Introduction
As organizations expand their digital infrastructure, keeping track of every cyber asset has become a growing challenge. Security teams struggle to maintain visibility across on-premises, cloud, and hybrid environments, leading to security gaps and increased cyber risks. This is where Cyber Asset Attack Surface Management (CAASM) comes in.
CAASM helps organizations comprehensively view all cyber assets, identify vulnerabilities, and strengthen their security posture. In this guide, we’ll explain what CAASM is, how it works, why it’s important, and how it compares to other security solutions.
What is CAASM?
Cyber Asset Attack Surface Management (CAASM) is a cybersecurity practice that provides organizations with complete visibility and control over their cyber assets. It helps security and IT teams identify, assess, and manage assets across all environments, including on-premises, cloud, and hybrid infrastructures.
Unlike traditional asset management tools, which often provide static lists of assets, CAASM enables real-time monitoring, risk analysis, and automation to reduce security gaps and improve overall resilience.
Key Functions of CAASM:
- Asset Discovery & Inventory: Identifies all internal and external cyber assets.
- Risk & Vulnerability Assessment: Prioritizes security gaps based on severity.
- Automation & Policy Enforcement: Streamlines remediation efforts.
- Continuous Monitoring & Threat Intelligence: Ensures up-to-date risk insights.
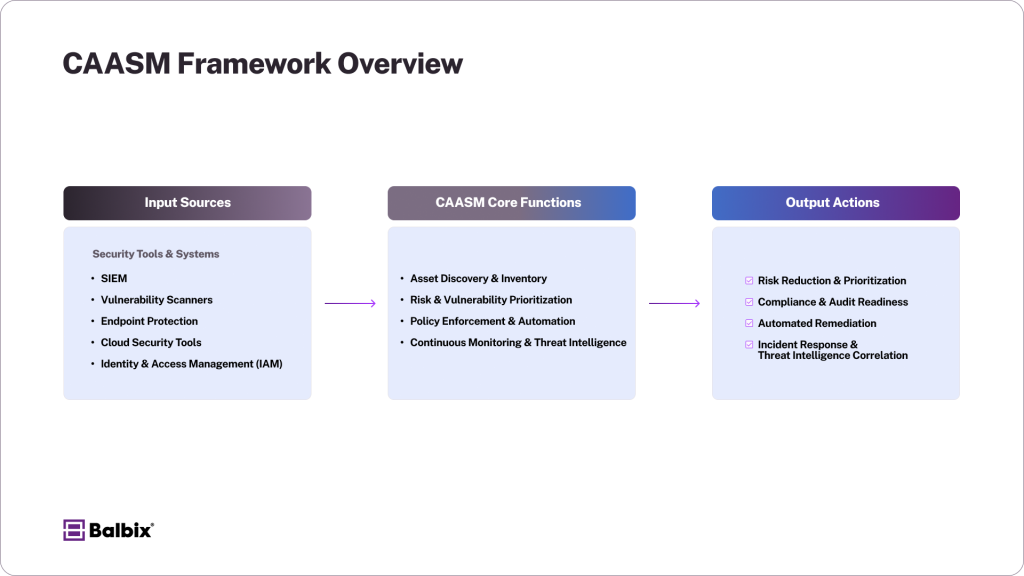
How Does CAASM Work?
CAASM platforms integrate with existing security tools to collect, analyze, and manage data related to cyber assets. Here’s how it works:
1. Comprehensive Asset Discovery
CAASM tools automatically discover, deduplicate, and inventory all cyber assets, including endpoints, servers, mobile devices, cloud resources, IoT devices, and applications. Unlike traditional asset management tools that rely on manual input, CAASM continuously updates asset inventories in real-time. This ensures that newly added or decommissioned assets are accurately reflected, reducing the risk of shadow IT and asset sprawl.
2. Risk & Vulnerability Prioritization
Once assets are identified, CAASM evaluates them for security gaps, such as outdated software, misconfigurations, or unauthorized access points. Each vulnerability is assessed based on its potential impact, exploitability, and relevance to the organization’s security posture.
By integrating with vulnerability management tools, CAASM helps prioritize risks based on severity, allowing security teams to focus on high-impact threats first. Additionally, it correlates asset risk data with external threat intelligence sources to identify emerging attack vectors before they can be exploited.
3. Automation & Remediation
Through automated workflows, CAASM helps security teams quickly patch vulnerabilities, enforce policies, and ensure compliance. It streamlines response actions by integrating security orchestration and automation tools (SOAR), ticketing systems, and endpoint protection platforms.
