Organizations rely heavily on software to manage operations and protect sensitive data, understanding zero-day exploits is key to staying safe, reducing their risk and impact on an organization.
Let’s break down what zero-day exploits are, why they’re dangerous, how they work, and practical ways to protect your organization.
What is a zero-day?
A zero-day refers to a newly discovered vulnerability in software, firmware, or hardware that the vendor or developers are unaware of. With no fix or patch available, attackers can exploit it immediately, posing a serious security threat. A zero-day exploit is one of the most dangerous methods of cyber attack. It targets an unpatched vulnerability, leaving systems highly susceptible to exploitation.
Cybercriminals capitalize on these vulnerabilities through zero-day attacks, launching strikes before the issue is identified or resolved. This leaves organizations vulnerable to data breaches, system compromises, and theft, often with no time to respond or mitigate the damage.
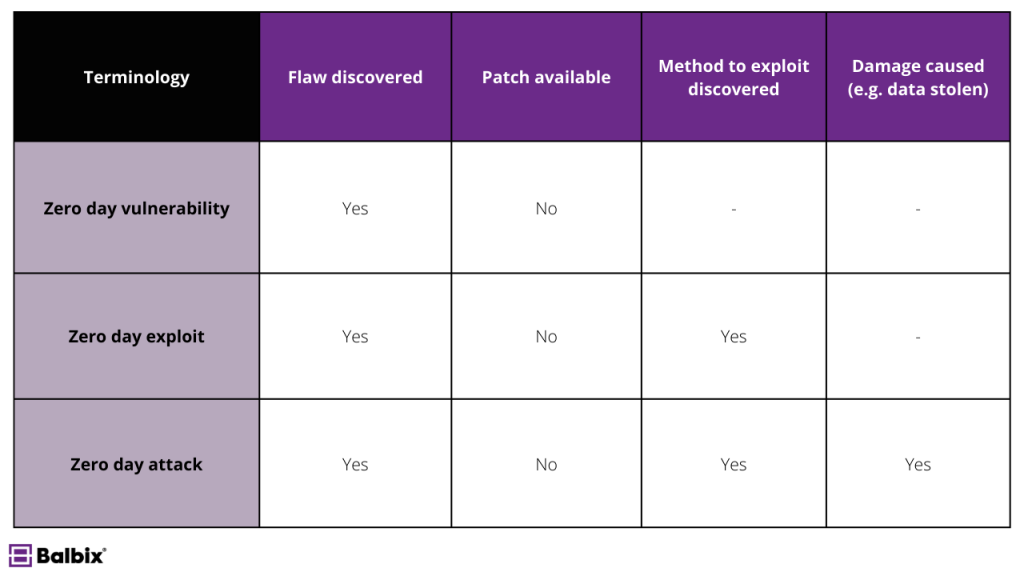
Defining a Zero-Day Vulnerability, Exploit, and Attack
Zero-day threats can be complex, especially with the variety of terms used to describe the different stages of an attack. To help clarify, here’s a detailed breakdown:
- Zero-Day Vulnerability: This refers to a security flaw in software or systems unknown to the vendor or developer. Because the vendor is unaware of the issue, no patch or fix has been created to address it, leaving the vulnerability open to exploitation. These flaws can exist in operating systems, applications, or even firmware, and often remain hidden until actively exploited or discovered by security researchers.
- Zero-Day Exploit: Once attackers identify a zero-day vulnerability, they develop a method or technique, known as an exploit, to exploit it. These exploits can be malicious code, phishing emails, or other tactics to bypass security measures and gain unauthorized system access.
- Zero-Day Attack: This is when cybercriminals use a zero-day exploit to compromise a system, steal sensitive data, disrupt services, or install malware. These attacks often occur in secret, targeting individuals, organizations, or even governments, and can cause severe damage before the vulnerability is patched.
