September 8, 2022
In the military, you approach periods of war and peace differently.
Peace-time is used to train the troops for battle. Peace-time’s stability is used to steadily enhance assets and strategic position for future war.
When war comes, the approach is quite different. The focus turns to making rapid decisions and acting quickly on the battlefield while under fire. War-time is about facing the unknown – it’s about survival and protection.
Vulnerability management is the same. In peace-time, security teams are focused on burning down high volumes of important vulnerabilities and closing security gaps quickly and efficiently. In war-time, the attention turns to urgently identifying and deploying patches or quick mitigations to fix critical vulnerabilities before attackers can cause serious damage to the organization.
In both situations, speed is of the essence. But, because peace-time and war-time are very different in terms of the challenges, constraints and goals, security teams require distinct approaches for each. In this blog, we highlight two key concepts: Patch Prioritization and CVE Prioritization – and how they help teams work more efficiently, during peace-time and war-time.
Patching security flaws is a challenging and never-ending task for most security professionals. This daunting task gets more difficult each year as the number of new security vulnerabilities continues to grow. To put this into perspective, the number of new CVEs reported in 2021 was 28,495 with this number expected to be even higher in 2022 (16,568 new CVEs have been reported this year)!
Traditional approaches and legacy tools are no longer able to keep up with the pace of new CVEs. Security teams typically rely on severity and threat data that supposedly identify the top vulnerabilities to remediate. While this seems like a good strategy on the surface, it tends to be cumbersome, inefficient and leads to risk accumulating over a long period of time due to a backlog of unpatched key assets.
If you are using a legacy vulnerability management solution, this is probably what your vulnerability management process looks like:
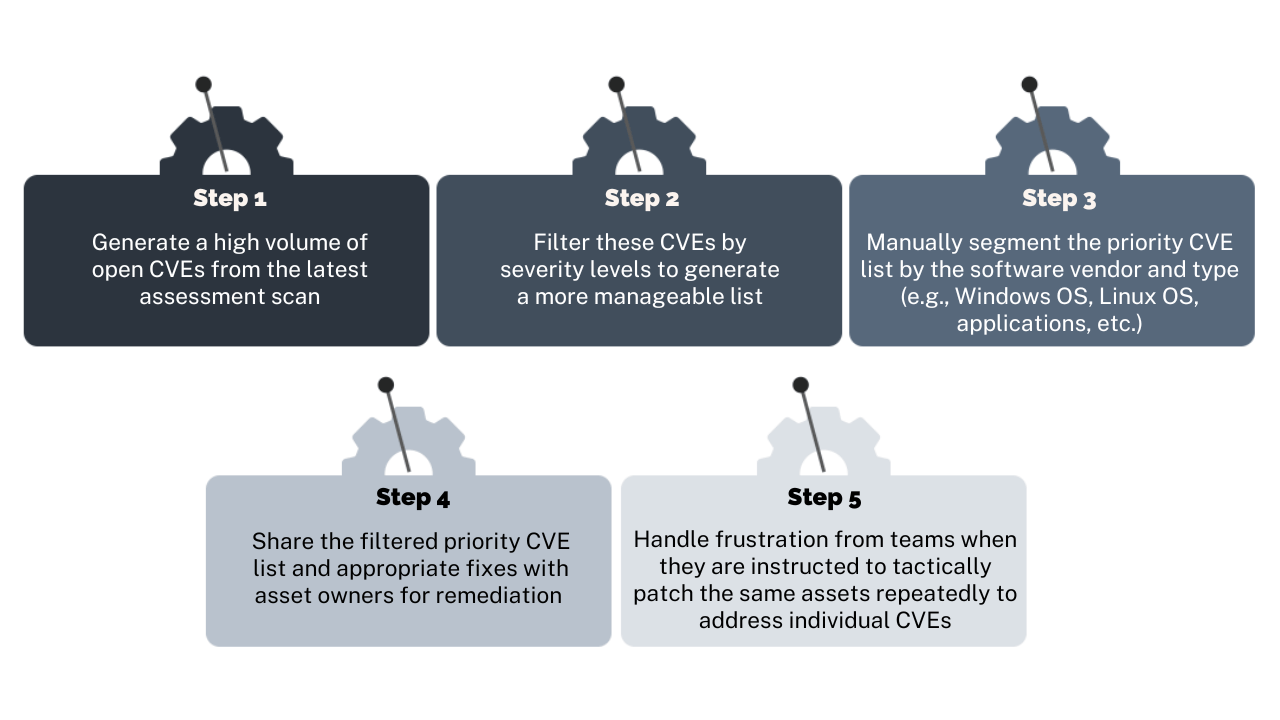
As you can see, this approach creates unnecessary work for IT and patching teams because they are required to apply multiple patches for the same product as they close individual vulnerabilities, despite the fact that updates for most applications today include patches for all prior vulnerabilities in addition to patches for newly identified vulnerabilities.
