What is the FAIR Model?
The FAIR Model (Factor Analysis of Information Risk) is a quantitative risk analysis framework that helps organizations assess and quantify cyber risks in monetary terms. The FAIR model estimates potential loss exposure by analyzing specific risk scenarios, enabling businesses to understand where they are most vulnerable to cyberattacks. Recognized as an international standard, FAIR helps organizations make informed decisions about risk management and mitigation strategies.
The FAIR Methodology
The FAIR methodology provides a structured way to assess and quantify cyber risk by analyzing the impact and likelihood of potential threats. Unlike deterministic models, FAIR uses a probabilistic approach, recognizing randomness in data for more accurate risk analysis. It focuses on critical assets and probable risk scenarios, allowing organizations to evaluate financial implications and prioritize cybersecurity efforts. This model supports informed decision-making by translating complex risks into clear financial terms.
How does the FAIR methodology work?
The FAIR methodology quantifies cybersecurity risk by breaking it down into individual factors using statistical analysis and probabilities. It assesses risk through carefully scoped scenarios by evaluating the probable frequency of loss events (Loss Event Frequency) and the potential impact of those losses (Loss Magnitude). By combining these components, FAIR provides a comprehensive and quantitative understanding of risk in monetary terms, enabling organizations to make informed, data-driven security decisions.
The FAIR methodology ties the frequency and magnitude of potential losses to specific assets within an organization. Identifying and valuing these assets is crucial for defining and measuring risk. An investment can be any device, data, or component with intrinsic value that could suffer a loss. FAIR considers various types of losses, including:
- Productivity: Reductions due to an inability to deliver critical products or services.
- Response: Resources spent responding to a risk or threat immediately after it occurs.
- Replacement: Costs of replacing compromised assets.
- Reputation: Missed opportunities or sales due to diminished brand or shareholder perception.
- Competitive Advantage: Losses from intellectual property or market share, weakening a competitive edge.
- Judgments and Fines: Legal costs or fines resulting from the threat event.
A “threat agent” or “threat community” is any event or situation that can cause these losses, such as a natural disaster or a malware attack.
The 2 Main FAIR Components
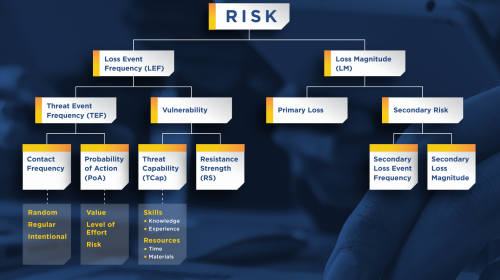
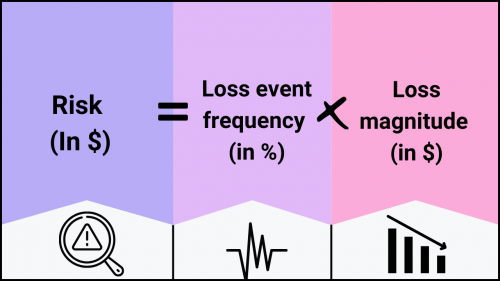
To quantify risk, FAIR divides it into two main components: Loss Event Frequency (LEF) and Loss Magnitude (LM).
Loss Event Frequency (LEF) measures how often a loss event is likely to occur, considering:
- Threat Event Frequency (TEF): How often a threat might occur.
- Vulnerabilities (Vul): The likelihood of a threat leading to a loss event.
- Additional factors include:
- Contact Frequency (CF): How often an asset encounters a threat.
- Probability of Action (PoA): The likelihood of a threat acting against an asset.
- Threat Capability (TCap): The strength and resources a threat has to compromise an asset.
- Resistance Strength (RS): The asset’s ability to resist a threat.
Loss Magnitude (LM) captures the impact of a threat, divided into:
- Primary Loss (PL): Direct loss to the primary stakeholder.
- Secondary Loss (SL): Losses resulting from the reactions of secondary stakeholders.
Ultimately, the FAIR model helps organizations minimize risk by identifying contributing factors. It offers two main strategies: reducing the frequency of loss events or mitigating the financial impact when they occur.
