About 6 months back, I entered the office to see the words “How can we help make your job easier?” written in bold letters on the giant whiteboard. “Is this a new program from HR?”, I thought to myself, but it soon became clear. This was a call to action from our leadership team on how we could make our customers’ daily jobs easier and more efficient.
The raison d’etre of the cybersecurity function in an organization is to keep the enterprise, it’s data, infrastructure, and technology systems, safe. The CISO is the guardian of the cybersecurity function and to best protect the enterprise from breaches, the CISO and the overall cybersecurity program have to perform a set of “jobs” on an ongoing basis. These jobs are not granular-level tasks, but higher-level responsibilities.
We polled a number of CISOs and asked them this question, “What are the top jobs that your team needs to do on a daily basis?” As you’re probably already well aware, there are a lot of jobs for your team to stay on top of in order to protect the enterprise:
In this 7-part blog series, we will address several of the most important jobs that your team needs to get done, helping you pinpoint inefficiencies, and offer strategies for accomplishing them effectively. These are:
- Assess and report on breach risk
- Keep systems patched
- Prevent data loss and fraud
- Adjust to changes in IT landscape
- Govern your cybersecurity program
- Proactively hunt for threats
- Respond to cybersecurity incidents
All of these jobs roll up under the cybersecurity “uber” job, improving overall cybersecurity posture.
Improving overall security posture
Around 16 billion records have been exposed in the first half of 2020, out of which 8.4 billion records were exposed in the first quarter alone, a 273% increase from the first half of 2019 which saw “only” 4.1 billion exposed. That is a sobering statistic. CISOs and security teams are overwhelmed by the challenge of how to maintain and optimize their security posture and only 1 in 3 say that they are confident that they can avoid breaches.
While there is more awareness amongst top leadership and board members on cybersecurity, the perspective that cybersecurity is just another risk item persists. The board really only has three questions about cybersecurity posture:
- First, they want to know where the organization is on the cyber-risk spectrum.
- Then, they want to know where the organization should be? They rely on the security
team to come up with that recommendation. - And if the organization is not where it should be, they want to know the
plan to get there.
Your board and senior management rely on the security team to know the answers to these questions. Unfortunately, while these questions look deceptively simple, they are very hard to answer.
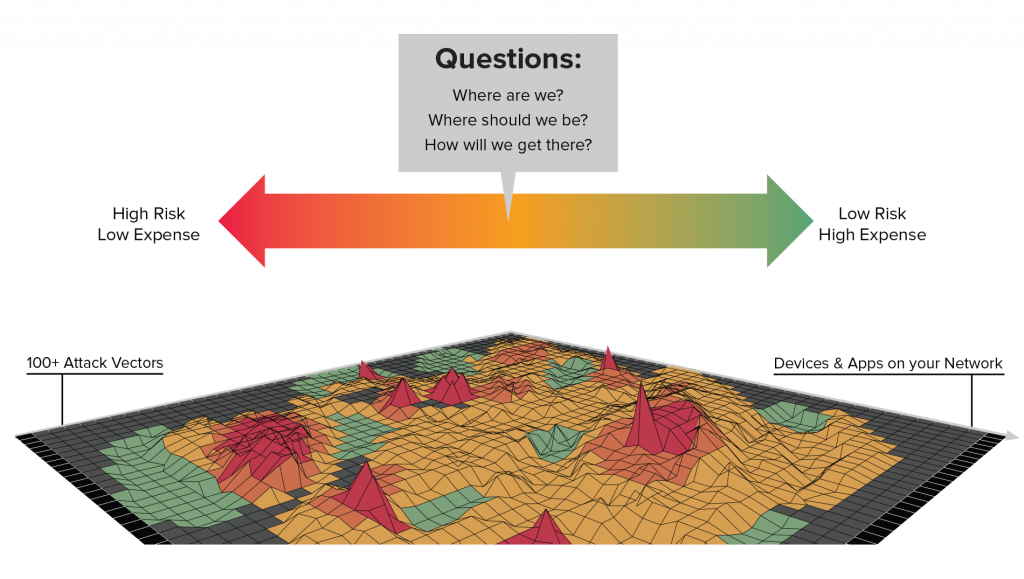
The starting point
At the very core of understanding your security posture is an accurate inventory of all your assets, including both core and perimeter assets. This includes on-premises, cloud, mobile, and 3rd party assets; managed and unmanaged assets; applications and infrastructure, catalogued based on geographic location. It is important to understand the business criticality of each asset as well, as this is an important component of calculating breach risk.
