This is post 6 in our series on making infosec jobs easier and covers threat hunting. You can read the previous 5 posts at one of the links below.
- Improve overall security posture
- Assess and report on breach risk
- Keep systems patched
- How to adjust to changes in the IT landscape
- Prevent data loss and fraud
Threat hunting is a cybersecurity practice that involves trained “hunters” that are knowledgeable in attacker behavior and techniques, searching for threats that might otherwise not be discovered by the security tools that your organization has deployed.
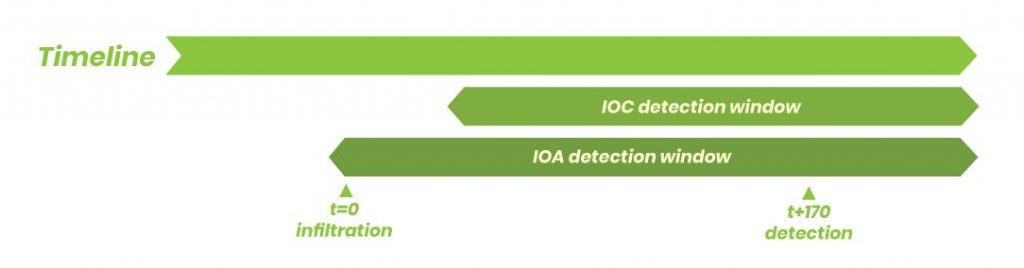
The traditional focus of threat hunting has been on detecting Indicators of Compromise (IoCs). An IoC represents evidence that an attack of some sort has already happened. While it may seem too little, too late to identify an attack after it has occurred, the overall idea is to minimize damage by identifying the breach as early as possible.
That said, skilled threat hunters recognized that they don’t need to wait for the compromise to have happened – there are plenty of clues and evidence left behind while the attack is happening. This has shifted the threat hunting focus to finding Indicators of Attack (IoAs). This makes intuitive sense. Why wait to figure out what has happened if I can shift the timeline up and figure out what is happening, potentially avoiding a breach altogether.
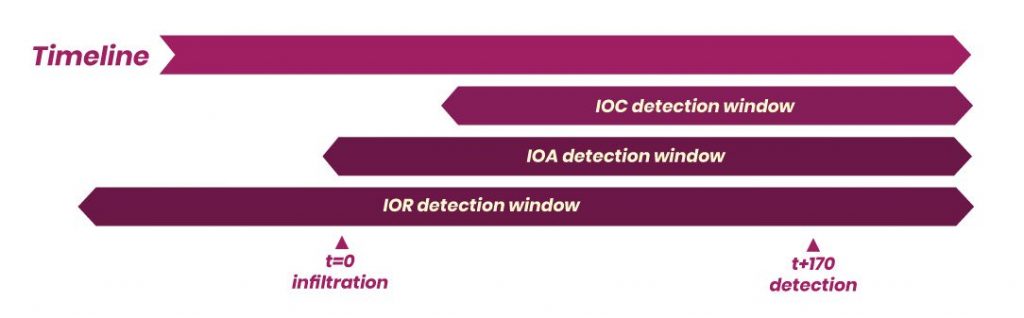
Still, this approach leaves something to be desired. After all, while the IoA approach does shift the timeline up, the fact that there is an IoA means that some adversary has already made progress in infiltrating your network. This is more reactive than proactive, which is what’s leading many of today’s threat hunters to focus even further upstream, identifying Indicators of Risk (IoRs). When hunting for IoRs, the threat hunter starts with hypotheses on how attacks might be conducted, and iterates through testing, but the difference with IORs is that the focus is on conducting this analysis before any attack begins. With this approach, the hunter is able to identify whether the organization is vulnerable to an attack in the future, as opposed to identifying whether the organization is being attacked right then.
Without Balbix, threat hunting tools and processes allow for detection anytime after initial infiltration (t=0), all the way up to the average detection time of 170 days after infiltration and beyond.
With Balbix, the job of threat hunting becomes proactive, rather than reactive.
The outcome?
Identification of possible attacks before initial infiltration. Not only does this make your threat hunting efforts more effective, but it saves valuable time and resources as there’s no longer an incident to respond to, as would be the case with reactive approaches.
