Dina Mathers
CISO, Carvana



Continuously calculate financial risk across all assets using live exposure, exploitability, and business impact—no more guesswork.
Translate technical risk into dollars to drive board-level conversations, justify investments, and make informed tradeoffs.
Eliminate manual, error-prone modeling with AI-powered automation— always on, always up to date, always audit-ready.
By significantly improving our security posture with Balbix and quantifying our risks, we were able to secure a 25% reduction in our cyber insurance premium, double our coverage, and unlock more options to increase coverage—options that weren’t available to us before.

Dina Mathers
CISO, Carvana
Quantify cyber risk with precision by integrating real-world data on assets, vulnerabilities, and security controls with breach loss intelligence from external sources.
Break down cyber risk quantification into specific assets and applications, highlighting vulnerabilities and gaps contributing to overall risk. Build trust with measurable, data-backed insights.
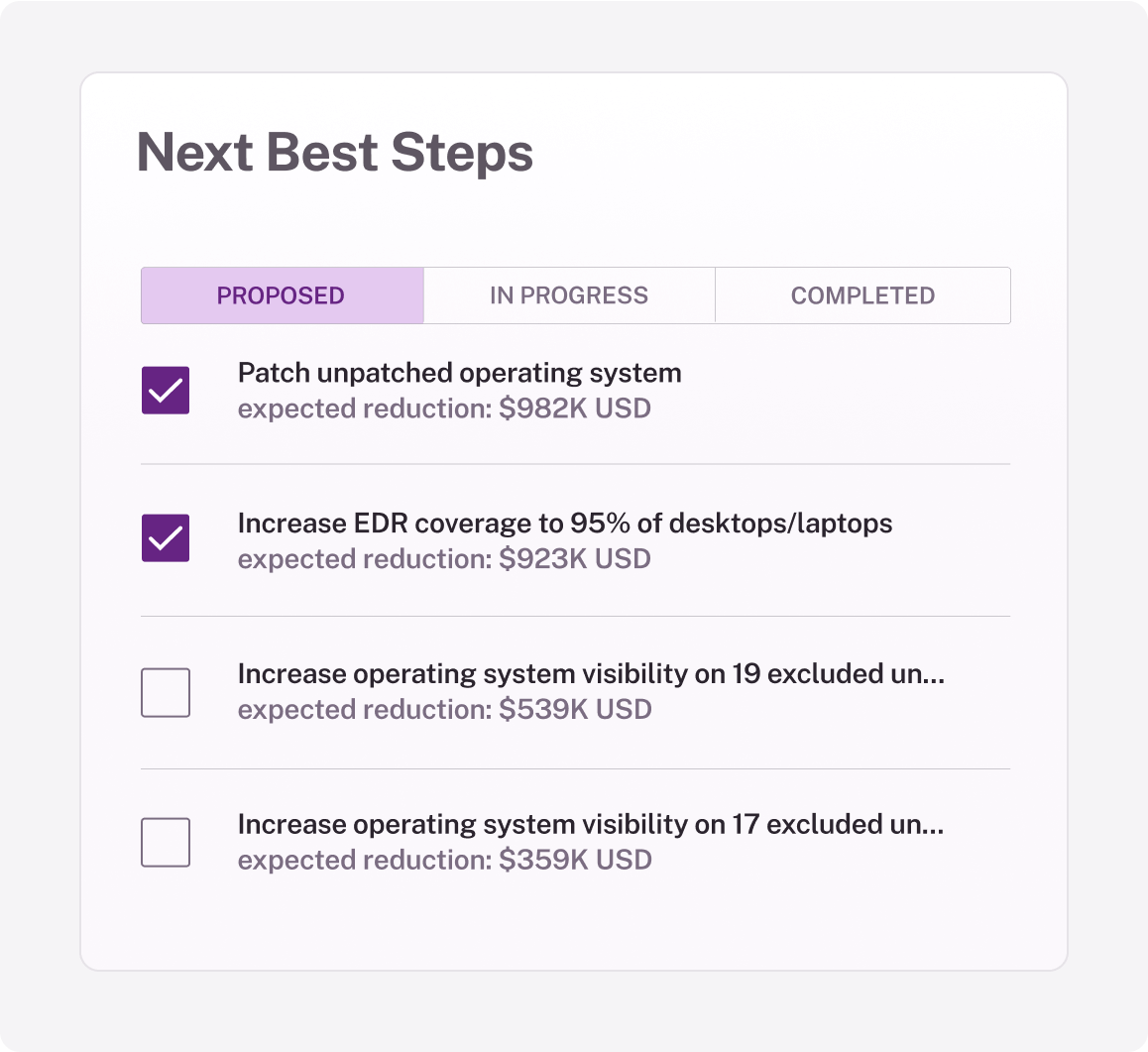
Generate prioritized steps to mitigate cyber risk effectively. Provide measurable outcomes for each action, including risk reduction quantified in monetary terms.
