Vulnerability management relies on prioritization to decide which vulnerabilities to mitigate and when. The Common Vulnerability Scoring System (CVSS) is a widely used framework that calculates the severity of vulnerabilities and allows them to be compared across environments.
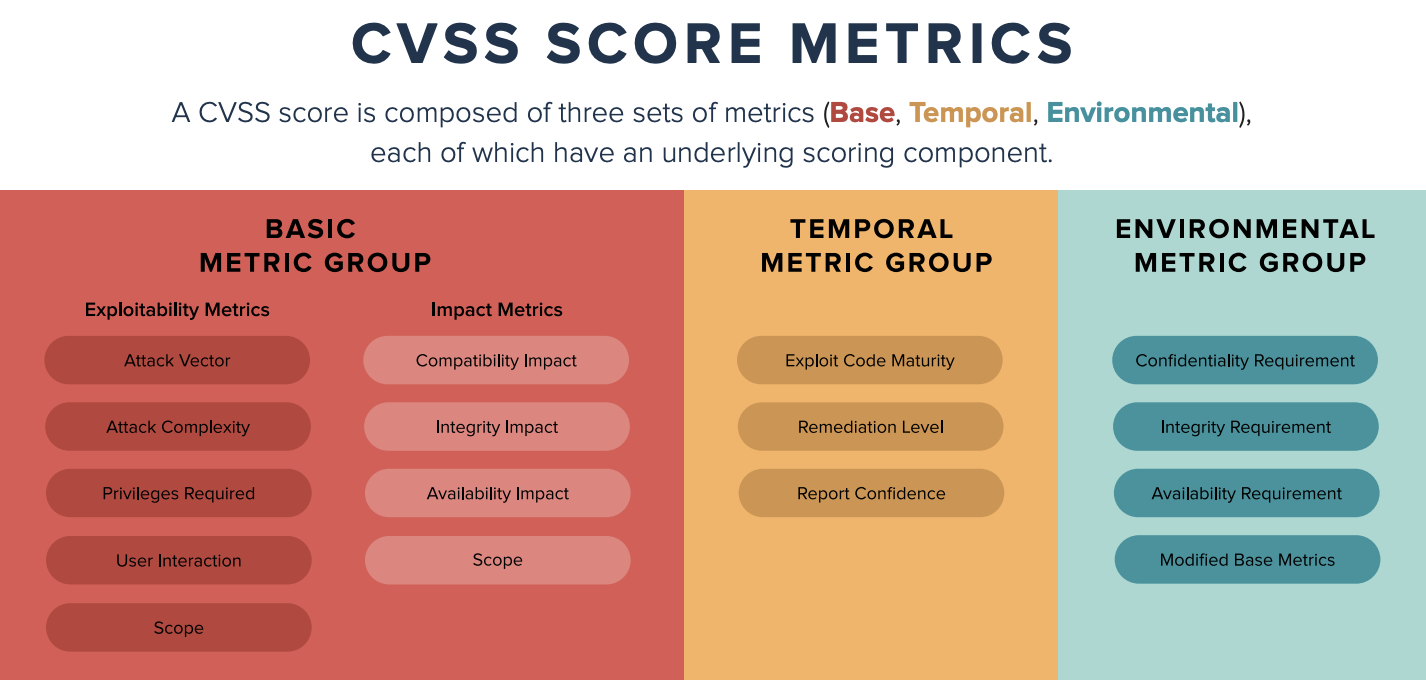
CVSS scores range from 0 to 10 and consist of Base, Temporal, and Environmental metric groups. Each group assesses different aspects of a vulnerability.