Following that, you must enumerate the existing security controls deployed to manage your defenses. Inherent in this enumeration is also an understanding of how effective these controls are in reducing your cyber risk.
You then need to understand the hundreds of attack vectors that could allow adversaries to infiltrate your network. Attack vectors take many different forms, ranging from malware and ransomware to man-in-the-middle attacks, compromised credentials, and phishing. Some attack vectors target weaknesses in your security and overall infrastructure, others target weaknesses in the humans that have access to your network.
Your attack surface is represented by all of the points on your network where an adversary can attempt to gain entry to your information systems. For a medium to large-sized enterprise, the attack surface can be gigantic.
Hundreds of thousands of assets potentially targeted by hundreds of attack vectors can mean that your attack surface is made up of tens of millions to hundreds of billions of signals that must be monitored at all times.
Warning: speed bumps ahead
The path to understanding and optimizing your security posture is fraught with challenges since the job of improving security posture is dependent on efficient progress towards all the other jobs that roll up to it.
- There is a significant gap between the business level view of the organization and the IT/security level view, which makes it difficult to align plans with business goals. Mechanisms for asset inventory of the organization are not up to date, require manual effort, and offer an incomplete picture, missing several types of IT assets like cloud, mobile, and IoT.
- There is no easy and systematic way to map business constructs, e.g., factories, business units, profit, and expense to IT/cybersecurity constructs like assets, patch state, security configuration, risk of phishing, password hygiene, etc.
