A security misconfiguration occurs when system or application settings are incorrectly configured or essential configurations are missing. This leaves the system exposed to threats, allowing unauthorized access or exploitation. Misconfigurations can expose your organization to significant risk, whether it’s an application, cloud infrastructure, or network setup.
Security misconfigurations are particularly widespread in cloud environments and are often cited as the top vulnerability in the cloud. With cloud platforms and services multiplying, it’s essential to understand the risks misconfigurations pose and how they can be prevented.
Examples of Security Misconfigurations
Security misconfigurations come in many forms, and recognizing them can help you safeguard your systems. Here are eight common examples of security misconfigurations:
- Unpatched Systems: Failing to apply the latest security patches leaves your system vulnerable to known exploits, making it easier for attackers to infiltrate.
- Default Account Settings: Keeping default usernames and passwords unchanged gives hackers an easy entry point. These credentials are often widely known or easily guessed.
- Unencrypted Files: Storing sensitive data without encryption exposes it to unauthorized users, leading to potential data breaches or leaks.
- Inadequate Access Controls: Granting excessive permissions to users who don’t need them increases the risk of internal threats or accidental data exposure.
- Unprotected Files and Directories: Publicly accessible files or directories can expose sensitive information, enabling attackers to exploit directory traversal vulnerabilities.
- Web Application Misconfigurations: Insecure configurations in web applications, such as improper authentication or exposing sensitive directories, can make them vulnerable to attacks like SQL injection or cross-site scripting.
- Cloud Misconfiguration: Misconfiguring cloud resources, such as leaving Amazon AWS S3 buckets open to the public, can result in unauthorized access to sensitive information.
6 Types of Security Misconfigurations
Misconfigurations can take many forms, depending on the type of system or application. Here are six common types of security misconfigurations:
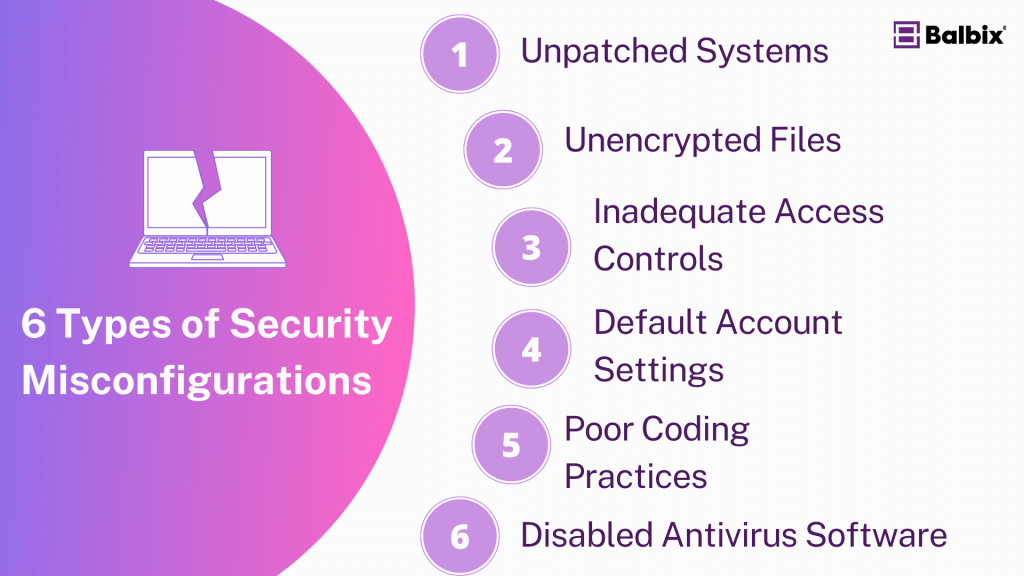
1. Unpatched Systems
When systems or software aren’t regularly updated with the latest security patches, they become easy targets for attackers. Known vulnerabilities are like open doors waiting to be exploited. Keeping your systems patched is one of the simplest ways to close those doors and stay protected.
2. Unencrypted Files
Sensitive information, like personal or financial data, should always be encrypted. If your files aren’t encrypted, anyone who gains access can easily read them. Encryption acts as a layer of protection, ensuring that even if data is accessed, it remains secure and unreadable without the right decryption keys.
3. Inadequate Access Controls
If your access controls are too lenient, you may unintentionally allow unauthorized users to see, modify, or delete important information. It’s essential to follow the principle of least privilege, which means giving people access only to what they need to do their jobs—nothing more, nothing less.
