
John Shaffer
CIO, Greenhill & Co.
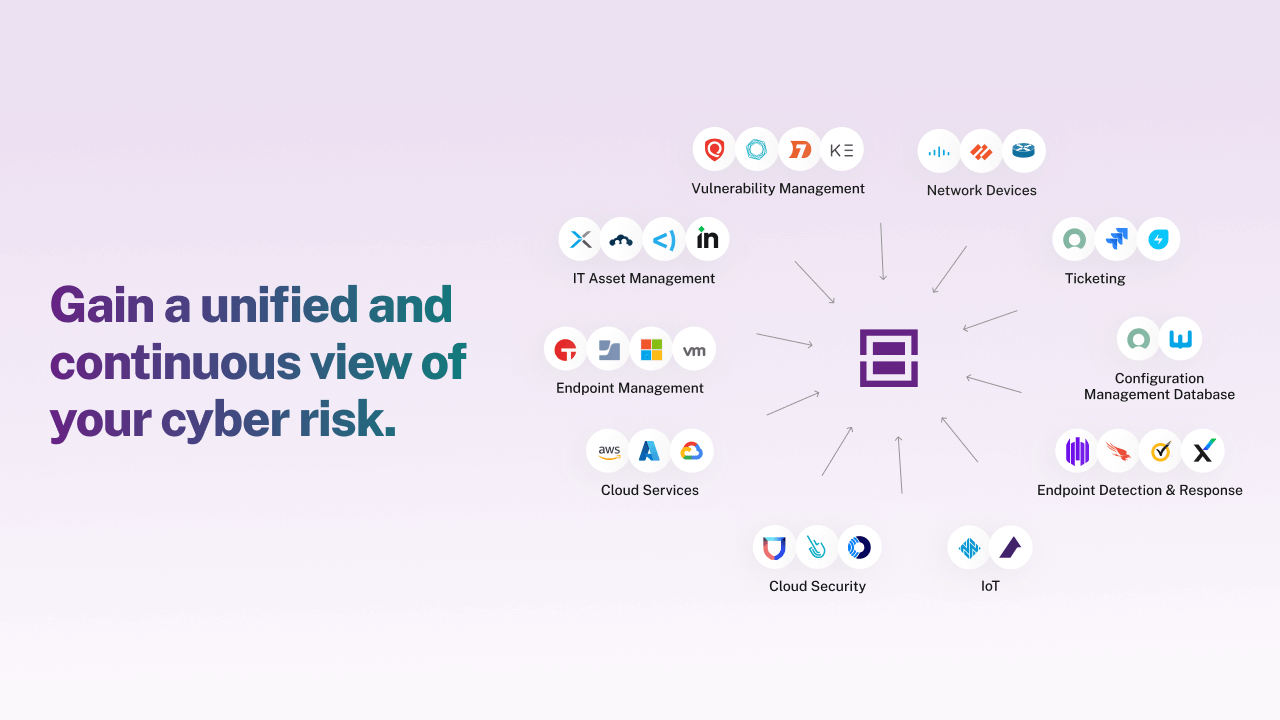
Full asset and risk visibility
You can’t protect what you can’t see. Balbix provides continuous, real-time visibility across your entire attack surface, ensuring that no vulnerability goes unnoticed and that coverage gaps are closed.
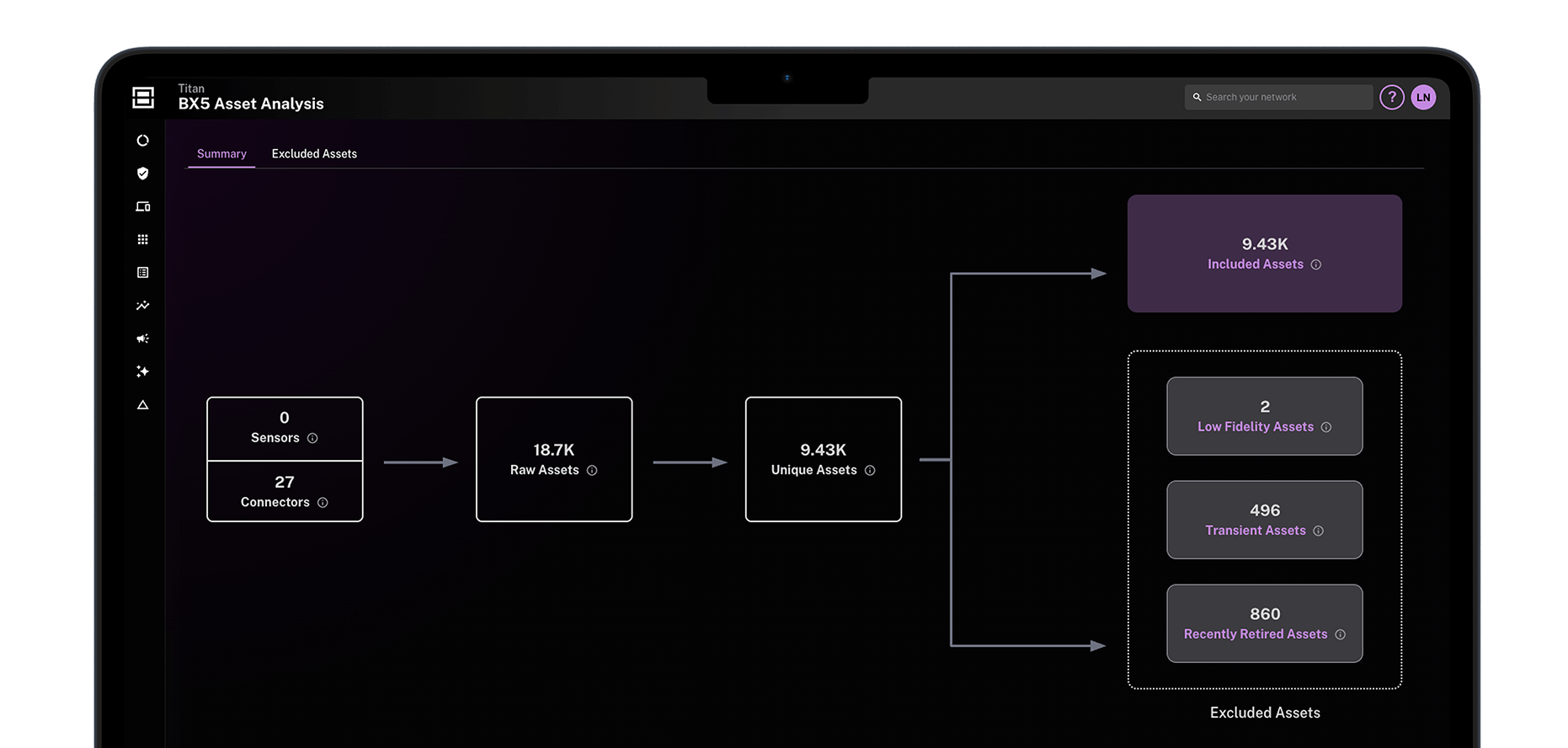

Unified security view
Get a complete inventory of assets, vulnerabilities, and security gaps in one dashboard. Filter out noise to focus on what truly matters.
