When NASA and SpaceX successfully launched the Crew Dragon capsule atop a Falcon 9 rocket, docking it with the International Space Station, it provided a much needed moment of optimism and positivity in an otherwise fractured and frightening time for our society. It also provided a glimpse into the technological progress in the 9 years since the last Space Shuttle mission.
Improved controls and overall user experience has made the astronauts’ jobs easier and more predictable, while also acting as the most visible aspect of a nearly 100x decrease in costs to bring a payload to orbit. At Balbix, we’ve challenged ourselves to a similar mission. Can we make the daily lives of our customers much easier, while also transforming their cybersecurity posture and dramatically reducing breach risk?
I’m happy to announce that our team has stepped up to the challenge, delivering on both fronts, with much more to come.
The Cockpit: Making Jobs Easier
One set of pictures making their rounds on social media compares the cockpit controls of the Shuttle to those in the Crew Dragon.

Dizzying arrays of switches and screens have been replaced with two simple touchscreen displays. The result of such simplification is a stressful job made easier. Fewer controls mean less chance of human error, and more time focused on the strategic task at hand.
Design and usability has made a similar impact on enterprise software in the last 10 years as well. Software vendors have realized that customers are happiest when they have the right information and the right controls at the right time.
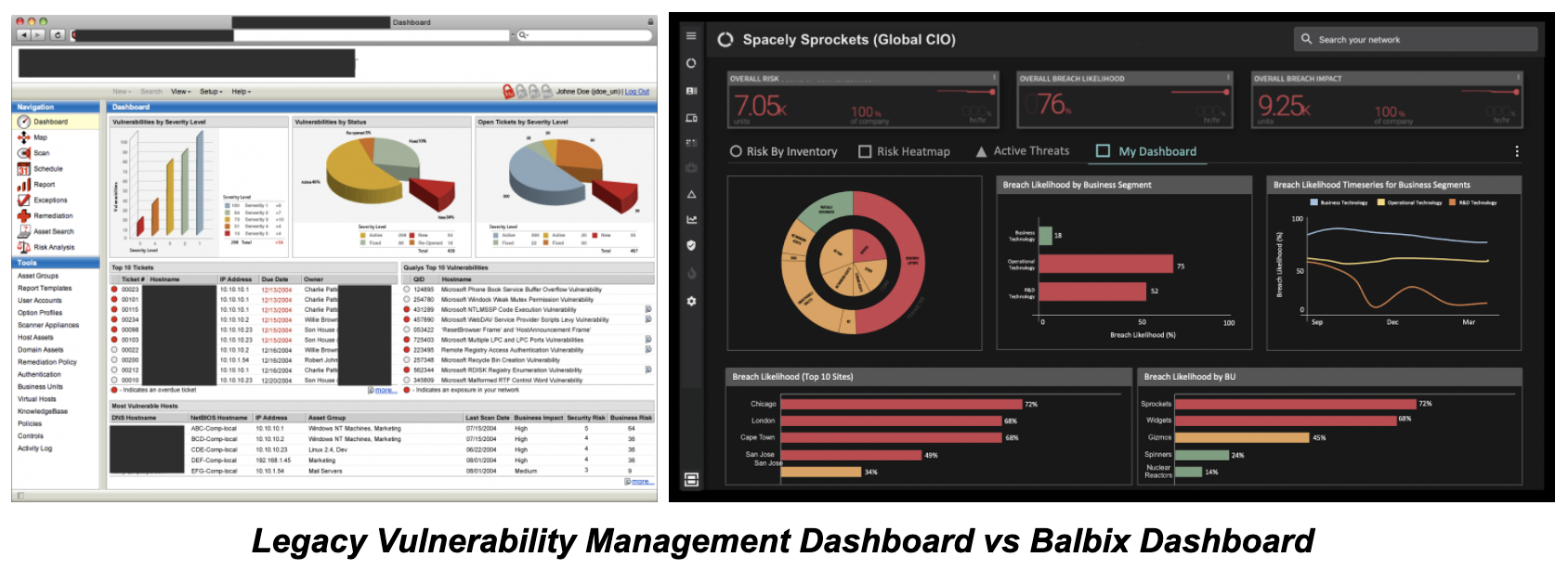
The Payload: 100x Efficiency Improvements
While the user interface, whether it’s a cockpit or a piece of software, is typically the most visible symbol of technological progress, there is often equally revolutionary change that has happened “under the hood.”
The image below shows the costs of getting a payload to Low Earth Orbit (LEO) between the original Space Shuttle mission in 1981, through to today.
