As the complexities of the cybersecurity landscape continue to rise, the ability to assess an organization’s vulnerabilities is crucial. Here, a scoring system serves as a critical navigational tool — providing a structured, standardized method for assessing the severity of vulnerabilities, turning a potentially overwhelming array of threats into a manageable list of priorities.
By quantifying the potential impact of each vulnerability, a scoring system enables organizations to make informed decisions about where to allocate their resources and protect their systems more effectively and efficiently. A scoring system essentially acts as the compass to guide organizations through an ever-expanding landscape of vulnerabilities.
Introduction to CVSS v4.0
The Common Vulnerability Scoring System (CVSS) is a commonly used method for assessing the severity of security vulnerabilities in digital systems. Developed by the Forum of Incident Response and Security Teams (FIRST), it provides a standardized approach for security professionals to evaluate and prioritize risks.
The latest version, CVSS v4.0, is a significant revision that offers a simpler, more flexible, and more accurate scoring system. This version addresses the limitations of the previous version, CVSS v3.0, by providing a more realistic representation of risks.
CVSS 4.0 Calculator
The CVSS 4.0 calculator is a tool used to assess the severity of vulnerabilities discovered in software systems. The calculator uses the metrics defined in the CVSS 4.0 standard to calculate a score that represents the potential impact of a vulnerability.
Breaking down the metrics
The calculator groups metrics into four key areas: base, threat, environmental, and supplemental — each of which contributes to the final score.
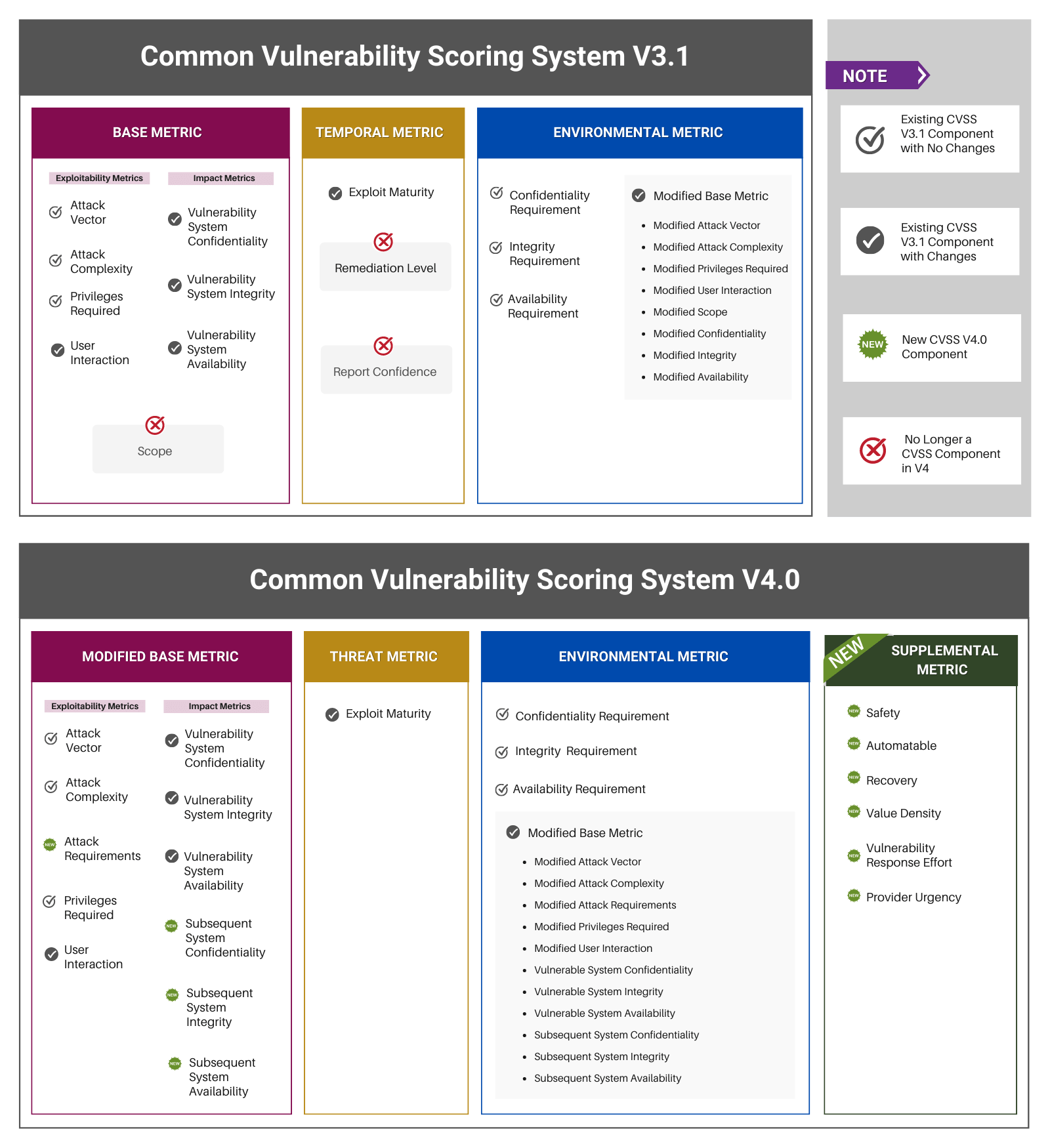
CVSS Base Metrics include exploitability metrics (such as Attack Vector, Attack Complexity, Attack Requirement, Privileges Required, and User Interaction) and vulnerable system impact metrics (such as Confidentiality, Integrity, and Availability) and subsequent system impact metrics (including Confidentiality, Integrity, and Availability) . These characteristics do not change over time and are not dependent on real-world exploitability or on compensating factors that an organization has put into place to prohibit exploitation.
CVSS Threat Metrics measure the current state of exploit techniques or code availability for a vulnerability. It includes a variable Exploit Maturity that measures the likelihood of the vulnerability being attacked
