April 13, 2023
In today’s fast-paced and ever-evolving cybersecurity landscape, CISOs and security leaders are grappling with the challenges of tight budgets, increased government scrutiny and looming fines, and a relentless barrage of cyber threats. Balancing the allocation of resources and budget against cyber risks is a critical aspect that is occupying CISO’s mindshare. The mantra of “do more with less” is no longer a mere cliché, but rather an urgent call to action that compels us to fundamentally rethink our vulnerability management programs in light of these constraints.
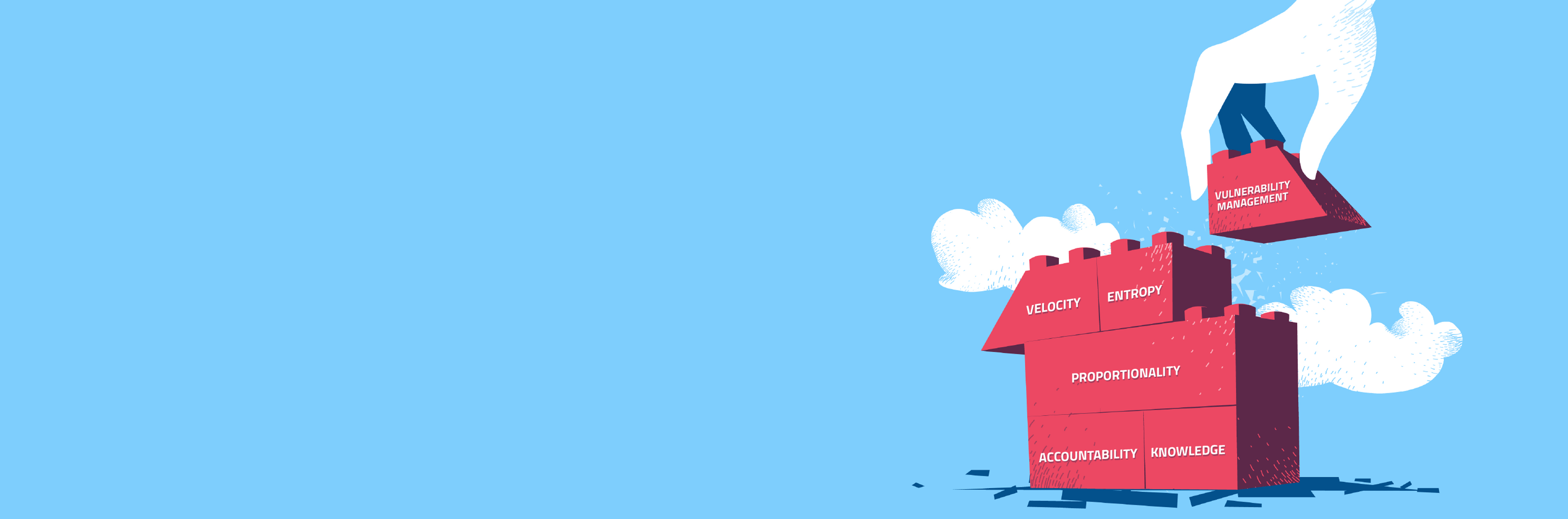
By employing first-principles thinking across various fields, we can dissect complex problems into their most basic components, paving the way for innovative solutions tailored to the unique cybersecurity challenges we face. This blog delves into five crucial first principles and establishes the association of how they serve as the foundation for a successful vulnerability management program. Furthermore, we will showcase how Balbix’s Risk-Based Vulnerability Management (RBVM) capabilities seamlessly align with these principles, delivering outstanding outcomes in securing your digital assets.
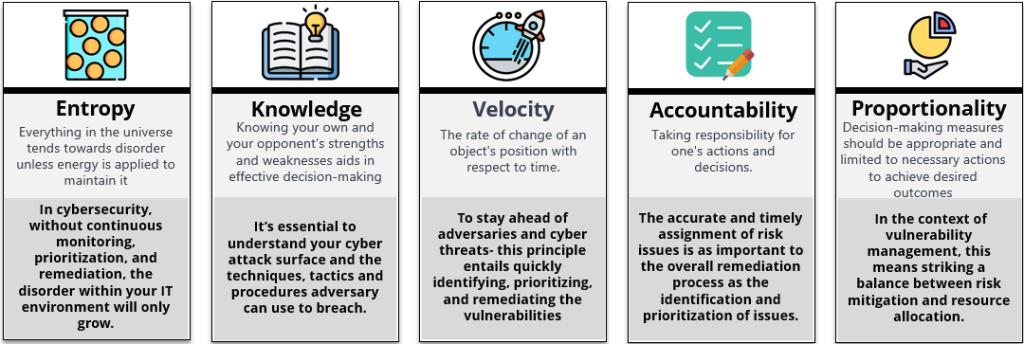
Entropy is a measure of disorder in a physical system. From the second law of thermodynamics, it is derived that entropy for an isolated system can only grow with time i.e. the state of an isolated system will tend towards disorder and randomness.
