What is an Attack Surface?
An attack surface refers to the total sum of all potential entry points or vulnerabilities within an organization’s internal and digital systems, networks, and applications where unauthorized access could occur. It encompasses all possible areas where cyber threats can exploit weaknesses, from technical vulnerabilities in software and hardware to human factors like social engineering. Understanding and minimizing the attack surface is essential for reducing the risk of cyberattacks.
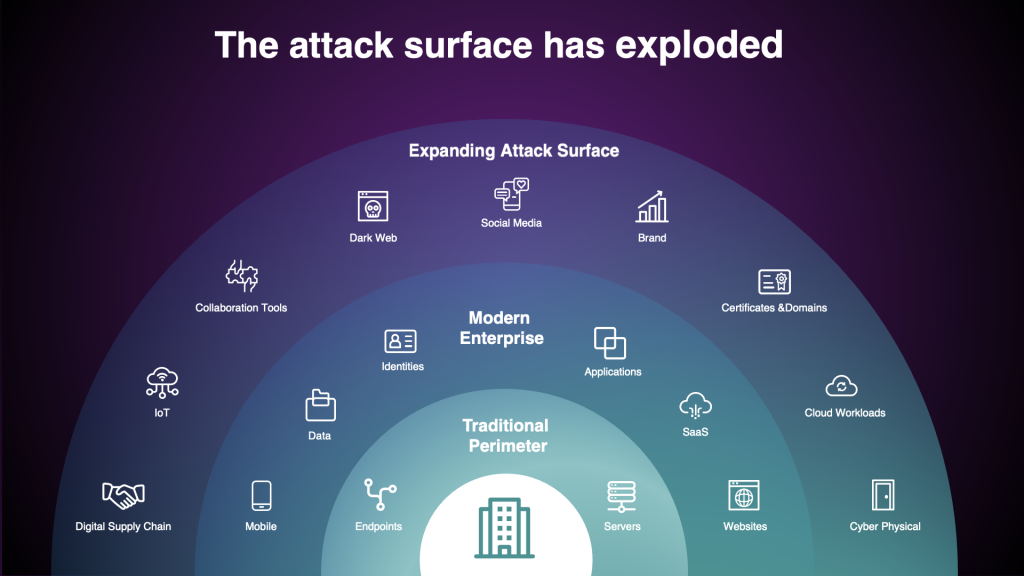
In recent years, the attack surface has exploded in the scope of the volume of assets an organization is responsible for.
Understanding Attack Surfaces
Attack surfaces can be categorized based on asset location—internal (within the organization’s physical network) or external (in the cloud or online). This distinction is crucial for assessing, securing, and managing cybersecurity risks.
Internal Attack Surface
The internal attack surface comprises all resources within the organization’s physical network. If compromised, these assets are vulnerable to attacks that could lead to lateral movement, data exfiltration, or further exploitation.
Examples:
- Infrastructure: Workstations, servers, routers, and storage systems located on-site.
- Operational Technology (OT): Critical infrastructure, including industrial control systems and IoT devices.
- Local Data Centers: On-premises data storage, including backups and archives.
External Attack Surface
The external attack surface includes assets and services outside the organization’s physical boundaries, often managed by third-party providers. These assets are exposed to internet-based threats and are prime targets for external attackers.
Examples:
- Public-Facing Web Applications: Websites, APIs, and other internet-accessible applications.
- Cloud Databases: Cloud-hosted databases or those managed by third-party vendors.
- External API Integrations: APIs that connect internal systems with third-party services.
Cloud Attack Surface
The cloud attack surface encompasses assets and services hosted in cloud environments. Cloud service providers manage these assets and face risks from both internal and external threats.
Examples:
- Cloud Storage Services: Data storage solutions provided by cloud vendors.
- Cloud-based Applications: Software as a Service (SaaS) applications and platforms.
- Cloud Infrastructure: Virtual machines, networks, and other cloud-based resources.
Digital Attack Surface
The digital attack surface includes all online assets not necessarily tied to the cloud but exposed to internet-based threats.
Examples:
- Internet-Accessible Systems: Systems and services accessible via the Internet, including web servers and online platforms.
- Digital Services: Online services and platforms that interact with users or other systems over the internet.
User Attack Surface
The user attack surface refers to vulnerabilities associated with individuals interacting with the organization’s systems, including employees, contractors, vendors, and other privileged users.
Examples:
- User Accounts: Employee, contractor, and vendor accounts with access to organizational systems.
- Authentication Methods: Login credentials, multi-factor authentication (MFA) setups, and access controls.
- User Devices: Personal and work devices individuals use to access organizational resources.
