What is Threat Intelligence in Cybersecurity?
Threat intelligence enables organizations to take a proactive approach to cyber security with more informed, faster, and data-driven decisions. Security incidents are the result of not knowing or not seeing. Threat intelligence remedies this by taking into account all areas of an organization’s attack surface.
Cyber threat intelligence results from disparate cyber threat data collected, processed, and analyzed to provide insights into cybercriminals’ motives, targets, and methodologies. Because cyber threat intelligence delivers accurate, timely, and relevant information, it can be used to identify existing or emerging security incidents reliably.
By understanding the entire ecosystem, organizations are able to better prepare for, prevent, and identify cyber threats with more optimized security mechanisms. Threat intelligence also provides the information needed to help leadership understand the scope and scale of the risks, the resource requirements for an effective security program, and the financial impact of cybersecurity efforts—both the risks and rewards.
Threat intelligence solutions aggregate raw data from a number of sources to create a rich pool of information. This data is then analyzed to identify anomalies, patterns, and other indicators of potential threats. This data is shared with security systems and teams. The information is also organized into accessible reports for audiences inside and outside of IT.
To fully realize the benefit of threat intelligence to reduce cyber risks, threat data should be integrated into a cybersecurity posture automation platform. Threat information ingested by a cybersecurity posture automation platform allows organizations to prioritize the remediation of vulnerable assets that might be exploited by threats. The platform also allows enterprises to quantify risk in monetary terms allowing security teams to prioritize remediation efforts based on business impact. Board members and senior management gain real-time visibility into the cyber risk posture of their organization and the potential financial impact of threats. The platform also provides unified asset inventory including a software bill of materials (SBOM) with asset details including libraries containing vulnerabilities currently being exploited.
Importance of Cyber Threat Intelligence
The importance of cyber threat intelligence crosses all parts of an organization—from IT to the C-suite. Cyber threat intelligence provides the actionable information needed to defend against the increasing and varied attacks that target all organizations.
Cyber threat intelligence brings clarity to the overwhelming volumes of data that is collected as well as alarms and alerts from security systems. By aggregating and analyzing all available data, cyber threat intelligence is able to identify risks and patterns that could be indicators of security vulnerabilities. With cyber threat intelligence, organizations are able to defend against all manner of risks, including advanced persistent threats (APT) and zero-day threats (ZDT).
Benefits of Cyber Threat Intelligence
- Enhances alert quality
- Improves an organization’s detection and response capabilities
- Increases incident coverage
- Minimizes investigation time
- Reduces mean time to respond
- Reveals critical threats
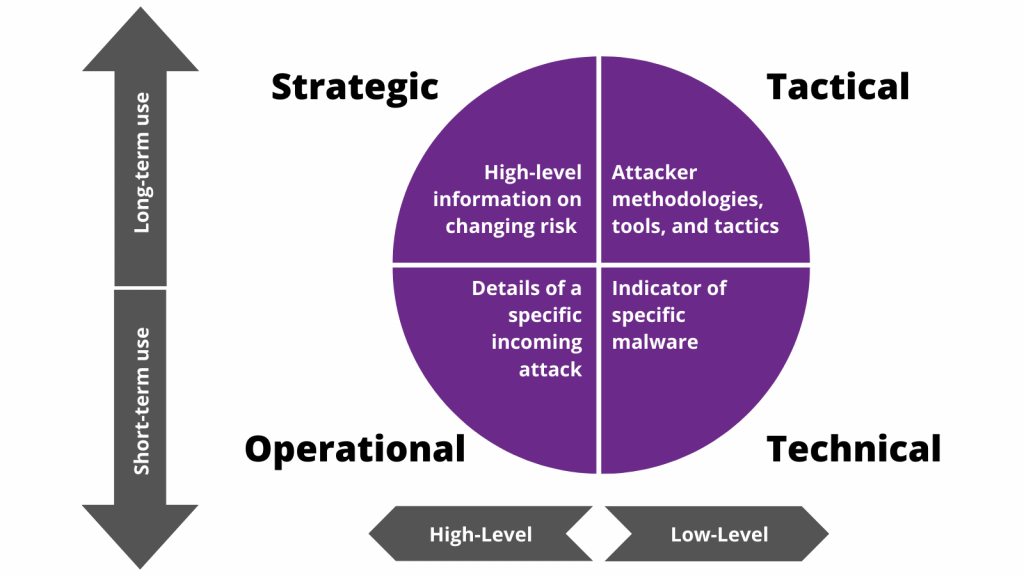
Types of Cyber Threat Intelligence
The three main categories of cyber threat intelligence are:
- Strategic
- Tactical
- Operational or technical
Strategic Cyber Threat Intelligence
Threat intelligence considers more than just the technical aspects of risks and takes into account the motivations behind them. The strategic angle of cyber threat intelligence considers who or what organization is driving attacks, what their objectives are, and the reason a target is selected. It is used to provide a timely warning about pending threats and to help organizations proactively put up defenses based on attack trends.
Strategic threat intelligence aggregates and analyzes disparate data, including news media, policy papers from governments and non-government organizations (NGOs), and subject-matter experts. The rich insights are compiled into briefings, papers, reports, and other content by security organizations. This information is usually consumed by IT managers and CISOs, with relevant highlights shared with the executive team. It helps organizations prioritize budgets and the allocation of internal resources.
