Exposure management in cybersecurity is the process of identifying, assessing, and mitigating potential vulnerabilities and threats to minimize the risk of cyberattacks on an organization’s assets. Unlike traditional vulnerability management, which focuses solely on software flaws (CVEs), exposure management consolidates various exposures—such as misconfigurations, end-of-life (EOL) systems, weak credentials, and control gaps—to reduce overall risk to the business.
This guide explores why exposure management is essential for modern cybersecurity, how it works, and the tangible benefits it offers.
What is Exposure Management?
Exposure management is a holistic approach to understanding and reducing risk across an organization’s entire attack surface. It expands beyond traditional vulnerability management by addressing all potential exposures that could compromise security. These exposures include common vulnerabilities and exposures (CVEs) and non-CVE issues such as misconfigurations, EOL systems, application security findings, weak credentials, and control gaps.
By consolidating and prioritizing findings from various security tools, exposure management ensures that mitigation efforts focus on the areas that pose the greatest risk to the organization. This approach helps organizations allocate resources efficiently and reduce the likelihood of cyberattacks.
Exposure Management vs. Vulnerability Management
While often used interchangeably, exposure management and vulnerability management serve different purposes in cybersecurity.
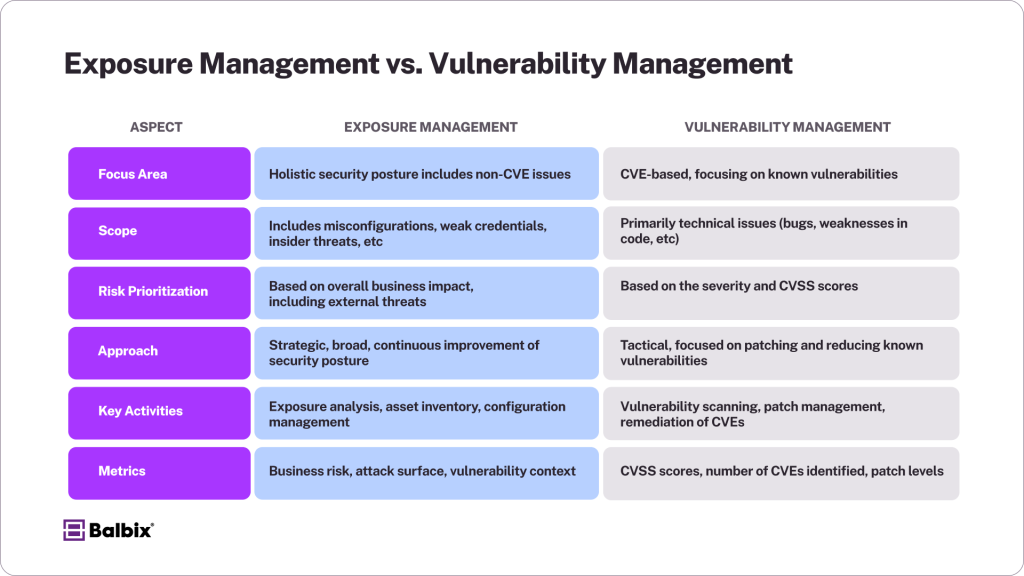
Vulnerability management focuses on identifying and patching software flaws, prioritizing based on severity metrics like CVSS scores. This approach primarily concerns remediating individual vulnerabilities quickly, often without considering broader risk factors or the organization’s overall security posture.
Exposure management takes a more comprehensive, risk-based approach. It evaluates all potential exposures—including software vulnerabilities, misconfigurations, outdated systems, weak security controls, and user-related risks—through the lens of business impact. Instead of focusing solely on severity, exposure management consolidates data from multiple tools to prioritize the exposures that pose the greatest threat to the organization.
This broader perspective allows exposure management to allocate resources more effectively, address critical risks first, and mitigate threats even when full remediation isn’t feasible. It’s a proactive approach to reducing risk across the entire attack surface.
What is CTEM, and Where Did It Originate?
Cybersecurity Threat Exposure Management (CTEM) is a framework introduced by Gartner in 2022 to help organizations take a structured and ongoing way of managing their attack surface. Instead of just focusing on individual vulnerabilities, CTEM looks at the bigger picture, helping organizations stay on top of potential risks.
