Asset inventory management tracks and manages an organization’s hardware, software, and network-connected devices. This includes physical and virtual assets, such as software licenses, servers, mobile devices, Internet of Things (IoT) devices, and unmanaged assets. An accurate inventory is essential for maintaining control over your organization’s IT environment and ensuring all assets are accounted for in your cybersecurity strategy.
An effective asset inventory management system provides real-time insights into your infrastructure, helping you to manage risk, improve operational efficiency, and maintain compliance.
Why Asset Inventory Management is Critical for Cybersecurity
As organizations evolve and expand their digital footprint, they become increasingly vulnerable to cyber threats. New devices, applications, and users are constantly added, creating an ever-changing attack surface. Security gaps can emerge without a robust asset inventory management system, exposing your organization to cyber risks.
Here’s why asset inventory management is crucial for your cybersecurity posture:
- Visibility and Control: Real-time visibility into all assets helps you identify potential security gaps and address vulnerabilities before they are exploited.
- Compliance and Governance: Accurate asset inventories ensure you meet regulatory requirements, such as GDPR or HIPAA, by clearly understanding where sensitive data resides.
- Risk Management: With asset inventory management, you can assign risk profiles to each asset and prioritize remediation efforts based on their criticality to your business.
Key Questions to Ask About Your Asset Inventory
When evaluating the effectiveness of your asset inventory management, consider the following:
- Do you have a comprehensive inventory of all assets, including users, applications, and devices?
- Can you track real-time changes to ensure your security measures keep pace with new threats?
- Can you prioritize assets based on their business impact and potential risk?
- Do you have continuous monitoring to detect unauthorized devices or rogue software?
- Is your asset inventory system automated to minimize manual errors and keep data up to date?
The Importance of Real-Time Asset Inventory Management
Static or outdated asset inventories can lead to blind spots in your security posture. To truly protect your organization, real-time asset inventory management is essential. This requires automated systems that continuously discover, track, and manage assets across your entire infrastructure.
Here’s why real-time asset inventory is vital:
- Continuous Discovery: Your organization constantly adds, removes, or changes assets. An automated system ensures that all devices and applications, whether on-premises, in the cloud, or mobile, are immediately identified and added to the inventory.
- Accurate Risk Assessment: Real-time asset tracking lets you quickly assess your network’s security posture. Based on this data, you can prioritize security measures, ensuring your critical assets are protected first.
- Proactive Threat Mitigation: With real-time monitoring, you can quickly detect and respond to suspicious or unauthorized activity. This proactive approach reduces the likelihood of a successful cyber attack.
Benefits of an Automated Asset Inventory System
An automated asset inventory system brings several advantages to your organization, ensuring that your IT environment remains secure and efficient:
- Improved Efficiency: Automated systems reduce the time and effort required for manual asset tracking, allowing your IT team to focus on higher-value tasks.
- Enhanced Accuracy: Manual asset inventories are prone to errors. Automation ensures that your inventory is always up-to-date and accurate.
- Seamless Integration with Security Tools: Automated asset management platforms integrate with your existing security tools, such as vulnerability scanners and firewalls, enabling a unified security approach.
- Real-Time Dashboards: Centralized dashboards provide instant access to asset data, enabling faster decision-making and a more efficient incident response process.
How to Implement Asset Inventory Management
To implement a successful asset inventory management program, follow these steps:
- Identify All Asset Types: Identify the assets that need to be tracked, including physical devices, software, virtual machines, and cloud-based assets.
- Choose the Right Tools: Select an asset management platform that offers automated discovery, real-time tracking, and integration with your existing security systems.
- Assign Risk Profiles: Assign risk profiles to each asset based on its business criticality and potential security vulnerabilities.
- Monitor Continuously: Ensure continuous monitoring to detect any changes in your asset inventory and to identify potential security threats in real time.
- Enforce Compliance: Use automated systems to ensure compliance with regulatory frameworks and internal policies. This includes tracking software licenses, hardware upgrades, and cloud services.