The types of information gathered as part of strategic cyber threat intelligence include:
- Attack trends
- Details about known breaches
- Financial impact of the cyber threats
- Known cybercriminals, criminal syndicates, and nation-state actors
- Statistical information related to data breaches and malware
- Threat landscape specific to industry sectors
Tactical Cyber Threat Intelligence
To identify the how and where of attacks, tactical cyber threat intelligence focuses on the tactics, techniques, and procedures (TTP) to develop a complete understanding of the technical details of attacks. Tactical cyber threat intelligence provides the information needed to develop an effective defense, allowing organizations to be well prepared to respond. In addition, it helps stop an attack or mitigate its impact.
In part, tactical cyber threat intelligence assesses real-time events and investigations to support day-to-day security activities, such as the development of signatures and indicators of compromise (IOC). In some cases, it includes low-level intelligence analysis. Often, tactical threat intelligence is provided by third-party vendors for consumption by IT team members, including network security, architecture, and administration.
Tactical cyber threat intelligence usually includes specifics about the attack vectors, tools, and infrastructure used by attackers. It also details vulnerabilities that are being targeted, tactics that attackers are leveraging, and the strategies and tools they are using to evade or delay detection.
Tactical cyber threat intelligence includes:
- Attack group reports
- Available patches
- Campaign reports
- Incident reports
- Information obtained from human intelligence gathering
- Known threat indicators
- Malware updates
Operational/Technical Cyber Threat Intelligence
The information provided from operational or technical cyber threat intelligence is collected from known attacks, including active campaigns, information gathered from investigations of past attacks, and data provided by third-party research groups. Additional operational or technical threat intelligence sources are humans, social media, and chat rooms.
This type of threat intelligence has a shorter shelf life than tactical threat intelligence and primarily focuses on specific indicators of compromise (IoC) to expedite responses to attacks. Operational or technical cyber threat intelligence is presented in reports that contain known malicious activities, recommendations for defense and remediation, and warnings of imminent attacks.
Operational or technical cyber threat intelligence gives IT and security teams specific details about identified indicators. These can then be incorporated into the defensive systems, such as SPAM filters, firewalls, intrusion detection systems (IDS) and intrusion prevention systems (IPS), security orchestration, automation and response (SOAR), and security information and event management (SIEM). Actions taken based on operational or technical cyber threat intelligence include blocking attacks, triaging and validating alerts, and searching for and neutralizing identified threats.
Examples of technical cyber threat intelligence include:
- Command and control channels
- Details related to the specific implementation of malware
- File names
- Malicious traffic
- Suspicious IP addresses and domains
- Tools used for attacks
- URLs
Threat Intelligence Lifecycle
A cyber threat intelligence lifecycle model is used to develop actionable information from raw data to help organizations tune defensive mechanisms, minimizing risk by reducing and hardening potential attack surfaces. Effective cyber threat lifecycle models take a holistic approach and work as a continuous, looping set of processes designed to identify intelligence gaps and prompt new collection requirements that start the intelligence cycle anew. The six main steps in a threat intelligence lifecycle are as follows.
1. Planning
In order to develop intelligence, it is critical to start with the right questions. These should focus on a specific fact, event, or activity rather than being open-ended questions. In addition, it is important to consider the audiences and consumers of the information. Taking time up-front to plan cyber threat intelligence activities ensures that the results will be useful and make the most of valuable resources.
2. Collection
When gathering raw data, it is best to tap into a broad range of internal and external sources that meet the criteria established in the planning phase. Sources of data to support a threat intelligence lifecycle include:
- Curated threat intelligence
- Data from the open web and the dark web
- Incident alerts from internal systems
- Information from news sources and social media
- Malicious IP addresses, domains, and file hashes
- Network event logs
- Open-source intelligence
- Records of past incident responses
- Third-party intelligence
3. Processing
Once collected, the raw data should be sorted and organized. To create a robust dataset for analysis, the following should be part of the processing.
- Addition of metadata
- Classification
- Cleansing
- Data modeling
- Deduplication
- Enrichment
- Normalization
4. Analysis
To turn the raw data into actionable information, the analysis phase is crucial. This is where security issues are surfaced by identifying suspicious activity and patterns. Different types of analysis should be performed to meet the needs of the varied audiences, such as threat lists and peer-reviewed reports. The analysis phase of the threat lifecycle uses structured analytical techniques that override biases and uncertainties. The analysis should include:
- Correlating indicators and incidents
- Establishing relationships
- Structuring data for indexing and search
- Visualizing data
5. Dissemination
Reports on the findings from the analysis phase should be disseminated as quickly as possible and provided in formats that suit the consumers’ preferences. Who receives what information should be established in the planning phase and executed during the dissemination phase. As noted earlier, threat data should be integrated with a cybersecurity posture automation platform to provide a unified, near real-time model of cyber risk for vulnerability prioritization and remediation to reduce the likelihood and impact of threats.
6. Feedback
Assessing the quality and efficacy of cyber threat intelligence affirms that the information met the requirements established in the planning phase. Gathering feedback also helps identify gaps or errors and brings forward more questions or issues perpetuating the threat intelligence lifecycle.
Stay Ahead of Attacks with Cyber Threat Intelligence.
Cyber threat intelligence, combined with the right tools, people, and processes, is a must-have for organizations to stay ahead of increasingly sophisticated and growing cybercrime. It provides the insights required to focus efforts and resources to ensure optimal protection and expedites responses when incidents occur.