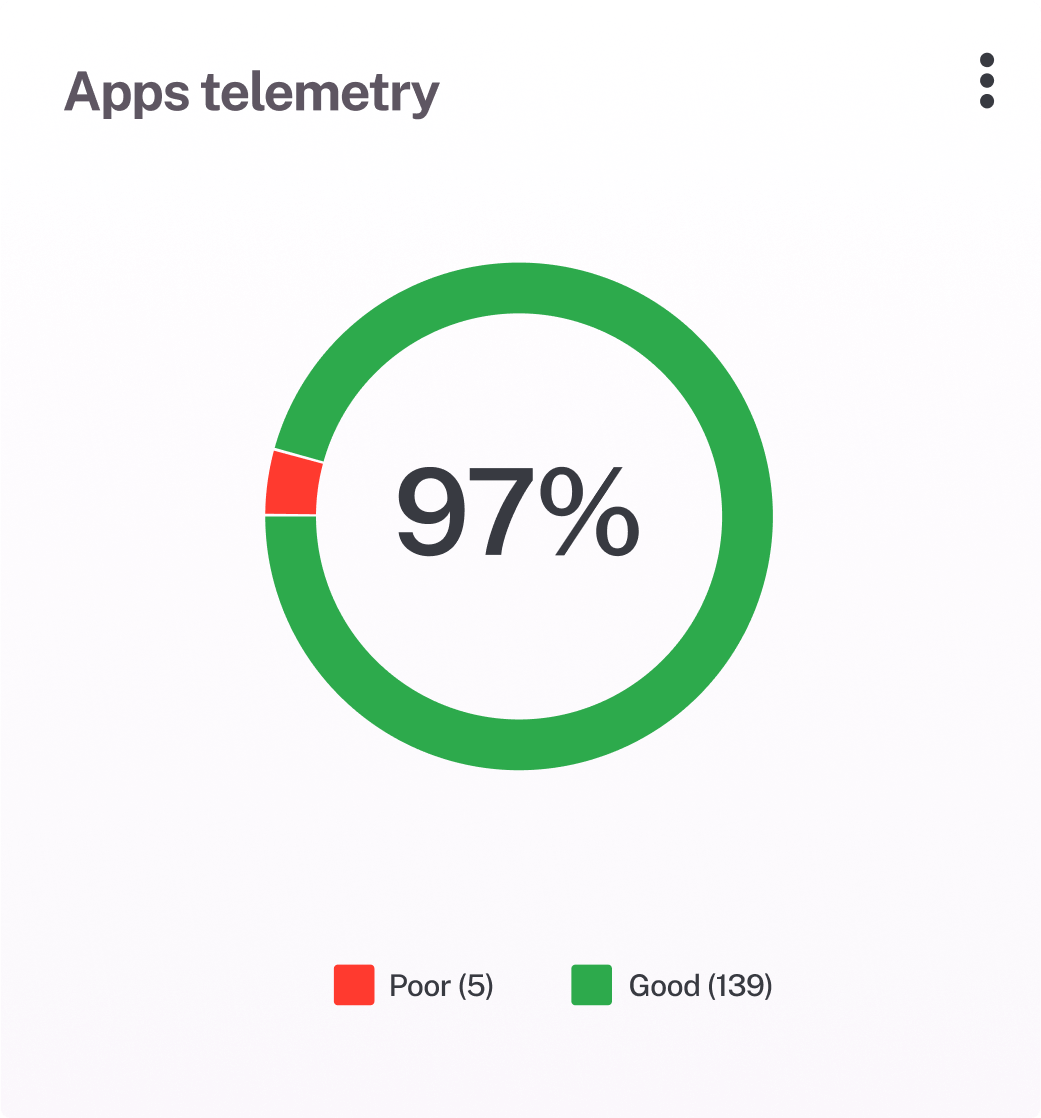
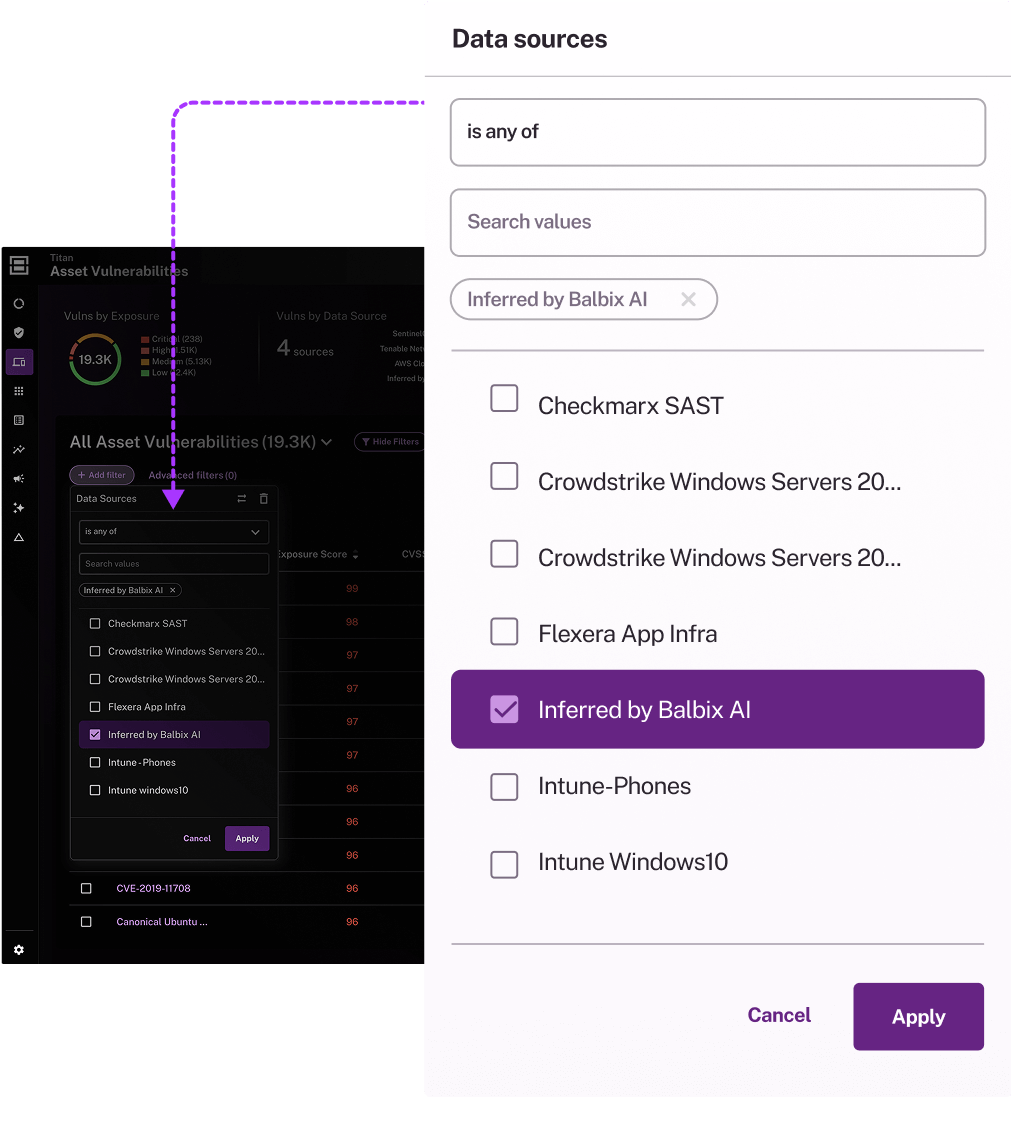
Identify hidden risks
Go beyond surface threats with advanced detection and inference. Uncover shadow IT, misconfigurations, EOL risks, and failed controls—aligned with your security policies.