The framework breaks down exposure management into five practical steps: scoping, discovery, prioritization, validation, and mobilization. These steps guide organizations through finding their assets, understanding potential risks, and taking action to fix the most pressing issues. By following these steps, organizations can strengthen their defenses and stay prepared for new threats while aligning their efforts with their specific needs.
CTEM came about because traditional methods of managing vulnerabilities often struggle to keep up with constantly evolving cybersecurity threats. Attack surfaces are constantly growing and shifting, and it’s hard to manage everything with more traditional systems. CTEM focuses on managing exposures instead of on a case-by-case basis with individual issues.
Core Principles of Exposure Management
To understand exposure management, you need to grasp its core principles. These principles guide organizations in effectively identifying, prioritizing, validating, and addressing exposures to reduce cyber risk.
Comprehensive Identification
The first principle of exposure management is the comprehensive identification of all assets and exposures. Organizations must assess internal and external assets, including endpoints, servers, cloud environments, internal and SaaS applications, and user accounts. Security teams can create a complete map of the organization’s attack surface by conducting a thorough inventory.
Once assets and exposures are identified, the data must be normalized and deduplicated to represent the attack surface accurately. This step eliminates redundancies and ensures that security teams clearly understand their environment.
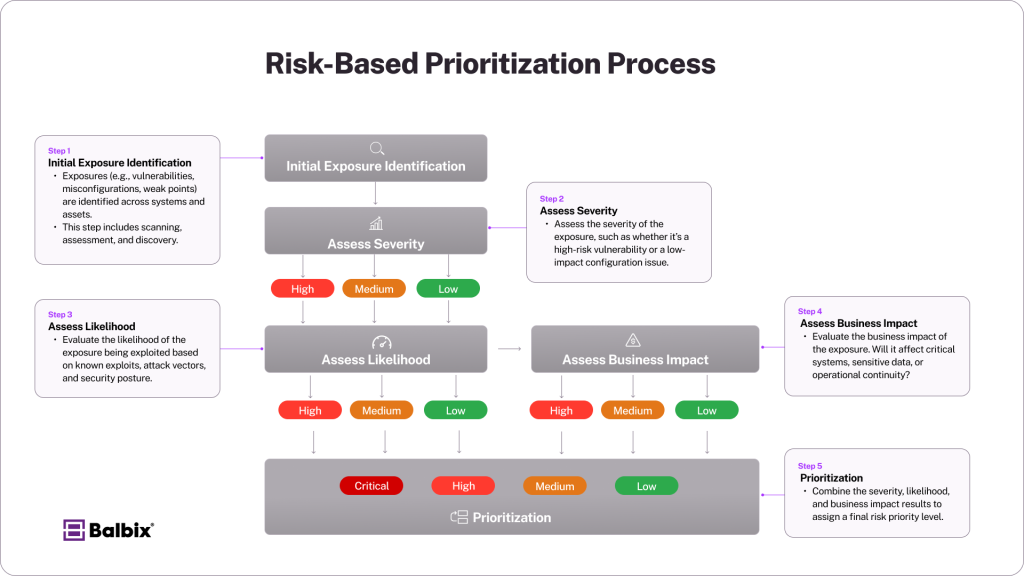
Risk-Based Prioritization
Risk-based prioritization is a cornerstone of exposure management. Instead of addressing every issue indiscriminately, organizations evaluate exposures based on several key factors. These factors include the severity of the issue, the likelihood of exploitation, and the potential business impact.
Severity is assessed based on the impact on confidentiality, integrity, and availability. Threat levels are evaluated by considering known exploits, the availability of exploit kits, and the potential consequences for the organization. Exploitability focuses on how easily attackers can exploit the exposure. Additionally, the effectiveness of existing security controls and the financial implications of a successful attack, such as fines or reputational damage, are considered.
Validation and Simulation
Validation and simulation are essential for distinguishing real threats from theoretical ones. Organizations can use methods like breach and attack simulations, penetration testing, and mapping to frameworks such as MITRE ATT&CK. These techniques allow security teams to understand how exposures could be exploited in real-world scenarios.
For example, Balbix maps exposures to tactics, techniques, and procedures (TTPs) and evaluates the effectiveness of existing security controls. This process provides actionable insights into which exposures require immediate attention.
Effective Mobilization
Effective mobilization ensures that identified risks are addressed promptly. Organizations must route remediation tasks to the appropriate teams with the necessary context and urgency. This process involves clear communication and tools like analytics dashboards to track progress and identify bottlenecks.