This ensures that remediation steps, such as software patching or access revocation, are executed efficiently with minimal manual intervention. By reducing remediation timelines, CAASM helps organizations mitigate risks before they escalate into full-blown security incidents.
4. Continuous Monitoring & Threat Intelligence
Cyber threats make continuous monitoring a crucial aspect of security. CAASM continuously tracks new assets, changes, and potential threats to provide real-time risk insights. It integrates asset inventory, patch management, security information and event management (SIEM) systems, and external threat intelligence feeds to maintain an accurate inventory and correlate asset behavior with potential security threats.
This enables security teams to detect anomalies, unauthorized changes, and suspicious activities across their infrastructure. Additionally, CAASM helps organizations maintain compliance by ensuring security configurations remain aligned with industry frameworks and best practices.
Why is CAASM Important?
With IT environments becoming increasingly complex, shadow IT risks, misconfigurations, and security blind spots pose significant threats. CAASM addresses these challenges by offering:
- Complete Cyber Asset Visibility: Reducing hidden security gaps by continuously tracking all internal and external assets.
- Improved Risk Management: Prioritizing and addressing vulnerabilities based on their threat level and business impact.
- Stronger Compliance & Governance: Aligning with regulatory frameworks such as NIST, SOC2, CIS, and GDPR through automated compliance tracking.
- Faster Incident Response: Enhancing detection and remediation efforts by providing real-time risk insights and automated response capabilities.
CAASM vs. Other Security Solutions
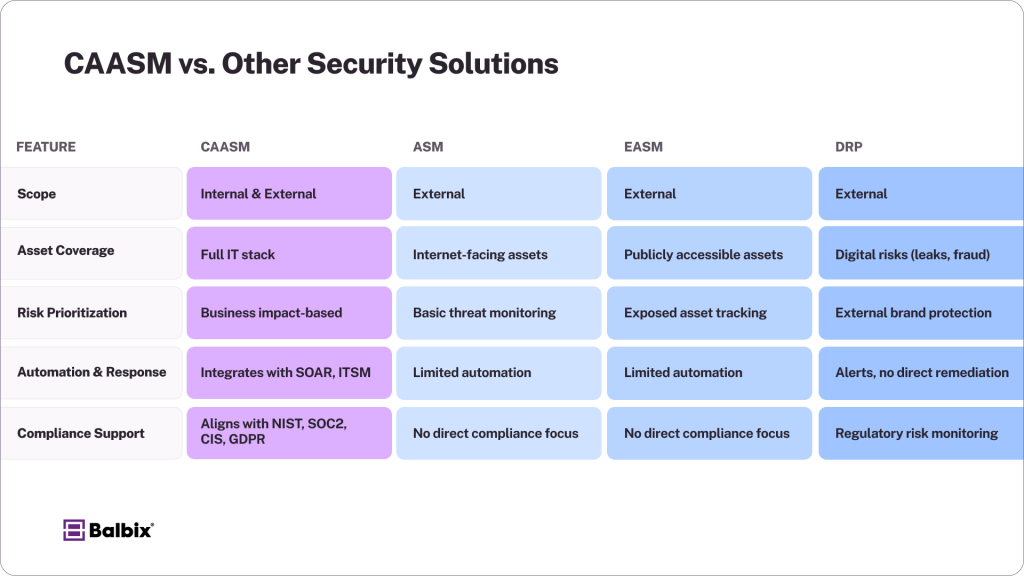
CAASM vs. Attack Surface Management (ASM)
- ASM focuses on external threats and internet-facing assets.
- CAASM provides visibility into internal and external cyber assets, ensuring a more holistic approach to security.
CAASM vs. External Attack Surface Management (EASM)
- EASM monitors publicly accessible assets, such as domains, IP addresses, and exposed cloud services.
- CAASM covers the entire IT infrastructure, including internal assets, devices, applications, and cloud resources, providing a more comprehensive security strategy.
CAASM vs. Digital Risk Protection (DRP)
- DRP focuses on external threats like data leaks, brand impersonation, and credential exposure.
- CAASM ensures comprehensive security monitoring by maintaining visibility across all environments, helping to mitigate both internal and external risks.
Key Use Cases of CAASM
1. Cyber Asset Inventory & Visibility
Organizations struggle to maintain an accurate and up-to-date inventory of their cyber assets, leading to blind spots that attackers can exploit. CAASM provides a centralized, real-time view of all assets across on-premises, cloud, and hybrid environments. By continuously discovering and categorizing assets, security teams can ensure that every device, application, and service is accounted for, reducing the risk of shadow IT and unauthorized access.