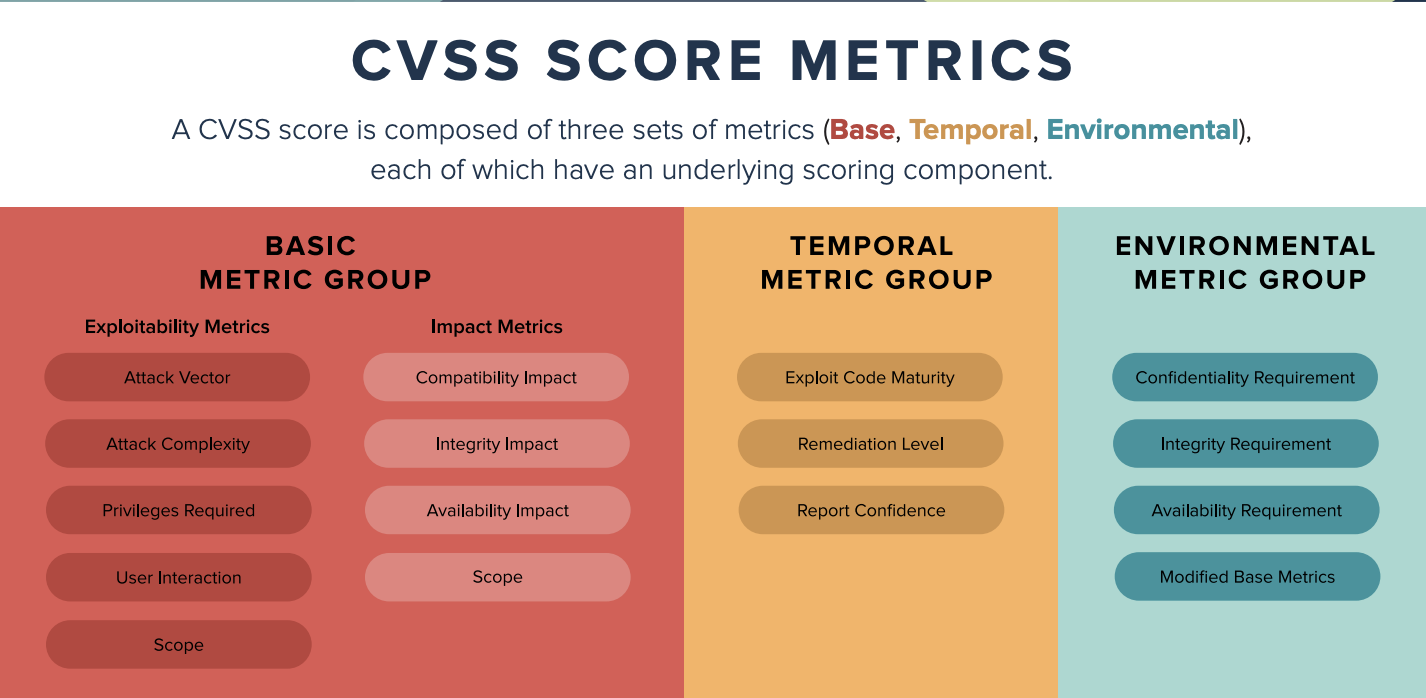
Base Metrics: The Static Core
Base metrics measure the intrinsic qualities of a vulnerability that remain constant over time. These metrics are reported in public databases such as NIST’s National Vulnerability Database (NVD) and are the most commonly referenced components of CVSS. However, they only provide a snapshot of the vulnerability’s potential impact without considering the evolving threat landscape.
Environmental Metrics: Enterprise-Specific Factors
Environmental metrics tailor CVSS scores to an organization’s unique environment. These metrics assess affected systems’ business criticality and compensating controls’ effectiveness. Since they are specific to each enterprise, environmental metrics vary significantly from one organization to another.
Temporal Metrics: The Changing Landscape
In contrast to the static nature of base metrics, temporal metrics capture the evolving nature of a vulnerability over time. These metrics reflect the availability of exploits and patches and the confidence in the vulnerability’s description. Temporal metrics offer a dynamic view of risk, making them crucial for vulnerability management.