- It is tough to prioritize effectively because there are too many signals to monitor for overall risk with no easy way to tell which methods would be most effective for risk reduction.
- There is a lack of data or tools to show internal and external benchmarks for breach risk handling and how they trend over time.
- You don’t have the reporting framework that can generate different types of reports appropriate for various scenarios and audiences.
- There is a lack of a systematic way to prioritize and fix non-patching related vulnerabilities including those related to passwords, phishing, misconfiguration, encryption, malicious insider, attach propagation, or lateral movement of adversary once inside the network.
- There is an explosion in the number of point products that have been deployed for various parts of the attack surface, and there is no way of understanding the effectiveness of all those tools.
- The various tools are not integrated together so you have a number of places and reports to scan through to get a picture of your security posture and getting all these tools to work together is very complex and resource-intensive.
- Automation of key tasks is missing.
- There are not enough people on your team to get all the things done!
If you were to organize all these into a “heatmap” for this job and color code it to see what’s working well, what’s automated, and what is not working, it would look like this.
Needed: a system of record, experience, and intelligence
Imagine if you had a system of record for your security team. This would enable you to understand your inventory including asset criticality, to know what CVEs are open, what your other risk items are, and which compensating controls are effective.
On top of that, if you had a system of Intelligence which enabled you to analyze all of the above on a continuous, real-time basis to prioritize the most important tasks.
And then, add in a system of experience that provides workflows, notifications, dashboards, and reports you need in order to do your job(s) well. That’s the Balbix platform, in a nutshell.