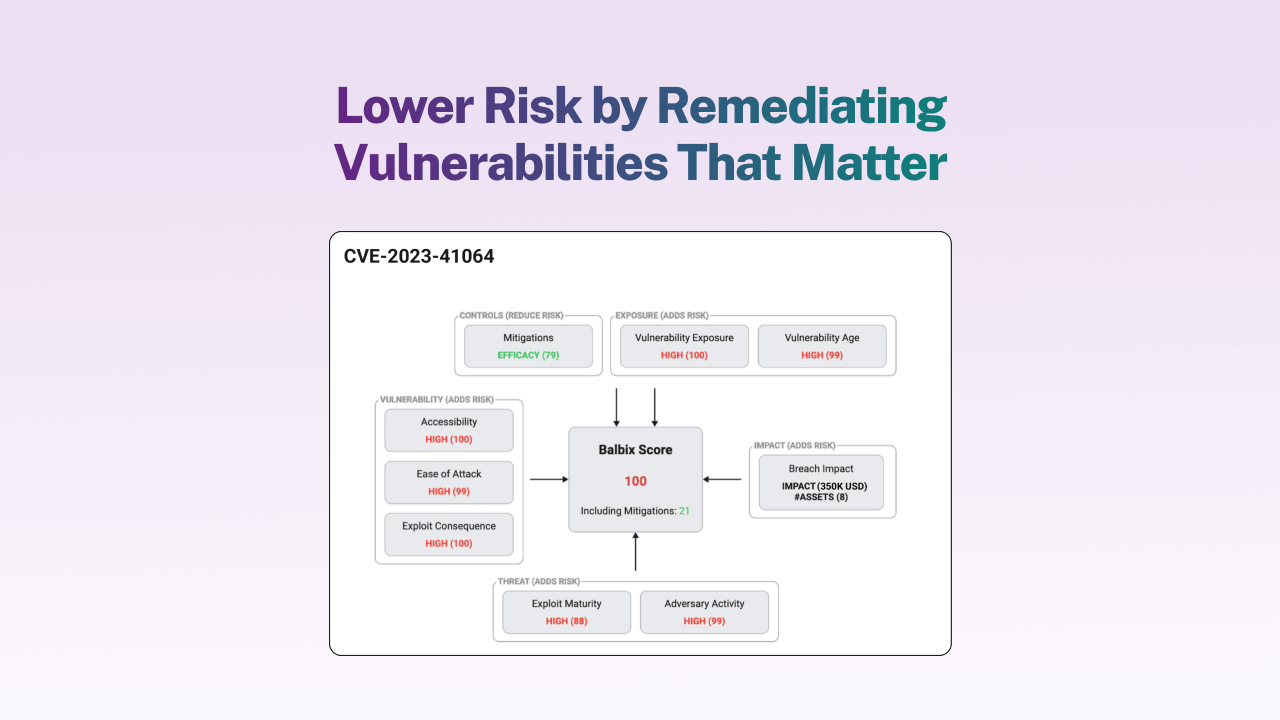
AI-powered risk prioritization
Vulnerability backlogs don’t secure your business—action does. Balbix uses threat intel, exploitability, business impact and security controls to identify vulnerabilities that matter most.