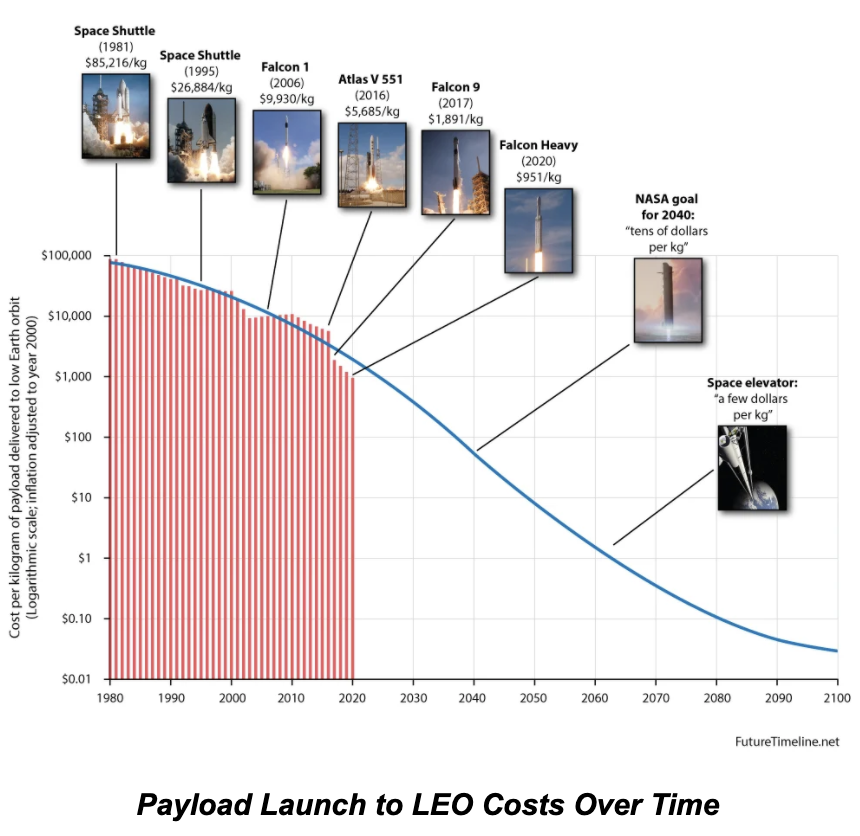
The numbers are striking. Along with better designed flight control software, the cost of sending a payload to space has been reduced by two orders of magnitude.
From the beginning, such transformational change has been our goal at Balbix. Everyday, we ask ourselves, “How can we make the jobs of our customers simpler and less stressful, while simultaneously transforming the economics of infosec programs?”
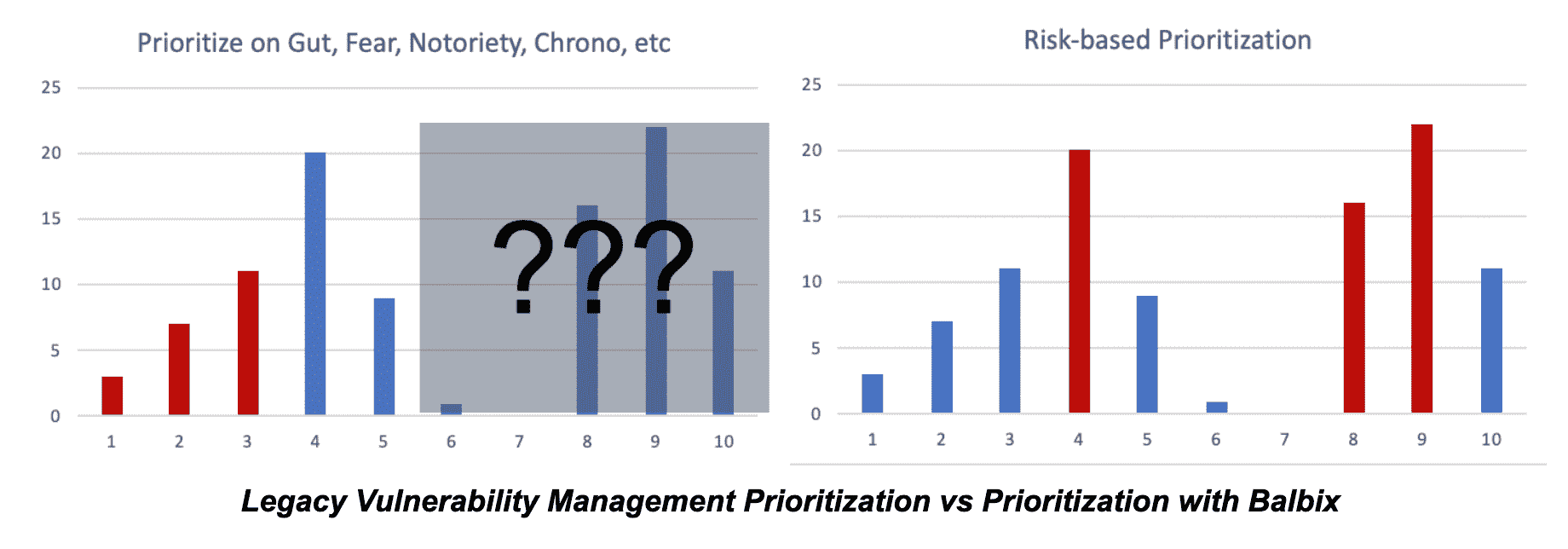
One such example is our easy-to-use, comprehensive approach to risk assessment and prioritization. The charts below show the difference between the “traditional” approach of vulnerability management programs, which relies on gut instinct, fear, arbitrary severity scores, chronological order, etc., as compared to comprehensive, risk-based prioritization from Balbix. In this new approach, infosec teams prioritize the riskiest issues first, across all risks to the business, not just unpatched software and misconfigurations.
The Eagle Has Landed