Just as the second law of thermodynamics dictates that the entropy of an isolated system will always increase, so too does the likelihood of a breach in your organization’s IT environment. The concept of entropy, a measure of disorder in a physical system, can be applied to vulnerability management. If left unchecked, your security posture will inevitably decline and become more susceptible to attacks.
Every month, thousands of new vulnerabilities are discovered, and without continuous monitoring, prioritization, and remediation, the chaos within your IT environment will only grow. By embracing the first principle of entropy, vulnerability management programs should adopt a proactive approach, focusing on continuous asset and vulnerability visibility, prioritizing threats, and implementing timely remediation measures to stay ahead of potential attacks.
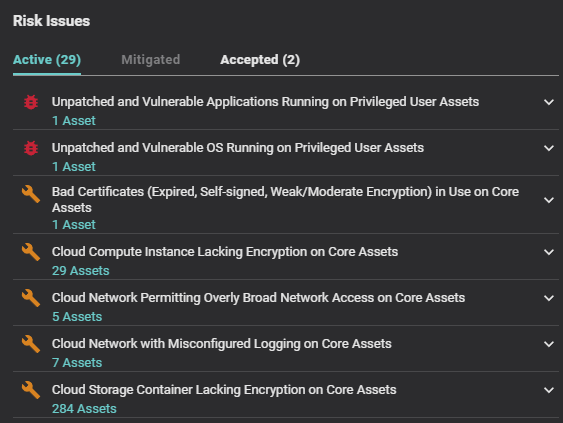
Balbix’s RBVM platform addresses the first principle of Entropy by offering near-real-time and unified-asset inventory, enabling organizations to stay on top of their security posture and mitigate risks effectively. Additionally, Balbix consolidates all vulnerabilities into a single, unified model. By continually ingesting findings from various vulnerability assessment tools, including IT infrastructure, IoT/OT, web apps, and cloud, Balbix ensures that all vulnerabilities are tracked and prioritized in one place
“If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.”
― Sun Tzu, The Art of War
Visualize knowledge as a ladder that must be climbed, with each step building on the previous one. The first step requires a comprehensive understanding of the problem, relying on high-quality data. Analyzing incomplete or inaccurate data is pointless when drawing conclusions about your organization’s IT security status. To gain a comprehensive understanding, it’s essential to develop metrics that provide insight into the present and project future scenarios. The knowledge derived from these indicators can drive strategic and tactical decisions.
The first principle of knowledge emphasizes the importance of thoroughly understanding your IT environment and adopting an attacker’s mindset to effectively manage your security posture. Internally, this necessitates breaking down silos among teams and departments to gain a comprehensive view of your assets, network topology, and application landscape. Externally, it requires familiarity with the tactics, techniques, and procedures (TTPs) employed by attackers to exploit your network. Without such knowledge, prioritizing vulnerabilities and allocating resources efficiently becomes challenging.
Balbix helps address this principle by providing a comprehensive view of your IT environment (Know Thyself), including asset and vulnerability data from various sources, enabling collaboration and knowledge sharing across teams. Balbix also provides an automatic mapping of the common vulnerabilities and exposures (CVEs) and endpoint security controls to the MITRE ATT&CK Framework, which provides insights into the latest attack vectors and TTPs (Know Thy Enemy), empowering organizations to make informed decisions about vulnerability prioritization and remediation.
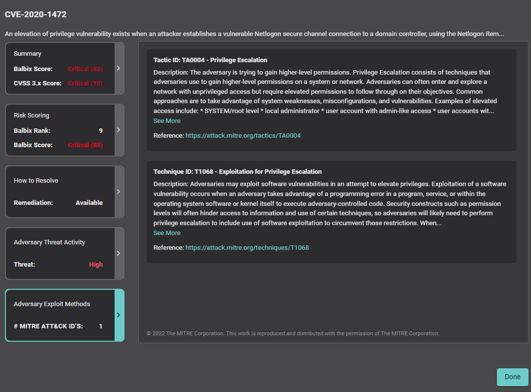
In today’s rapidly evolving threat landscape, vulnerabilities are discovered at a staggering pace. With more than 26,000 new CVEs discovered in 2022 alone (that’s three CVEs every hour, or 2,100 a month!), organizations must contend with the reality that vulnerabilities will grow faster than they can be fixed. This highlights the importance of developing a vulnerability management program that can quickly identify, prioritize, and address the most critical vulnerabilities.