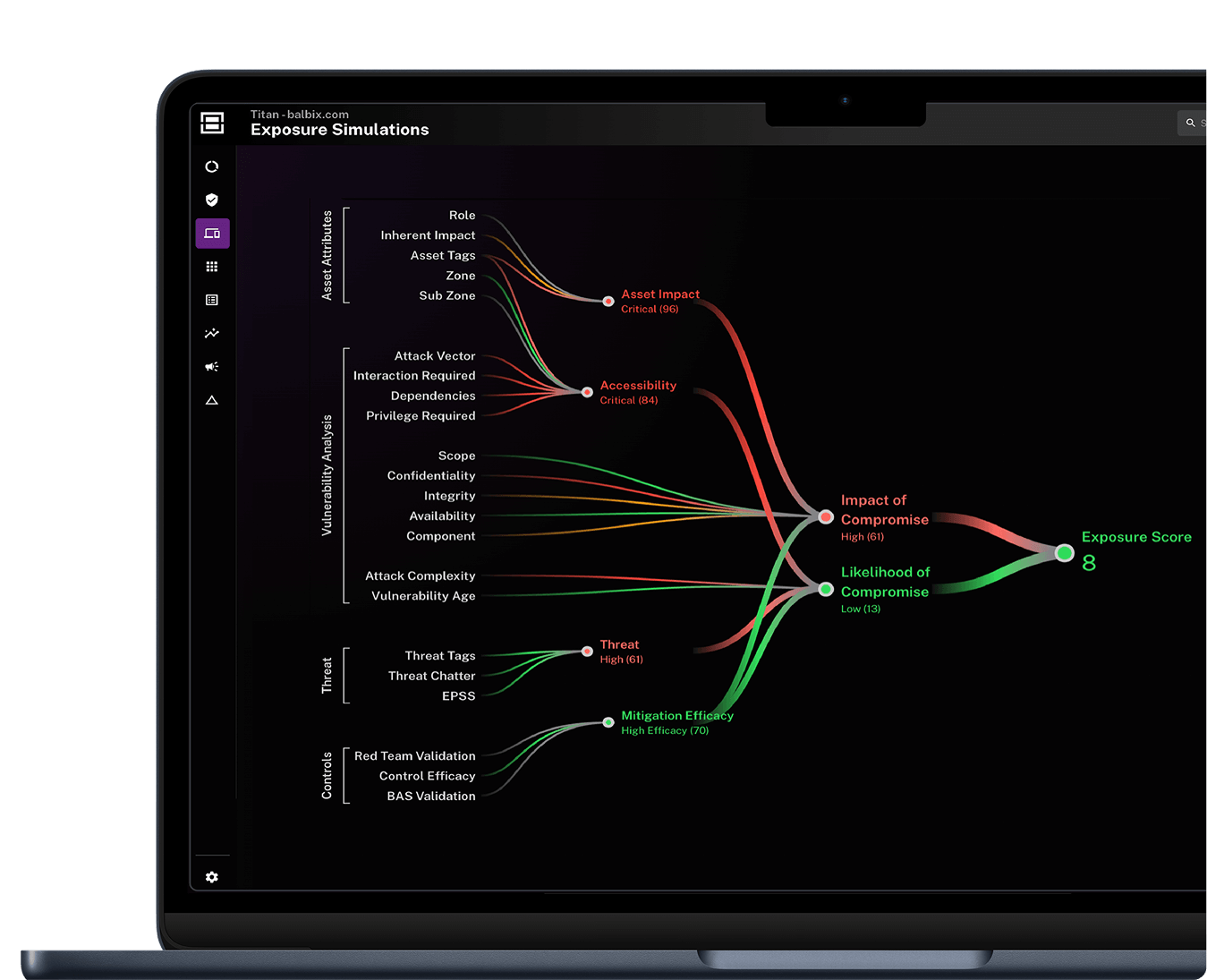
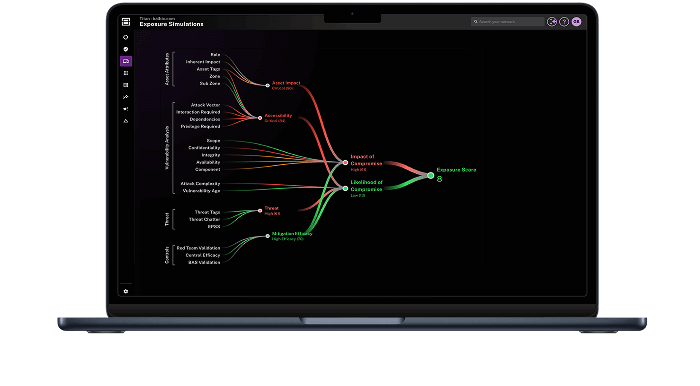
Eliminate CVSS overload
Cut through the noise and focus on the risks that truly matter. Map exposures to attacker TTPs to help prioritize the most exploitable risks and accelerate response times.
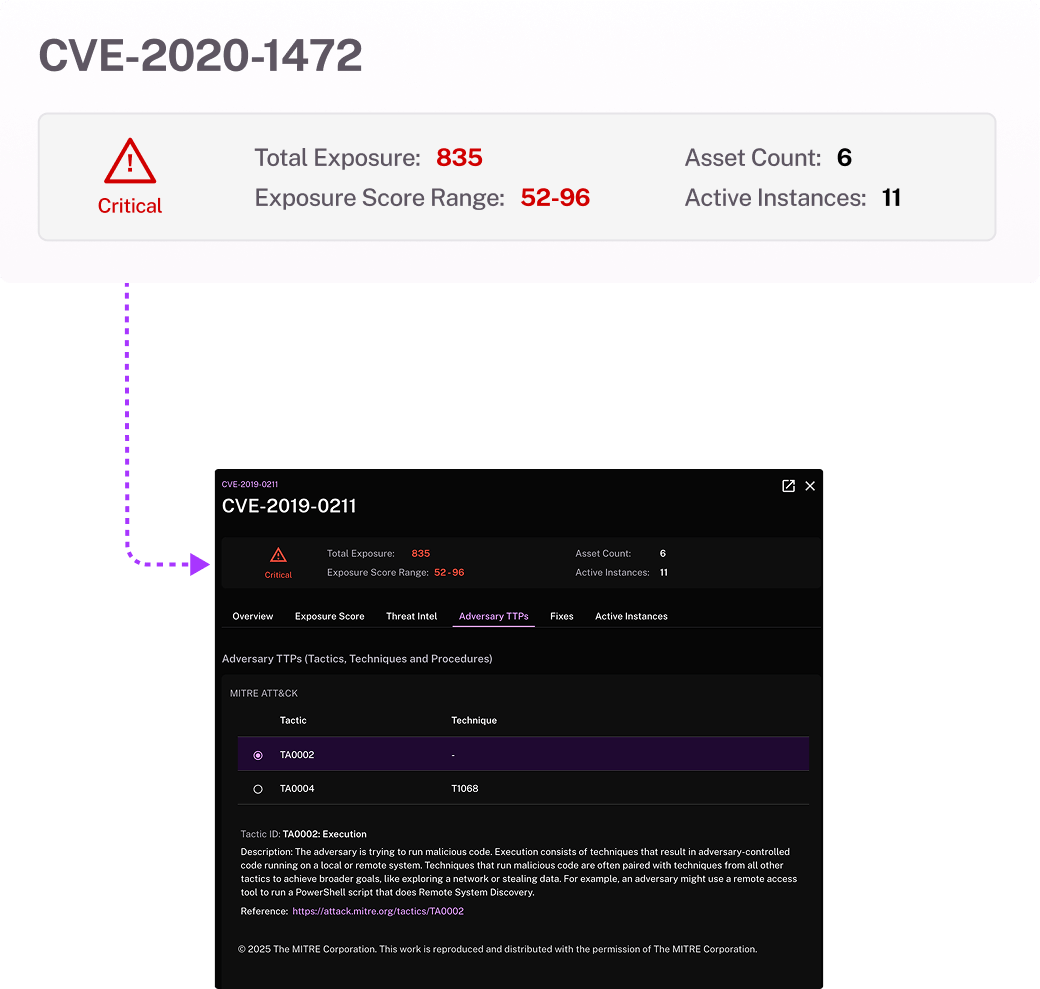
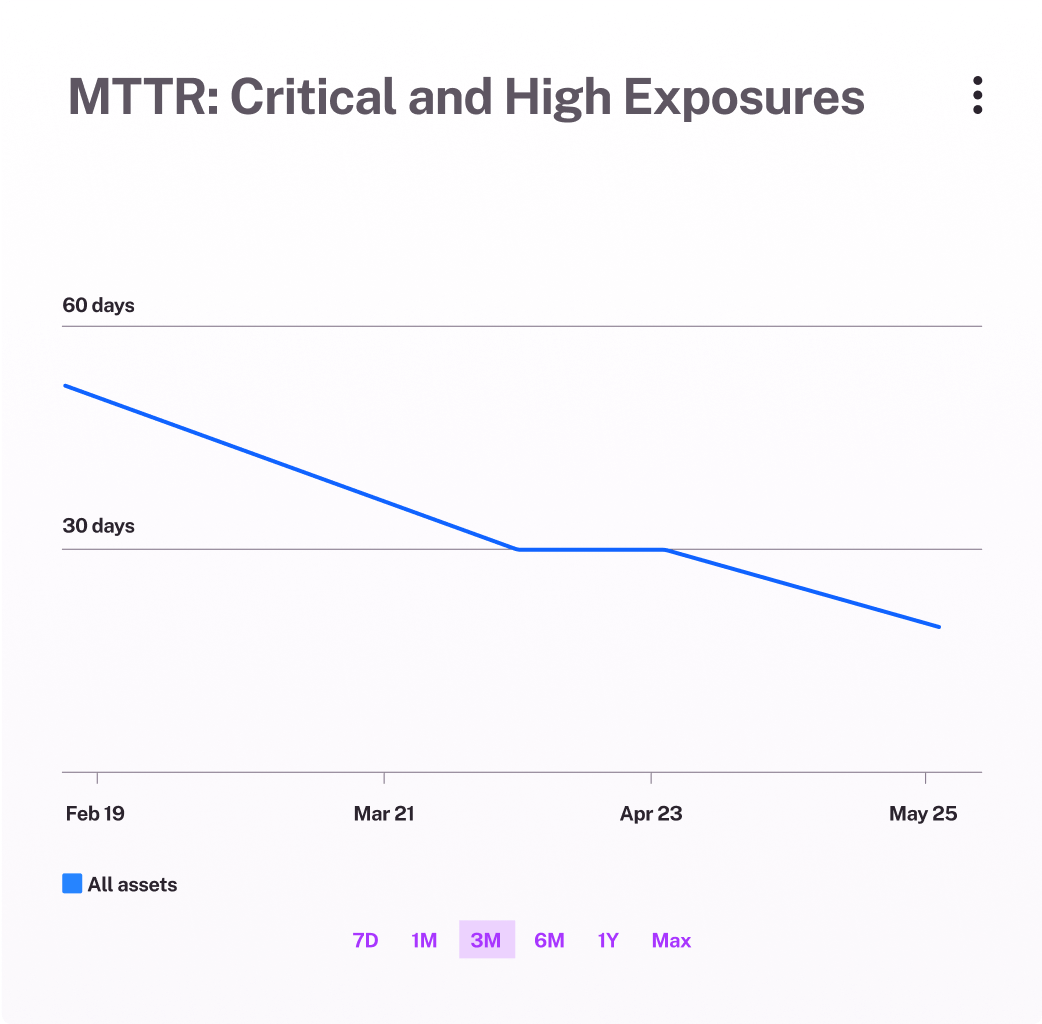
Prove vulnerability management program impact