Patch Prioritization, a feature of the Balbix platform’s Risk-based Vulnerability Management (RBVM) capabilities, recommends the patches that most efficiently address the maximum number of open CVEs for an application in order for security teams to more effectively reduce risk. With Patch Prioritization, teams can eliminate unnecessary patching and improve their overall cybersecurity risk posture.
Balbix’s Patch Prioritization makes recommendations by considering overall risk reduction of available patches. This is accomplished by accounting for the number of vulnerabilities, severity of vulnerabilities, threat data for the vulnerabilities under consideration, and business impact of assets while minimizing the number of patches that need to be applied for a given product.
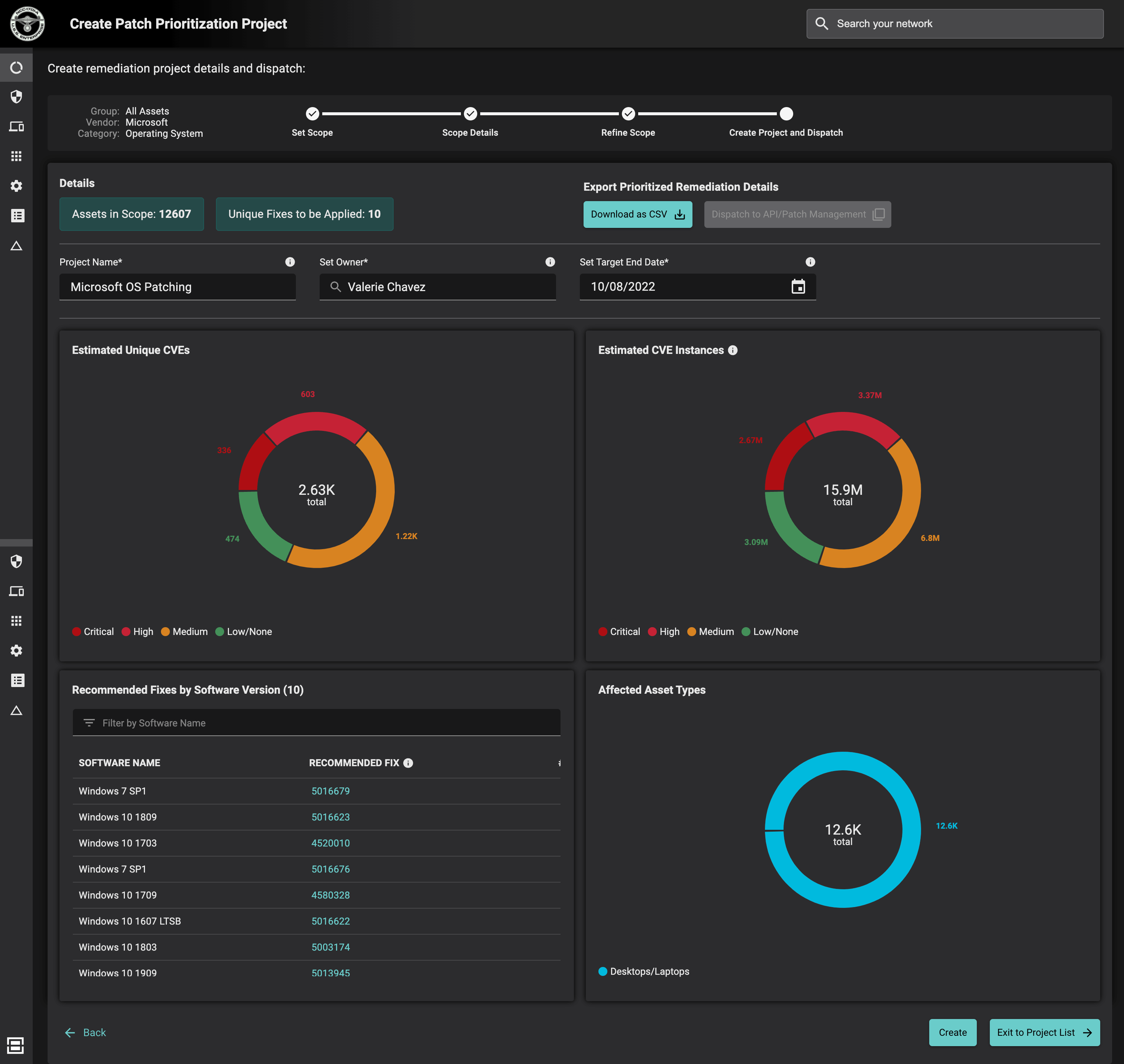
Balbix’s Patch Prioritization works in combination with other aspects of the Balbix RBVM solution to help with peace-time CVE remediation:
With Balbix, a peace-time risk-based patching process looks like this:
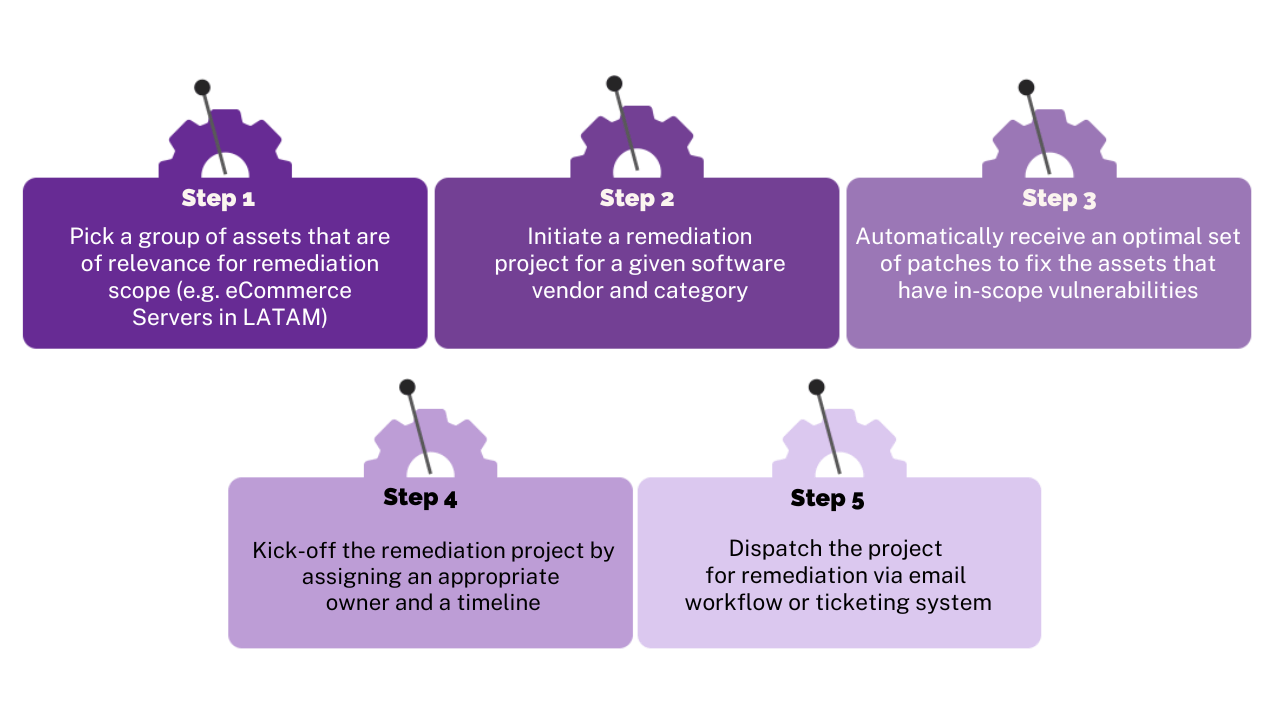
With Balbix’s RBVM solution, vulnerability management teams can supercharge their peace-time patch management program to burn through vulnerabilities faster and improve patching metrics – such as mean-time-to-patch (MTTP), mean-time-to-remediate (MTTR) – and their overall duty cycle. Ultimately, faster MTTRs coupled with risk-based prioritization result in substantially lower cyber risk.
