Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information security issues. A CVE number uniquely identifies one vulnerability from the list. CVE provides a convenient, reliable way for vendors, enterprises, academics, and all other interested parties to exchange information about cyber security issues. Enterprises typically use CVE, and corresponding CVSS scores, for planning and prioritization in their vulnerability management programs.
First launched in 1999, CVE is managed and maintained by the National Cybersecurity FFRDC (Federally Funded Research and Development Center), operated by the MITRE Corporation. CVE is sponsored by the US Federal Government, with both the US Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA) contributing operating funds. CVE is publicly available and free for anyone to use.
Difference Between a Vulnerability and an Exposure
A vulnerability is a weakness which can be exploited to gain unauthorized access to or perform unauthorized actions on a computer system. Vulnerabilities can allow attackers to get direct access to a system or a network, run code, install malware, and access internal systems to steal, destroy, or modify sensitive data. . If it goes undetected, it could allow an attacker to pose as a super-user or system administrator with full access privileges.
An exposure is a mistake that gives an attacker access to a system or network. Exposures can allow attackers to access personally identifiable information (PII) and exfiltrate it. Some of the biggest data breaches were caused by accidental exposure rather than sophisticated cyber attacks.
CVE Background
Before CVE was started in 1999, it was very difficult to share data on vulnerabilities across different databases and tools. Each vendor maintained their own database, with their own identification system and different sets of attributes for each vulnerability. CVE ensures that every tool can exchange data with other tools, while also providing a mechanism by which different tools, such as vulnerability scanners, can be compared.
While some may question whether publicly disclosing vulnerabilities makes it easier for hackers to exploit those vulnerabilities, it is generally accepted that the benefits outweigh the risks. CVE includes only publicly known security exposures and vulnerabilities. This means that hackers could get their hands on data related to the CVE whether it is in the CVE list or not. Additionally, details of a CVE are often withheld from the vulnerability list until the corresponding vendor can issue a patch or other fix, ensuring that enterprises can protect themselves once the information is made public. Additionally, information sharing across the cybersecurity industry can help speed mitigations, as well as ensure that all organizations are protected more quickly than if left to identify and find resolutions to CVEs on their own.
How Are CVEs Determined?
CVE IDs are assigned to flaws that meet a specific set of criteria. They must be fixed independently of any other bugs, they must be acknowledged by the vendor as having a negative impact on security, and they must be affecting only one codebase. Flaws that impact more than one product get separate CVEs.

Understanding CVE Identifiers
Every CVE is assigned a number known as a CVE Identifier. CVE identifiers are assigned by one of around 100 CVE Numbering Authorities (CNAs). CNAs include IT vendors, research organizations like universities, security companies, and even MITRE themselves.
A CVE identifier takes the form of CVE-[Year]-[Number]. Year represents the year in which the vulnerability was reported. The number is a sequential number assigned by the CNA.
For example, CVE-2019-0708, corresponds to a flaw in Microsoft’s Remote Desktop Protocol (RDP) implementation. While CVE-2019-0709 might not sound familiar, you might recognize the common name given to this CVE, BlueKeep. Infamous CVEs, like BlueKeep, that get a lot of enterprise (and press) attention commonly get an informal nickname as an easy way to remember the vulnerability in question. A select few CVEs even get their own cool custom logo or graphic (often designed by the marketing teams at the vendor or organization looking to publicize information on the vulnerability to attract journalist interest):

Benefits of CVEs
- Sharing CVE details is beneficial to all organizations it allows organizations to set a baseline for evaluating the coverage of their security tools. CVE numbers allow organizations to see what each tool covers and how appropriate they are for your organization.
- By using the CVE ID for a particular vulnerability or exposure, organizations can quickly and accurately obtain information about it from a variety of information sources and coordinate their efforts to prioritize and address these vulnerabilities to their organizations more secure.
- Security advisories can use CVE vulnerability details to search for known attack signatures to identify particular vulnerability exploits
Who Reports CVEs?