CVSS Environmental Metrics are modifiers to the base metric group. These are designed to account for the aspects of an enterprise that might increase or decrease the net severity of a vulnerability. Environmental metrics are made up of Exploitability Metrics, Vulnerable and Subsequent System Impact Metrics.
CVSS Supplemental Metrics are a new addition designed to provide additional context and describe extrinsic attributes of a vulnerability not covered by the other metric groups. These metrics are optional and can be used to provide a more comprehensive understanding of a vulnerability.
How does the current CVSS scoring system work?
To calculate a CVSS score, all the metrics are combined using a specific formula, resulting in a numeric score ranging from 0 to 10, with higher scores indicating more severe vulnerabilities.
The scores are categorized into four severity levels: Low (0-3.9), Medium (4-6.9), High (7-8.9), and Critical (9-10). Understanding the CVSS scoring system is vital for security practitioners, as it provides a consistent method to prioritize vulnerabilities and allocate resources to address the most pressing issues and concerns.
Decoding the CVSS Scoring System
The CVSS scoring system is like a lighthouse for cybersecurity vulnerabilities — providing a clear, reliable signal amidst the chaos, guiding security professionals safely through the treacherous waters of the digital landscape. Just as a lighthouse illuminates the path to safe harbor, the CVSS scoring system shines a light on the severity and potential impact of each vulnerability. The score’s metrics provide a comprehensive profile of each vulnerability, track its evolution over time, and allow customization based on an organization’s unique environment. The final score acts as a guide to allocate resources where they’re needed most.
Another way of looking at the CVSS scoring system is like a philosophy that challenges organizations to delve deeper into the nature of each vulnerability, to understand its origins, evolution, and potential impact.
CVSS v3.1 vs v4.0
CVSS v4.0 introduces several improvements over v3.1. Essentially, v4.0 offers enhanced clarity and simplicity, greater flexibility and adaptability, and improved representation of real-world risk. It also introduces new concepts such as “Automatable,” “Recovery,” and “Mitigation Effort,” which add depth to the understanding of each vulnerability.