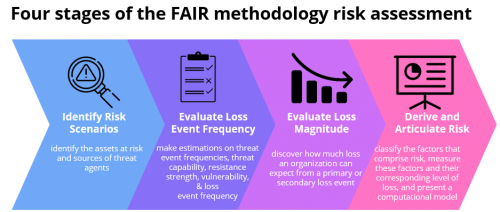
The Four Stages of the FAIR Methodology Risk Assessment
An organization looking to apply the FAIR methodology to perform a risk assessment can do so in four stages:
Stage 1: Identify Risk Scenarios
The first stage of the FAIR methodology involves identifying and defining the specific risk scenarios relevant to your organization. This process begins by pinpointing the assets that could be at risk, such as sensitive data, critical infrastructure, or intellectual property. These assets are then linked to potential threats, referred to as “threat agents” or “threat communities.” Threat agents could be anything from cybercriminals and nation-state actors to internal threats like disgruntled employees. Identifying these risk scenarios is crucial because it establishes the context for the entire risk analysis, ensuring that the subsequent stages are focused on the most relevant and impactful threats to the organization.
Stage 2: Evaluate Loss Event Frequency
In the second stage, the focus shifts to quantifying how often a loss event is likely to occur, known as the Loss Event Frequency (LEF). This is done by evaluating several factors:
- Threat Event Frequency (TEF): The number of times a threat agent is expected to attempt a harmful action.
- Threat Capability (TCap): The level of skill, resources, and motivation the threat agent possesses to execute an attack successfully.
- Resistance Strength (RS): The organization’s defenses (technical, procedural, etc.) ability to withstand the threat agent’s capabilities.
- Vulnerability (Vul): The probability that a threat event will successfully result in a loss event, considering the resistance strength of the target asset.
By gathering data and making informed estimations on these factors, organizations can calculate the Loss Event Frequency, which helps them understand the likelihood of different risk scenarios materializing.
Stage 3: Evaluate Loss Magnitude
The third stage focuses on determining the potential financial impact of a loss event, known as Loss Magnitude (LM). This involves calculating direct (primary) and indirect (secondary) losses that could result from a threat event.
- Primary Loss: Direct losses incurred by the organization, such as asset damage, immediate response costs, or loss of productivity.
- Secondary Loss: Indirect losses, including reputational damage, legal penalties, or loss of market share, caused by the reactions of external stakeholders like customers, regulators, or partners.
Understanding the potential magnitude of these losses allows organizations to gauge the overall impact that a threat event could have, both within and externally.
Stage 4: Derive and Articulate Risk
In the final stage, all the information gathered in the previous stages is synthesized into a comprehensive risk analysis. This involves:
- Classifying Factors: Grouping the identified risk factors (TEF, TCap, RS, Vul, LM) to build a detailed risk profile.
- Measuring Loss: Quantifying the expected level of loss associated with each risk scenario.
- Computational Modeling: Using simulation tools like the Monte Carlo simulation to analyze the probability distributions of various risk factors, allowing for a more nuanced understanding of potential outcomes.
This stage culminates in a detailed risk assessment that articulates the financial impact of different risk scenarios. By presenting this data clearly, organizations can make informed decisions about where to allocate resources, how to prioritize risk mitigation efforts, and how to communicate risks to stakeholders, such as executives or board members. This holistic approach ensures that the organization’s risk management strategy is both comprehensive and aligned with its overall business objectives.
Benefits of the FAIR Risk Model
FAIR provides a comprehensive framework for evaluating and quantifying cyber risks, offering numerous benefits for organizations looking to strengthen their cybersecurity posture and make informed business decisions. By focusing on financial quantification, FAIR allows organizations to assess the impact of individual threat events or aggregate risks across multiple scenarios, providing deeper insights into how these threats can affect key business units and stakeholders. This ability to translate complex risk scenarios into monetary terms is can be useful for organizations of all sizes for organizations aiming to prioritize cybersecurity investments and strategies.
- Financial Quantification of Cyber Risks
One of the most significant benefits of the FAIR risk model is its ability to quantify cyber risks in financial terms. Organizations can answer critical questions, such as the potential financial impact of a specific threat event and the frequency with which it might occur. This quantification enables businesses to understand the potential cost of cyber incidents, helping them to allocate resources more effectively and justify cybersecurity budgets to stakeholders. - Informed Decision-Making for Risk Mitigation
FAIR empowers organizations to make informed decisions about risk mitigation by evaluating the effectiveness of different control solutions. Businesses can choose the most effective strategy for minimizing risk by comparing the potential risk reduction of various solutions. This approach ensures that investments in cybersecurity provide the best return on investment (ROI), focusing on the areas where they will have the most significant impact. - Enhanced Prioritization of Cybersecurity Efforts
FAIR is more useful for estimating the expected loss curves for a specific set of assets/scenarios that have been predetermined, but less useful for understanding which (out of all assets) are most at risk. By understanding which assets are most vulnerable to specific threats, businesses can focus their resources on protecting the most critical parts of their infrastructure. This targeted approach improves overall security and ensures that the most significant risks are addressed first. - Facilitating Business Decisions on Cybersecurity Investments
Beyond risk mitigation, the FAIR model assists organizations in making broader business decisions related to cybersecurity. For example, by providing a clear picture of potential financial losses, FAIR helps companies determine the appropriate level of investment in cybersecurity insurance across the scenarios analyzed. It also helps organizations choose between different risk reduction solutions, ensuring they select the option that offers the best protection for their risk profile. - Supporting Regulatory Compliance
In today’s regulatory environment, demonstrating a thorough understanding of cyber risks and the measures in place to mitigate them is crucial for compliance. The FAIR model facilitates regulatory compliance by providing a structured method for assessing and documenting risks. This documentation can be used to show regulators that the organization has taken appropriate steps to manage and reduce cyber risks, thereby meeting compliance requirements.
