Cyberattacks often seem to arise out of nowhere, but in reality, they frequently exploit vulnerabilities lurking in the systems and processes we depend on. These weak spots can be as small as an outdated software patch or as broad as a lack of security awareness among employees. Yet, a single vulnerability can lead to breaches, financial losses, and reputational damage.
Understanding vulnerabilities isn’t just important; it’s foundational for reducing cyber risk in an interconnected, technology-driven world. This article dives into the essence of vulnerabilities, uncovers common examples, explains their impact, and highlights how smart vulnerability management practices can safeguard your business.
What Is a Vulnerability in Cybersecurity?
At its core, a vulnerability in cybersecurity refers to a weakness or flaw in technology, processes, or human behavior that leaves systems open to exploitation. Vulnerabilities are essentially “doors” that attackers attempt to unlock using various techniques.
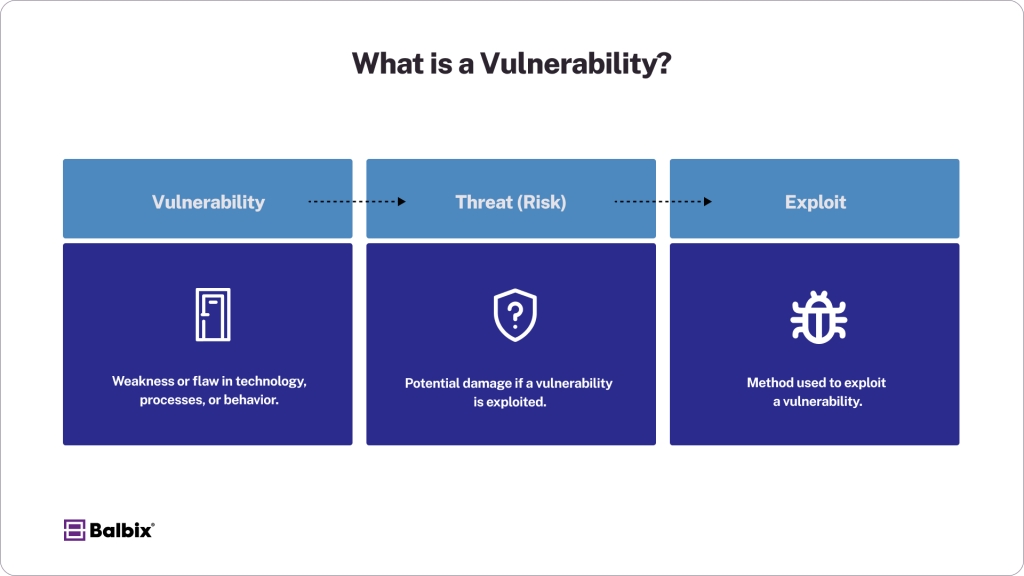
It’s crucial to distinguish between three related terms:
- Vulnerability: Vulnerabilities allow attackers to access a system, run code, install malware, and access internal systems to steal, destroy, or modify sensitive data. If undetected, attackers can pose as superusers or system administrators with full access privileges.
- Threat (Risk): Risk refers to the potential damage if a vulnerability is exploited. It combines both the likelihood and impact of the threat. Cyber risk is the expected loss from a cyberattack or data breach. Vulnerability is part of the likelihood in the risk equation.
- Exploit: An exploit is a method or technique cybercriminals use to exploit a security vulnerability in software or hardware. It allows attackers to gain unauthorized access, disrupt services, or steal data. Exploits are often used in cyberattacks to breach systems and cause harm.
Vulnerabilities can be technical, procedural, or behavioral in nature. Frameworks like the National Institute of Standards and Technology (NIST) and repositories such as the Common Vulnerabilities and Exposures (CVE) provide a structured way to identify, categorize, and address vulnerabilities. For example, CVE-2021-44228, or Log4Shell, shook the cybersecurity world by exposing a critical flaw in a widely used logging library.
Understanding vulnerabilities is essential for security professionals, IT staff, and software developers since proactive protection starts with recognizing the risks you face.
Examples of Vulnerabilities
Vulnerabilities span multiple categories, from hardware and software gaps to human errors. By breaking them into technical vulnerabilities and human-centric vulnerabilities, organizations can see the breadth of the attack surface they must protect.
Technical Vulnerabilities
- Unpatched Software or Outdated Systems: Failing to apply security updates leaves known vulnerabilities open to exploitation. For example, the infamous WannaCry ransomware attack in 2017 exploited unpatched Windows systems.
- Weak or Default Passwords: Cybercriminals easily crack predictable or reused passwords. Many breaches, like the 2021 Colonial Pipeline incident, resulted from poor password hygiene.
- Misconfigured Cloud Services: Incorrectly configured cloud storage or systems can expose sensitive data. For instance, a 2019 Capital One breach was traced back to a vulnerable AWS environment.
- Missing Encryption or Using Unsafe Protocols: Relying on HTTP instead of HTTPS or not encrypting sensitive data with a strong cipher can expose information in transit to eavesdroppers.
