This is post 4 in our series on making infosec jobs easier and covers how cybersecurity teams can adjust to changes in IT landscape. The first post covered improving overall security posture. The second post discussed assessing and reporting on breach risk. The third post was all about keeping systems patched.
Part of what makes IT and infosec so exciting, and simultaneously scary, is that it’s a highly dynamic environment. The recent past is a striking example of this dynamism, where the vast majority of employees switched overnight from office work to working from home, dramatically altering the enterprise attack surface. At the same time, economic uncertainty forced many organizations to cut budgets and curtail spending and recruiting, exacerbating the extent of the challenge.
When these types of changes happen, the security team is expected to move at the same pace as the business, but there are several inherent challenges in doing so. Prioritization is always an issue because a lack of understanding of breach risk impact makes it impossible to ensure that your team is focused on activities that have the biggest impact on breach risk. And with dozens of point products, each with their own reporting and their own view of the world, it’s unclear how effective each tool is. Since it’s impossible to tell which tools stop using, and which to replace with better tools, decision making slows to a crawl.
Adjusting to Changes in the IT Landscape
If we look at the typical process that an organization follows for adapting to changes in the IT landscape, there are a number of areas where tools and processes fall short, as indicated in the picture below.
Unfortunately, there are big challenges and shortcomings throughout the majority of the Discovery, Assessment, and Planning phases of this job.
Balbix was designed as a continuous, real-time platform, ensuring that you always have up-to-date, accurate information about your attack surface, including the impact of compensating controls and other mitigations, as well as the impact of the near constant changes in your environment. With built-in simulation and planning tools, you’ll always know where your organization is on the cyber-risk spectrum, as well as what (if anything) happens to overall cyber-risk as a result of changes, regardless of whether those changes are planned, or unanticipated.
If, for example, I wanted to look at the effectiveness of our existing controls, including their effectiveness and impact on overall risk reduction, I might create a custom Balbix dashboard like the one below. Here I can clearly see how much each mitigation is impacting overall risk. I can also look at the potential impact of proposed controls, which is particularly helpful when defending new budget line items or when proposing changes to the cybersecurity strategy for the organization.
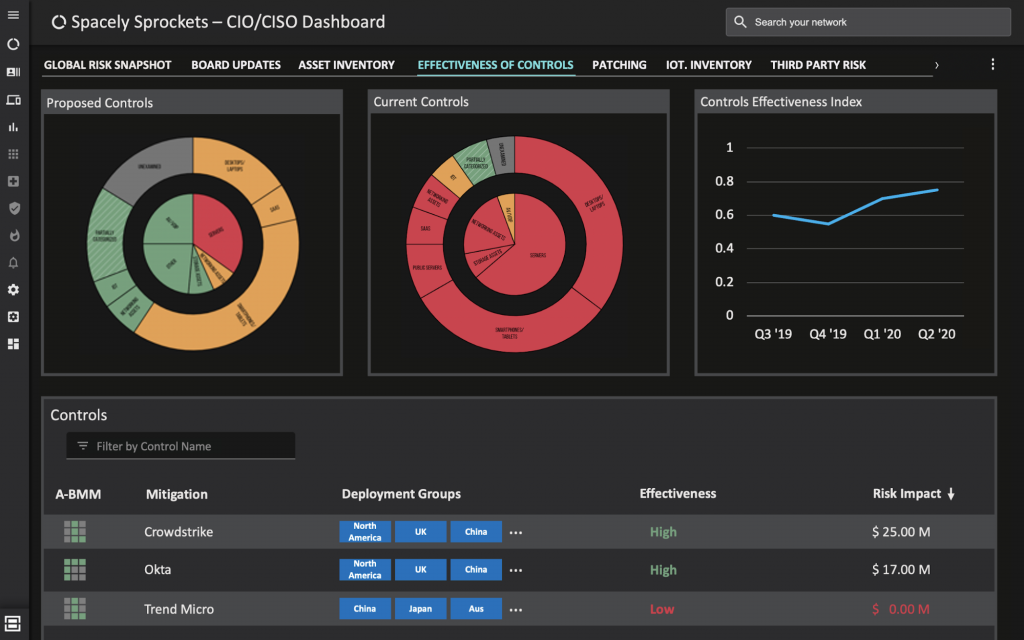
I can also see the outcome of changes made by various groups. For example, I might want to monitor how new initiatives in one business segment are working over time as compared with other Business Segments, so I would use a chart like one of the two examples below.