Over the last year, we have spent a lot of time understanding the nitty gritty details of the various “jobs” that you and your colleagues are trying to do, and the specific obstacles you encounter while doing these jobs. These include, but are not limited to:
- CISO responsibilities
- Breach risk assessment and strategic planning
- Cybersecurity posture management
- Board-level reporting
- Cybersecurity governance
- Cost optimization
- Operational infosec activities
- Vulnerability assessment and patching
- Incident response
- Threat hunting
- Asset discovery and IT asset inventory
Your cybersecurity jobs consist of many activities, tasks and linked workflows, all of which are fraught with challenges, inefficiencies and roadblocks. The motivation behind our new feature release was to help make your cybersecurity jobs easier and more effective.
Of the dozens of newly introduced features, a couple of highlights include:
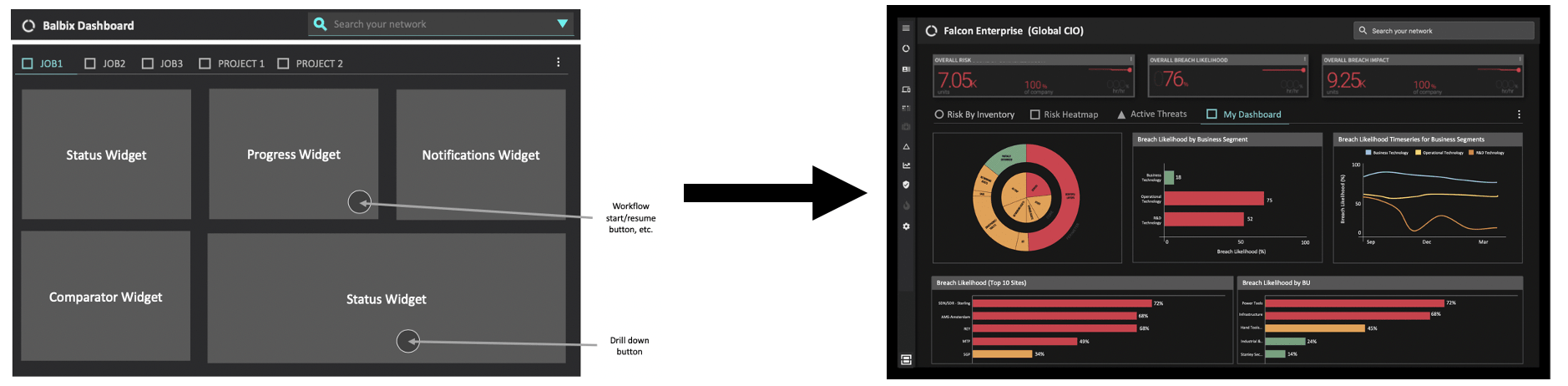
Custom Dashboards
Customizable dashboards allow you to tune your visibility to the most important aspects of your daily jobs. Get exactly the information you need, exactly when you need it.