The Exposure Management Lifecycle
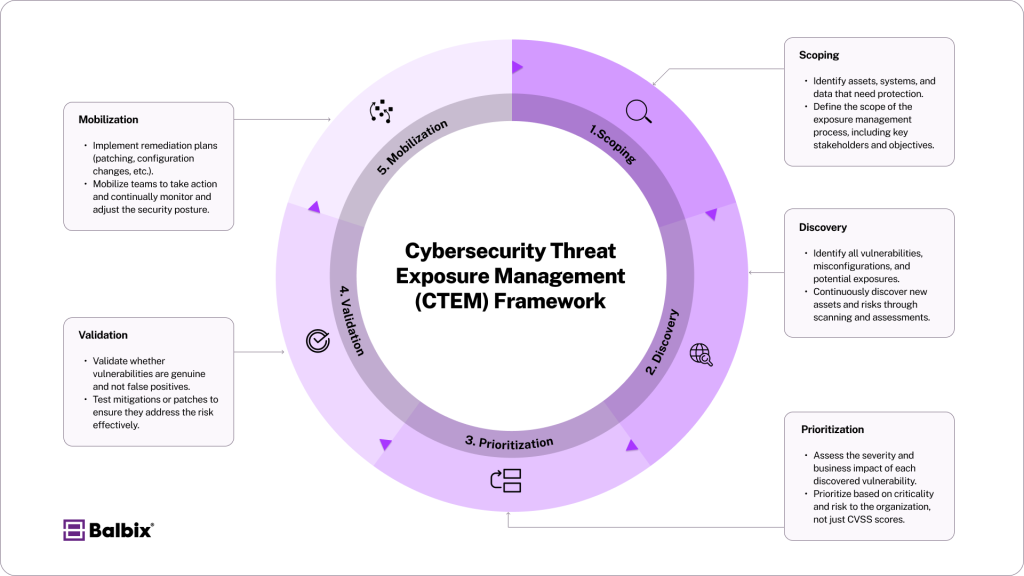
Step 1 – Scoping
In Cybersecurity Threat Exposure Management (CTEM), scoping starts by defining the boundaries of the organization’s attack surface. This includes identifying internal and external assets like endpoints, servers, cloud resources, SaaS applications, and user accounts.
Tools such as Attack Surface Management (ASM), External Attack Surface Management (EASM), Cyber Asset Attack Surface Management (CAASM), and Digital Risk Protection (DRP) are employed to map out these assets comprehensively, ensuring all potential exposures are accounted for.
- Attack Surface Management (ASM): Identifies and manages vulnerabilities across an organization’s digital footprint, supporting comprehensive exposure management.
- External Attack Surface Management (EASM): Focuses on external-facing assets, providing visibility into risks from outside the network and ensuring all external exposures are accounted for.
- Cyber Asset Attack Surface Management (CAASM): Extends exposure management to include all cyber assets, such as devices and systems, ensuring a broad view of potential vulnerabilities.
- Digital Risk Protection (DRP): This proactive approach mitigates risks from external threats like digital fraud and data breaches, safeguarding against external exposures.
Step 2 – Discovery
The Discovery phase is a critical step in exposure management, focusing on identifying vulnerabilities, misconfigurations, and other potential exposures across an organization’s attack surface. During this phase, multiple assessment tools are integrated to scan for a wide range of risks, including:
- Common Vulnerabilities and Exposures (CVEs): These are publicly disclosed security flaws in software or hardware that attackers can exploit. Discovery tools search for known CVEs that could put systems at risk.
- Misconfigurations: Many security breaches stem from improperly configured systems or applications. The discovery phase checks configurations across systems, networks, and cloud environments to ensure they align with security best practices.
- End-of-Life (EOL) Systems: Legacy systems no longer supported by vendors pose significant risks, as they no longer receive security updates. Discovery tools identify these outdated systems within the organization’s network, allowing for timely remediation or replacement.
CTEM frameworks emphasize automating this process to provide a continuous and up-to-date view of the organization’s security posture.
Step 3 – Prioritization
Using CTEM (Continuous Threat Exposure Management) principles, prioritization evaluates exposures based on several factors rather than just severity. Key techniques include:
- Likelihood of Exploitation: Considers how likely an exposure is to be exploited, influenced by factors like publicly known vulnerabilities, exploitability, and threat intelligence on emerging risks.