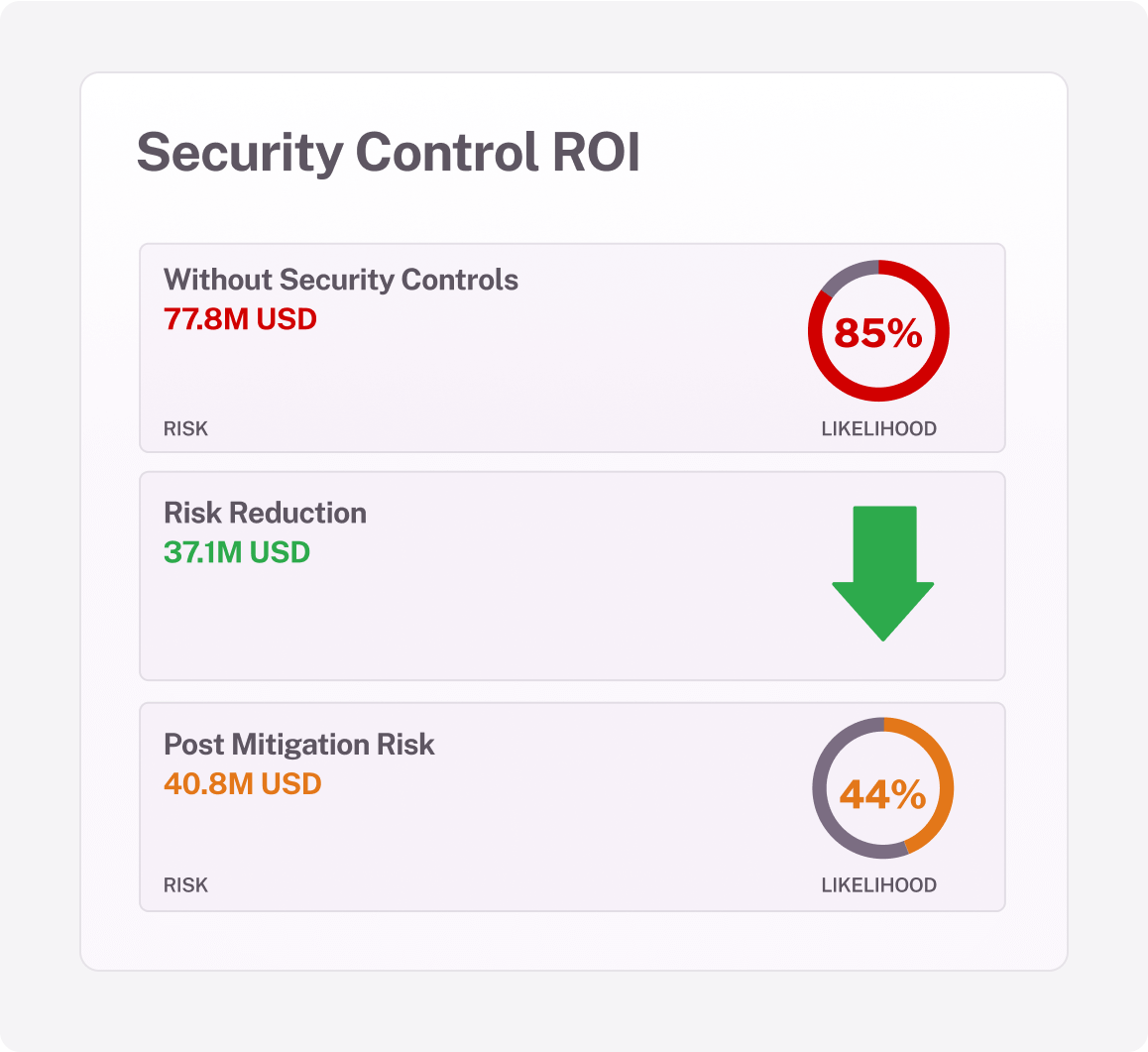
Deliver comprehensive reports on cyber risk quantification, including risk distribution by applications, business units, and ROI of security investments. Visualize inherent, mitigated, and residual cyber risk for informed decision-making.
