
June 20, 2023
May Microsoft Patch Tuesday Releases fixes for 38 new CVEs including 6 Microsoft-rated critical vulnerabilities and 2 new zero-day vulnerabilities, 1 update to a previously reported exploitable vulnerability as well as 12 other updates to previously released CVEs.
This month, Microsoft announced fixes for 78 new CVEs including 6 Microsoft-rated critical vulnerabilities. This month there were no new zero-day vulnerabilities disclosed however there were 2 updates to previously reported exploitable vulnerabilities (CVE-2023-24880 and CVE-2021-34527) as well as 9 other updates to previously released CVEs and advisories.
Of the 78 new vulnerabilities, the fix sources break down as follows:
This month’s headline issues are the continuing exploitation of the soon-to-be End of Life (EOL) operating system Windows Server 2012 R2 (EOL October 2023). The three vulnerabilities all rank a base CVE score of 9.8 and either provides remote code execution capability. The three CVEs in question affect the Windows Pragmatic General Multicast (PGM). Pragmatic General Multicast (PGM) is a protocol designed to deliver packets between multiple network members in a reliable manner. On Windows, the implementation of this protocol is referred to as reliable multicast.
As always, Balbix can identify all affected assets within hours of release. There are no scans to run. Balbix customers search for the CVE name in their Balbix dashboard to view the list of affected assets. Filtered search functionality can also be used to search for the CVE by site, subnet, location, or other distinguishing factors.
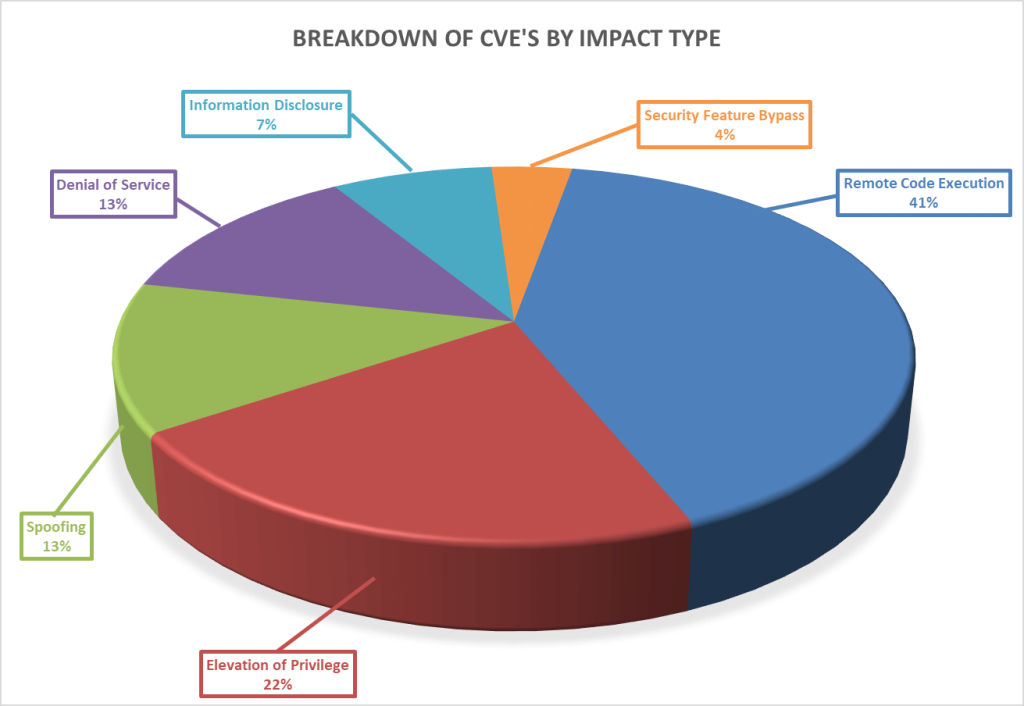
Breaking down the 78 vulnerabilities further by impact type, we can see that remote code execution leads the way again this month with an elevation of privileges and information disclosure tied right behind it.
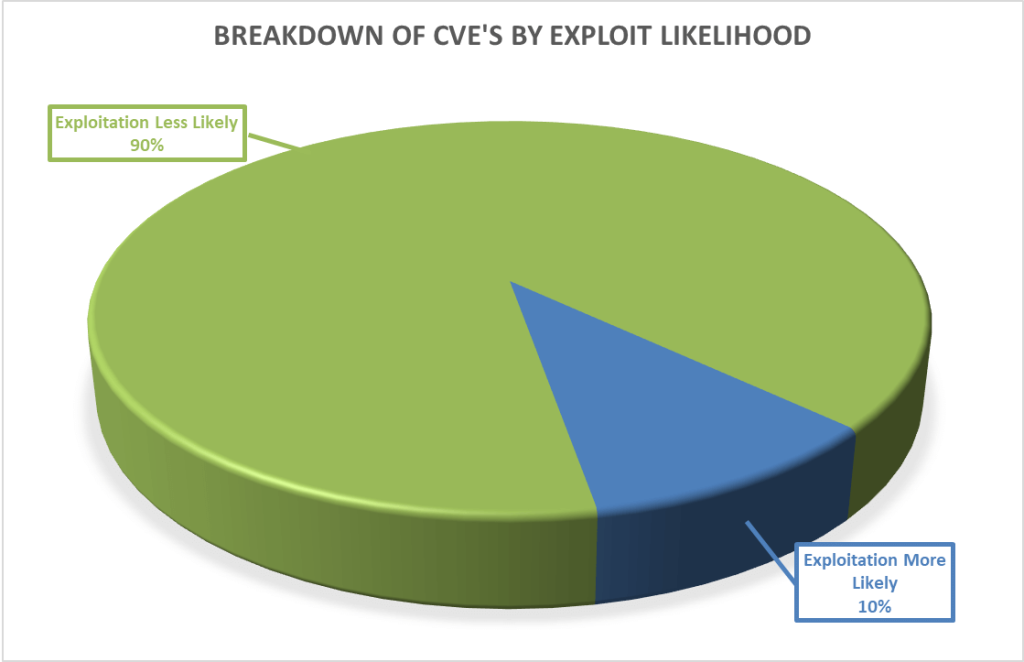
Furthermore, as can be seen below, these vulnerabilities vary in terms of how likely they are to be exploited, with 26% of the vulnerabilities this month either already exploited or highly likely to be exploited as ranked by the Microsoft Exploitability Index
As always, Balbix can identify all affected assets within hours of release. There are no scans to run. Balbix customers search for the CVE name in their Balbix dashboard to view the list of affected assets. Filtered search functionality can also be used to search for the CVE by site, subnet, location, or other distinguishing factors.
If you have additional questions, please contact support@balbix.com.