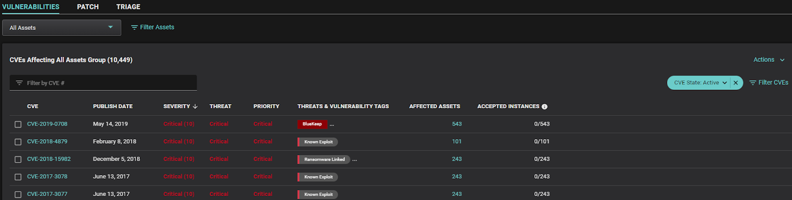
In contrast to other vendors, Balbix takes a holistic approach to risk-based prioritization by covering distinct approaches for vulnerability management scenarios during war-time and peace-time. War-time refers to an environment that is under attack or threat. Peace-time vulnerability management refers to the routine management of vulnerabilities in a non-crisis environment. Balbix’s Vulnerability and Patch Prioritization capabilities address these requirements effectively.
For war-time scenarios, Balbix’s Vulnerability Prioritization provides real-time prioritization of CVEs, considering factors like severity, threat level, software vendor, and category.
For peace-time scenarios, Balbix’s Patch Prioritization recommends optimized patches based on overall risk reduction while minimizing the number of patches to be applied, effectively accelerating the remediation process.
Despite its apparent simplicity, the principle of accountability is often overlooked, and many risk issues remain unassigned. The siloed nature of the problem is one reason for this oversight. IT departments are focused on maximizing system availability and performance while minimizing costs, with security often taking a back seat. This underscores the importance of the security team’s intervention to identify and draw attention to risky situations that require immediate action.
Assigning risk issues timely to the correct resolution team is a crucial step in the remediation process, as accuracy and timeliness are essential. Assigning an issue to the wrong team can lead to significant delays in resolution, which can be particularly problematic during a security crisis. The accuracy and timeliness of assignments are just as critical to the overall remediation process as identifying and prioritizing the issues themselves.
With Balbix’s integrations with ticketing platforms like ServiceNow ITSM (IT Service Management), creating remediation tickets is a breeze. By pushing detailed fix information to remediation tickets, your teams can quickly address prioritized vulnerabilities with minimal manual effort. Plus, these integrations enable your security and IT teams to work more efficiently by utilizing your established systems for their remediation workflows.
The first principle of proportionality states that measures taken in decision-making should be limited to what is necessary and appropriate to achieve the desired outcome.
In the context of vulnerability management, this means striking a balance between risk mitigation and resource allocation.
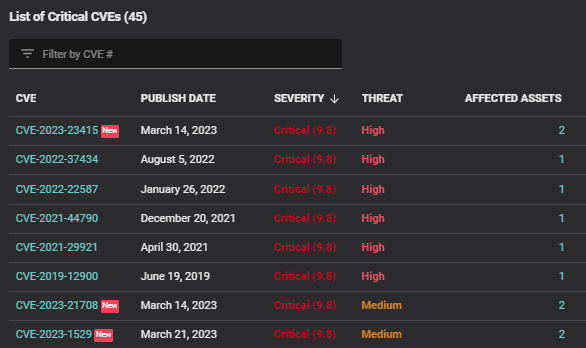
In the absence of a cohesive risk management strategy, organizations may struggle with inconsistent risk definitions across key cybersecurity areas such as Risk-Based Vulnerability Management (RVBM), Cyber Risk Quantification (CRQ), and Governance, Risk, and Compliance (GRC), leading to imprecise risk evaluations. Balbix’s unified risk model addresses this challenge effectively. By employing a risk-based prioritization grounded in a comprehensive five-factor risk equation, Balbix considers vulnerability severity, threat level, business importance, exposure, and the mitigating impact of supplementary security controls. This methodology yields precise prioritization that aligns with your organization’s objectives and allows you to circumvent unnecessary efforts addressing low-priority concerns.
In conclusion, Balbix’s Risk-Based Vulnerability Management (RBVM) capabilities offer a powerful and comprehensive solution that excels in addressing the first principles of vulnerability management. By focusing on entropy, knowledge, velocity, accountability, and proportionality, Balbix enables organizations to build a more effective and resilient vulnerability management program tailored to the unique challenges of today’s threat landscape.
Balbix goes beyond just RBVM – it offers a comprehensive solution with Cyber Asset Attack Surface Management (CAASM), RBVM, and Cyber Risk Quantification (CRQ) capabilities that deliver exceptional value to organizations. This helps CISOs to create a more robust and adaptable security posture that can meet the demands of shrinking budgets, increasing regulations, and the ever-changing threat landscape.