The Threat of Attack Vectors
As we defined, attack surfaces represent all potential entry points that must be defended. Attack surfaces are vulnerable to various attack vectors, which attackers use to exploit vulnerabilities and gain unauthorized access to a network. Securing an enterprise’s extensive attack surface requires continuous monitoring to protect against common attack vectors like compromised credentials, weak authentication, and phishing.
Learn more about attack vectors and how they differ from attack surfaces.
How to Conduct an Attack Surface Analysis
- Create an Asset Inventory
Compile a complete inventory of your organization’s on-prem and cloud assets. Assess each asset’s business impact to determine which ones require the most protection. - Perform an Exposure Assessment
Evaluate your network for vulnerabilities, misconfigurations, and other exposure points attackers could exploit. Use both automated tools and manual methods for a thorough assessment. - Identify and Prioritize Exposures
Prioritize identified exposures based on their threat to critical assets. Consider ease of exploitation and potential financial impact to focus remediation efforts on the most significant risks. - Validate Exposures and Calculate Cyber Risk
Validate identified exposures through methods like penetration testing. Quantify cyber risk by assessing the likelihood of exploitation and potential impact, giving you a clear picture of your security posture. - Mobilize Your IT Team
Engage your IT or asset owners to remediate exposures through security patches, system reconfigurations, and enhanced monitoring. Continuous monitoring and regular reassessments are vital to adapting to evolving threats.
What is Attack Surface Management?
Attack surface management involves continuous processes to mitigate cyber risk, including asset discovery, vulnerability assessments, and penetration testing. It also covers deploying security controls and managing vulnerabilities. The goal is to minimize the likelihood and impact of cyberattacks by continuously monitoring and securing the attack surface and protecting critical assets and data.
How Does Exposure Management Fit In?
Exposure management (EM) is a continuous strategy for identifying, assessing, prioritizing, and mitigating security risks across all assets and applications. EM helps reduce the risk to the attack surface by cataloging CVEs and non-CVE vulnerabilities, evaluating their impact, prioritizing critical risks, and mitigating them.
In summary, Attack Surface Management identifies and monitors vulnerabilities, while Exposure Management assesses and prioritizes them to effectively manage and reduce risk.
9 Ways to Reduce the Risk to Your Attack Surface
Reducing your attack surface is crucial for enhancing your organization’s cybersecurity and protecting critical assets. Implement these ten strategies to minimize potential entry points and strengthen your overall security posture.
- Inventory Attack Surface: Regularly identify and catalog all assets within your network to understand your complete attack surface.
- Risk Prioritization: Assess and rank risks based on their potential impact and likelihood.
- Implement Exposure Management: Focus on a comprehensive risk management strategy like exposure management that considers the entire attack surface.
- Network Segmentation: Divide your network into smaller segments to limit the potential damage of a breach by isolating critical assets and data.
- Implement Zero-Trust: Implement a security model that assumes no user or device, whether inside or outside the network, should be trusted by default.
- Minimize Complexity: Simplify your IT environment by removing unnecessary applications, devices, and features.
- Strong Access Control: Use multi-factor authentication and web application firewalls for strong access control.
- End-User Protection: Protect devices with browser security and Endpoint Detection and Response (EDR) solutions.
- Regularly Patch High-Risk Exposures: Keep software updated with the latest security patches to reduce exposures.
By implementing these strategies, organizations can significantly reduce their attack surface, making it harder for attackers to find and exploit vulnerabilities. Learn more about how an exposure management platform can help you reduce your attack surface risk.
Frequently Asked Questions
- What is the difference between attack surface and vulnerability?
-
An attack surface refers to the points where an attacker can potentially exploit a system, including hardware, software, and network elements. On the other hand, a vulnerability is a specific weakness within that attack surface that could be exploited.
- Why is a person or user considered part of the attack surface?
-
A person or user is part of the attack surface because they can be targeted through social engineering, phishing, or insider threats. Human behavior can unintentionally expose sensitive information or create entry points for attackers.
- Which is the most vulnerable cyberattack surface?
-
The most vulnerable cyberattack surface often varies, but commonly, it includes outdated software and systems, poorly configured networks, and user weaknesses such as weak passwords or social engineering vulnerabilities. These areas are frequently exploited due to their widespread presence and potential for oversight.
- How does cloud computing impact an organization’s attack surface?
-
Cloud computing expands an organization’s attack surface by adding externally managed assets like cloud applications and databases accessible via the Internet. This increases the risk of unauthorized access and cyberattacks. Effective attack surface management in the cloud requires continuous monitoring, secure configurations, and proactive security measures to mitigate these risks.
- What role does cybersecurity automation play in managing the attack surface?
-
Cybersecurity automation is essential for managing the attack surface, as it automates vulnerability detection, analysis, and remediation. Automated tools quickly identify exposures and prioritize risks, reducing manual effort and response time.