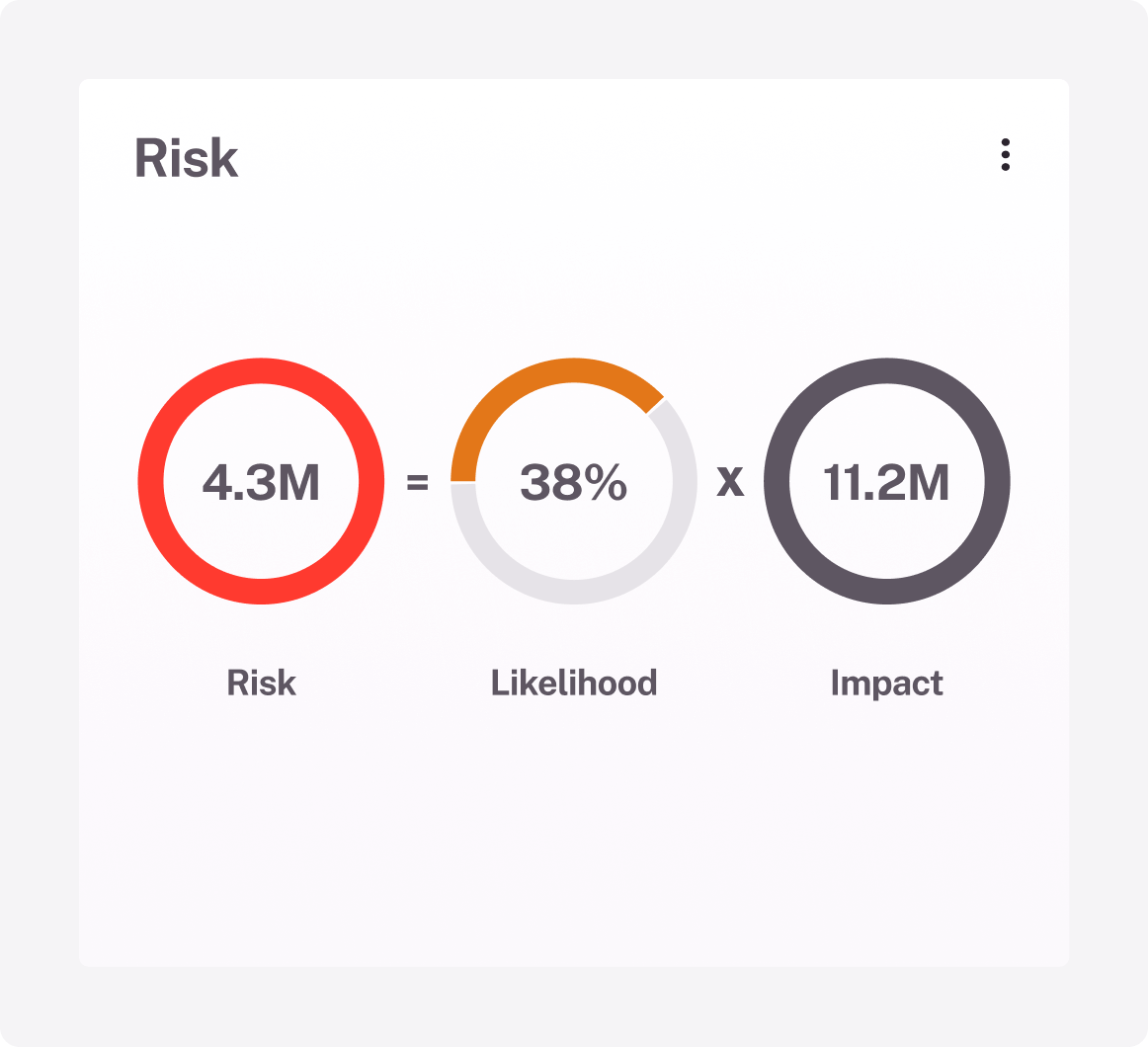
Translate technical risks into monetary terms to effectively communicate with senior executives. Improve alignment between security investments and business goals.
