirements. A thorough assessment is a key component of a robust cybersecurity strategy, empowering your organization to mitigate risks and safeguard its digital assets.
How to Conduct a Cyber Risk Assessment in 5 Steps
Conducting a thorough cyber risk assessment is complex but vital for understanding and strengthening your organization’s cybersecurity posture. It’s a structured process that enables you to identify vulnerabilities, assess potential threats, and prioritize actions to mitigate risks. Below is a step-by-step guide to performing a practical cybersecurity risk assessment.
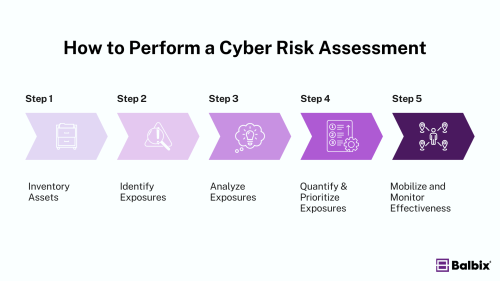
Step 1: Inventory Assets
The first step in any cyber resilience strategy is cataloging all assets within your organization’s network to get a big picture of your attack surface, including devices, users, applications, and data. Understanding the scope of your environment is crucial for identifying potential entry points for cyber threats.
Use an automated asset discovery tool to map out every connected device and resource. This tool should enable you to classify assets based on their criticality to your business operations. For instance, identify which assets are mission-critical and which are less essential. Assess how likely each asset is to be targeted and the potential impact a successful attack would have on your business.
Cyber Asset Attack Surface Management (CAASM) solutions can further enhance this process by providing continuous visibility and determining which assets are most vulnerable to exploitation. This automated approach ensures that your asset inventory remains current and accurate, a foundational step for the entire cyber risk assessment process.
Step 2: Identify and Prioritize Exposures and Vulnerabilities
The next step involves identifying and mapping all potential exposures across your network. Exposures can take various forms, including unpatched vulnerabilities, misconfigurations, or even unauthorized devices within your environment.
In this phase, leverage tools specializing in vulnerability management and exposure detection. These tools help you uncover weaknesses that cyber threats could exploit. Additionally, they enable you to map how these exposures relate to your critical assets, providing business context around each identified issue.
Step 3: Analyze and Assess Exposures
With exposures identified and mapped, the next step is to analyze and assess their potential impact on your organization. This analysis should consider both the likelihood of an exposure being exploited and the possible consequences for your business if a breach occurs.
Advanced exposure management tools can simulate various attack scenarios, providing insights into how threat actors might leverage different exposures. This analysis should incorporate real-time threat intelligence and historical data to view your exposure landscape comprehensively.
Assessing your exposures in this manner allows you to quantify the risk each one poses, enabling you to prioritize mitigation efforts based on both likelihood and impact.
Step 4: Quantify and Prioritize Cyber Risks and Exposures
In this step, you translate the findings from your analysis into quantifiable cyber risks. This involves calculating the likelihood of an attack and its potential impact, often in financial terms.
Quantifying cyber risks in dollars allows you to communicate effectively with stakeholders, such as the CFO or board members, who may not have a technical background.
Additionally, this approach helps make informed decisions about resource allocation, ensuring that investments in security controls align with the financial risks they mitigate. Quantifying risks effectively also enables the consolidation of tools and technologies.
Automated cyber risk quantification tools that leverage machine learning and AI can provide real-time updates to your risk calculations. As your environment changes—whether due to new vulnerabilities, emerging threats, or other factors—these tools ensure that your risk assessment remains current and accurate, enabling better decision-making.
Step 5: Mobilize and Monitor Effectiveness
The final step in your cyber resilience strategy is implementing security controls to mitigate identified exposures and establish a continuous monitoring process. Deploy security measures tailored to address the most critical exposures first. Continuous monitoring tools are essential for tracking the effectiveness of these controls, detecting new exposures as they arise, and adapting to changes in your environment.
Regularly revisiting and updating your exposure management strategy ensures your organization remains resilient against emerging threats. Continuous monitoring and proactive management of exposures are crucial to maintaining a robust cybersecurity posture.
Cyber Risk Assessment with Balbix
The Balbix Cyber Risk Assessment provides organizations with a comprehensive analysis of their cybersecurity posture and resilience strategy. This one-time assessment uses data from your current security and IT tools to create a detailed risk model for every digital asset.
It highlights key findings and provides metrics such as estimated financial impact, mean open vulnerability age (MOVA), and high-risk CVE instances. Delivered as a PDF report, it offers executives and security teams actionable insights. With quick onboarding and data ingestion, your team will receive clear, quantified results and recommendations for risk reduction within 7-10 days.
Frequently Asked Questions
- What are some of the questions answered with a cyber risk assessment?
-
A cyber risk assessment allows you to answer the following questions:
- What are my most critical assets?
- Which vulnerabilities pose the most risk to my internally- and externally-facing assets?
- What is the potential impact if those vulnerabilities are exploited?
- Do we have real-time visibility into our entire threat environment?
- What is the likelihood and impact of each identified threat?
- What is the measure of our cyber risk in quantifiable terms?
- Who should perform a cyber risk assessment?
-
Cyber risk assessments are critical to any robust cybersecurity resilience strategy and should be conducted continuously. As your organization’s attack surface grows, even the most comprehensive security controls cannot eliminate risk.
However, regular cyber risk assessments empower your security team with insights to reduce that risk proactively. By identifying vulnerabilities and exposures, these assessments enable your team to take informed actions that enhance your overall security posture, ensuring that your defenses evolve with emerging threats.
- What should you do before performing a cyber risk assessment?
-
Before conducting a cybersecurity risk assessment, setting clear objectives and scope is important. This involves identifying the systems, networks, and data to be evaluated and establishing specific goals, such as finding vulnerabilities or improving security.
It’s also crucial to identify potential weaknesses that cyber threats could exploit and to inform the assessment team in advance, ensuring it includes individuals from various departments. Lastly, it’s essential to understand how to quantify risk using the risk equation: Risk = Likelihood x Impact.
- How often should a cyber risk assessment be conducted to manage exposures effectively?
-
Because of the constantly changing threat landscape and expanding attack surface, Cyber risk assessments should be conducted continuously or at least quarterly to stay ahead of emerging threats and adapt to environmental changes. Regular assessments ensure that your organization remains proactive in identifying and mitigating risks.
- How can small to mid-sized businesses implement cyber risk assessments with limited resources?
-
Small to mid-sized businesses can start with automated tools like Balbix, prioritize critical assets, and focus on crucial vulnerabilities. Partnering with a managed security service provider (MSSP) can also help leverage expertise and resources efficiently.