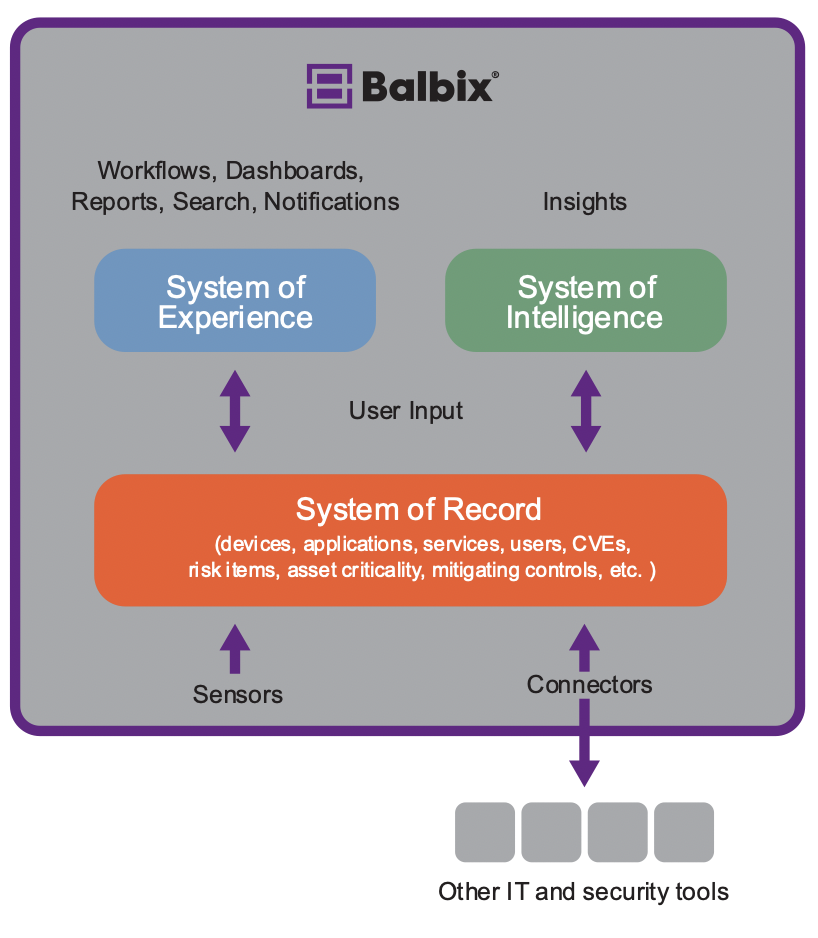
The Balbix platform uses specialized AI algorithms to discover and analyze the enterprise attack surface to enable a broad set of vulnerability and risk management use cases that help to improve your enterprise cybersecurity posture. Balbix offers:
- Continuous and automatic discovery of IT assets and monitoring across 100+ attack vectors.
- Comprehensive coverage of all asset types (on-prem, cloud, IoT, mobile, managed, and unmanaged) and all attack vectors.
- Discovery of mitigation/compensating controls to understand the effectiveness of your cybersecurity program.
- Calculation and financial quantification of risk using 5 factors – vulnerabilities, threats, asset exposure, business criticality, and compensating controls.
- A prioritized set of actions that you can take to transform your cybersecurity posture and reduce cyber risk by 95% or more while making your security team 10x more efficient.
- Visibility into overall cybersecurity posture including risk heatmaps by owners, sites, business units.
- Dashboard and workflows for various tasks necessary for cybersecurity posture transformation and reports for various stakeholders to indicate state/progress of risk management.
- APIs to enable other security tools to take advantage of risk context.
- Gamification to drive all stakeholders to do their part in improving cybersecurity posture.
With an AI-powered platform like Balbix that provides a singular source of truth for all your security posture programs, iteratively analyzing and improving your security posture to the point of transformation is now within reach of enterprise CISOs. Schedule a demo to learn more about the platform and see how you can use it to discover and address your unique security posture challenges.
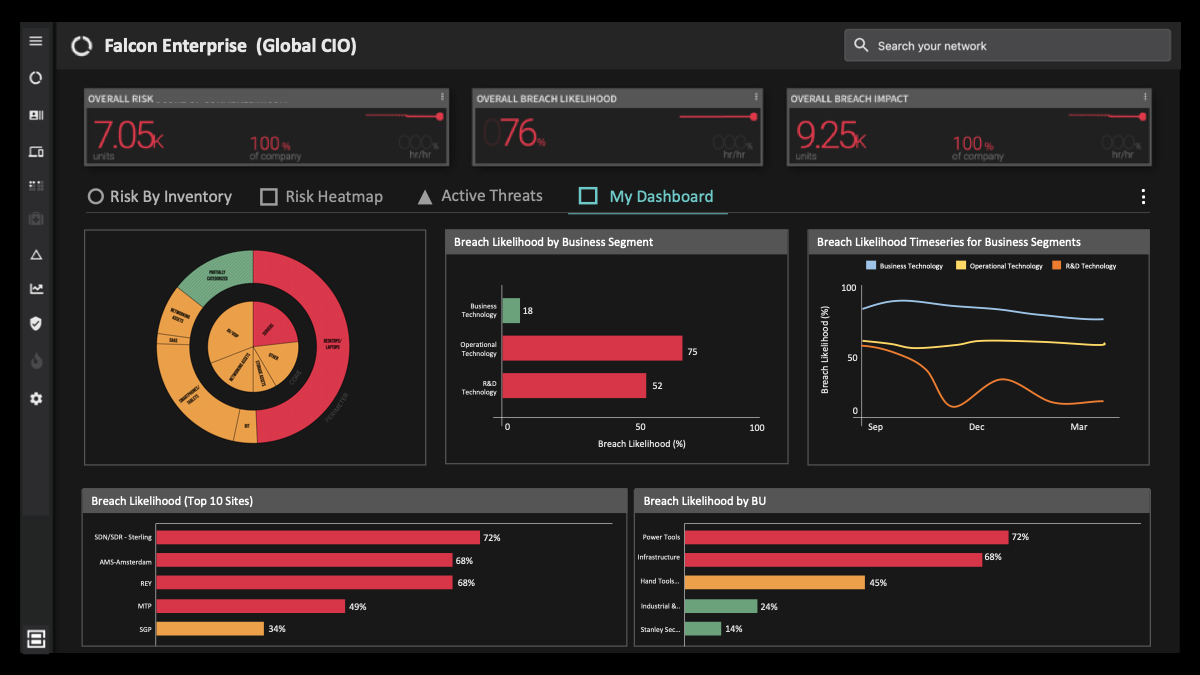
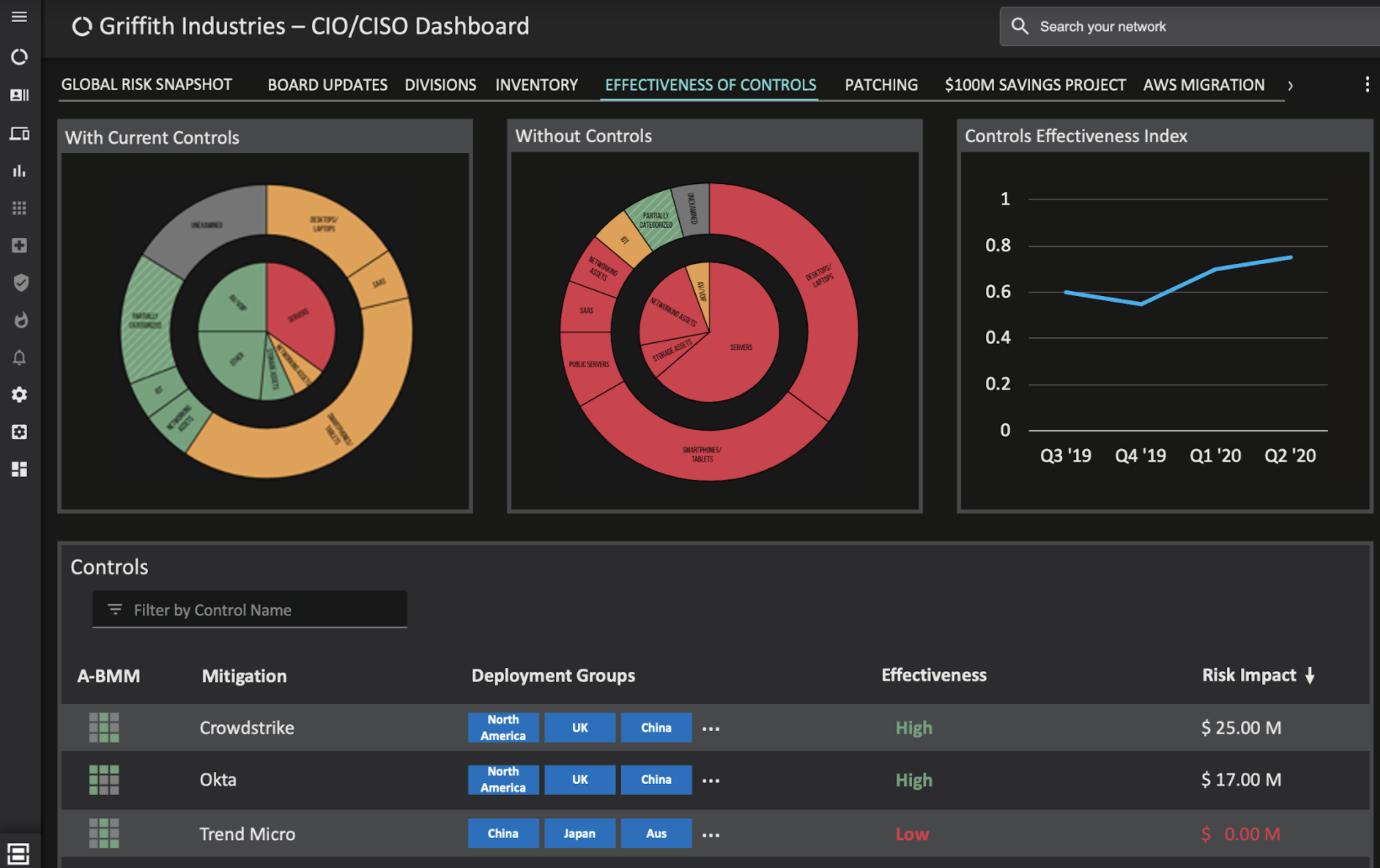
Check out some of our custom dashboards that you can use to improve security posture below.