Make informed decisions by prioritizing the most critical risks based on real exposure trends and financial impact. Meet VM reporting requirements with granular analysis, and extend risk assessments with built-in modeling that gives executives a clear view of potential business risk.
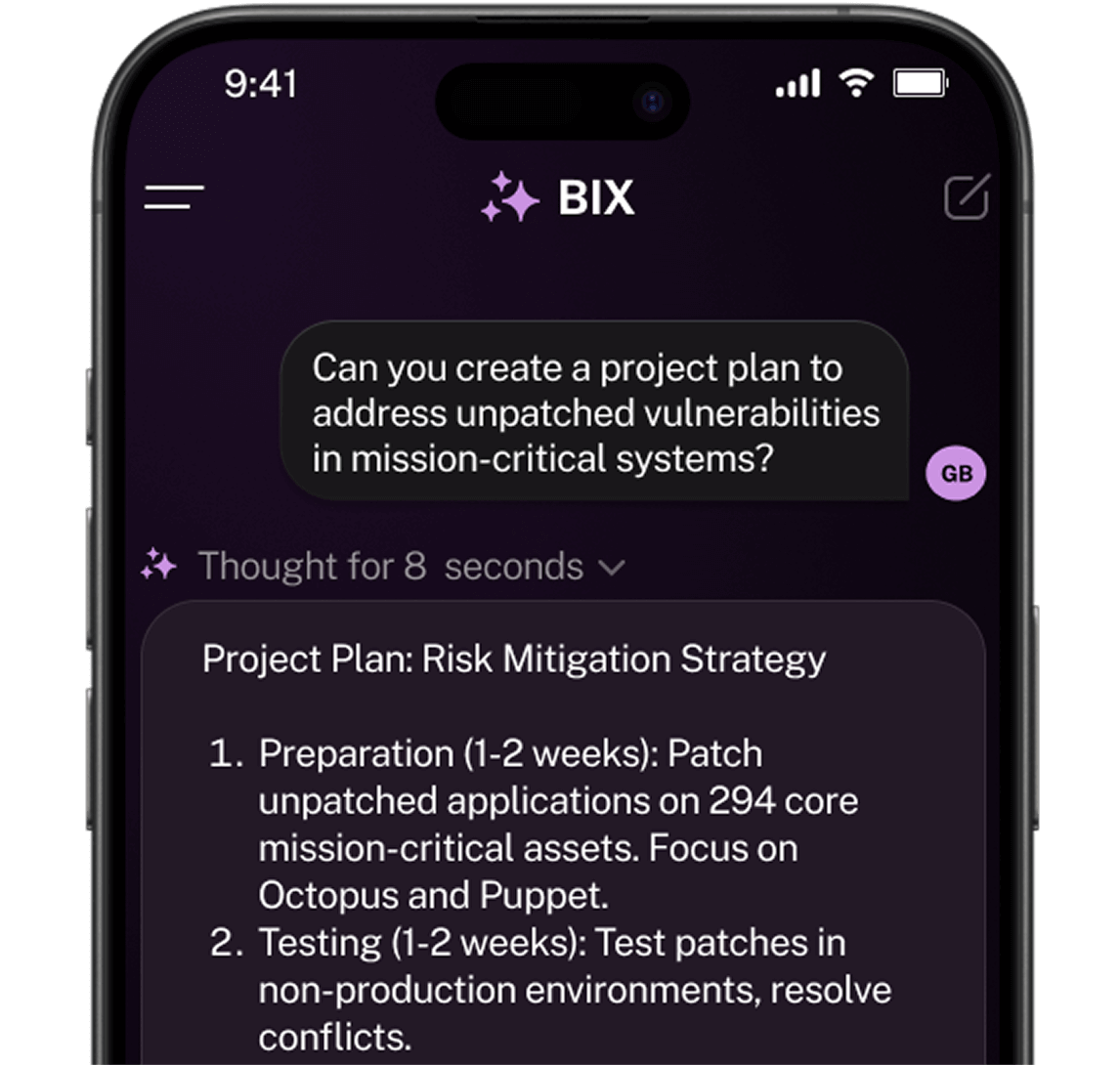
Automated remediation and AI assistant, BIX
With automated workflows, integrations, and Balbix’s GenAI assistant, BIX, reduces unnecessary communication and streamlines workload.