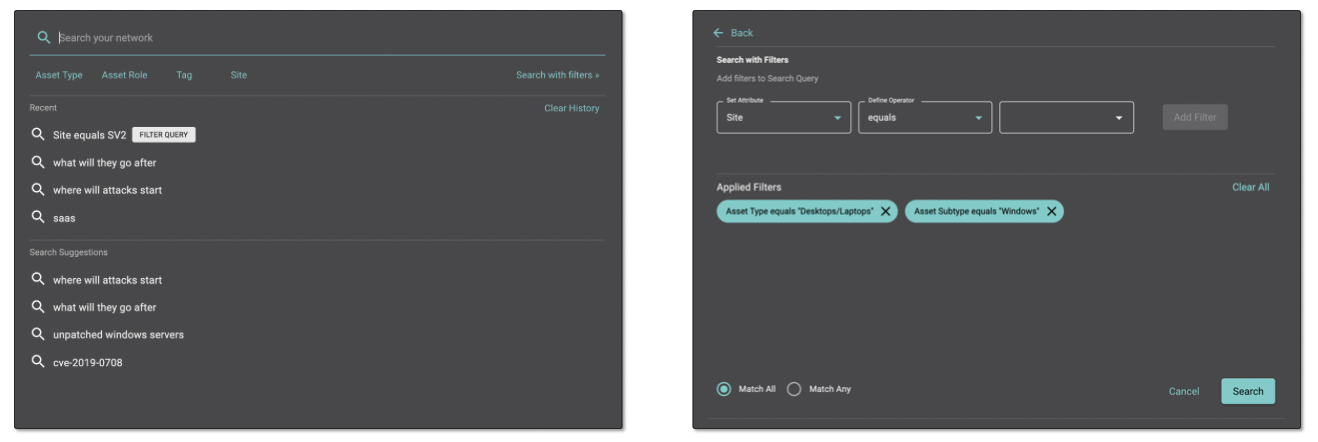
Filtered Search
Many of Balbix’s customers already love our natural language search capabilities, which provide answers to your most important questions through easy to understand queries. Filtered search makes this capability even more powerful, allowing you to combine the power of Google-like search with structured queries to get results and create dynamic groups per your exact needs.
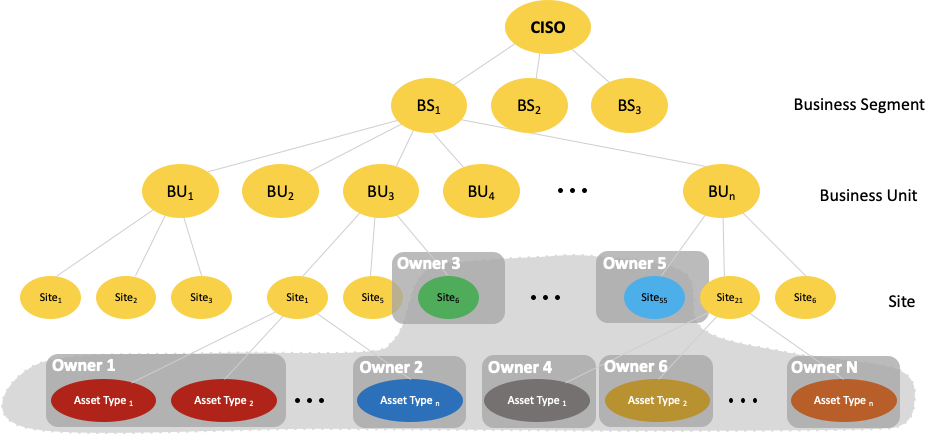
Risk Ownership Hierarchy
Risk hierarchy ownership allows you to create dashboards for risk owners that are tuned to their place in the organization. For example, a status dashboard for a CISO in the context of the hierarchy might show high level risk metrics for the entire organization, such as risk by Business Segment or Business Unit, and top areas of organizational risk. A BU owner’s dashboard, by contrast, would show metrics related to their job and group, such as mean time to patch critical assets and risk by server type.
Failure is Not an Option
Just like space exploration, the stakes are high in cybersecurity and failure is not an option. Our customers report security teams that are 10x more efficient and breach risk reduced by 95% or more.
That is transformational change worth checking out.
I’d love for you to get a taste for how Balbix can make your job easier, dramatically reducing risk. For the next 50 enterprises* that attend a demo, I will personally gift you (and the CISO and CIO of your organization) a copy of bestseller, “Failure is not an Option,” a truly fascinating behind the scenes look at NASA’s Mercury, Gemini, and Apollo programs, written by the Flight Director for those programs, Gene Kranz.
* Organization must have $1 Bn in revenues or more. CISO, CIO, or other top ranking cybersecurity leader must attend.
