Lower Risk by Remediating Vulnerabilities That Matter
Prioritize vulnerabilities based on risk and automate VM workflows
Gain visibility into all vulnerabilities by aggregating data from various vulnerability sources. Leverage AI to infer unseen vulnerabilities, eliminate duplicates, and reduce false positives
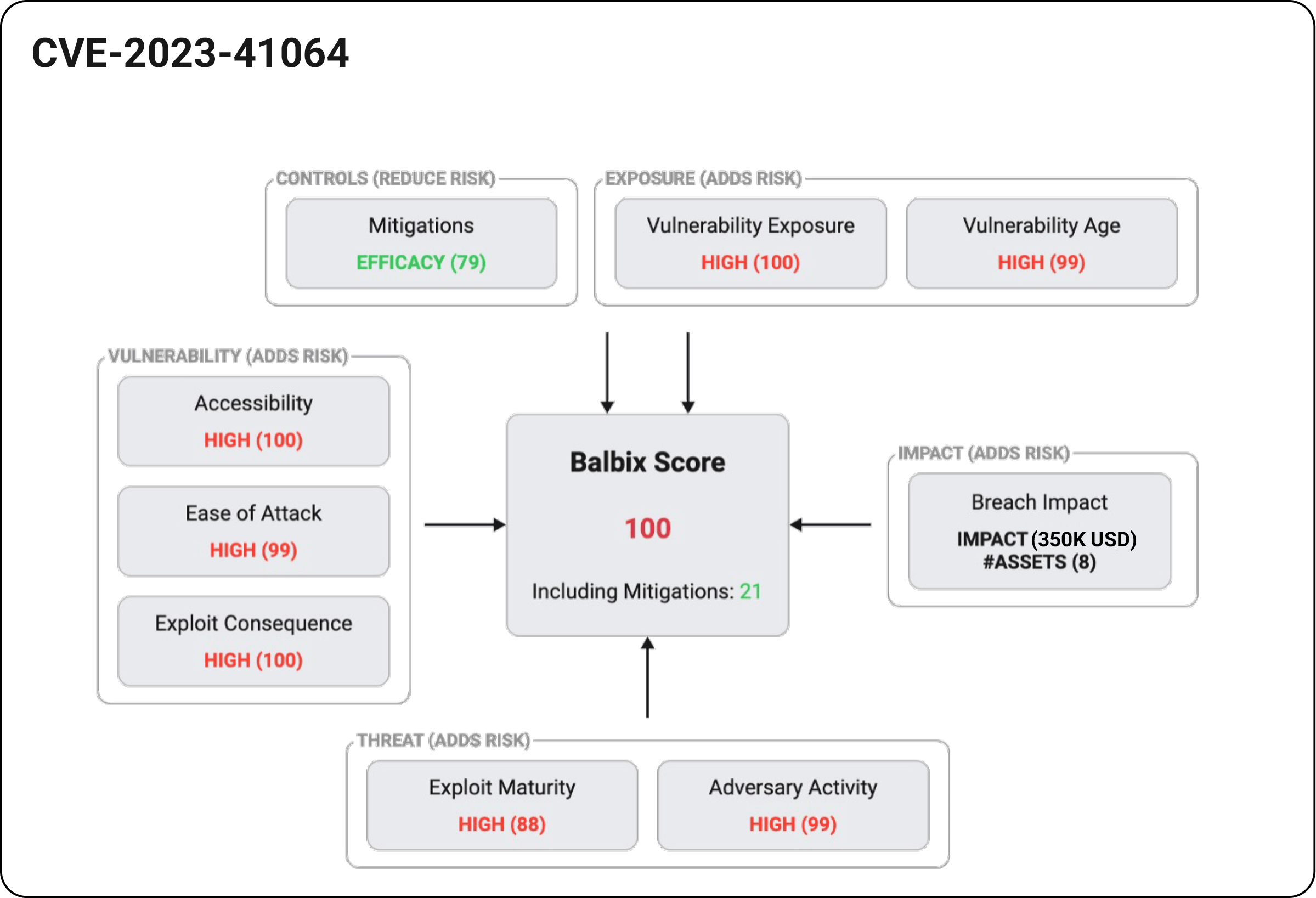
