Cyber Risk Quantification (CRQ) calculates risk exposure and its potential financial impact on an organization in business-relevant terms, providing a way for organizations to drive alignment between security strategy and business objectives. This has changed conversations around cyber security posture from the data center to the boardroom, enabling improved cyber risk decision-making at the executive level.
Why is Cyber Risk Quantification Important?
Cyber Risk Quantification (CRQ) is the process of assessing and calculating the potential financial impact of cyber threats on an organization. It translates cybersecurity risks into business-relevant terms, allowing organizations to understand the monetary value of their risk exposure.
CRQ aligns security strategies with business objectives by providing a clear, data-driven understanding of which risks to prioritize based on their potential financial impact. This approach enables organizations to make informed decisions about where to allocate resources, ensuring that cybersecurity efforts are strategic and cost-effective.
How do you Quantify Cyber Risk?
Cyber Risk Quantification allows you to quantify cyber risk in monetary terms so that your business leaders, CFO, CEO, and board can assess your organization’s cyber risk in dollars (and other currencies). Calculating cyber risk in monetary terms provides a common language that you and your leadership and stakeholders can use to prioritize projects and spending and track the effectiveness of your overall cyber resilience program.
A meaningful way to calculate cyber risk is by determining the expected loss or business impact of a cyberattack or breach.
To obtain a quantifiable measure of risk, underlying breach risk is calculated on a per-asset and per-vulnerability basis:
breach risk = breach likelihood x breach impact
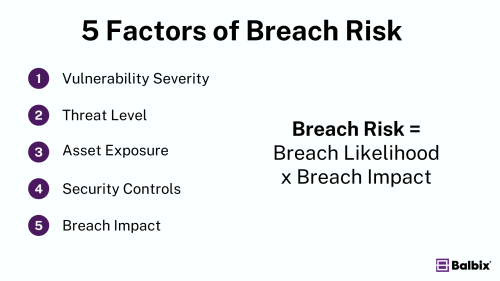
Breach Risk
Breach risk considers five critical factors. The first four factors are used to calculate breach likelihood:
- Vulnerability Severity: How critical the vulnerabilities in the system are.
- Threat Level: The likelihood of those vulnerabilities being exploited.
- Asset Exposure: How accessible and exposed the assets are to threats.
- Security Controls: The effectiveness of the current security measures in place.
Breach Impact
The fourth critical factor is Breach Impact, which assesses the business consequences of a successful cyberattack.
Breach Impact includes:
- Detection and Escalation Costs: The resources needed to detect and address the breach.
- Notification Costs: The expenses associated with notifying stakeholders and regulators.
- Post-Breach Response Costs: Expenses related to remediation efforts and regulatory fines.
- Lost Business Costs: Revenue losses due to downtime, damaged reputation, or stolen intellectual property.
The breach risk calculation provides an estimated financial impact of a cyber breach, representing the potential cost to the organization if such an event occurs. This value quantifies the risk in business terms, allowing your leadership to understand a breach’s financial implications and prioritize resources accordingly.
Using Automation and AI to Understand Your Attack Surface
Cyber risk calculation should account for most of the attack surface, which is only possible with automation and AI. Due to the number of attack vectors and assets, an attack surface for a large enterprise can be massive.
In addition, the attack surface expands and continuously changes as an organization grows. Understanding the attack surface ensures a more accurate risk score and provides security teams with the detailed remediation guidance they need to reduce risk.
Determining the Business Significance of Each Asset
The risk calculation should understand the business significance of each asset as it is an important variable in determining breach impact. For example, your breach impact is significantly higher for core servers containing sensitive data than personal smartphones sequestered on your guest network. Attacking your company’s source code repositories will likely have a more significant impact than the guest sign-in kiosks in your building lobby.
While assessing an asset’s business criticality, you must consider inherent (e.g., asset category, business unit) and contextual properties (e.g., roles, applications, user privilege, and interaction with other assets). A cyber risk quantification solution with integrated asset inventory powered by automation and AI reduces errors and costs.
What are the benefits of Cyber Risk Quantification?
Quantifying cyber risk offers several key benefits:
- Optimizes Resource and Budget Allocation: By measuring risk reduction for specific tools and programs, CISOs can consolidate or decommission tools that do not provide expected ROI and enable you to focus your resources where they’ll have the most impact.
- Prioritizes Risk Management: Identify and address the most significant risks first.
- Enhanced Communication: With monetary measures for cyber risk, CISOs can improve communications and credibility with senior executives and better align security budgets with risk.
- Tracks Performance: Monitor and measure the effectiveness of your cybersecurity programs.
- Rapidly Lower Cyber Risk: Security teams can lower risk with actionable recommendations that specify specific programs, tools, and tasks based on business context.
- Identify Material Risks: Using a quantitative approach to identify material risks, CISOs can quickly establish materiality for disclosures to the SEC, DORA and other governing bodies.
With Cyber Risk Quantification, your organization can answer critical questions such as:
- What is my organization’s cyber risk exposure in monetary terms, and how do I calculate it?
