
Rhonda Gass
Stanley Black & Decker
Automated remediation and AI assistant, BIX
With automated workflows, integrations, and Balbix’s GenAI assistant, BIX reduces unnecessary communication and streamlines workloads.
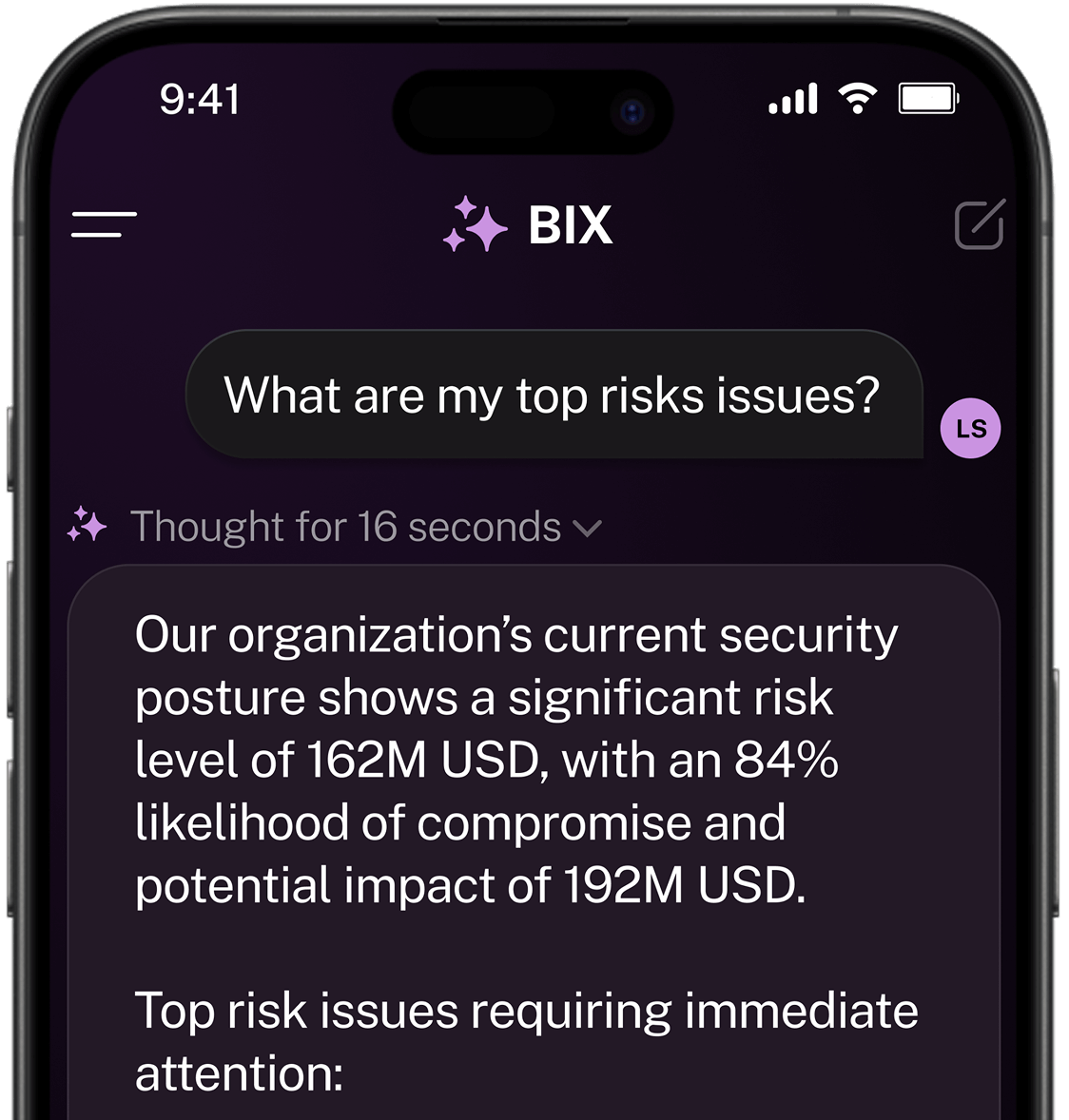
Benchmark and assess cyber risk
Assess and compare cyber risk metrics across business units, locations, and asset groups. Establish benchmarks for overall risk posture and prioritize resources to strengthen security and minimize organizational exposure.