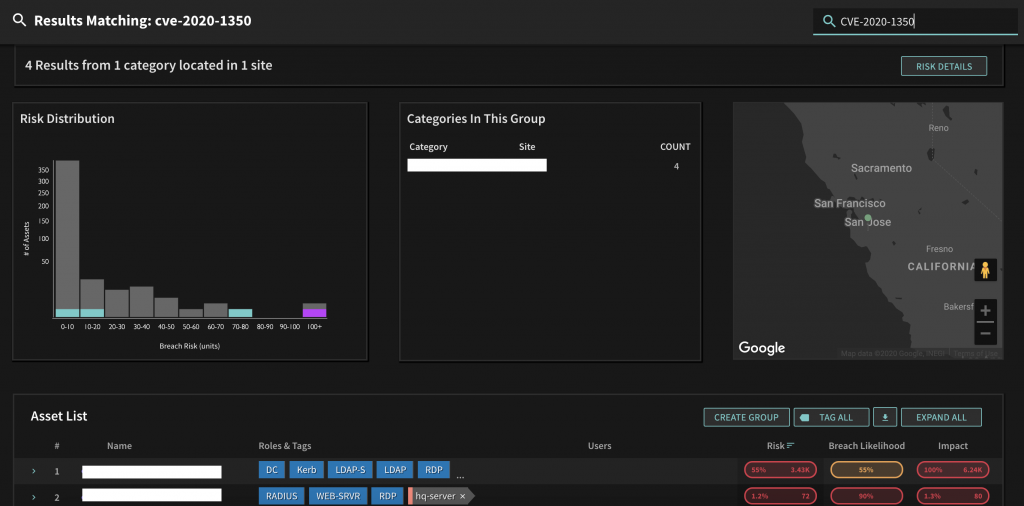
As an example of IoR hunting, suppose you have a particular CVE in mind that you feel attackers will attempt to exploit. Let’s use SIGRed (CVE-2020-1350). Traditional threat hunting, focused on IoA or IoC, necessitates waiting for something to happen so that you can detect, and hopefully stop, the compromise. Leveraging Balbix to proactively hunt for the IoR, however, allows you to use a simple, proactive, natural language search query to identify susceptible systems.
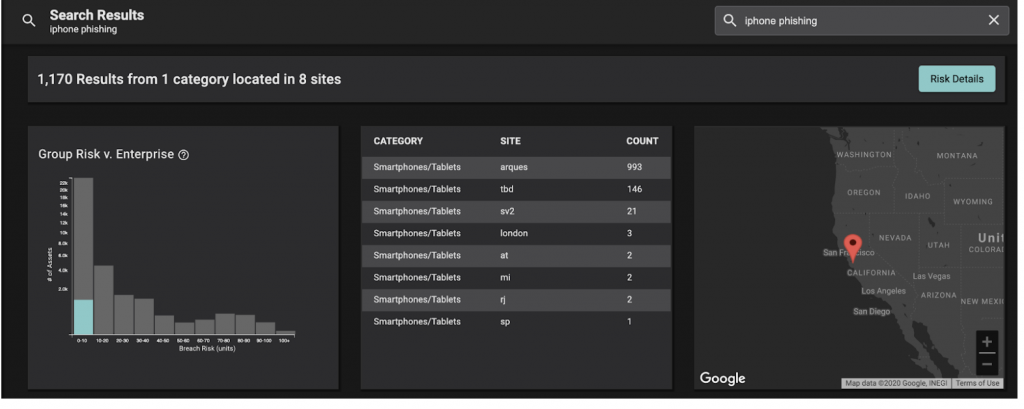
In another example, suppose you hypothesize that risky browsing behavior by iPhone users on your network are unnecessarily exposing your organization to increased phishing risk. Rather than waiting for a phishing event to occur, we can quickly and easily search on this risk to find the specific devices and users that are most susceptible, allowing us to offer additional training on the risk that their behaviors pose, and how to avoid being phished moving forward.
Overall, a proactive approach to cybersecurity is almost always preferred over a reactive approach. Adapting threat hunting to a proactive model is different than how you might have been trained, but with some reframing and the appropriate threat hunting tools, you will find much great outcomes in your threat hunting efforts.
Request a demo today to learn more about these and other capabilities in the Balbix platform.