Accelerate ticket resolution
Eliminate bottlenecks in your vulnerability management workflow by seamlessly integrating with ticketing systems, reducing manual effort and ensuring the most critical issues are addressed first—so they can focus on mitigation, not chasing data.
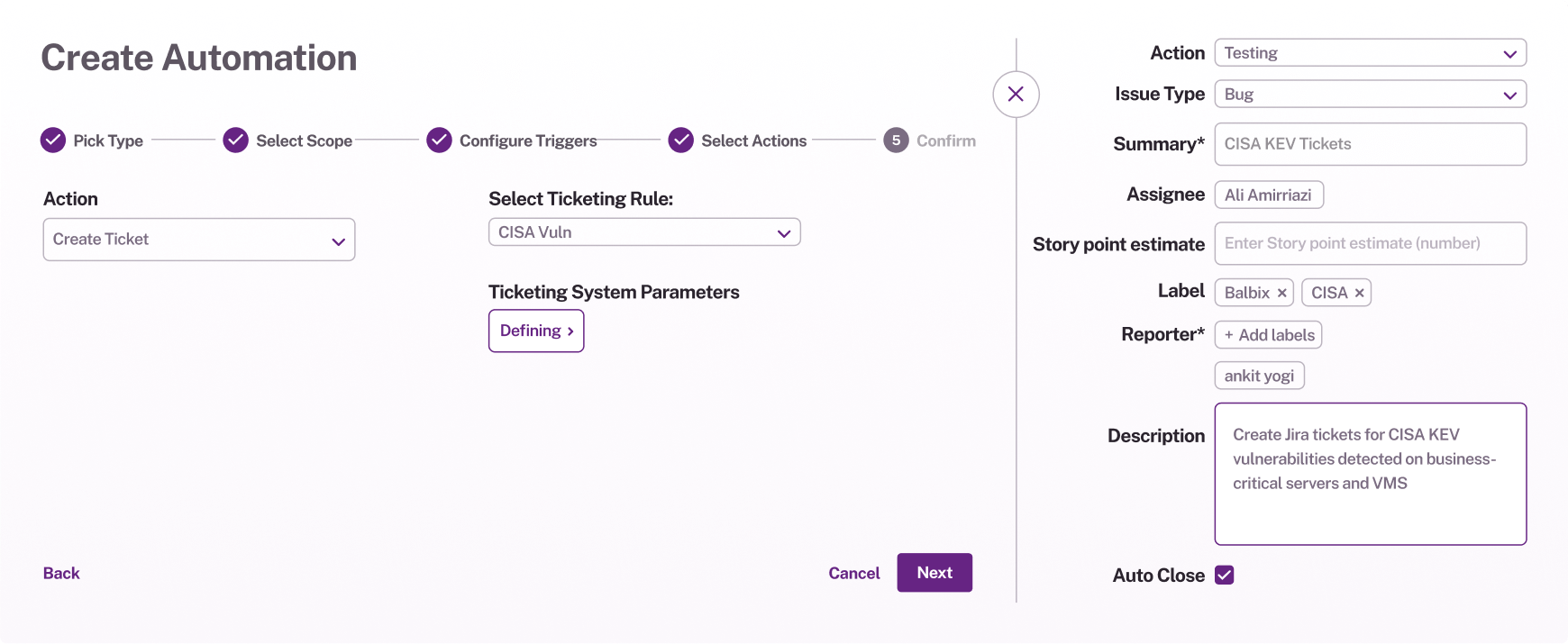
Integrate seamlessly, remediate faster
Connect your existing data sources and ticketing systems to streamline workflows. Automate ticketing, reduce manual effort, and give teams the right insights at the right time for faster remediation.
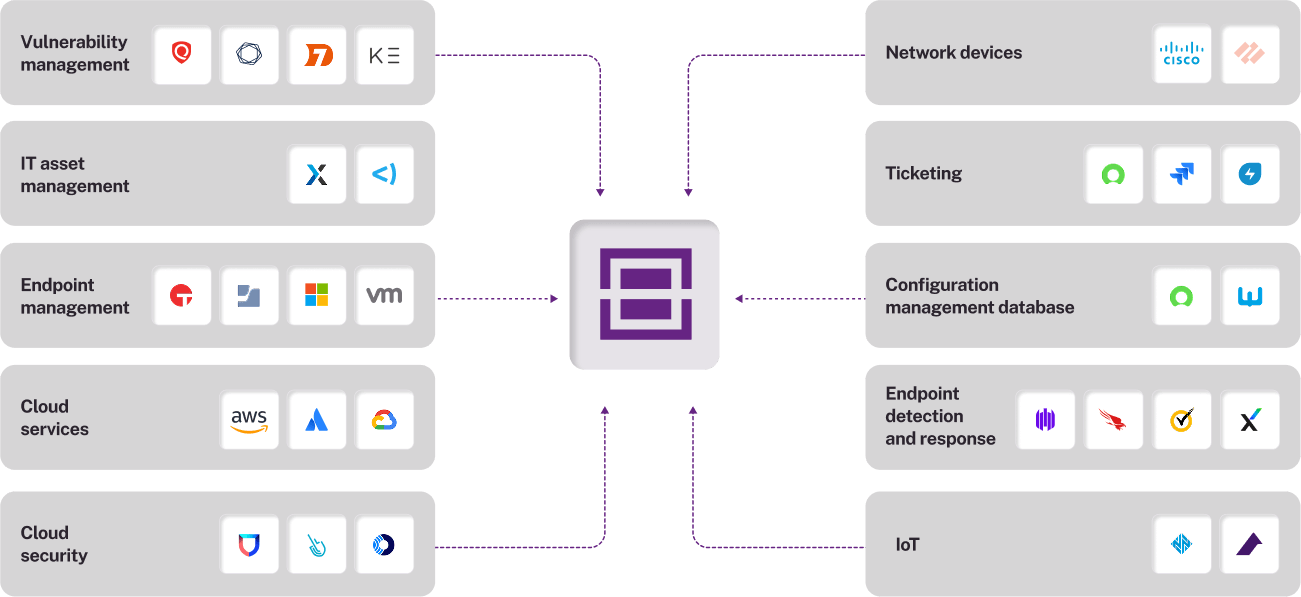
See all your cyber risks in one place
Move beyond CVEs—get a unified view of all exposures, including misconfigurations, failed controls, and EOL systems. Balbix consolidates your security data, helping you identify, quantify, and remediate risks automatically. Cut through the noise, reduce costs, and take proactive action to prevent breaches.