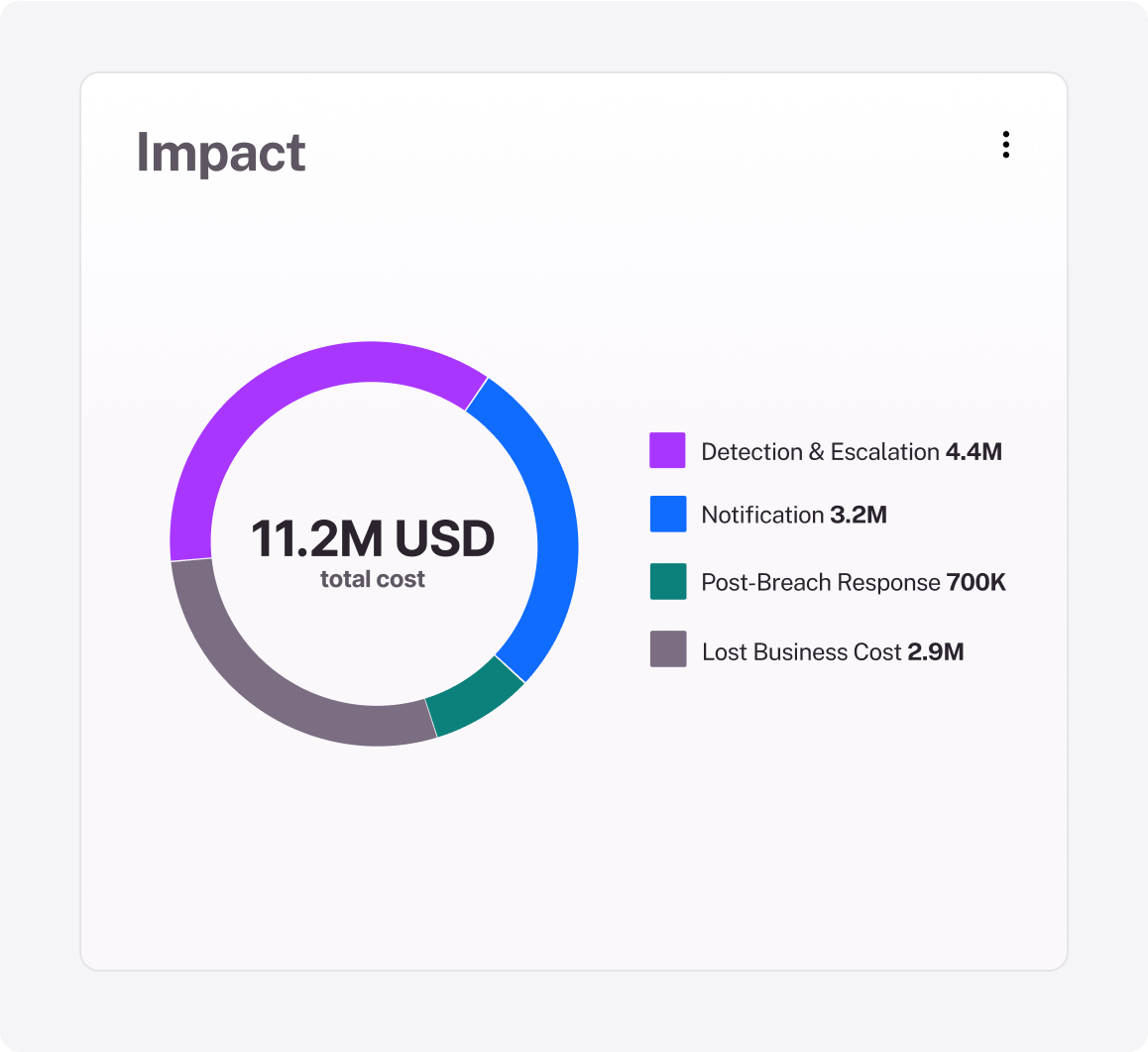
Leverage a quantitative approach to prioritize security initiatives, tools, and tasks, enabling faster and more effective risk reduction.