Dashboard showing the effectiveness of your security controls.
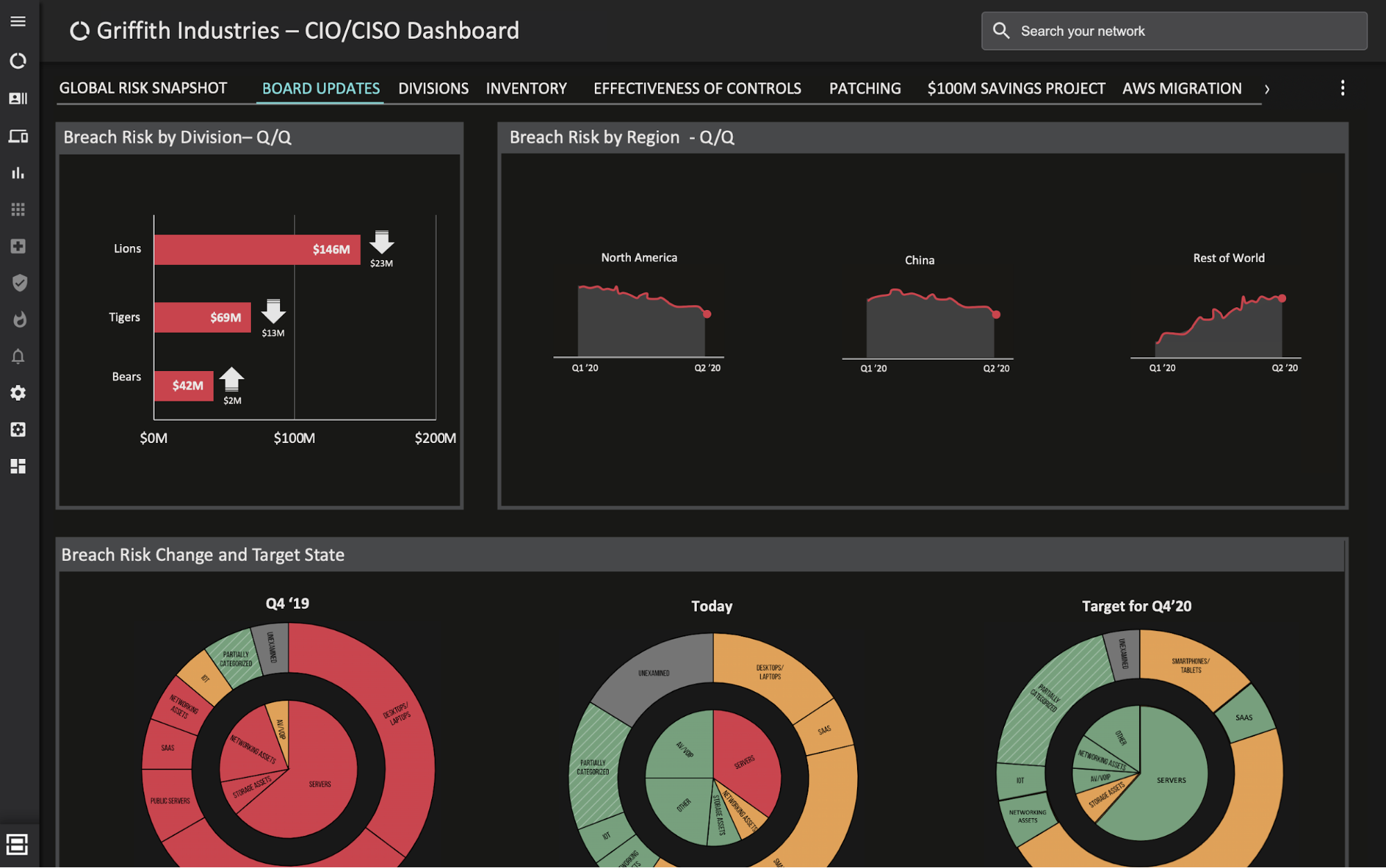
Dashboard that can be used for board updates showing breach risk by division and region and changes over time.
Dashboard showing critical KPIs for improving security posture.