What Is Cyber Threat Hunting?
Wikipedia defines cyber threat hunting as “the process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions.” In practice, cyber threat hunting is a manual process where trained hunters combine expertise in attacker behavior and techniques with deep knowledge of the networks and assets they are protecting. Today, new tools using automation and AI are emerging to truly transform cyber threat hunting into a highly efficient and effective practice – quickly detecting cyber security gaps and stopping attacks BEFORE they occur.
How does Cyber Threat Hunting work?
Cyber threat hunting teams search networks, endpoints, and datasets (e.g., log files, antivirus events) to identify malicious, suspicious, or risky activities that monitoring and detection tools did not catch or properly categorize. Three key elements of threat hunting are methodology, technology, and threat intelligence.
- Methodology can vary depending on the approach taken within the threat hunting program, but it must be consistent and continuous. Investigation-based methodologies are reactive by nature, while a more proactive threat hunting approach combines advanced analytics and machine-learning to automate the investigative process and achieve much quicker results.
- Technology plays a crucial role in cyber threat hunting. As with threat hunting methodology, some reactive tools such as Security Incident and Event Management (SIEM) are utilized and combined with proactive tools such as Unified Asset Inventory, Risk-based Vulnerability Management and Cyber Risk Quantification that enable quicker and more prescriptive mitigation of potential threats.
- Threat intelligence enhances and expedites threat hunting for known threats.
From Reactive to Proactive Threat Hunting
IOC Detection
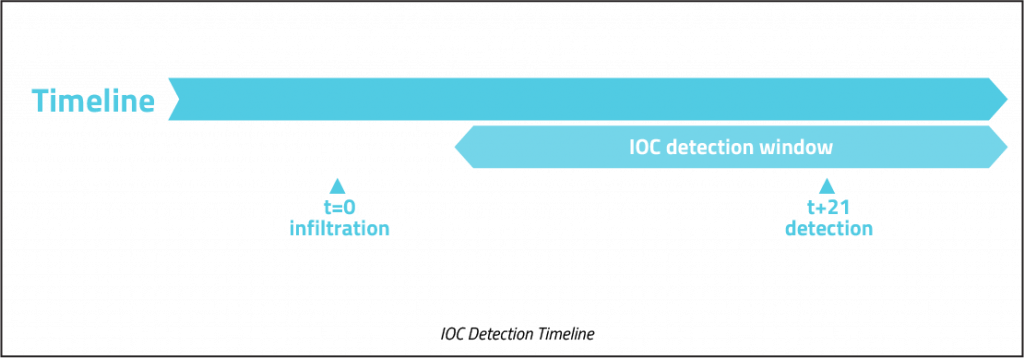
Initially, hunters sought to identify Indicators of Compromise (IOCs). At its simplest, an IOC is evidence that an attack of some sort has occurred. Examples of IOCs include malware infection, unexpected outbound traffic from an internal asset, and large outbound data transfers. The goal behind IOC identification is to shrink the 21 day average dwell time before a company detects a threat. However, an IOC approach is completely reactive as damage has already been done.
IOA Detection
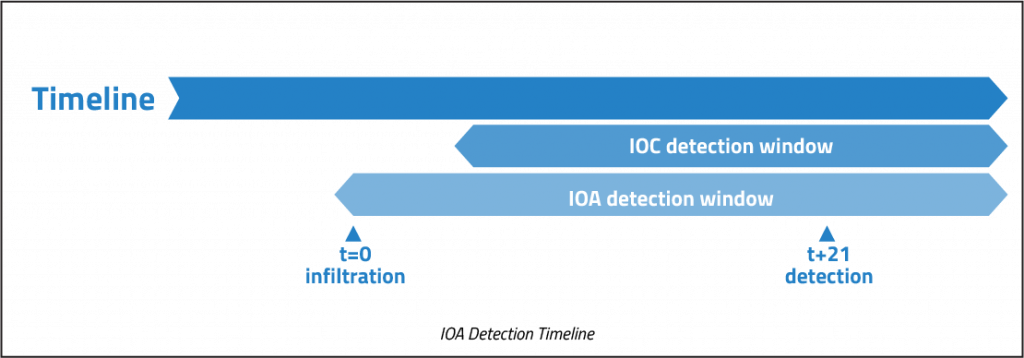
The reactive nature of IOC detection made infosec teams realize they needed to narrow the finding between infiltration to detection focusing on “What’s happening” and not “What has happened”. Indication of Attack (IOA) detection focuses on adversaries activities and behaviors leading up to an attack, often corresponding to the reconnaissance step of the Cyber Kill Chain. While IOA detection helps to identify threats sooner in the process, its Achilles’ Heel is that detection is still only possible after an initial infiltration event has occurred.
IOR Detection
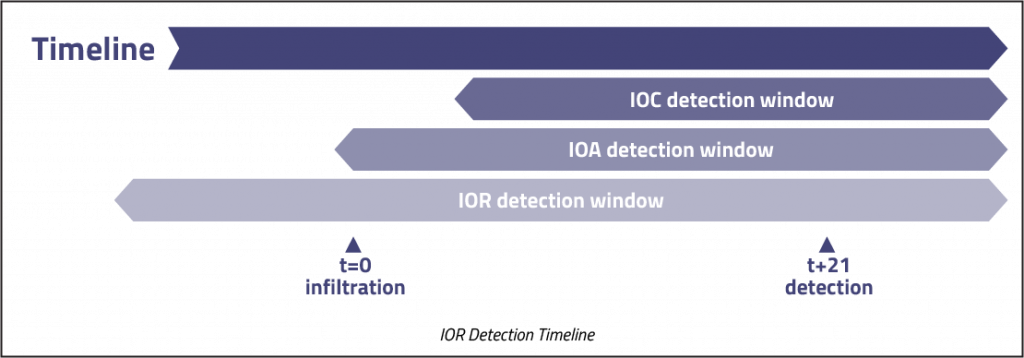
Threat hunting teams require more proactive measures and are increasingly turning their attention to indicators that are observable before the adversary has infiltrated the organization – Indicators of Risk (IORs). As with the IOC and IOA models, the threat hunter starts with a hypothesis on how attacks might be conducted, and iterates through testing. The difference with IOR is that the focus is on conducting this analysis before any attack begins.
Risk-based vulnerability management with integrated asset inventory and cyber risk quantification are great solutions to provide early indicators of risk with quicker and more effective mitigation outcomes. For example, these solutions could uncover and prioritize unpatched, high-value assets currently exposed to active exploits. Risk owners can then receive detailed remediation instructions identifying the best patches to apply and in what order to prevent the vulnerabilities being exploited.
Reacting to threats after they’ve happened, or even as they happen, will always be a losing proposition. As the enterprise attack surface continues to grow, proactive threat hunting is the only viable path forward.