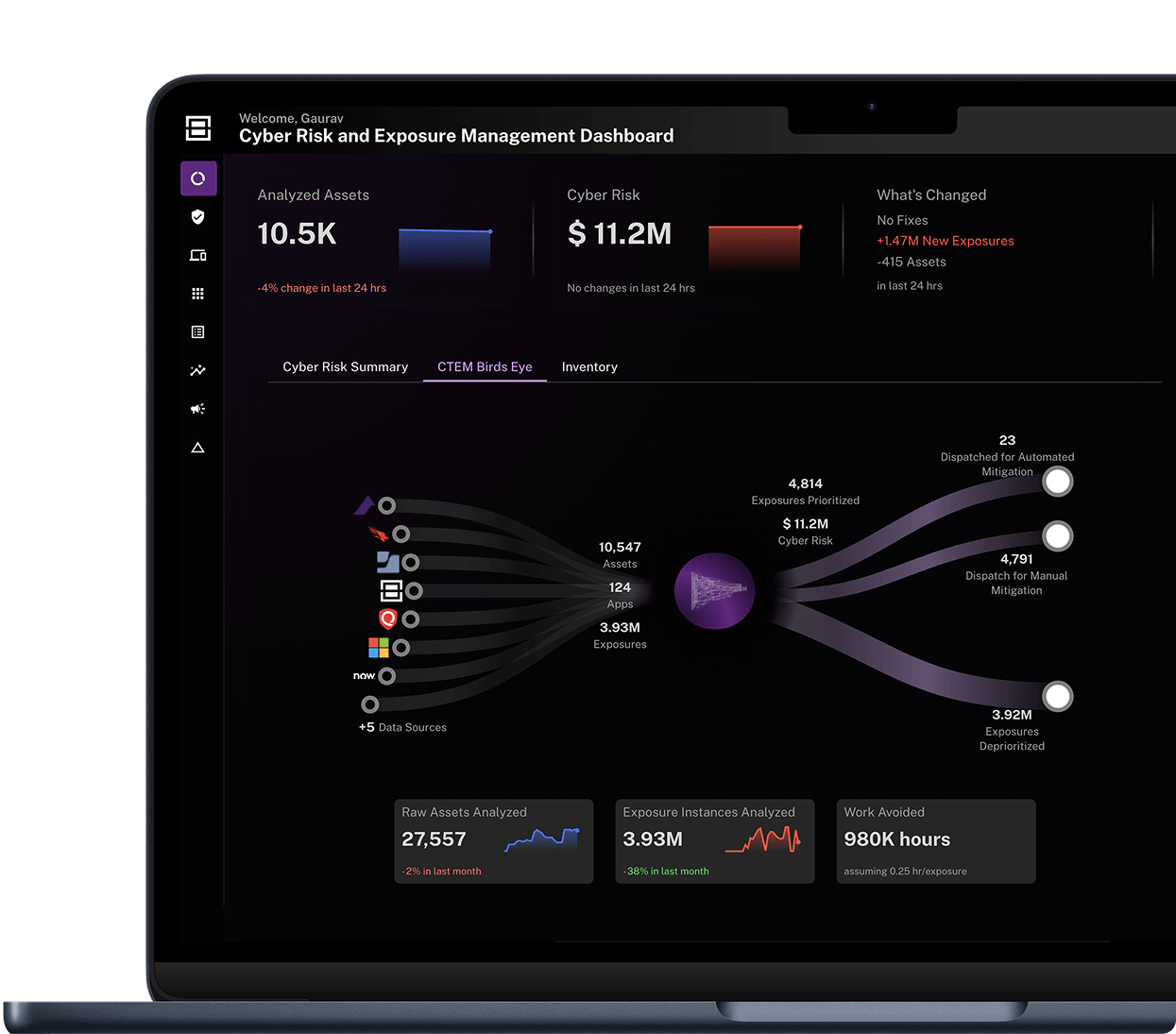
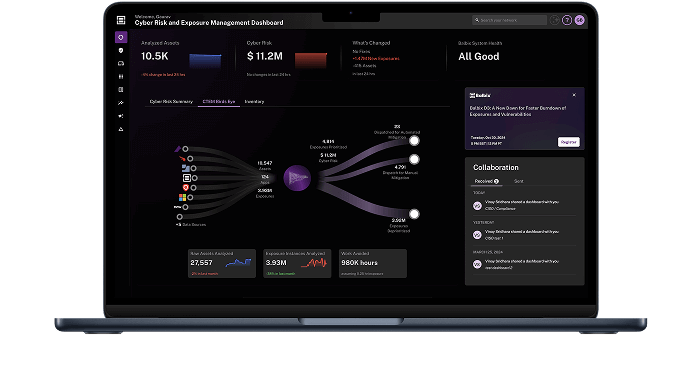
Prioritized exposure management
Not all exposures pose the same risk. Balbix analyzes misconfigurations, failed controls, and other weaknesses alongside threat intel and business impact—so you can focus on the most urgent security gaps before they’re exploited.