Use severity, threat level, exposure, control effectiveness, and business impact to prioritize vulnerabilities. Map vulnerabilities to CISA KEV and MITRE ATT&CK to understand attacker tactics

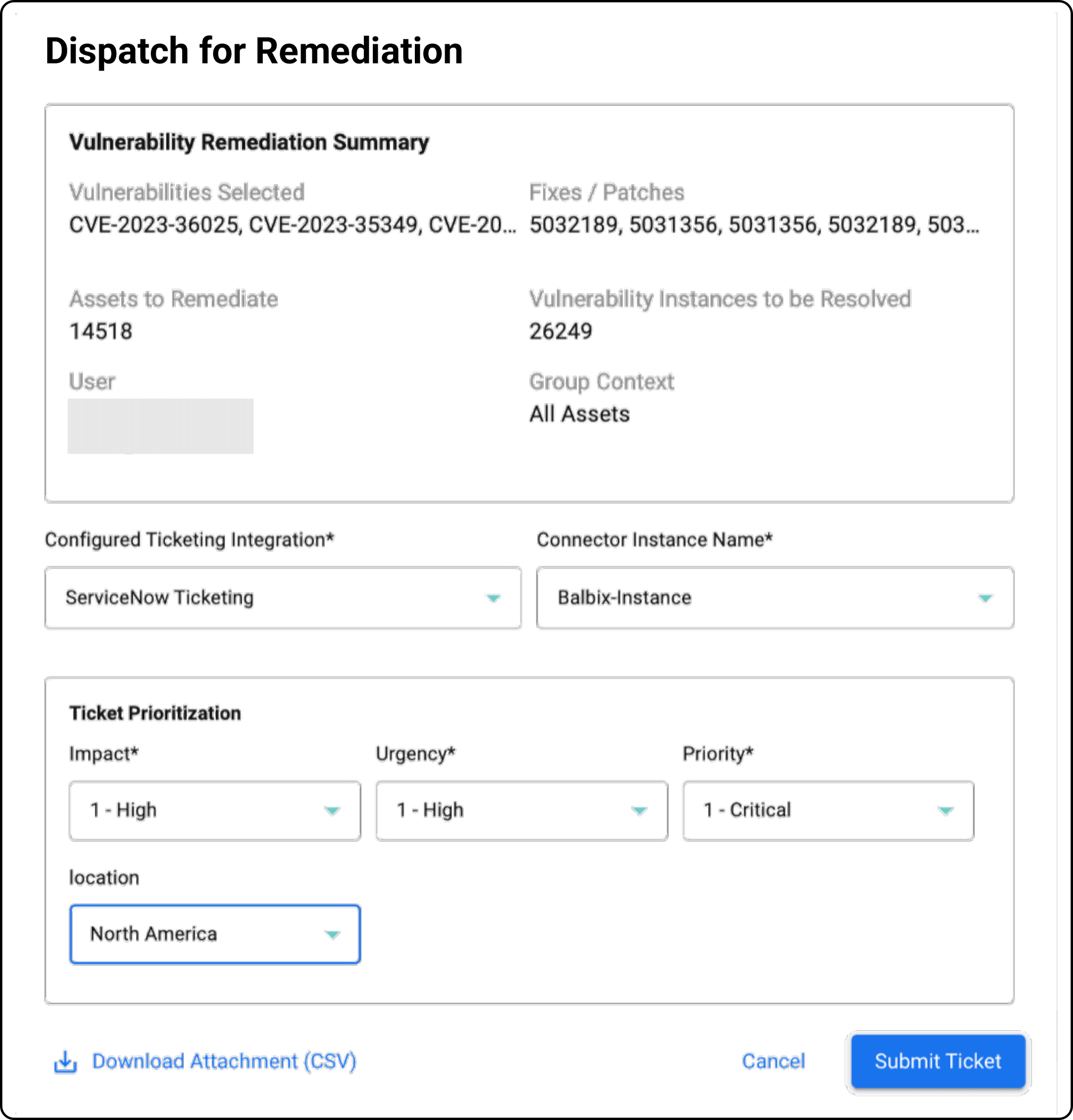
Empower owners to remediate by recommending the latest patches & automatically verifying deployed patches. Offer mitigation options when remediation is not possible
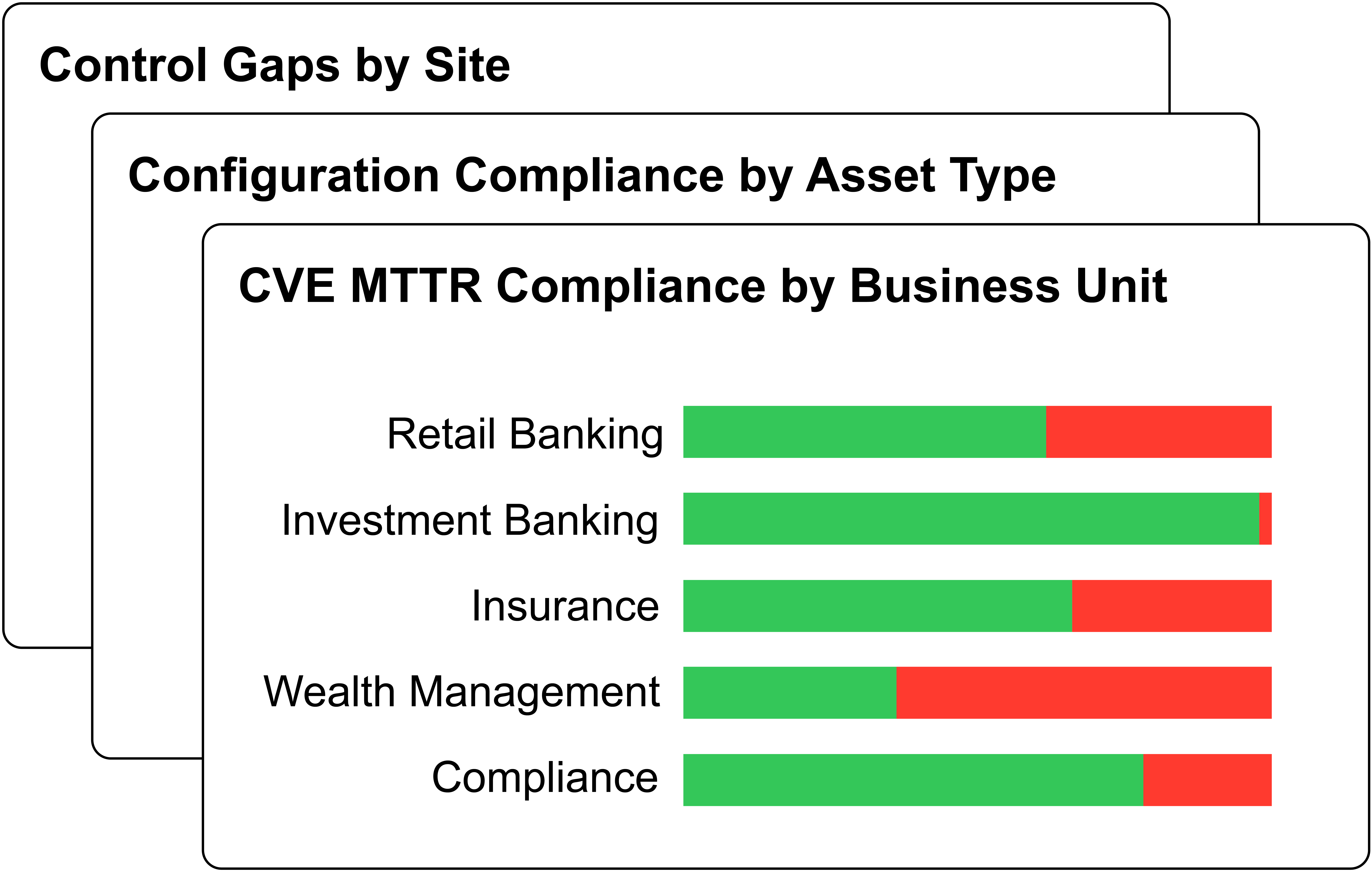
Slice and dice vulnerabilities by business units, asset type, criticality, and owners to benchmark mean-time-to-remediate (MTTR) and mean-open-vulnerability-age (MOVA)
Identify vulnerabilities related to malware, CISA-tagged vulnerabilities, and ransomware. Prioritize vulnerability instances that carry the highest risk. Using a risk-based approach enables security teams to focus remediation on high-risk scenarios.