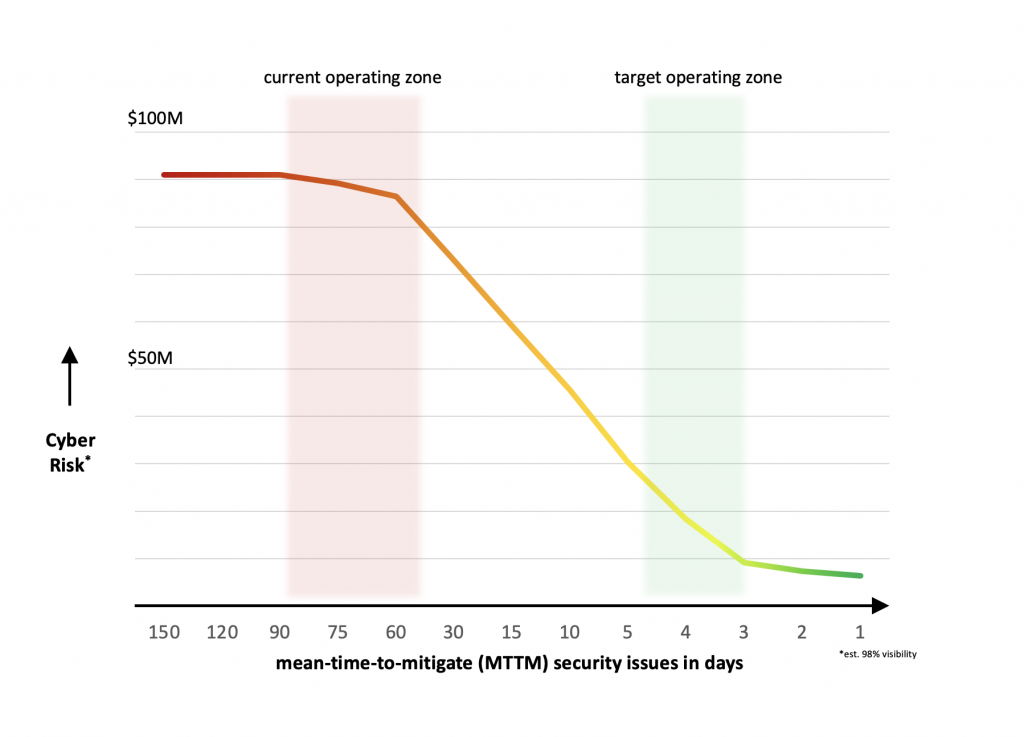
During war-time, critical vulnerabilities can arise out of nowhere. It can be stressful and time-consuming to deploy emergency patches, and security teams often lack the resources and visibility needed to quickly identify, triage and resolve the vulnerabilities in a timely manner.
Remember the Log4j vulnerabilities?