4. Default Account Settings
Keeping default usernames and passwords the same is a common security misstep. Attackers often try these first because they’re easy to guess, like “admin/admin.” Changing these settings immediately is a simple but crucial step in securing your system and keeping attackers out.
5. Poor Coding Practices
Developers must follow secure coding practices to prevent vulnerabilities like SQL injection or buffer overflows. Simple mistakes, like not validating user inputs or failing to sanitize data, can lead to major security risks. Adopting secure coding standards helps prevent these issues from creeping in.
6. Disabled Antivirus Software
Antivirus software is often disabled to improve system performance or avoid false positives, but doing so can leave your systems exposed to malware, viruses, and ransomware. Keeping your antivirus enabled and updated provides an important line of defense against these threats.
How a Misconfiguration Creates Vulnerabilities
Security misconfigurations often lead to serious vulnerabilities that attackers can exploit. Here’s how they can create entry points for malicious activities:
- Sensitive Data Exposure: Unencrypted or open directories can expose personal information, intellectual property, or financial records. Attackers can easily access this data if the proper security measures aren’t in place.
- Directory Traversal Attacks: Misconfigured files and directories can allow attackers to move freely within a system, accessing confidential areas and escalating privileges to gain deeper control over the system.
- Broken Authentication: Improper configuration of authentication mechanisms can allow unauthorized users to bypass login processes and gain administrative access.
These vulnerabilities make it easier for hackers to launch sophisticated attacks, ranging from data breaches to ransomware infections, putting your entire organization at risk.
How to Prevent Misconfiguration Vulnerabilities
Preventing security misconfigurations requires a proactive approach, an essential step toward maintaining a strong security posture. By following these best practices, you can significantly lower the risk of exposure and keep your systems safe from misconfigurations.
Regular Patch Management
Keeping your systems and applications updated with the latest patches is one of the most straightforward ways to prevent misconfigurations. Regular patching helps to close known vulnerabilities, reducing the chance of an attacker exploiting outdated software. Automated solutions, like Balbix, can streamline this process, ensuring you’re always protected against the latest threats.
Implement Strong Access Controls
Always follow the principle of least privilege when setting access controls. This means granting users access only to the systems and data they need to perform their role. Limiting permissions helps reduce the risk of internal threats and prevents compromised accounts from doing significant damage.
Secure Coding Practices
Training developers on secure coding practices is crucial for preventing application misconfigurations. Practices like validating inputs, encoding outputs, and handling errors properly can stop many vulnerabilities before they occur. Developers should integrate security into the development process from the very start to avoid mistakes that can lead to security breaches.
Conduct Regular Audits
Regular security audits and vulnerability scans are essential for catching misconfigurations before they can be exploited. These audits help identify weaknesses in your system, allowing you to fix them before they become problems. Tools like Balbix’s exposure management platform can help automate and streamline this process, ensuring continuous visibility into your security posture.
Enable Alerts and Monitoring
Set up alerts and monitoring systems to notify your team of any unusual activity or configuration changes. These tools can detect misconfigurations as soon as they happen, allowing quick response times. With Balbix’s real-time monitoring capabilities, you can receive alerts and recommendations, helping you fix issues before they escalate into bigger security concerns.
Training and Awareness
Regular employee training sessions can make a big difference in preventing misconfigurations. Ensuring that everyone understands the importance of secure configurations and follows best practices can reduce the risk of human error. From IT staff to everyday users, education is key to keeping your systems safe and secure.
Security misconfigurations may seem like minor oversights, but they can lead to major security incidents if left unchecked. These vulnerabilities, from unpatched systems to open cloud storage, give attackers easy access to sensitive information and critical systems. When you understand security misconfiguration, recognize common types, and follow best practices for prevention, you can help protect your organization from potential threats.
Whether managing a complex cloud infrastructure or a simple internal system, proper configuration is always a priority to keep your data and assets secure.
Frequently Asked Questions
- How does a Security Misconfiguration occur?
-
It can occur for various reasons, such as default configurations not being secured or updated, unnecessary services being enabled, or incorrect permissions being set.
- Why is it important to avoid Security Misconfigurations?
-
Avoiding Security Misconfigurations is crucial because they can expose sensitive information, allow unauthorized access, and potentially lead to data breaches or system compromises.
- Can Security Misconfigurations affect all types of systems?
-
Security Misconfigurations can affect any system, including web applications, databases, and network devices if they are not properly configured and maintained.