

May 1, 2024

The Verizon DBIR is the most anticipated annual report on data breaches with many incredible insights, and this year is no exception. The most surprising finding is the rapid explosion in vulnerability exploitation, which now constitutes one of the most critical paths to initiating breaches.
Balbix is a data contributor to Verizon DBIR, and we have poured over this report to provide seven key actionable takeaways to enable you and your organization to navigate the riskiest areas of cyber risk and deliver suggestions to improve your security.
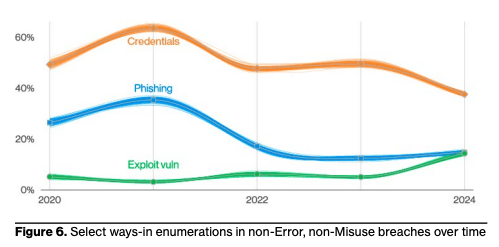
This year has seen a 180% increase in vulnerability exploits, with the MOVEit vulnerability and other zero-day exploits increasingly leveraged by ransomware and extortion-related threat actors.
Recommendation: Use a Risk-Based Approach to Remediating Vulnerabilities
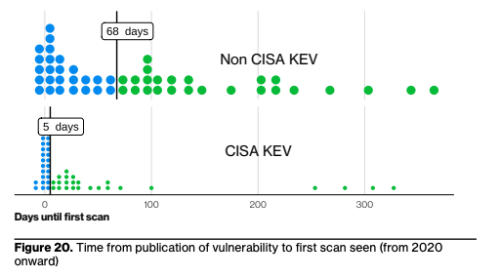
The median time from initial vulnerability publication to first detection of adversary scanning activity for CISA KEV is five days, compared to 68 days for non-CISA KEV CVEs.
Recommendation: Prioritize Remediation of CISA KEV Listed Vulnerabilities
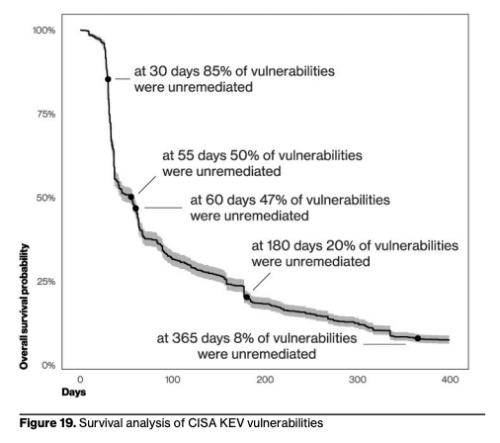
By doing a survival analysis of vulnerability management data and focusing on the vulnerabilities in the CISA Known Exploited Vulnerabilities (KEV) catalog (an area of focus in vulnerability management), the report found it takes around 55 days to remediate 50% of those critical vulnerabilities once their patches are available. The patching doesn’t start picking up until after the 30-day mark, and by the end of the year, around 8% are still open.
Recommendation: Track Vulnerability Management Metrics such as Mean Open Vulnerability Age (MOVA) and Mean Time to Remediate (MTTR).
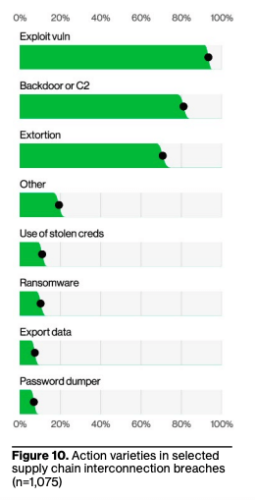 Key DBIR Finding #4: Third-Party Vulnerabilities Are on the Rise
Key DBIR Finding #4: Third-Party Vulnerabilities Are on the RiseThird-party vulnerabilities (e.g., SaaS, business, and open-source apps) are rising. Supply chain interconnection influenced 15% of the breaches this year, a significant increase from 9% last year.
Recommendation: Understand your software supply chain and maintain an accurate and up-to-date Software Bill of Materials (SBOM).
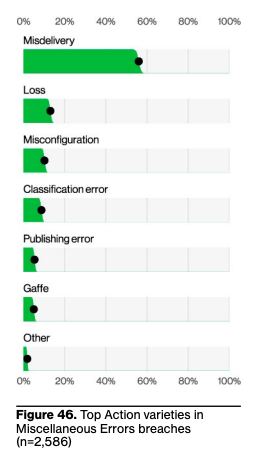
Misconfigurations were seen in approximately 10% of breaches. While on a downward trend they still pose a considerable risk of exploitation.
Recommendation: Monitor Software Configurations and leverage automated techniques to identify and remediate misconfigurations.
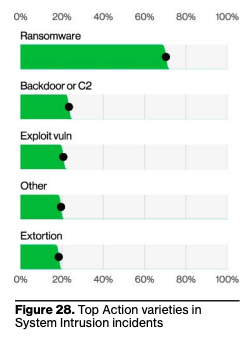 Key DBIR Finding #6: Ransomware/extortion Is Still Dominant
Key DBIR Finding #6: Ransomware/extortion Is Still DominantRoughly one-third of all breaches involve Ransomware or Extortion. Extortion attacks, which are less familiar to many, may or may not involve actual access to data like ransomware but use the threat of damage or disclosure to coerce payment. These attacks have risen over the past year and are now a component of 9% of all breaches (as opposed to a decline in Ransomware to 23%.)
Recommendation: Backup Data and monitor all systems, software and applications for high-severity vulnerabilities and patch them before they can be exploited by ransomware.
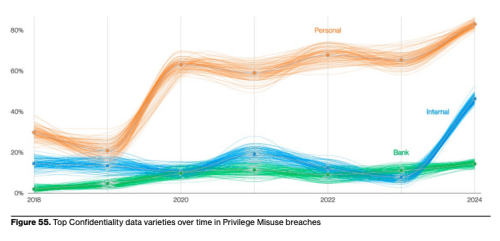 Key DBIR Finding #7: Privilege Misuse Is Growing
Key DBIR Finding #7: Privilege Misuse Is GrowingSocial engineering and abuse of privileges have been an evergreen challenge. Yet, the latter is increasingly used by internal bad actors (35%, a significant increase from last year’s 20%.) vs. external attackers (65%).
Recommendation: Adopt a zero-trust mindset, enforce the principle of least privilege and implement MFA.
By implementing these 7 suggestions, your organization can enhance its defensive mechanisms, stay ahead of potential threats, and foster a more secure operational environment. Embracing these insights will not only safeguard your data and systems but also reinforce your organization’s commitment to maintaining cyber resilience. In the digital age, an informed and proactive approach to cybersecurity is not just an option—it is a necessity.