Zero-day vulnerabilities are particularly dangerous because they pose a high risk to systems and data. The longer they remain undetected, the more time attackers have to exploit them without interference. This makes identifying and mitigating zero-day threats a critical priority for security teams and organizations worldwide.
The Zero-Day Lifecycle
A zero-day exploit goes through several stages, from discovery to eventual resolution. Understanding this lifecycle can provide insight into how zero-day vulnerabilities develop, why they pose a significant threat, and why early detection and response are critical.
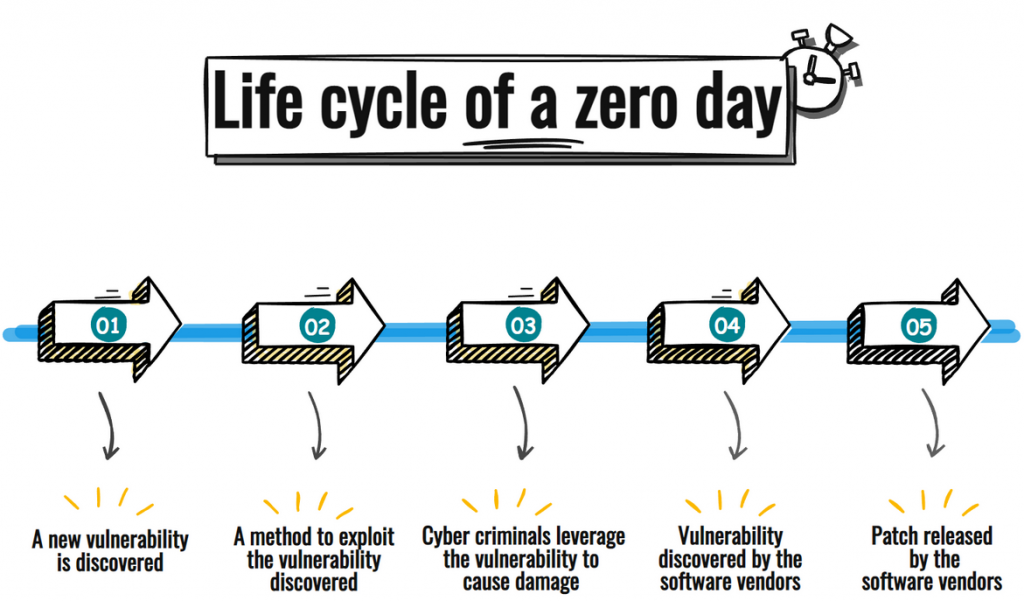
1. Discovery
The lifecycle begins when a vulnerability is first discovered. This discovery can occur in several ways—it may be identified by malicious actors, independent cybersecurity researchers, or software developers during routine audits.
When cybercriminals discover a zero-day vulnerability, they often keep it a closely guarded secret, using it to launch targeted attacks and infiltrate systems without detection. This secrecy allows them to exploit the vulnerability for as long as it remains undisclosed, often causing widespread damage before detection.
2. Exploitation
Once discovered, attackers move quickly to exploit the vulnerability. This is where the most harm occurs, as attackers use the flaw to gain unauthorized access to systems, steal data, deliver malware, or disrupt operations. The longer it takes for the vulnerability to be identified and addressed by the vendor, the greater the damage can be. In some cases, attackers may sell or share the exploit on dark web marketplaces, amplifying its reach and potential impact.
3. Disclosure and Patch Development
If a security researcher or software vendor identifies the vulnerability, they may follow a responsible disclosure process. This involves privately informing the affected organization or vendor, giving them time to develop a patch before publicizing the vulnerability.
The patch development process can take a few days, weeks, or even months, depending on the issue’s complexity. Unfortunately, systems remain exposed during this period, and attackers may continue to exploit the vulnerability, making timely remediation essential.
4. Public Awareness
The final stage occurs when the vulnerability and its patch are made public, typically through security bulletins or advisories from the vendor. While this transparency is crucial for informing system administrators and users about the need to update their software, it also has a downside.