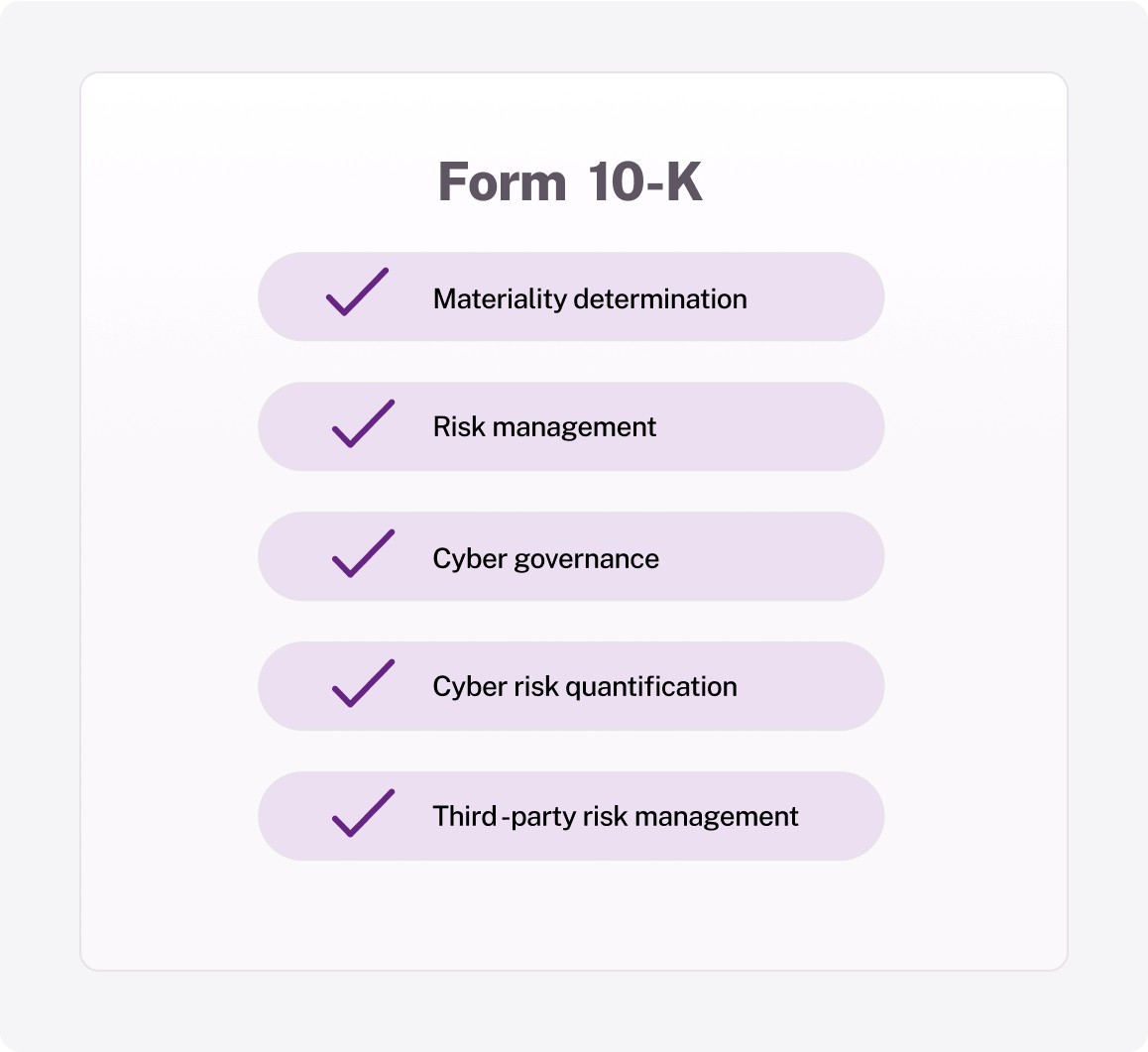
Easily quantify and prioritize material risks to streamline SEC disclosures like 8-K and 10-K filings, demonstrating a robust approach to cyber risk quantification.
Measure the risk reduction impact of security tools and programs. Identify under-performing solutions for consolidation or elimination, lowering costs while improving efficiency.