- Business Impact: Assesses the potential damage to the organization, considering data sensitivity, operational disruption, and reputational harm.
- Effectiveness of Existing Controls: Evaluate the effectiveness of current security measures, such as firewalls, MFA, and patch management, in mitigating the exposure.
By combining these factors, organizations can assign risk scores to exposures and prioritize efforts accordingly. Frameworks like MITRE ATT&CK refine this process by mapping exposures to real-world attack techniques, helping teams focus on the most relevant threats.
Step 4 – Validation
Validation in the CTEM (Continuous Threat Exposure Management) lifecycle tests exposures under simulated attack conditions to determine their true risk. Key validation techniques include:
- Penetration Testing (Pentesting): Ethical hackers simulate real-world attacks to exploit vulnerabilities and assess how easily an attacker could breach systems.
- Threat Modeling: This structured process identifies potential attack vectors and evaluates the risks by mapping out system components and simulating how an attacker might exploit them.
- Red Teaming: Red teams simulate full-scale, multi-faceted attacks, including social engineering and cyberattacks, to test an organization’s security posture, detection, and response capabilities.
- Breach & Attack Simulations (BAS): These controlled simulations mimic attack scenarios to gauge efficacy and evaluate how quickly security teams can detect and respond to incidents.
These techniques help verify whether identified vulnerabilities are practically exploitable and ensure that resources are directed toward mitigating real threats, not theoretical ones.
Step 5 – Mobilization
This final mobilization phase turns findings into actionable tasks by integrating CTEM frameworks with automated workflows and collaborative processes.
- Task Routing: Tasks are automatically assigned to the appropriate teams, with clear context, priority, and urgency, ensuring quick action.
- Analytics Dashboards: Real-time dashboards track remediation progress, providing visibility into key performance indicators (KPIs) such as response times and resolution rates. They also provide trend graphs to allow teams to measure progress over time.
- Tracking Tools: These tools help identify bottlenecks, ensuring that critical risks are addressed promptly and resources are efficiently allocated to mitigate the highest-priority exposures.
Key Benefits of Exposure Management
Enhanced Visibility
Exposure management integrates data from multiple tools, providing a unified view of the organization’s attack surface. This eliminates blind spots and ensures that security teams comprehensively understand their environment.
Proactive Risk Reduction
By prioritizing risks based on real-world threat levels and business impact, exposure management enables organizations to address critical vulnerabilities before they can be exploited. This proactive approach reduces the likelihood of successful attacks and minimizes potential damage.
Reduced IT Workload
Traditional vulnerability management methods often create excessive workloads for IT teams by requiring them to address every identified issue. Exposure management streamlines remediation efforts by focusing only on the most significant risks. This reduces manual efforts and accelerates patch cycles.
Improved Executive Reporting
Exposure management translates technical risks into business impacts, such as financial and reputational costs. This makes it easier for security teams to communicate cybersecurity issues to non-technical stakeholders and gain executive support for remediation efforts.
Regulatory Compliance
Structured processes within exposure management help organizations align with industry standards and regulatory requirements. This ensures compliance with frameworks and reduces the risk of penalties or fines.
Challenges in Exposure Management
Effectively managing exposure comes with several challenges that can impact the efficiency of a cybersecurity program. These obstacles must be addressed to ensure a comprehensive, well-prioritized approach to mitigating risks. Key challenges include:
- Complex Environments: Hybrid IT infrastructures, which combine on-premise systems with cloud resources, make it difficult to get a full view of the attack surface, leading to blind spots and overlooked vulnerabilities.
- AppSec: Adding application and software vulnerabilities and misconfigurations exacerbates the problem by adding another layer of knowledge and tooling to the mix. Apps don’t follow the same cycles as infrastructure assets, and security processes must align with the company’s Software Development Life Cycle (SDLC) to minimize friction.
- Data Overload: Managing vast amounts of data from security tools requires advanced analytics and prioritization to avoid overwhelming teams and delaying critical responses.
- Security vs. Business Continuity: Remediation efforts need to balance security with the need to maintain business operations, ensuring that critical services aren’t disrupted.
- Cross-Team Collaboration: Alignment and communication between IT, security, and executive teams is crucial for successful exposure management and preventing stalled initiatives.