Attackers often analyze the patch to understand the vulnerability it addresses, potentially using that knowledge to identify similar system flaws or target users who have not yet applied the update, underscoring the importance of prompt patching and ongoing vulnerability management to reduce the risk of future attacks.
Why Are Zero-Day Vulnerabilities Significant?
Cybercriminals highly prize zero-day exploits because they represent a golden opportunity to launch undetected attacks. Here’s why they pose such a significant threat:
- Lack of Prevention or Defense: Zero-day vulnerabilities are, by nature, unknown, leaving organizations without any preventative measures or defenses until the issue is identified.
- Targeted Attacks: These vulnerabilities are often exploited in highly targeted attacks, making them particularly dangerous for organizations and individuals alike.
- No Available Patch: Zero-day vulnerabilities remain unpatched until a fix is developed and deployed. This leaves systems exposed and vulnerable for an unpredictable period.
- High Value to Cybercriminals: Zero-day exploits are prized assets on dark web marketplaces, often selling at a premium. They are sought after by cybercriminals, hacktivists, and even nation-states for their ability to cause significant harm.
- Potential for Widespread Damage: If a zero-day vulnerability impacts commonly used software, it can compromise millions of devices globally. The scale of potential damage is immense, especially for widely integrated platforms.
- Challenges in Detection: Traditional security tools, such as antivirus programs, are largely ineffective against zero-day threats because these vulnerabilities are unknown. This makes detection difficult, allowing such attacks to go unnoticed for extended periods.
These factors make zero-day vulnerabilities one of the most dangerous weapons in a hacker’s arsenal.
Notable Examples of Zero-Day Exploits
Several high-profile zero-day exploits have caused widespread disruption and drawn attention to the seriousness of this threat. Below are some of the most notable examples:
Stuxnet (2010)
Stuxnet is one of the most famous zero-day exploits. In 2010, it targeted Iran’s nuclear facilities. The malware exploited four zero-day vulnerabilities in Windows to disrupt uranium enrichment processes by manipulating industrial control systems.
Zoom (2020)
In the early days of the pandemic, Zoom became a lifeline for remote work and communication. A zero-day exploit in Zoom’s software allowed attackers to access users’ devices, raising significant privacy and security concerns.
Log4Shell (2021)
This zero-day vulnerability in the widely used Log4j library sent shockwaves through the tech world. Log4Shell allowed attackers to execute code remotely on affected systems, impacting thousands of organizations globally.
Google Chrome Zero-Day Vulnerabilities (2022)
Google Chrome, one of the most popular web browsers, was targeted by multiple zero-day exploits in 2022. Although these vulnerabilities were quickly patched, they exposed users to risks ranging from data theft to complete system takeover.
Barracuda Networks Exploit (2023)
This zero-day vulnerability affected Barracuda’s Email Security Gateway, allowing threat actors to install backdoors and execute arbitrary commands on affected systems. It was linked to Chinese state-sponsored groups, and attackers used this vulnerability to access sensitive data and exploit network security.
How Do Cybercriminals Find and Exploit Zero-Day Vulnerabilities?
Cybercriminals employ a range of sophisticated methods to discover and exploit zero-day vulnerabilities, often staying ahead of security measures:
Reverse Engineering: Hackers frequently reverse-engineer patches vendors release to identify unpatched code vulnerabilities. By analyzing the fixes applied to software, they can pinpoint weaknesses that have not yet been fully addressed or disclosed, allowing them to exploit these gaps before vendors can respond effectively.
Vulnerability Scanning: Attackers can systematically scan software for flaws using automated vulnerability scanning tools. These highly efficient tools can identify weaknesses, including potential zero-day vulnerabilities that even the software’s creators may not yet know about. By leveraging such tools, cybercriminals can quickly target exploitable issues across various systems.