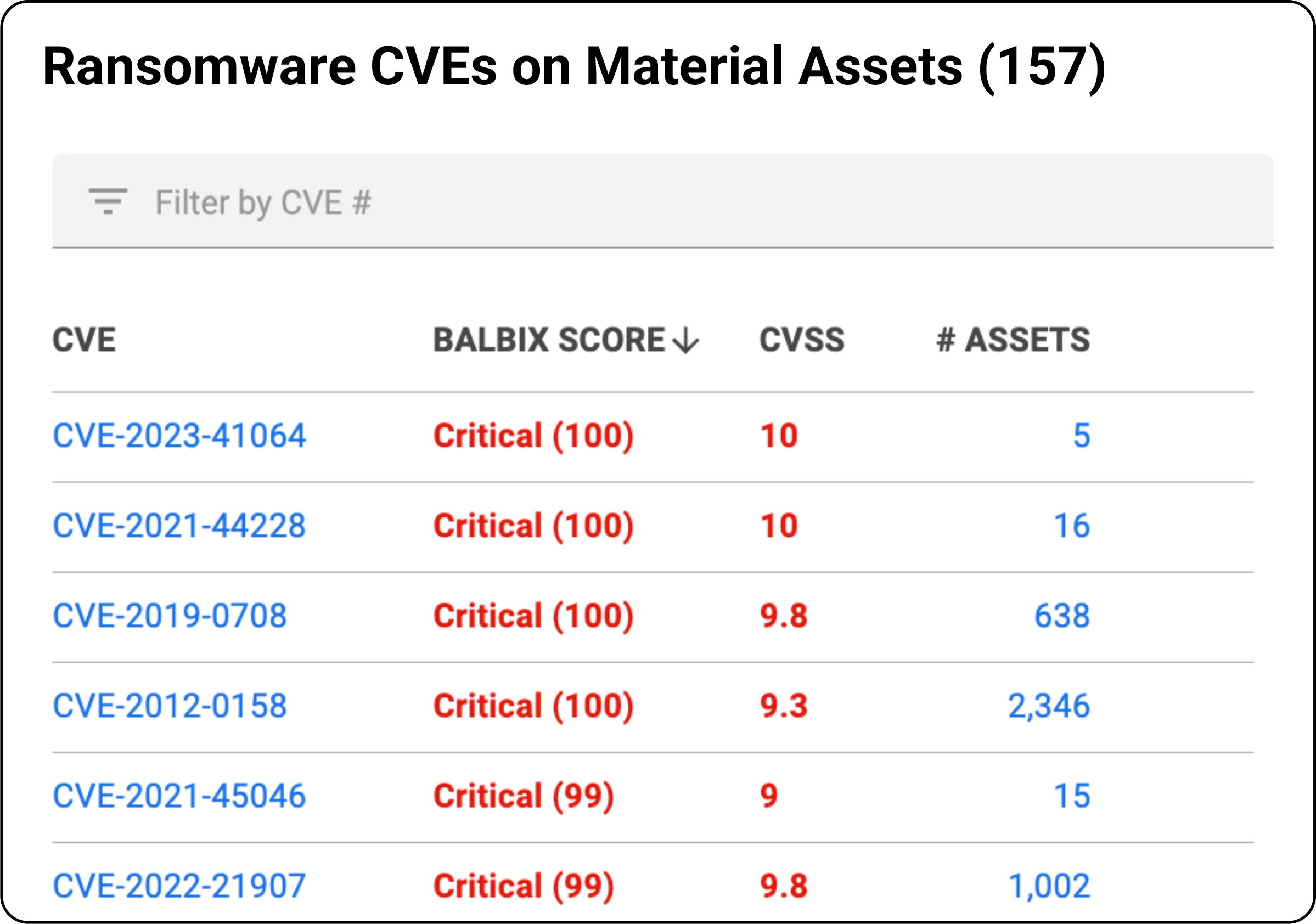
With Balbix, security leaders can slice and dice vulnerability remediation by owners, business units, or assets to track and ensure service level agreements (SLAs) required by various global compliance regulations like PCI & HIPAA and many more.
With automated patch recommendations, ticketing, and remediation IT teams can achieve their desired mean time to remediate (MTTR) without additional spend.




Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.