- Lack of Input Validation: When an input isn’t sanitized and validated, vulnerabilities like injection flaws or buffer overflows occur, allowing attackers to manipulate systems.
Human-Centric Vulnerabilities
- Social Engineering Susceptibility: Phishing attacks prey on human psychology. The 2016 DNC email breach remains an infamous example of a successful social engineering exploit.
- Poor Password Hygiene: Over-reliance on simple, repeated passwords creates openings for credential-stuffing attacks.
- Lack of Security Awareness Training: Employees are unaware of basic cybersecurity best practices, like spotting phishing emails, which increases organizational risk.
- Misuse of Access Rights: Granting unnecessary admin privileges or sharing user credentials can lead to privilege escalation and insider threats.
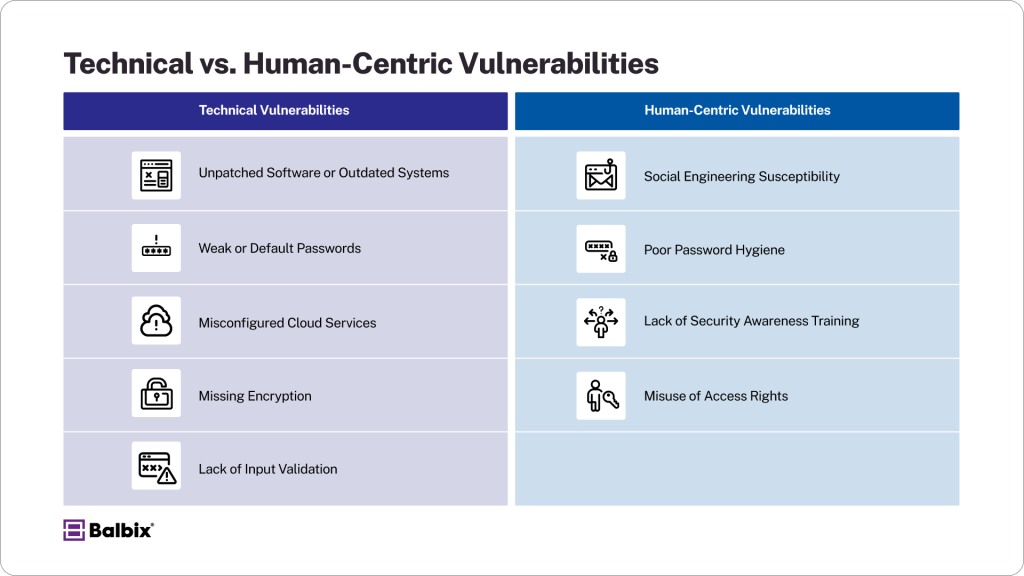
These examples show how vulnerabilities can arise from systemic flaws and human behavior. Proactively addressing these weak spots is critical to staying ahead of attackers.
Why Vulnerabilities Matter
Vulnerabilities are often the starting point for cyberattacks. They act as footholds that attackers exploit to access sensitive data, deploy ransomware, or disrupt operations.
Key Risks of Unaddressed Vulnerabilities
- Ransomware: Ransomware attacks are among the most disruptive cyber threats organizations face today. Vulnerabilities like unpatched or outdated software make attackers easy targets, allowing them to infiltrate systems and encrypt critical data.If ransom demands are met—or even worse, if data cannot be recovered —these attacks can paralyze operations, halt productivity, and lead to significant financial losses. Regular software updates and backups are essential to mitigating this risk.
- Data Breaches: Data breaches occur when sensitive information is exposed due to weaknesses like poor authentication protocols, insecure configurations, or unpatched vulnerabilities.One infamous example is the Equifax breach in 2017, where an unpatched software vulnerability allowed attackers to access the personal data of over 147 million individuals, including Social Security numbers, birth dates, and other sensitive information. Such breaches harm the affected individuals, damage the organization’s reputation, and result in legal and financial repercussions.
- Lateral Movement and System-Wide Impact: Exploiting a single vulnerability often serves as the first step for attackers. Once inside, they can use lateral movement techniques to navigate interconnected networks and systems, escalating privileges. This allows attackers to compromise multiple systems, amplifying the damage across the organization.Such breaches can lead to widespread operational disruption, intellectual property theft, or exposure of critical business data, making it crucial to monitor for unusual activity and secure system interconnectivity.
Financial Costs and Damage to Reputation
The financial toll of unresolved vulnerabilities is staggering. According to IBM, data breach costs reached an average of $4.45 million in 2023. Furthermore, compliance violations (like failing to meet GDPR or CCPA standards) can result in hefty fines.
With the increased interconnectivity of digital systems and hybrid environments, vulnerabilities can act as breaking points that ripple across entire industries.
The Role of Vulnerability Management
Vulnerability management is an essential process that involves identifying, assessing, prioritizing, and fixing vulnerabilities. A strong vulnerability management program does more than just patch holes; it strategically reduces risk.