More importantly, v4.0 makes significant adjustments to the framework, such as replacing the Temporal metric group with the Threat metric group and introducing a new Supplemental metric group.
CVSS v4.0 enables organizations to gain a deeper, more nuanced understanding of each vulnerability, thus driving changes and leading the charge toward a more secure digital future.
The evolution from CVSS v3.1 to v4.0 represents a transformation in our ability to learn, adapt, and improve. The change has evolved from a world of static, one-size-fits-all scores to a dynamic, customizable scoring system that reflects the unique needs and challenges of each organization.
Alternatives to CVSS and their benefits
While CVSS is a widely adopted scoring system, other alternatives may better suit an organization’s needs. These include the Exploit Prediction Scoring System (EPSS), Microsoft’s DREAD model, OWASP’s Risk Rating Methodology, NIST’s Common Misuse Scoring System (CMSS), and the MITRE ATT&CK framework.
- The Exploit Prediction Scoring System (EPSS) uses machine learning to predict the likelihood of a vulnerability being exploited, and offers a more forward-looking and proactive approach to risk assessment.
- Microsoft’s DREAD model, designed specifically for software vulnerabilities, offers a simple and straightforward scoring system that’s easy to understand and implement.
- OWASP’s Risk Rating Methodology provides a flexible framework that can be tailored to the specific needs and context of an organization, allowing for a more customized approach to vulnerability management.
- NIST’s Common Misuse Scoring System (CMSS) focuses on the misuse of software, offering a unique perspective on software vulnerabilities that complements traditional scoring systems.
- The MITRE ATT&CK framework provides a comprehensive overview of the tactics, techniques, and procedures (TTPs) used by attackers, offering valuable insights into the threat landscape. It’s important to note that while CVSS helps with vulnerability assessment and prioritization, the ATT&CK framework promotes understanding the threat landscape and improving defense strategies.
These alternatives represent opportunities to tailor vulnerability management strategies to specific needs. Ultimately, using one framework is great; more than one is even better.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

How to choose an effective scoring system?
Choosing a scoring system involves evaluating various factors, including:
- The system’s ability to accurately mirror real-world risk
- Its adaptability to the organization’s specific context
- The clarity of its methodology
- Its compatibility with existing operational workflows and tools
The right scoring system should align with the organization’s risk posture, cybersecurity strategy, and overall business objectives. Choosing properly can significantly impact an organization’s ability to manage vulnerabilities and maintain a robust security posture.
Here’s an analogy: choosing an effective scoring system for assessing vulnerabilities is like selecting the right tool for a job. Just as you wouldn’t use a hammer to drive in a screw, you wouldn’t want to use a scoring system that doesn’t align with your organization’s specific needs and context.
Here are some considerations to keep in mind:
Real-World Risk Representation: Just as a weather forecast model should accurately predict the weather conditions, your scoring system should accurately reflect the real-world risks to your organization. It should consider factors like the likelihood of a vulnerability being exploited and the potential impact of that exploit.
Adaptability: Like a multi-tool that can adapt to various tasks, your scoring system should be flexible enough to account for your organization’s unique environment and threat landscape, and should allow for customization to reflect specific organizational characteristics and priorities.
Clarity and Ease of Use: A scoring system should be as easy to understand and use as a well-designed tool. It should provide clear and straightforward metrics and methodologies, reducing subjectivity and the potential for misinterpretation.
Compatibility: Just as a power tool should be compatible with the power outlets in a workshop, your scoring system should be compatible with your existing operational workflows and tools. It should integrate seamlessly into your vulnerability management processes and systems.
Alignment with Objectives: The scoring system should align with your organization’s risk posture, cybersecurity strategy, and overall business objectives.
By considering these factors, you can choose a scoring system that not only provides useful and practical scores but also enhances your overall vulnerability management process. With the right system or systems, you can work more effectively and efficiently, ensuring the security of your organization’s systems and data.