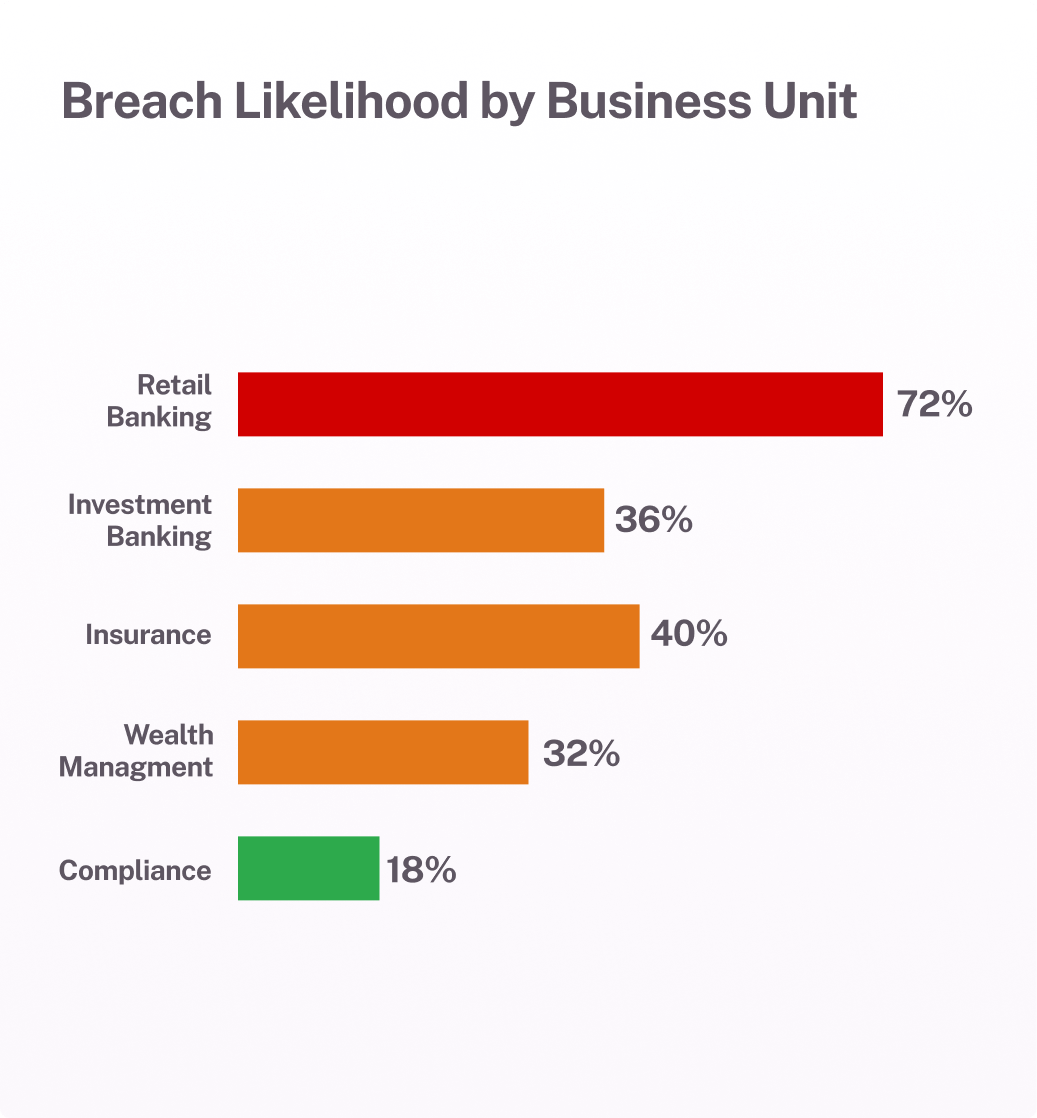
Actionable next best steps
Lower risk with actionable next best steps. Understand specific risk issues to resolve to bring the cyber risk down to acceptable levels.