Drawbacks to Using the FAIR Risk Model
Quantifying cyber risk based on the FAIR four-stage method has several drawbacks.
Stage 1: Identify Risk Scenarios typically involves a group of people assessing a set of considered threats and their estimated loss and filling up a questionnaire in a FAIR tool based on their qualitative knowledge. The drawbacks in this stage are:
- Time-consuming and costly
- Requires a deep understanding of the FAIR risk ontology
- Entails manual data collection
- Requires input from scenario-related experts or consultants
- Uses subjective information that can lead to inaccuracies
Due to the manual effort needed, it requires focus on the few scenarios/areas of the environment that are estimated to be most important/high risk. So, the scope of risk scenarios that can be covered is limited in practice.
Stage 2: Evaluate Loss Event Frequency and Stage 3: Evaluate Loss Magnitude, which involves collecting information based on identified risk scenarios and estimating Loss Event Frequency and Loss Magnitude. The drawback to these stages is:
Stage 4: Derive and Articulate Risk focuses on analyzing, articulating, and deriving the probable financial impact of risk using a simulation model. The drawbacks in this stage are:
- This is perhaps FAIR’s greatest practical drawback: It does not prioritize vulnerabilities or provide actionable steps an organization can take to improve its cybersecurity posture and reduce breach risk.
- It does not provide remediation guidance that security teams can use to quickly and effectively manage threats within their entire network because security controls are pinpointed for specific threats.
- It makes the remediation and mitigation of cyber threats in a continuous and repeatable manner challenging to operationalize.
FAIR’s many drawbacks stem from creating this methodology when detailed cybersecurity data was not readily available. This is no longer true.
Paul Kelly, former head of Cyber Risk Management at HSBC, explains this well: “The issue here is that in the digital age, IT environments are dynamic. New threats and vulnerabilities are identified frequently. Config updates, patches, upgrades, new code releases, etc, are a continuous feature of the modern technology landscape. If you want to understand your current risk exposure, you need a calculation engine to keep up with the daily changes. You need to be able to take swift, targeted, and efficient action to keep your risk exposure at an acceptable level.”
Using Balbix for Cyber Risk Quantification
While FAIR requires extensive human intervention to collect and analyze data to calculate risk, solutions like Balbix Cyber Risk Quantification (CRQ) incorporate business context into the risk model and automate risk discovery and quantification.
Balbix automatically ingests data from an organization’s existing IT and security applications into a unified cyber risk model in dollars. This solution calculates breach likelihood and impact on an asset-based level and provides risk-mitigation options so organizations can improve their security posture. As remediation actions are taken, Balbix automatically updates the risk calculations. The result is a more continuous, real-time, and accurate cyber risk calculation. Balbix also automates board and executive-level risk reporting with comprehensive business-aligned dashboards.
Frequently Asked Questions
- What does FAIR stand for in risk management?
-
FAIR stands for Factor Analysis of Information Risk. It’s a methodology used in risk management to quantify and analyze information security risks in financial terms. By breaking down risks into individual components, FAIR helps organizations understand the potential impact of cyber threats and make more informed decisions.
- How do you calculate FAIR risk?
-
FAIR risk is calculated by analyzing two main components: Loss Event Frequency (how often a risk event might happen) and Loss Magnitude (the potential financial impact if it does). These factors estimate the overall financial risk, helping organizations prioritize their cybersecurity efforts based on potential losses.
- What is the best risk calculation methodology?
-
The best risk calculation methodology depends on the organization’s needs. FAIR is widely regarded for its ability to quantify risks in financial terms, making it easier to prioritize and justify cybersecurity investments. Other methods, like qualitative assessments, may be more straightforward but offer less precision in understanding financial impacts.