If you are using a legacy vulnerability tool to deploy emergency patches, your war-time patch management workflow might look something like this:
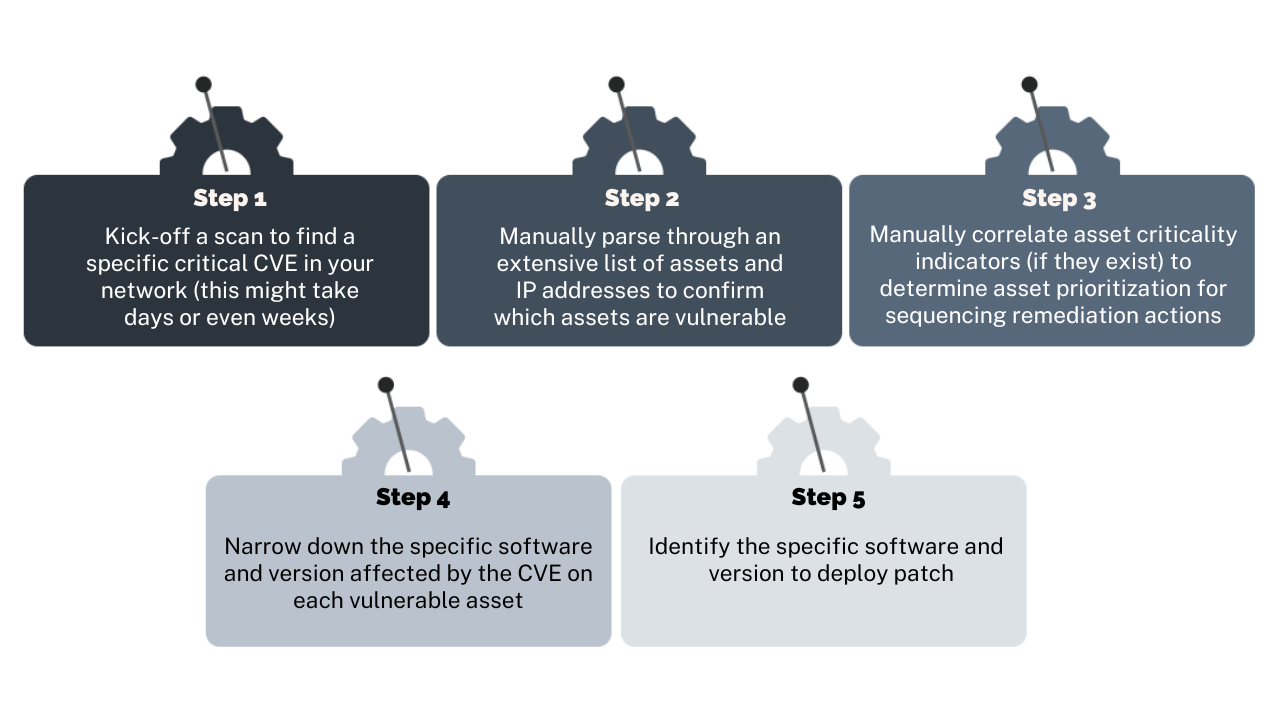
Balbix’s CVE Prioritization capabilities enables real-time prioritization of CVEs not just by CVE severity and threat level, but also by software vendor, category and many other factors. Cybersecurity professionals can scope the list of open vulnerabilities of concern in the enterprise using a wide variety of filters such as operational and business tags, threat levels, threat names and threat categories (e.g. ransomware, ongoing exploits, available exploit code etc.) and use this information to drive an efficient remediation strategy.
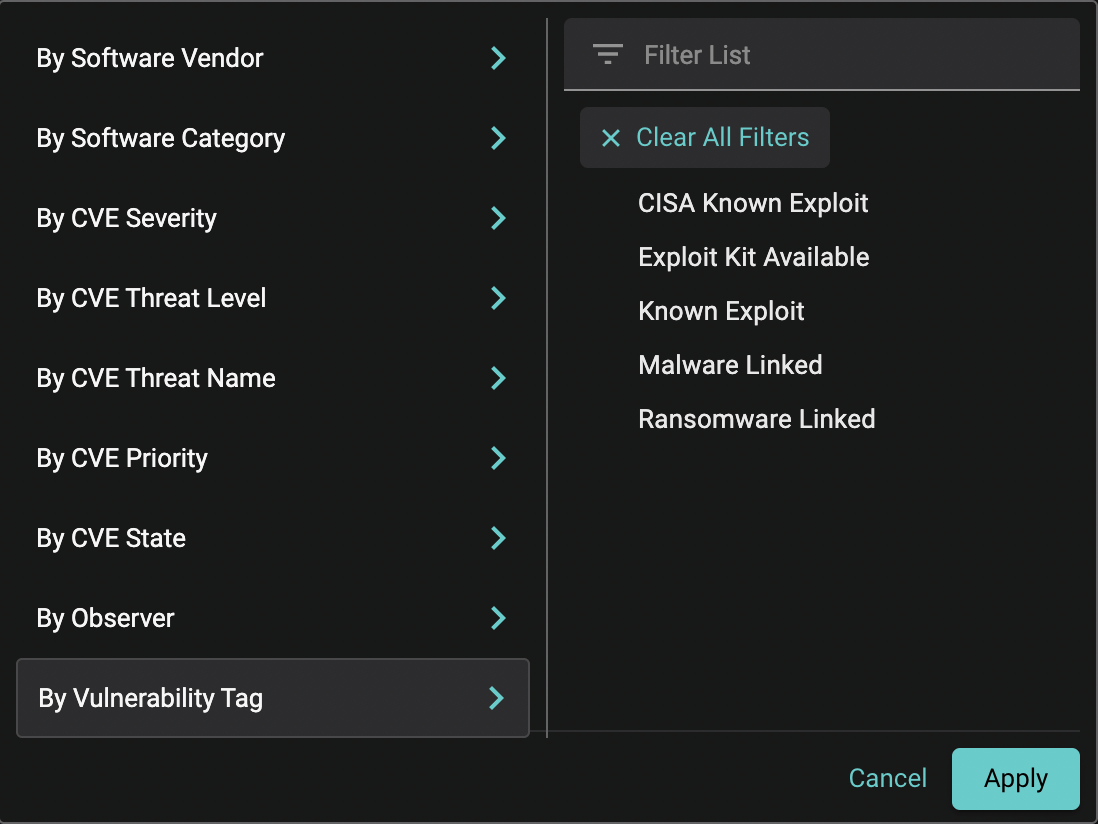