CVSS Temporal Metrics Breakdown
Temporal metrics focus on the current state of a vulnerability in the wild. According to the Forum of Incident Response and Security Teams (FIRST), temporal metrics assess the maturity of exploit code, remediation availability, and report confidence. Let’s break down these key factors:
Exploit Code Maturity
Exploit code maturity measures whether a vulnerability has been weaponized. Some vulnerabilities are only exploitable in a lab environment while others have fully functional exploit code actively used by attackers. The more widely available and reliable the exploit code, the higher the temporal score.
- High (H): Widely available, reliable, easy-to-use exploit code.
- Functional (F): Exploit code exists but may require some skill.
- Proof-of-concept (P): Code exists but is not fully reliable.
- Unproven (U): No known exploit code.
Remediation Level
This metric indicates the availability of patches or workarounds. As remediation options mature and become available, the vulnerability’s temporal score decreases, reflecting the reduced risk.
- Official Fix (O): A permanent fix is available.
- Temporary Fix (T): A vendor-created temporary solution exists.
- Workaround (W): There’s an unofficial patch or mitigation.
- Unavailable (U): No fix or patch exists.
Report Confidence
This measures the confidence in the vulnerability’s existence and details. Higher confidence reduces the uncertainty surrounding the vulnerability, affecting prioritization.
- Confirmed (C): Verified by multiple sources, including the vendor.
- Reasonable (R): Public details exist, but verification is pending.
- Unknown (U): Reports exist, but validity is uncertain.
Temporal Metrics vs. Base and Environmental CVSS Scores
While base metrics offer a snapshot of the vulnerability’s potential impact, they fail to account for real-world factors like exploit availability or patch development. Temporal scores add this evolving context, updating the vulnerability’s severity as new information emerges, such as exploit code being developed or a vendor releasing a patch.
Stop Sabotaging Your Cybersecurity
Avoid the 11 common vulnerability management pitfalls

In contrast, environmental scores consider how a specific organization is affected by the vulnerability, considering compensating controls or the criticality of vulnerable assets. Unlike temporal scores, which change based on external factors like the availability of exploits or patches, environmental scores reflect the organization’s internal risk factors.
For example, a vulnerability might have a high base score but be downgraded by a low temporal score if a widely available patch reduces the risk. Conversely, the environmental score may vary significantly depending on how critical the affected systems are to a particular organization.
Operationalizing CVSS Scores with Temporal Metrics
CVSS base scores are often the starting point for vulnerability management, but focusing solely on them can lead to an incomplete picture. To assess and prioritize vulnerabilities accurately, you must account for temporal and environmental factors.
Including temporal metrics in your vulnerability management workflow helps ensure that you’re responding to current threats, such as newly developed exploits or patch availability. By integrating all three CVSS components, organizations can prioritize remediation efforts and mitigate risk more effectively.
Understanding the differences between base, temporal, and environmental scores allows security teams to make informed decisions, ensuring they focus their resources on vulnerabilities that pose the most significant current risk.
Frequently Asked Questions
- Is CVSS a risk assessment?
-
CVSS, or the Common Vulnerability Scoring System, is not a risk assessment tool but rather a standard for assessing the severity of security vulnerabilities. Its scores provide an initial overview but lack the context of the broader risk landscape, which involves considering specific environmental factors and potential impacts on the affected organization.
- What is the difference between CVE and CWE?
-
The difference between CVE (Common Vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) lies in their focus. CVE identifies specific vulnerabilities in software and hardware, providing a unique identifier for each known vulnerability. CWE, on the other hand, categorizes common types of software weaknesses and errors, offering a comprehensive classification for vulnerability types rather than individual instances.
- How do Temporal Metrics differ from Base and Environmental Metrics?
-
Temporal Metrics, part of the CVSS scoring system, differ from Base and Environmental Metrics by focusing on factors that change over time, such as the availability of exploits or the maturity of countermeasures. Base Metrics assess the intrinsic qualities of a vulnerability that are constant over time and context, while Environmental Metrics tailor the CVSS score to reflect the specific impact on an organization, taking into account its unique environment and mitigations.