Insider Information: In some cases, zero-day vulnerabilities are leaked or sold by insiders with privileged access to sensitive information. These insiders might be disgruntled employees, contractors, or individuals incentivized through financial gain. Such leaks make zero-day vulnerabilities particularly dangerous, as they provide attackers with critical intelligence that is not yet publicly available, further complicating detection and mitigation efforts.
By combining these tactics, cybercriminals can uncover and exploit vulnerabilities before they are widely known or patched, increasing their chances of success in launching attacks. Zero-day vulnerabilities’ secretive and time-sensitive nature makes them one of the most challenging threats for organizations to defend against.
Who Are the Common Targets of Zero-Day Attacks?
Zero-day attacks are not limited to specific industries. Here are some of the most common targets:
Government Agencies: Nation-states often target agencies for espionage, stealing classified data, and compromising critical infrastructure.
Large Corporations: Corporations, especially those in the technology, finance, and healthcare sectors, are frequently targeted to steal intellectual property or disrupt operations.
Critical Infrastructure: Attacks on critical infrastructure, such as power grids, hospitals, and transportation systems, can cause widespread chaos and are often motivated by political or military agendas.
Individuals: High-profile individuals, such as executives or those with privileged access to sensitive data, can also be targeted, often for financial gain or sabotage.
How to Protect Against Zero-Day Exploits
While zero-day exploits are challenging to predict, there are several proactive steps organizations and individuals can take to reduce their risk:
- Patch Management: Keeping software up-to-date is one of the most effective defenses against zero-day exploits. Regular updates ensure that known vulnerabilities are patched promptly.
- Vulnerability Management: A robust vulnerability management process involves identifying, assessing, and prioritizing software vulnerabilities to reduce the attack surface.
- Attack Surface Management (ASM): ASM involves proactive measures to secure digital assets by monitoring all aspects of cyber-physical asset behavior to proactively identify and respond to risk. We discuss this further below.
- Threat Intelligence: Leveraging threat intelligence feeds can help organizations stay informed about emerging zero-day threats and respond quickly.
- Anomaly-Based Detection Systems: Implementing anomaly-based detection systems can help identify suspicious behavior that may indicate a zero-day exploit in progress.
- Zero Trust Architecture: By implementing zero-trust principles, organizations can limit attackers’ movement within their networks, reducing the impact of a zero-day exploit.
- Application Sandboxing: Isolating applications in a controlled environment prevents attackers from gaining full access to your system if a zero-day vulnerability is exploited.
The Role of Attack Surface Management in Defending Against Zero-Day Exploits
An effective defense against zero-day exploits requires constant vigilance. Attack surface management tools provide organizations with continuous monitoring and real-time risk exposure assessments, allowing them to take proactive measures before vulnerabilities are exploited.
- Continuous Monitoring
Organizations can detect potential weaknesses by monitoring all assets before they become entry points for zero-day attacks. - Automated Remediation
Automated systems can prioritize and remediate vulnerabilities in real time, significantly reducing attackers’ time to exploit them.
Frequently Asked Questions
- What is a zero-day vulnerability?
-
A zero-day vulnerability is a software security flaw that is unknown to the vendor or developer. Because no patch exists, attackers can exploit it before it’s publicly disclosed or fixed.
- Why are zero-day attacks dangerous?
-
Zero-day attacks are dangerous because they exploit unknown vulnerabilities, giving defenders no time to prepare or patch the system. This makes them highly effective for cybercriminals and state actors.
- How are zero-day vulnerabilities discovered?
-
Zero-days can be discovered by ethical hackers, researchers, or malicious actors scanning software code for flaws. Sometimes, they’re found through reverse engineering or fuzz testing.
- Can zero-day vulnerabilities be prevented?
-
While it’s impossible to prevent all zero-days, strong security practices like threat modeling, regular code audits, and endpoint detection can reduce exposure and impact.
- What should organizations do after a zero-day is found?
-
Once a zero-day is identified, organizations should implement mitigations, monitor for exploit activity, and apply patches as soon as they’re released. Communication with vendors and users is also critical.


