
November 1, 2023
In a classic tale from ancient India, a few blindfolded individuals approach an elephant, each examining a different part. One touches the trunk and believes it resembles a snake. Another feels a leg and thinks it’s a tree. Yet another, holding the tusk, considers it a spear. Although each one’s perception is genuine based on their limited interaction, none sees the complete picture of the elephant.
This tale offers an enlightening parallel to the multifaceted challenges cybersecurity teams face in today’s organizations. Just as in the ancient story, different stakeholders—be they from Leadership (CEO, CFO, CISO), Vulnerability Management (VM), or Governance, Risk Management, and Compliance (GRC)—often hold divergent views of what constitutes ‘cyber risk.’
This is not merely a theoretical parallel, as a security leader from a major insurance firm recently shared with us:
‘In our infrastructure with disparate cybersecurity tools, we see fragmented perceptions of risk. Each tool, operating in its own silo, leads different functions—the Board, SecOps, or GRC—to interpret risk in their unique ways. This often leads to strategies that are misaligned and hampers efforts to take a cohesive approach.'”
So, what causes this fragmented understanding of cyber risk?
In the following chart, we zoom in on the core operations that make up enterprise cybersecurity. Specifically focused on cybersecurity risks, this illustration shows how these components work together proactively to mitigate such risks.
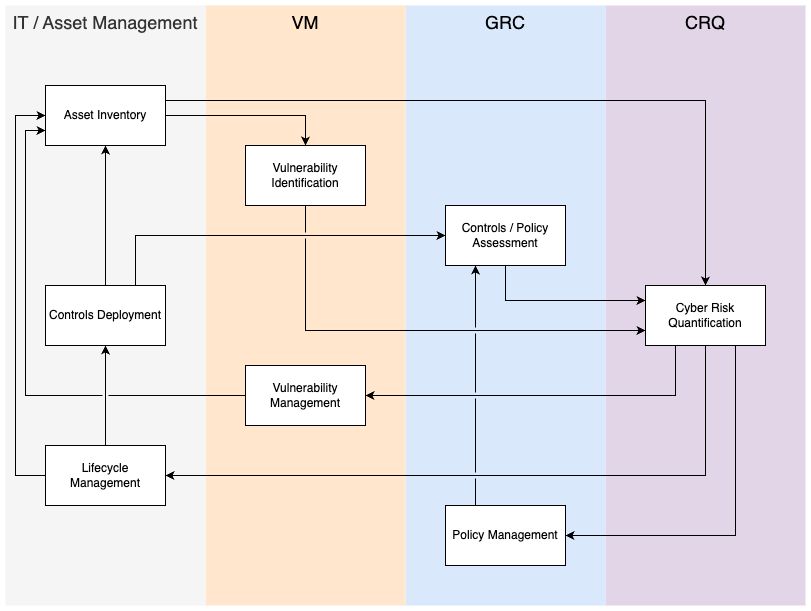
While each operation serves its indispensable purpose, the strength and effectiveness of an organization’s cybersecurity posture hinge on each function’s symbiotic relationships. To understand this better, let’s delve into some scenarios:
Siloed Operations: While ‘Asset Inventory’ under the ‘IT/Asset Management’ operation plays a foundational role, its effectiveness—and potential discrepancies between inventory and actual assets—directly influences ‘Vulnerability Identification’ in VM. If assets aren’t inventoried correctly, vulnerabilities can be overlooked. This is an example of how a process residing in one silo impacts the efficacy of another. Adding another layer of complexity is the challenge of accountability. In such a siloed environment, determining who is responsible for risk reduction becomes a pressing question.
Interdependent Dynamics: Delving deeper, the “Controls/Policy Assessment” in GRC, when done in isolation, might seem adequate. But if it doesn’t account for real-time vulnerabilities (from VM) or the up-to-date asset lifecycle (from IT/Asset Management), the controls and policies may not be as robust as assumed. GRC, IT/Asset Management, and VM aren’t merely isolated departments; they are cogs in a giant machine working towards making the organization secure.
Unified Vision: CRQ acts as the barometer, measuring the efficacy of all other processes. However, CRQ needs to be informed by every process. For instance, if the output of “Controls Deployment” in IT/Asset Management isn’t accurate, it could impact quantified risk, potentially underestimating threats. Moreover, CRQ should guide and inform other operations; for instance, whether the policies from GRC are sufficient for an enterprise to achieve its risk management goals depends on CRQ’s assessment of the residual risk, irrespective of existing policy enforcement.
Compartmentalization of Tools: Different teams use different tools optimized for their specific needs. While efficient in their respective functions, these tools are often not designed to share data or insights seamlessly with other tools.
Vendor Dependence and Technological Evolution: Organizations often rely heavily on specific vendor ecosystems, making it difficult to integrate third-party solutions. When coupled with the fast pace of technological advancements, existing tools and strategies can quickly become outdated.
Organizational Hierarchies: Silos often develop in traditional corporate structures as individual departments focus on their own specific goals.. In many cases, different departments have different goals, KPIs, skill requirements, and operational boundaries.
