This is post 9 in our series on making infosec jobs easier. Today we are covering the job of responding to cybersecurity incidents. You can read the previous 8 posts at one of the links below.
- Improve overall security posture
- Assess and report on breach risk
- Keep systems patched
- How to adjust to changes in the IT landscape
- Prevent data loss and fraud
- Threat Hunting
- Cybersecurity Governance
- Preventing ransomware
Responding to cybersecurity incidents
Incident response is the systematic approach taken by an organization to prepare for, detect, contain, and recover from a suspected cybersecurity breach. Preparing an incident response plan is an essential job of the infosec team which helps ensure an orderly and effective response to breach incidents. An effective plan can have tremendous bearing on the ultimate impact of the incident, however, a recent study showed that 77% of organizations lack a cybersecurity incident response plan.
This is concerning, as slow and uncoordinated responses to breaches result in regulatory fines, loss of customer trust and brand reputation, and business operations downtime. Moreover, on average, companies take about 197 days to identify and 69 days to contain a breach according to the 2020 Cost of Data Breach study, which only adds to the problems at hand.
According to the NIST Computer Security Incident Handling Guide, a standard framework for Incident Response plans, there are four key phases to plan around.
- Preparation
- Detection and analysis
- Containment and eradication
- Post-incident recovery
Preparation
This is perhaps the most important phase which stresses the importance of taking proactive action so you can avoid cybersecurity incidents in the first place. Preparation starts with having a baseline inventory of all assets, especially critical system files so you know what is on your network and can identify changes to these immediately.
For example, the Balbix dashboard below can be used as a baseline to know all your IT asset inventory categorized by asset type and location.
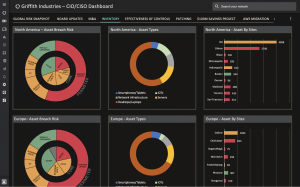
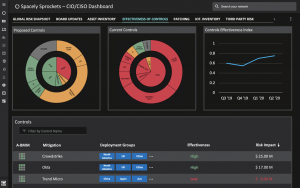
Another key aspect of preparation is understanding the effectiveness of your existing security controls. Balbix can help you understand that using dashboards such as this:
Detection and analysis
This stage refers to the readiness of an organization to quickly detect indicators of compromise (IOCs) by having appropriate systems and controls in place that identify breach events.
Such identifiers of Indicators of Compromise include:
- Unusual outbound network traffic
- New admin users created
- Anomalies in privileged user account activity such as first time logging on to a system
- Geographical irregularities like non-standard login attempts
- Large numbers of request for the same file
- Suspicious registry or system file changes
- Unexpected patching
- Signs of DDoS activity
However, keeping track of indicators of compromise is easier said than done as organizations
of all sizes struggle with the daily volume of alerts produced by their security controls, which often exceed the capacity of their security teams. It is not uncommon for a SIEM in a medium-sized organization to produce hundreds of security alerts each day. Each trained SOC analyst can typically handle 4-6 alerts daily with manual methods. Therefore, managing and acting upon daily security events while factoring in relevant business criticality information requires a level of resourcing impossible for most businesses.
The Balbix platform helps address this challenge by automatically ingesting indicators of compromise data from SIEM tools, such as Splunk and LogRhythm, and applies deep context around business criticality, analysis of external threats and local knowledge of unresolved vulnerabilities to greatly improve the quality of mitigation actions.
Besides providing context for tactical event handling, Balbix also provides a list of strategic actions to minimize ongoing risk from IOCs and improve cyber-resilience.
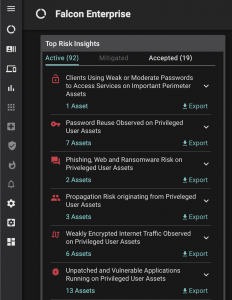
Containment and eradication
Once you have rock solid plans in place for the above two phases and are confident that a potential cybersecurity incident can/will be identified, you can turn your focus to strategizing on containing potential incidents. A prudent plan involves defining courses of action based on the potential impact of various incidents. Eradication refers to completely eliminating the cause, the actual incident and the compromise itself. Once this is done, it’s imperative that the eradication is verified (e.g. by monitoring traffic and reviewing critical logs).
Typical eradication steps include:
- Removing the attack from the network
- Deleting malware
- Disabling breached user accounts
- Identifying vulnerabilities that were exploited
- Mitigating vulnerabilities that were exploited
Post incident recovery
A detailed recovery plan should be prepared and reviewed to determine that all recovery processes are carried out to ensure the restoration of the system as soon as possible, such as restoring the system from back-up logs, notifying the relevant stakeholders and addressing similar identified vulnerabilities on the network. The restore phase must also consider validating that systems are back to being fully operational and protected.
Although it is not possible to fully prepare for unknown future incidents, there are elements of an Incident Response process which require preparation to allow effective incident mitigation.
Risk-based cybersecurity strategies are at the top of many CISOs’ priority lists. They allow for an organization to proactively identify cybersecurity risks, mitigating the most important ones first.
Balbix can help you baseline your cybersecurity posture in real-time and continuously keep track of the effectiveness of your existing security controls to know where the gaps are and where you need to invest more budget. Balbix also enables security teams to get prioritized risk insights to know clearly which security issues to address first.
Reach out to us and get a 30 min demo of the platform to see how Balbix can help.