2. Vulnerability & Risk Prioritization
Not all vulnerabilities pose the same level of risk. CAASM platforms help security teams identify, assess, and prioritize vulnerabilities based on severity, exploitability, and business impact. This ensures that high-risk security gaps—such as exposed credentials, unpatched software, or misconfigured assets—are addressed before attackers can exploit them. With automated risk scoring and contextual analysis, CAASM allows organizations to focus on the most critical threats first.
3. Compliance & Regulatory Alignment
Meeting regulatory and compliance requirements is a challenge for many organizations. CAASM simplifies this process by providing continuous compliance monitoring and automated reporting.
Whether aligning with frameworks like NIST, SOC2, CIS, or GDPR, CAASM ensures that security policies are enforced consistently. Security teams can generate audit-ready reports and demonstrate compliance with minimal manual effort, reducing the risk of fines or reputational damage.
4. Incident Response & Threat Intelligence
A swift and effective incident response strategy requires complete visibility into an organization’s cyber assets. CAASM enhances incident detection, investigation, and response by correlating asset data with threat intelligence feeds.
When a security incident occurs, teams can quickly determine the scope of the attack, identify affected assets, and implement remediation measures. By integrating with SIEM and SOAR solutions, CAASM enables faster and more coordinated responses to cyber threats.
5. Third-Party & Supply Chain Risk Management
Organizations increasingly rely on third-party vendors, SaaS applications, and cloud providers to run their operations. However, these third parties introduce security risks that must be managed proactively.
CAASM helps assess vendor security posture, track integrations, and identify potential supply chain risks. Organizations can enforce security policies and mitigate risks associated with external dependencies by maintaining visibility into third-party assets and their security configurations.
Benefits of CAASM
1. Complete Asset Visibility
CAASM provides a single source of truth for all cyber assets, ensuring security teams have complete visibility across their entire IT environment. By integrating data from various security tools, CAASM helps eliminate blind spots and uncover shadow IT, reducing security risks associated with unknown or unmanaged assets.
2. Faster Risk Identification & Remediation
Traditional asset management approaches often leave security teams scrambling to assess and address vulnerabilities manually. CAASM streamlines this process by automating risk identification and prioritization. Security teams can quickly detect outdated software, misconfigurations, and other security gaps, allowing for faster remediation and reducing an organization’s exposure to cyber threats.
3. Automated Security Workflows
Many security incidents occur due to slow, manual response times. CAASM enables automated workflows to handle everyday security tasks, such as patching vulnerabilities, enforcing compliance policies, and updating asset inventories. This improves efficiency and ensures security protocols are consistently applied across the organization.
4. Stronger Cyber Resilience
A well-managed attack surface significantly reduces an organization’s overall cyber risk. CAASM helps organizations build cyber resilience by continuously monitoring assets, identifying emerging threats, and integrating with threat intelligence platforms. By proactively managing security risks, organizations can mitigate potential cyberattacks before they cause serious damage.
5. Improved Compliance & Audit Readiness
Regulatory compliance is a major concern for many organizations. CAASM helps streamline compliance efforts by maintaining a comprehensive, real-time inventory of cyber assets and their associated security statuses. By automating compliance tracking and reporting, organizations can ensure they remain aligned with industry standards such as NIST, SOC2, and CIS.
Conclusion
As cyber threats evolve, complete visibility into your attack surface is critical. CAASM helps security teams quickly identify, prioritize, and address risks, reducing exposure and strengthening resilience.
With Balbix, you can take control of your cyber assets. Streamline security operations, enhance compliance, and manage risks proactively—all with real-time insights that empower better decisions and faster responses.
Frequently Asked Questions
- What is Cyber Asset Attack Surface Management (CAASM)?
-
CAASM is a cybersecurity approach that provides organizations with complete visibility into their digital assets, helping them identify security gaps, reduce risks, and streamline vulnerability management.
- How does CAASM improve cybersecurity?
-
CAASM enhances cybersecurity by continuously monitoring assets, identifying vulnerabilities, and automating remediation workflows, ensuring organizations can proactively manage threats.
- What’s the difference between CAASM and Attack Surface Management (ASM)?
-
While ASM focuses on external risks, CAASM provides full asset visibility across internal and external IT environments, making it more comprehensive.
- Can CAASM help with compliance and regulatory requirements?
-
Yes, CAASM helps organizations maintain compliance with NIST, SOC2, CIS, and other regulatory standards by ensuring a complete and up-to-date asset inventory.
- How do I choose the right CAASM solution for my organization?
-
Look for a CAASM solution that offers real-time asset discovery, risk prioritization, automation, and seamless integration with your existing security tools.