The Vulnerability Management Process
Step 1: Identification
The first step in addressing vulnerabilities is identifying them. Tools like vulnerability scanners (e.g., Nessus, Qualys) or endpoint detection systems play a crucial role in this process. These tools systematically scan networks, devices, and applications to detect weaknesses, misconfigurations, or outdated software that could be exploited. Regular scanning ensures that new vulnerabilities are caught promptly, reducing the exposure window.
Step 2: Assessment
Once vulnerabilities are identified, they must be assessed for their potential impact. Not all vulnerabilities pose the same level of risk, so frameworks like the Common Vulnerability Scoring System (CVSS) are essential.
CVSS assigns a numerical score to vulnerabilities based on factors such as exploitability, complexity, and potential system damage. This scoring helps teams determine which vulnerabilities require immediate attention and which can be addressed later. Additionally, assessing the criticality of affected assets further refines the prioritization process.
Step 3: Prioritization
With a clear understanding of the risks, vulnerabilities must be prioritized to ensure the most critical issues are addressed first.
Vulnerabilities impacting essential systems, sensitive data, or services with high business importance demand faster action. AI-powered platforms like Balbix enhance this process by providing context-driven insights, factoring in real-time exploitability, determining the business impact of affected systems, and even determining the likelihood of a vulnerability being targeted. This intelligent prioritization ensures resources are allocated where they are needed most.
Step 4: Remediation
Once priorities are set, the focus shifts to remediation, which involves taking concrete actions to eliminate or mitigate vulnerabilities. This could include applying security patches to software, reconfiguring system settings to close security gaps, or removing outdated and unsupported components.
Human vulnerabilities, such as susceptibility to phishing or weak password practices, are addressed through targeted training and awareness programs. A comprehensive remediation strategy resolves current vulnerabilities and strengthens the security posture to prevent future issues.
To learn more about vulnerability management, read our complete vulnerability management guide.
Exposure Management
Modern exposure management tools leverage AI to bridge the gap between traditional vulnerability scanning and proactive risk mitigation. Exposure management ensures enterprises don’t spread themselves too thin by focusing resources on vulnerabilities most likely to be exploited.
Get a detailed walkthrough on exposure management in our comprehensive guide.
Who’s Responsible?
Effective vulnerability management requires collaboration across multiple teams:
- Security Teams focus on identifying and addressing technical weaknesses.
- IT Teams implement fixes such as software patches or infrastructure updates.
- DevOps Teams create more secure code by integrating security into the software development lifecycle (DevSecOps).
A shared understanding of risks and responsibilities is essential to manage vulnerabilities collectively.
Securing The Future by Managing Vulnerabilities
Vulnerabilities may be inevitable, but they don’t have to result in breaches. Understanding where weak spots exist and embedding a strong vulnerability management process into your cybersecurity strategy can significantly reduce risk and cost.
Stay proactive. Leverage AI-powered tools like Balbix to inform smarter decisions, prioritize effectively, and protect your most critical assets.
Frequently Asked Questions
- What’s the difference between a vulnerability, a threat, and an exploit?
-
-
A vulnerability is a weakness in your system.
-
A threat is the potential harm if that weakness is targeted.
-
An exploit is the actual method attackers use to take advantage of the vulnerability.
Understanding these distinctions helps organizations better assess and manage cyber risk.
-
- Why is vulnerability management important in cybersecurity?
-
Vulnerability management is crucial because it helps organizations proactively identify and fix weaknesses before attackers can exploit them. A well-run program reduces the risk of breaches, ransomware attacks, and compliance violations while protecting sensitive data and critical systems.
- What is the difference between a threat and a vulnerability?
-
A threat is a potential danger that could exploit a vulnerability to cause harm, such as cyberattacks. A vulnerability is a weakness in a system that a threat, such as outdated software or poor security practices, can exploit.
- Is phishing a threat or vulnerability?
-
Phishing is a threat. It is a malicious tactic used by attackers to deceive individuals into revealing sensitive information or installing malware. It exploits existing vulnerabilities in human behavior and security practices.
- Is malware a threat or vulnerability?
-
Malware is a threat. It is malicious software designed to damage or gain unauthorized access to systems. It exploits vulnerabilities to achieve its goals, such as stealing data or disrupting operations.
- What is the difference between a bug and a vulnerability?
-
A bug is an unintended error or flaw in software that causes it to function incorrectly. A vulnerability is a specific type of bug that poses a security risk, allowing attackers to exploit it to compromise the system’s integrity or confidentiality.
- How do hackers exploit vulnerabilities?
-
Hackers exploit vulnerabilities by using tools or techniques called exploits. These are designed to take advantage of software, hardware, or human behavior flaws, allowing attackers to gain unauthorized access, deploy malware, steal data, or disrupt systems.
- Who is responsible for managing vulnerabilities in an organization?
-
Managing vulnerabilities is a shared responsibility. Security teams identify and assess weaknesses, IT teams apply patches and updates, and DevOps teams build secure code. A collaborative approach across departments is essential for effective risk reduction.