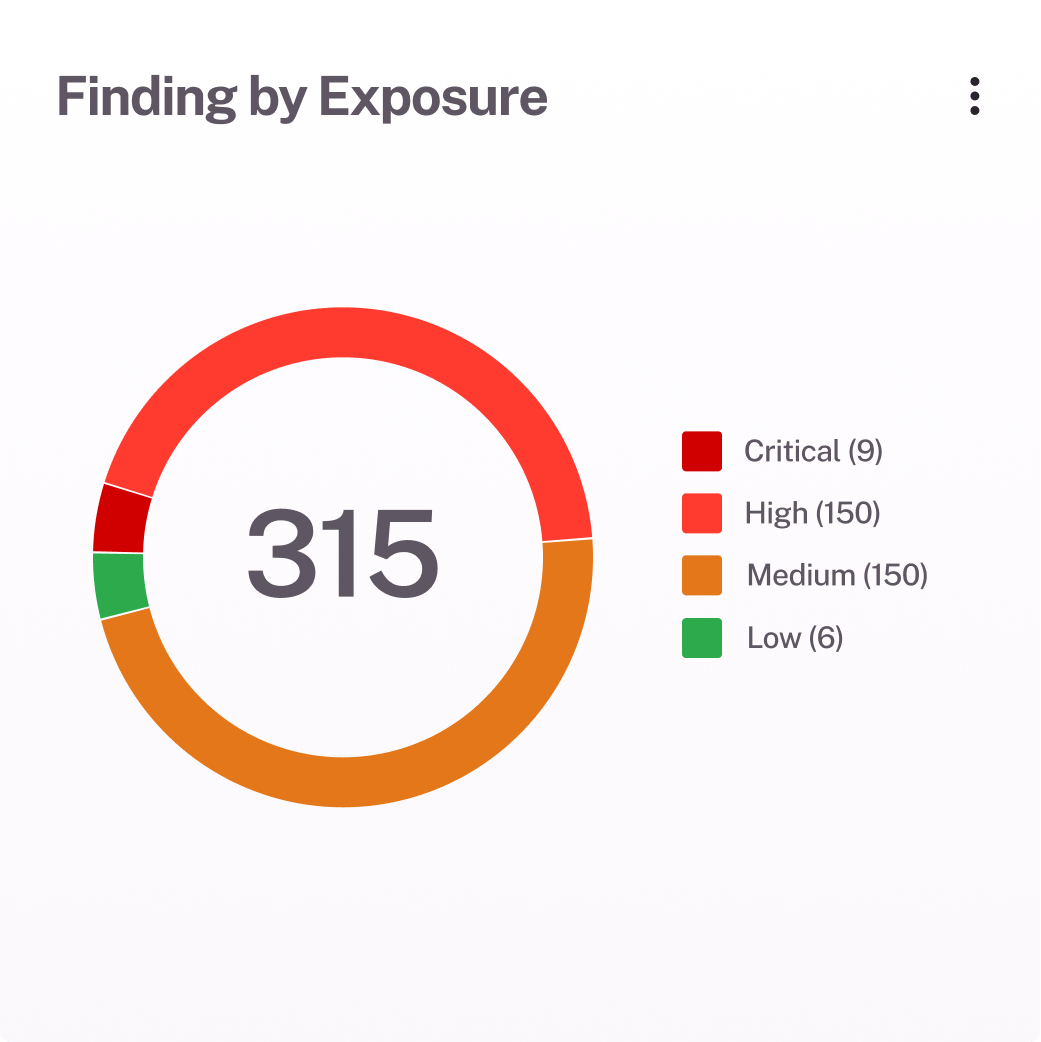
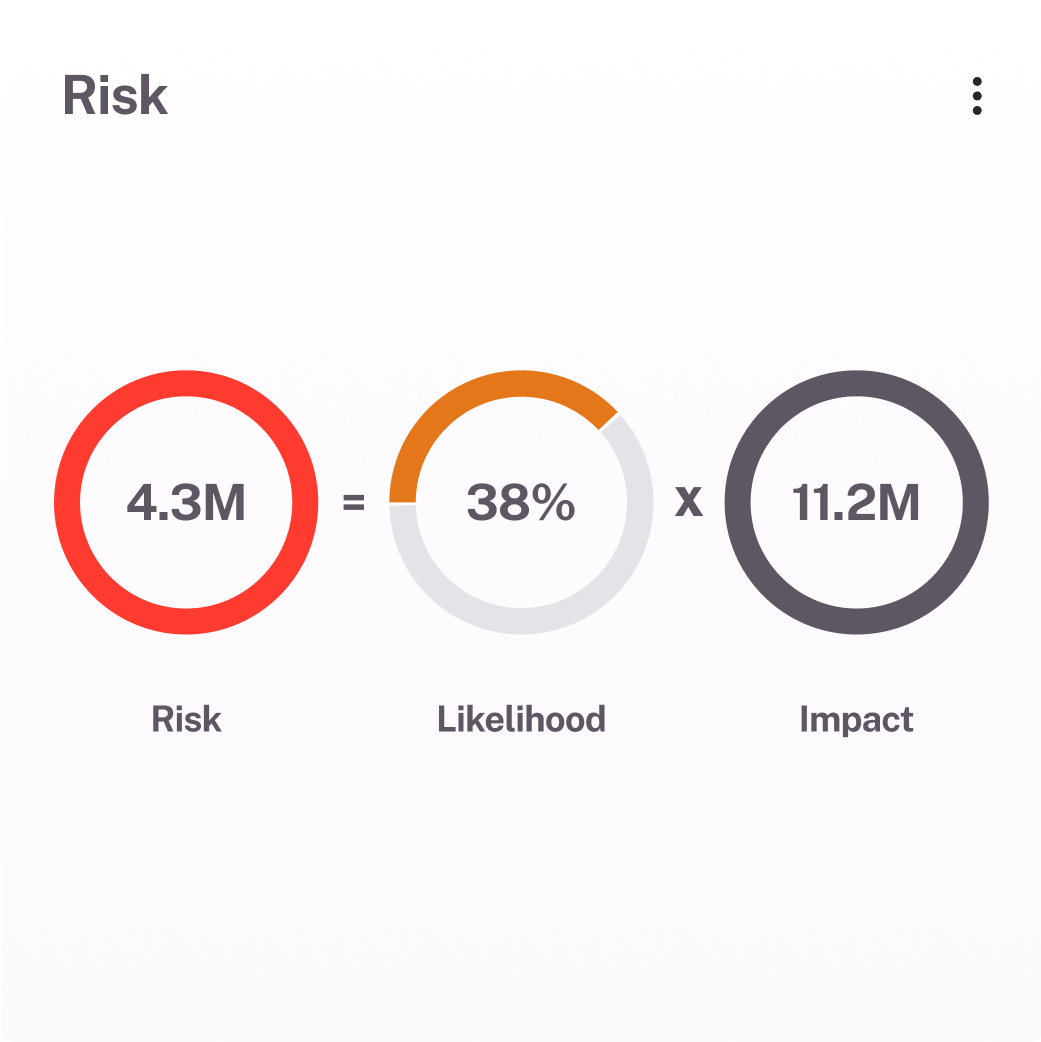
Quantify risk in business terms
Turn exposure gaps into clear financial insights. Understand the potential cost of cyber risk, justify investments, and drive strategic decisions with data that speaks the language of business.
“Balbix shows the ROI of my entire cybersecurity program. We have invested a lot of money and effort in our security initiatives. With Balbix, for the first time, I am able to see the overall effect of the cybersecurity program.”

John Shaffer
CIO, Greenhill & Co.
Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.