Lack of a Unified Strategy: Security leaders need a clear, unified strategy and should communicate this vision so everyone understands how each team depends on the others. Without a focused plan that pushes for teamwork and integration, different operations can easily drift apart.
Mastering individual domains like IT/Asset Management, VM, GRC, and CRQ is crucial, but it’s their integrated functioning that ensures a robust cybersecurity defense.
1. Ineffective Risk Prioritization: With non-uniform risk understanding, critical threats will likely get incorrectly prioritized.
Example: The IT team allocates most of its budget to updating legacy systems, perceiving them to be the highest risk. Meanwhile, the VM team, alarmed by a rise in ransomware attacks, argues that immediate investment in advanced threat protection is the real priority. Without a shared, quantified understanding of cyber risk, both departments proceed according to their own risk assessments, leading to an uncoordinated defense strategy
2. Wasted Resources & Budget: Misunderstanding risks across departments can lead to misallocated funds, causing inefficiencies.
Example: A major IT upgrade program has eaten a large chunk of the budget, leaving VM without the budget to update their tools stack.. Both areas are essential, but the mismatched allocation hinders comprehensive cybersecurity efforts, potentially leaving the organization vulnerable to cyber threats.
3. Delayed Incident Responses: A fragmented perception of risk can lead to slower reaction times during crucial incidents, escalating damage.
Example: In high-stakes scenarios, for instance, the zero-day exploits—actively exploited in the wild—the VM team typically understands the imperative need for immediate action. However, the IT team is typically constrained by change management protocols, necessitating delays for compatibility tests before deploying a patch.
4. Regulatory & Legal Repercussions: Misjudged risks can result in non-compliance with industry regulations, attracting legal complications and penalties.
Example: In light of the new SEC rulings on the materiality of cybersecurity incidents, a company downplays a data breach as non-material. Later, it faces severe regulatory backlash for non-disclosure.
5. Erosion of Leadership Confidence: If risks are misinterpreted or overlooked, it can result in significant breaches, undermining leadership and board confidence.
Example: The leadership believes the organization’s cybersecurity posture is strong based on frequent but low-impact security incidents reported. However, a major undetected breach later surfaces, shaking the board’s trust in the security team leadership’s competence.
The shortcomings in our current understanding of cyber risk don’t just stem from gaps between departments; they arise from the absence of a unified risk framework that ties everything together.
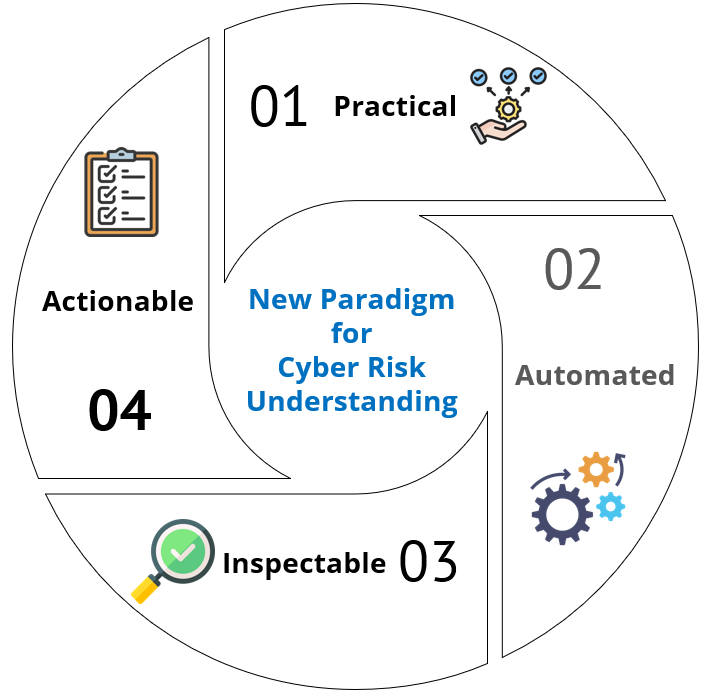
To address this, consider adopting an approach characterized by the following principles:
Practical:
Should be highly data-driven, using near-real-time inputs for risk calculations. It must consider each asset’s IT, cybersecurity, and business context to ensure an accurate and relative representation of risk.
Automated:
Should eliminate manual data crunching and one-off analyses. It must be automated, calculating risk using up-to-date asset-level data, including vulnerabilities, threats, exposure, applicable security controls, and business criticality.
Inspectable:
Should provide transparency into its calculations, offering insights on what drives higher likelihood and impact.
Actionable:
Should provide actionable insights and automate the workflow for risk mitigation. Following remediation actions, the risk calculations should immediately update the model.
In this blog, we’ve explored the challenges of fragmented views on cyber risk across various organizational roles, including GRC, VM, and the leadership. We described a unified, quantifiable approach to build a shared understanding of cyber risk. In an upcoming blog, we will explore how Balbix acts as a unifier, coalescing all dimensions of risk into a single, comprehensive model, creating a shared language of risk in cybersecurity.
See it in Action: To learn more, schedule a 30-minute demo and experience our CRQ model in action. It allows security leaders to consolidate their cybersecurity data into a comprehensive model. As a result, everyone—from security analysts to board members—gains a dollar-value perspective on cyber risk.