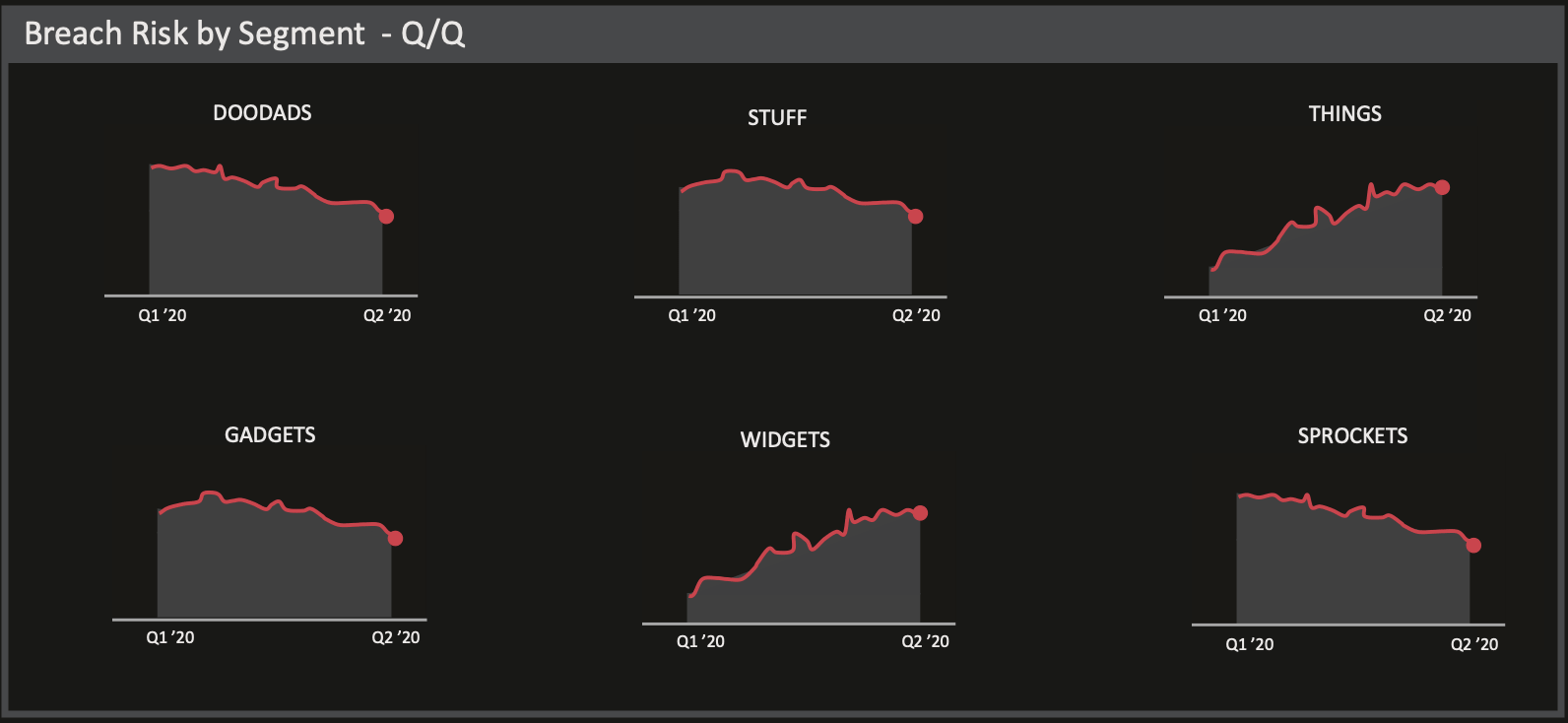
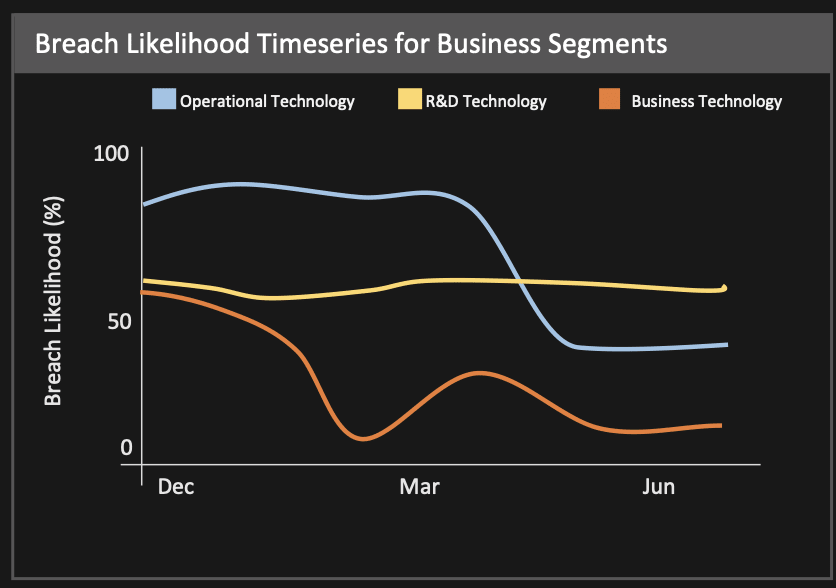
Overall, the most important way to adapt to changes in the IT landscape is to monitor the impact of those changes so that you can tune your infosec program to the risk tolerance of the organization as a whole. The result is that you can much more efficiently and effectively ensure that you’re getting the job of adapting to changes in the IT landscape done.



