Risk posture collectively refers to the status of an organization’s overall cybersecurity program and its approach to managing risk. Risk posture management encompasses identifying, evaluating, and mitigating potential threats to its infrastructure. It defines the organization’s strategy for addressing cybersecurity risks and vulnerabilities. A strong risk posture balances accepting certain levels of risk with implementing effective controls to mitigate them.
Organizations can make informed decisions that align with their strategic goals by understanding their risk posture. This requires regular assessment to evaluate current strategies’ effectiveness and identify areas for improvement. Organizations with a robust risk posture can confidently address potential threats while minimizing impacts on business operations.
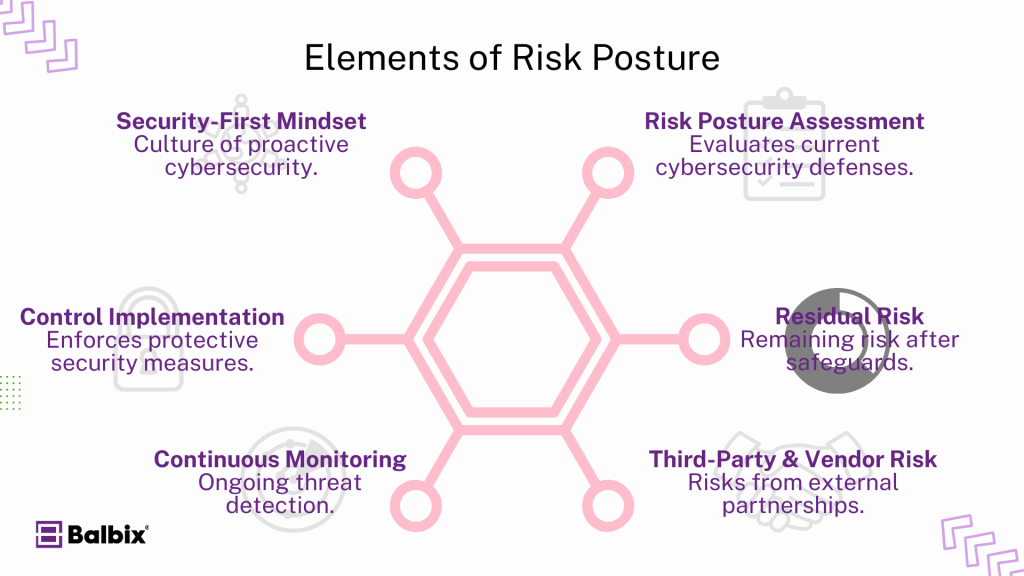
What is Residual Risk?
Residual risk is the level of risk that remains after an organization has applied all its risk mitigation measures. It’s important to recognize that some risks will always remain regardless of how strong your security policies are. Residual risk is the portion that isn’t entirely eliminated but is deemed acceptable based on the organization’s risk tolerance.
Understanding residual risk allows organizations to focus on enhancing their safeguards without the unrealistic expectation of zero risk. Instead, they strive to minimize this residual risk as much as possible. This involves continuously monitoring and assessing existing controls and adapting them to address evolving threats effectively.
What is Third-Party and Vendor Risk?
Organizations often depend on third-party vendors for critical systems like payment processing and servers. However, these partnerships can expand an organization’s attack surface, introducing additional risks. These third-party and vendor risks stem from potential vulnerabilities in the external partners’ systems or processes that could compromise your organization’s security.
Organizations should evaluate vendors’ security practices to mitigate risks and establish clear contractual agreements. This involves assessing vendors’ risk profiles to ensure alignment with your security standards. Effective third-party risk management requires regular assessments, audits, and open communication to address concerns promptly.
What is a Risk Posture Assessment?
A risk posture assessment is an evaluation process that helps organizations gauge their current risk levels and identify areas for improvement. This assessment involves analyzing various factors, such as the effectiveness of existing security measures, potential vulnerabilities, and the organization’s risk appetite. The goal is to understand how well the organization can handle potential cyber threats.
Regular risk posture assessments provide valuable insights into an organization’s security strengths and weaknesses. It enables organizations to prioritize their efforts, allocate resources strategically, and implement controls aligning with risk tolerance. A thorough risk posture assessment ultimately empowers organizations to make informed decisions and enhance their overall security posture.
Why is Risk Posture Important?
Understanding and managing risk posture is important for organizations that want to protect themselves from cybersecurity threats. A strong risk posture helps organizations allocate resources, prioritize security tasks, and maintain a competitive edge. By addressing potential risks early, organizations can reduce the chances of security breaches and their related costs.
A solid risk posture also builds confidence among stakeholders like customers, partners, and regulators. Showing a commitment to cybersecurity boosts an organization’s reputation and builds trust with its audience. Organizations that invest in developing a strong risk posture position help support a security-first culture.
How to Build a Strong Cyber Risk Posture
Building a strong cyber risk posture requires a strategic approach and a commitment to continuous improvement. Here are some practical steps organizations can take to strengthen their risk posture:
- Conduct Comprehensive Assessments: Regularly evaluate your organization’s risk posture to identify vulnerabilities and areas for improvement. Use these assessments to inform your risk management strategy and prioritize actions.
- Implement Robust Controls: Establish controls that align with your organization’s risk tolerance and address identified vulnerabilities. This includes implementing firewalls, encryption, access controls, and other security measures to protect your digital assets.
- Security-First Mindset: Encourage a culture of security awareness within your organization. Provide training and resources to employees, promoting responsible cybersecurity practices and ensuring everyone understands their role in maintaining security.
Conclusion
Understanding and managing your organization’s risk posture is key to protecting your digital assets and staying competitive in today’s cybersecurity landscape. Regular risk assessments, strong controls, and a security-first culture can help you build a solid cyber risk posture that reduces threats and keeps your residual risk in check.
To boost your organization’s risk posture even further, consider implementing an exposure management platform like Balbix, which uses AI to give you smart insights into your cyber risks, making it easier to stay ahead of potential threats. It’s all about equipping organizations with the visibility and insights to burn down cyber risk quickly.
Frequently Asked Questions
- What does posture mean in security?
-
In security, posture is the overall strength and readiness of an organization’s cybersecurity strategies, which details how well an organization is prepared to prevent, detect, and respond to security threats. This includes assessing technology, processes, and policies to protect data and systems and the organization’s awareness and responsiveness to emerging threats
- What is threat posture?
-
Threat posture refers to an organization’s current exposure level to cyber threats and ability to manage them effectively. It indicates how prepared the organization is to detect, respond to, and recover from potential attacks.
- What does posture assessment do?
-
A risk posture assessment evaluates an organization’s security measures, identifying strengths and vulnerabilities to determine overall readiness against cyber threats. It helps prioritize areas needing improvement to enhance the organization’s cybersecurity strategies and processes.