Tools and Best Practices for Asset Inventory Management
To maximize the effectiveness of your asset inventory management program, consider the following tools and best practices:
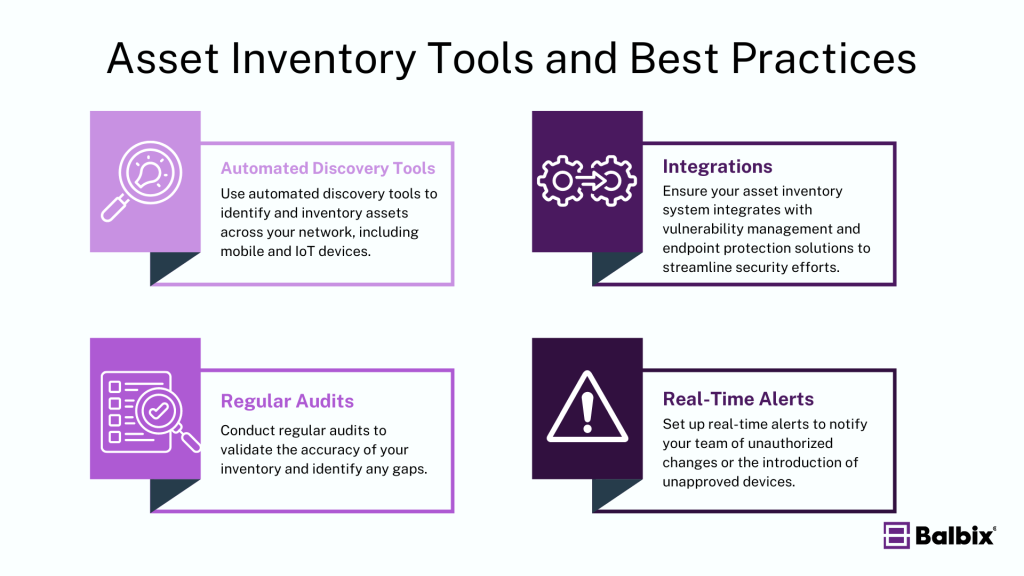
- Automated Discovery Tools: Use automated discovery tools to identify and inventory assets across your network, including mobile and IoT devices.
- Regular Audits: Conduct regular audits to validate the accuracy of your inventory and identify any gaps.
- Integration with Security Solutions: Ensure your asset inventory system integrates with vulnerability management and endpoint protection solutions to streamline security efforts.
- Real-Time Alerts: Set up real-time alerts to notify your team of unauthorized changes or the introduction of unapproved devices.
Asset inventory management is the foundation of a strong cybersecurity posture. With solutions like Balbix, which provides continuous visibility and real-time risk assessments across all assets, you can enhance your asset inventory management. Balbix’s AI-powered platform enables you to automatically discover, monitor, and assess your asset landscape, transforming inventory management from a reactive task into a proactive strategic advantage that strengthens your overall cybersecurity posture.
Frequently Asked Questions
- Why is asset inventory management important for cybersecurity?
-
Think of asset inventory management as knowing every door and window in a house to make sure they’re all locked to keep burglars out. In an organization, it helps you see all the “entry points” that hackers might target. By keeping track of all your digital “doors and windows” (your assets), you can better protect them from cyber threats.
- How does real-time asset inventory management help?
-
Real-time asset inventory management is like having a security camera that gives you live footage of what’s happening. It lets you see instantly if something new pops up or changes, so you can quickly decide if it’s safe or if you need to take action. This way, you’re always one step ahead in protecting your organization.
- How do you start with asset inventory management?
-
Getting started with asset inventory management is like planning a big, detailed journey. First, you decide on all the types of things you need to keep track of (like computers, software, etc.).
Then, you choose the best tools that can help you automatically keep an eye on everything and update your list in real-time. Finally, you need to keep watching everything closely to make sure it all stays safe and up-to-date.