Anyone can report a CVE to a CNA. Most commonly, researchers, white hat hackers, and vendors find and submit CVE reports to one of the CNAs. Many vendors actively encourage people to seek out vulnerabilities as a “free” way to improve upon the security posture of their products. In fact, many even offer bug bounties and other forms of contests and prizes to encourage the community to test, and find the flaws in, the security of their products.
The full list of CNAs includes many household names, including MITRE, Adobe, Apple, CERT, Cisco, Dell, Facebook, Google, IBM, Intel, and more.
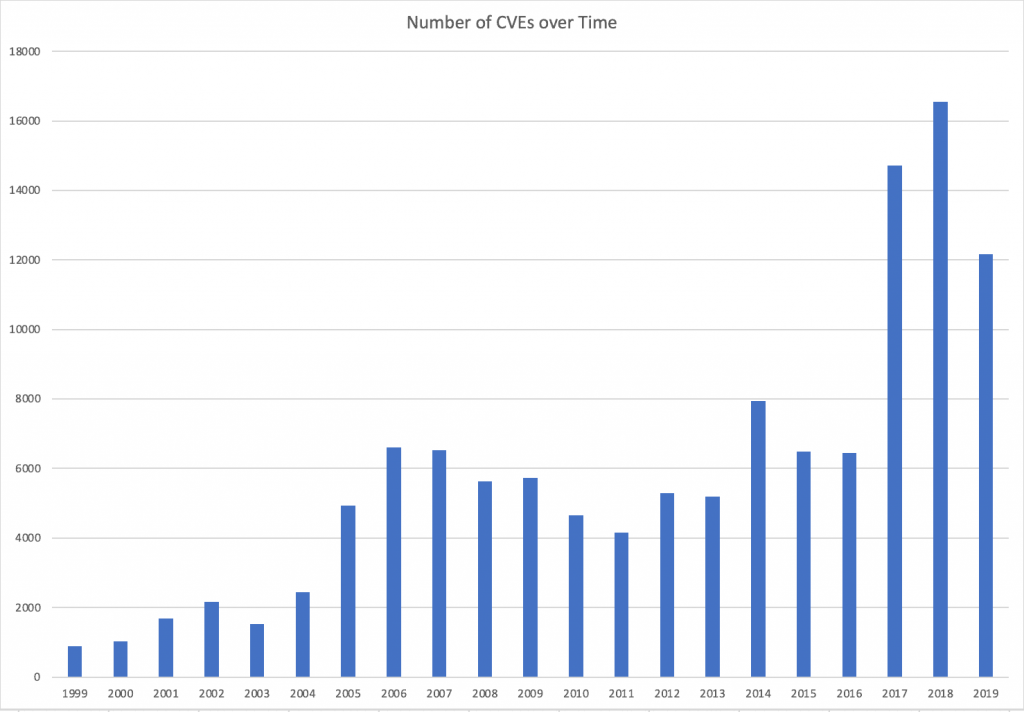
How Many CVEs Are There?
There are thousands of new CVEs every year. Since the CVE program was started in 1999, over 130,000 CVE Identifiers have been issued. Over the last few years, there have been 12,000-15,000 new CVEs annually.
Large software vendors with many products represent a large portion of the reported CVEs. Microsoft and Oracle, for example, each have over 6000 reported CVEs across their many product lines. In fact, the top 50 software vendors represent more than half of all CVEs issued since the inception of the CVE program.
What are the Limitations of CVE?
CVE is not meant to be a vulnerability database, so (by design) it does not contain some of the information needed to run a comprehensive vulnerability management program. In addition to the CVE identifier, the CVE entry includes only a brief description of the security vulnerability, and references to more information about the CVE, such as vendor advisories.
Additional information on each CVE can be found directly on vendor websites, as well as in the NIST National Vulnerability Database (NVD). The NVD provides CVSS Based Scores, fix information, and other important details often needed by information security teams that want to mitigate the vulnerability or assess its overall priority.
Additionally, CVE represents vulnerabilities in unpatched software only. While traditional vulnerability management programs viewed unpatched software as the primary issue for resolution, modern, risk-based approaches to vulnerability management recognize that there are many types of “vulnerabilities” introducing risk to an organization, all of which need to be identified and mitigated. Many of these do not fit the definition of a CVE and cannot be found in the CVE security list.