- What is the effectiveness of my security investments, and how can I justify my cybersecurity spending?
- How can I quickly prioritize remediation efforts to address cyber risks with the highest business impact?
- How do I effectively report the cyber risk exposure to senior management and the Board? How do I better partner with business risk owners to operationalize risk reduction?
What are the Challenges of Quantifying Cyber Risk?
Cyber risk quantification is crucial for organizations, but calculating risk comes with several challenges:
Data Doesn’t Equal Visibility
While organizations may have numerous data-gathering tools, using this information to identify risk indicators is often difficult and time-consuming. Many organizations also face gaps in their asset inventory, which hamper accurate risk assessments and limits understanding of vulnerabilities and the effectiveness of security tools.
Organizations struggle to analyze attack types, frequency, and severity without comprehensive data. Required data is often available but too dynamic and time-consuming to process manually and effectively.
Difficulty in Calculating Risk
Unifying disparate data into a common risk model can be challenging. Different tools use varying formats and semantics for asset or user attributes, often leading to conflicting information. Additionally, various stakeholders may use different terminology, making it difficult to standardize risk metrics and communicate effectively.
Partial Remediation
The emergence of new vulnerabilities makes it hard to quickly identify, prioritize, and remediate risks that would impact your organization most if exploited. A lack of real-time visibility into the attack surface makes it challenging for security teams to stay ahead of threats. Organizations struggle to respond to risks quickly and comprehensively without automated, continuous monitoring.
Best Practices for Cyber Risk Quantification
Effective cyber risk quantification is crucial for assessing and managing the potential financial impacts of cyber threats. Here are several best practices to consider:
- Strengthen cyber resilience by leveraging up-to-date and accurate data, identifying and protecting key assets, and performing thorough security risk assessments.
- Prioritize risks based on their potential financial implications and communicate these findings in financial terms to both technical and non-technical stakeholders.
- Regularly update your risk assessments and vulnerability checks to stay ahead of threats.
- Incorporate an incident response plan for efficient issue remediation.
- For more accurate risk calculations, utilize advanced analytics, including AI and machine learning.
- Lastly, continuously measure the effectiveness of your risk mitigation strategies to ensure ongoing improvement in your cybersecurity efforts.
How Balbix Helps
Balbix empowers stakeholders with real-time, customizable business reports through dynamic risk dashboards. These dashboards are continuously updated based on the latest asset information and vulnerability data, reflecting your evolving cybersecurity posture.
Trend reports allow leadership to monitor breach risk over various periods—such as 90 days, 6 months, or year over year—helping them track progress towards improved cyber resilience.
Stakeholders can view cyber risk data by business units, sites, risk owners, assets, attack vectors, and specific CVEs. All are quantified in financial terms, enabling leadership to quickly identify which business units or processes contribute the most risk to the organization.
How Can Cyber Risk Quantification Justify Security Investments?
Cyber Risk Quantification provides a data-driven approach to rationalizing cybersecurity budgets and investments. By quantifying cyber risk in monetary terms, security leaders can effectively track the ROI of their security programs and justify the costs of cybersecurity initiatives. For example, you can demonstrate how investments in endpoint security controls reduce breach risk, clearly showing their impact in financial terms.
This quantitative approach enables organizations to prioritize cyber risks, communicate effectively with executive leadership and the board, and make informed decisions about mitigation strategies and security investments based on financial outcomes.
Frequently Asked Questions
- How does Cyber Risk Quantification (CRQ) integrate with existing cybersecurity strategies in an organization?
-
Cyber Risk Quantification (CRQ) complements existing cybersecurity strategies by providing a financial metric for cyber risk. This allows organizations to make informed decisions about where to allocate resources for maximum impact. CRQ integrates with risk management frameworks to prioritize threats and vulnerabilities based on their potential financial impact, facilitating a strategic approach to cybersecurity investments.
- Can CRQ be applied to organizations of all sizes, or is it more suitable for large enterprises with complex systems?
-
CRQ is versatile and can be applied to organizations of any size. While it’s particularly beneficial for large enterprises with complex systems due to their higher risk exposure, small and mid-sized businesses with fewer resources can leverage CRQ to understand their risk landscape and make informed cybersecurity investments, enhancing their overall security posture.
- What are some of the specific tools or software solutions used in CRQ to assess and quantify cyber risk?
-
Tools and software solutions used in CRQ include risk assessment platforms that utilize algorithms and statistical models to quantify cyber risk in monetary terms. These tools often incorporate threat intelligence, vulnerability data, and business context to assess risk levels accurately.
- In the context of CRQ, how is an organization's attack surface accurately defined and measured, especially with automation and AI?
-
Accurately defining and measuring an organization’s attack surface in the context of CRQ involves identifying all potential points of vulnerability that attackers could exploit. This includes digital assets, physical assets, and personnel. Including automation and AI in CRQ helps tools dynamically map and assess the attack surface, considering the evolving nature of cyber threats and the organization’s expanding attack surface.