For organizations interested in vulnerability prioritization, Balbix provides a comprehensive view of vulnerabilities and prioritizes the ones most critical to your organization.
How can Balbix help?
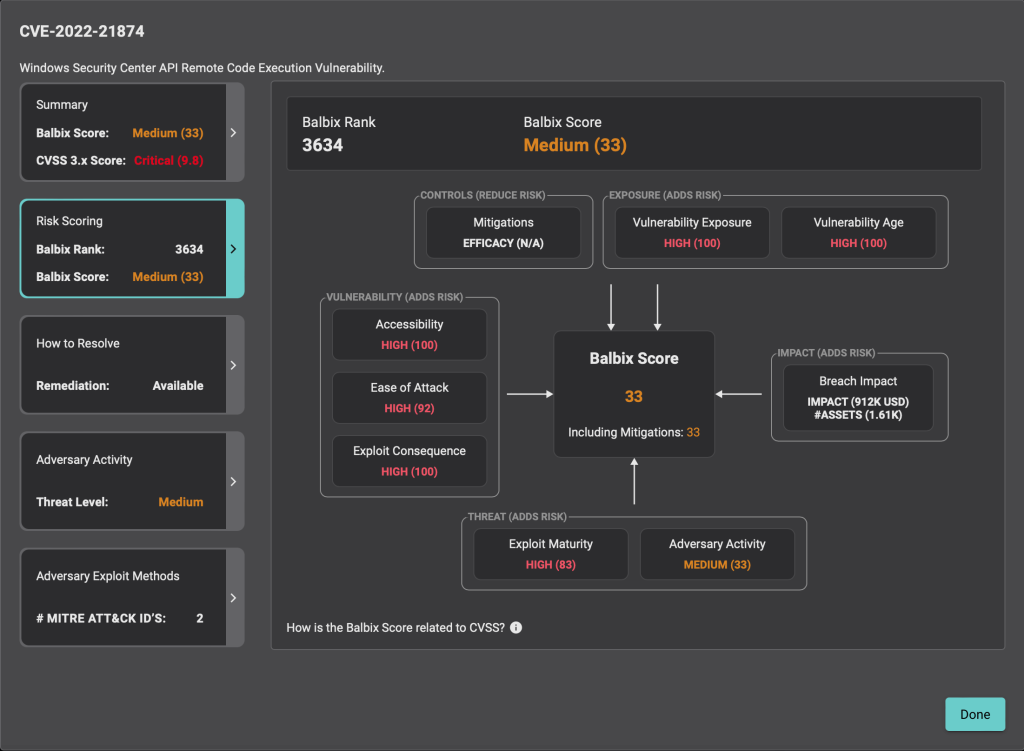
Balbix uses a proprietary scoring system, ‘Balbix Score & Rank’, to assess vulnerabilities. This system transcends conventional methods by integrating critical parameters: vulnerability characteristics, threat indicators, and real risk factors. While the CVSS primarily focuses on vulnerability parameters, such as attack vector, complexity, and impact consequences, Balbix’s system further incorporates a threat-based vulnerability management approach by including knowledge of exploits, their availability, and predictability.
Balbix’s Score and Rank system uniquely takes real risk factors into account. It calculates the exposure level of each vulnerability instance, checks the effectiveness of mitigation measures, considers the age of vulnerabilities, and assesses the present and potential future impacts if these vulnerabilities were to be exploited.
This comprehensive view allows Balbix to identify which vulnerabilities need immediate patching precisely and to prioritize them based on the increased likelihood and risk of a breach for the identified assets. Consequently, Balbix offers a holistic and prioritized view of vulnerabilities, fostering more effective risk management.
Let’s consider an example: CVE-2022-21874 (WINDOWS SECURITY CENTER API RCE)
This example features a vulnerability with a critical CVSS score of 9.8 and a medium threat level but still results in a medium Balbix score. The screenshot below displays the details of the Balbix score. The score is lower due to fewer external threat factors, such as the absence of known exploits and the medium severity of overall adversary activity and exploits maturity.