For our customers, CVE Prioritization has reduced the triaging effort from weeks to minutes. For each vulnerability, Balbix provides a tactical fix (a patch version that is minimally required for remediation) as well as a strategic fix (a patch that addresses the maximum number of vulnerabilities for the affected versions of software).
For example, a Fortune 100 Telco with several million assets relied on Balbix to identify all vulnerable instances of Log4j with extremely high accuracy across their enterprise environment. Using CVE Prioritization, they reduced their remediation time from several months to a short number of weeks.
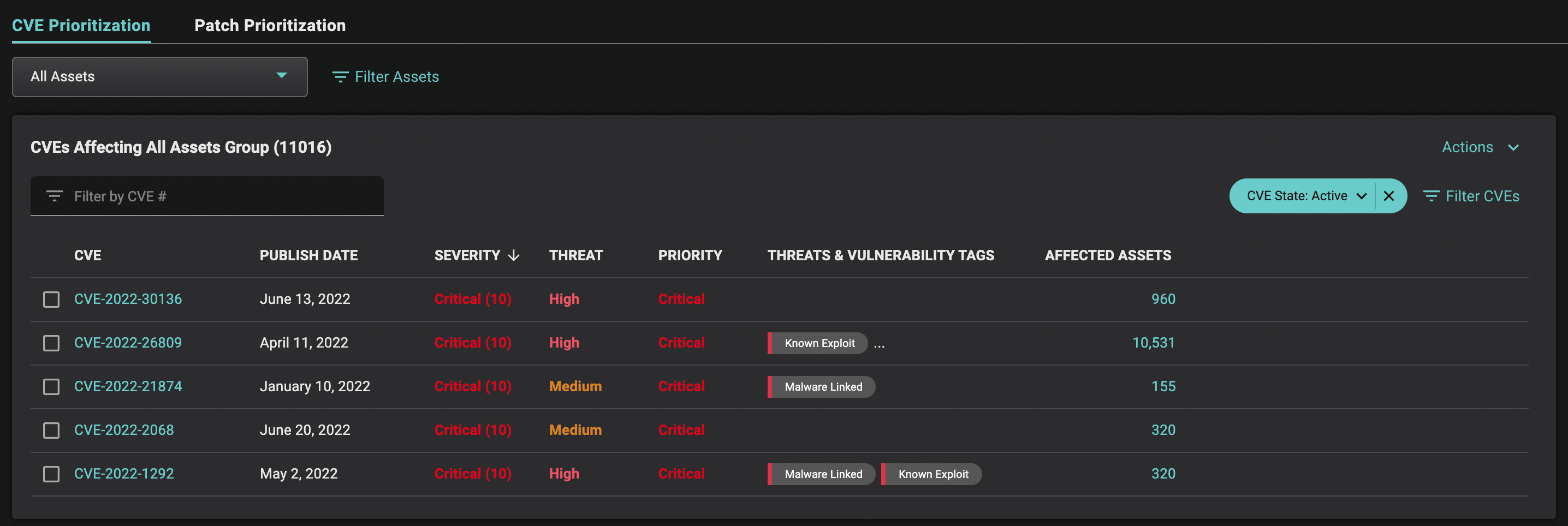
CVE Prioritization works in combination with other aspects of the Balbix RBVM solution to help with war-time CVE remediation:
With CVE Prioritization and these additional features your war-time patch management process looks like this:
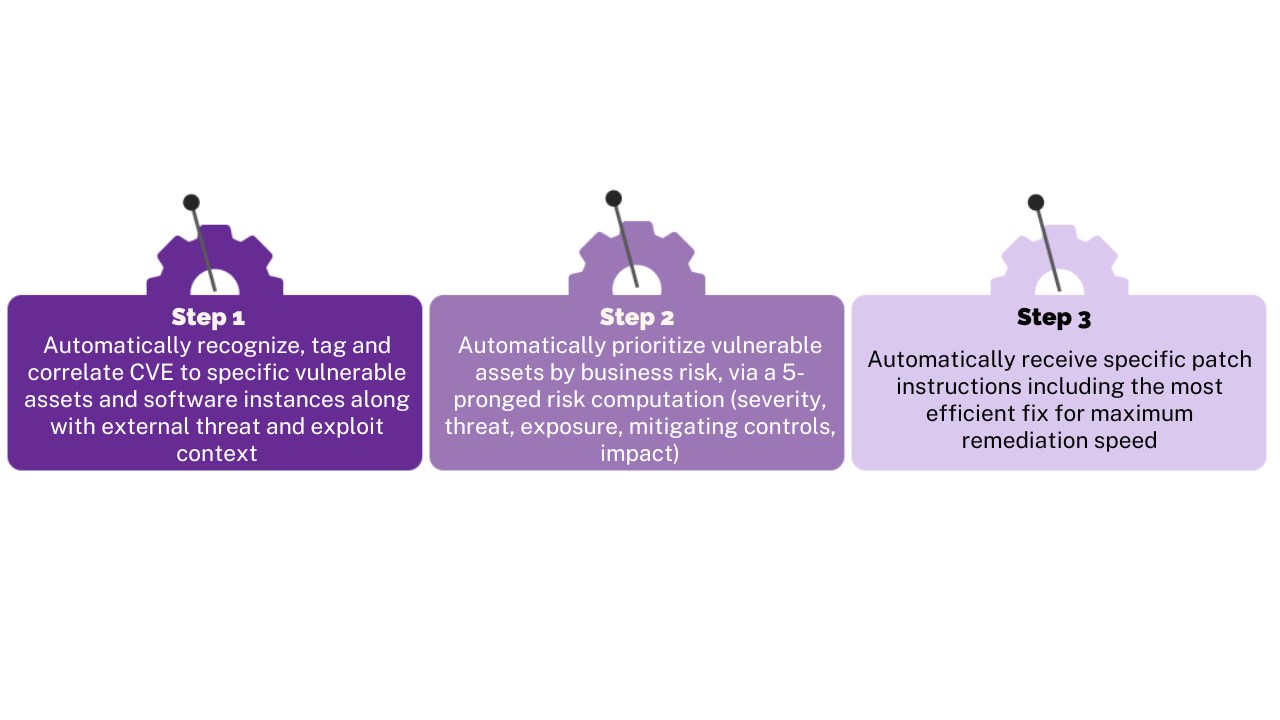
As I mentioned earlier, vulnerability management is a lot like preparing for and fighting a war. In times of peace, your security teams are focused on enhancing security posture by tackling mountains of important CVEs as efficiently as possible. But during war-time their attention is turned to taking action to quickly fix critical vulnerabilities before their organization is hit by a cyberattack.
Peace-time and war-time are very different in terms of challenges, constraints and goals, which means that security teams require distinct approaches for each. Balbix’s RBVM solution, and two unique features in particular – Patch Prioritization and CVE Prioritization – can help security teams work more efficiently in each situation. And with Balbix maximally automating your workflow, you won’t need an army!
Start your journey to a more efficient patch management program by scheduling a 30-minute demo with Balbix.