- Coordinated Approach: Overcoming these challenges requires a strategy integrating advanced technology, streamlined processes, and cross-functional collaboration.
Best Practices for Successful Exposure Management
- Conduct Regular Audits and Updates: Make exposure management a continuous process. Regularly review and update your security posture to include new assets, vulnerabilities, and evolving threats. Frequent audits help quickly identify and address potential blind spots.
- Implement Comprehensive Monitoring: Set up monitoring across all areas of your attack surface, including endpoints, cloud environments, internal and SaaS applications, and user accounts. Advanced tools can detect anomalies and exposures in real-time, enabling faster responses.
- Leverage Automation: Use automated tools for exposure assessment, prioritization, and remediation. Automation speeds up risk identification, reduces manual work, and ensures consistent organizational vulnerability management.
- Foster Cross-Functional Collaboration: Encourage collaboration between security, IT, and leadership teams. Aligning these groups ensures a unified approach to risk management and improves decision-making and resource allocation.
- Use Threat Modeling Frameworks: Implement frameworks like MITRE ATT&CK to map exposures to real-world attack techniques. This helps prioritize critical threats and aligns security efforts with potential attack methods.
- Simulate Attacker Behavior: Conduct breach simulations, penetration tests, and red teaming exercises. These tests help identify exploitable exposures and allow teams to focus on the highest-risk threats.
- Prioritize Based on Risk: Assess risks based on business impact, exploitability, and the effectiveness of existing controls—not just severity. This approach helps ensure resources are focused where they can reduce the greatest organizational risk.
- Streamline Workflows: Use analytics dashboards and automated workflows to assign remediation tasks with clear context and urgency. This reduces bottlenecks and enhances remediation efficiency. Ensure the workflows align with the business requirements of the various environments.
- Train and Empower Teams: Provide ongoing training to IT and security teams to ensure they’re equipped to manage exposures. Empowered teams are more adaptable to changing threats and technologies.
- Validate and Update Regularly: Continuously test and update your exposure management processes. Regular validation keeps strategies effective, even as new threats and changes arise.
The Future of Exposure Management
Traditional methods must evolve as organizations adopt IoT, OT, and hybrid infrastructures. The future of exposure management will leverage AI and machine learning to accelerate detection, prioritize threats more effectively, and predict risks before they occur.
Balbix is already leading this shift with AI-powered solutions that continuously assess risks across all assets and integrate real-time threat data. This enables organizations to take clear, actionable steps to reduce cyber risks. Additionally, Balbix translates cyber risks into financial terms, helping decision-makers align security efforts with business goals and plan for the future.
Key trends shaping exposure management include increased automation, stronger risk calculation integration, and strategies that address threats before they escalate. As attack surfaces expand and threats evolve, staying ahead requires adopting advanced tools that simplify and enhance risk management.
Conclusion
Exposure management is a proactive, comprehensive approach to cybersecurity that addresses gaps left by traditional vulnerability management. By focusing on all exposures—CVE and non-CVE—organizations can strengthen their cyber resilience with risk-based prioritization, validation, and mobilization.
Request a demo today to see how Balbix can enhance your exposure management strategy.
Frequently Asked Questions
- What is exposure management in cybersecurity?
-
Exposure management is a comprehensive process of identifying, assessing, and mitigating all potential security exposures within an organization, beyond just software vulnerabilities, to reduce the risk of cyberattacks.
- How does exposure management differ from vulnerability management?
-
Unlike vulnerability management, which focuses mainly on software flaws (CVEs), exposure management addresses a broader range of risks, including misconfigurations, outdated systems, weak credentials, and more, prioritizing them based on business impact.
- What is CTEM, and why is it important for exposure management?
-
CTEM (Cybersecurity Threat Exposure Management) is a structured framework that helps organizations manage their attack surface more effectively. It focuses on continuously identifying and mitigating risks, offering a proactive approach to cybersecurity.
- What are the core principles of exposure management?
-
The core principles include comprehensive identification of assets and exposures, risk-based prioritization, validation through testing, and effective resource mobilization to promptly address critical risks.
- Why are AI and machine learning important for exposure management?
-
AI and machine learning enhance exposure management by automating risk detection, predicting potential threats, and prioritizing exposures based on real-time data, making it faster and more efficient in an increasingly complex threat landscape.