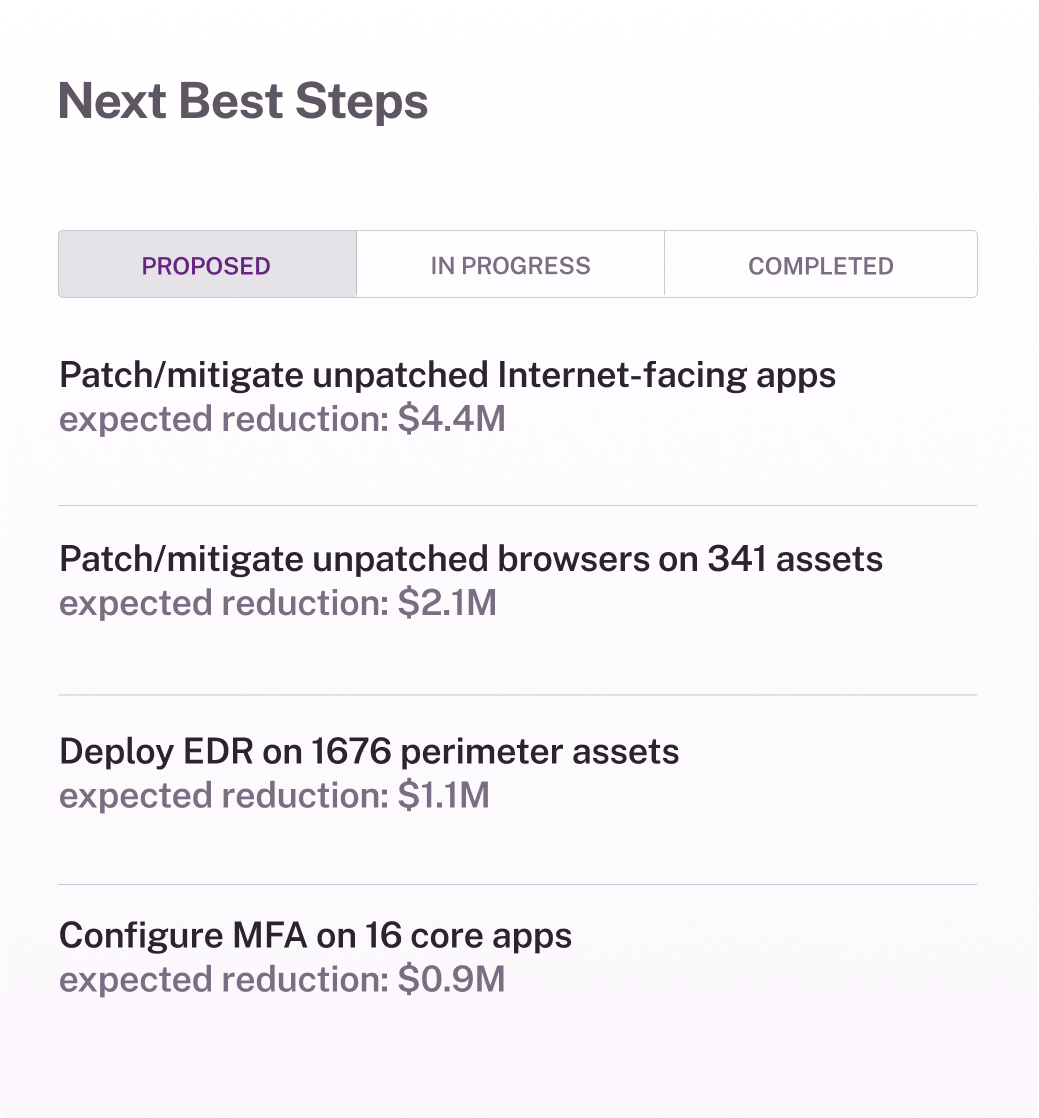
Quantify cyber risk in dollars
Bridge the gap between cybersecurity and business priorities with CRQ (Cyber Risk Quantification). Equip senior leadership, the board, and stakeholders with clear, financial insights into your cyber risk landscape. Use the language of money to demonstrate the ROI of security investments, quantify risk gaps, and present actionable strategies for informed decision-making.
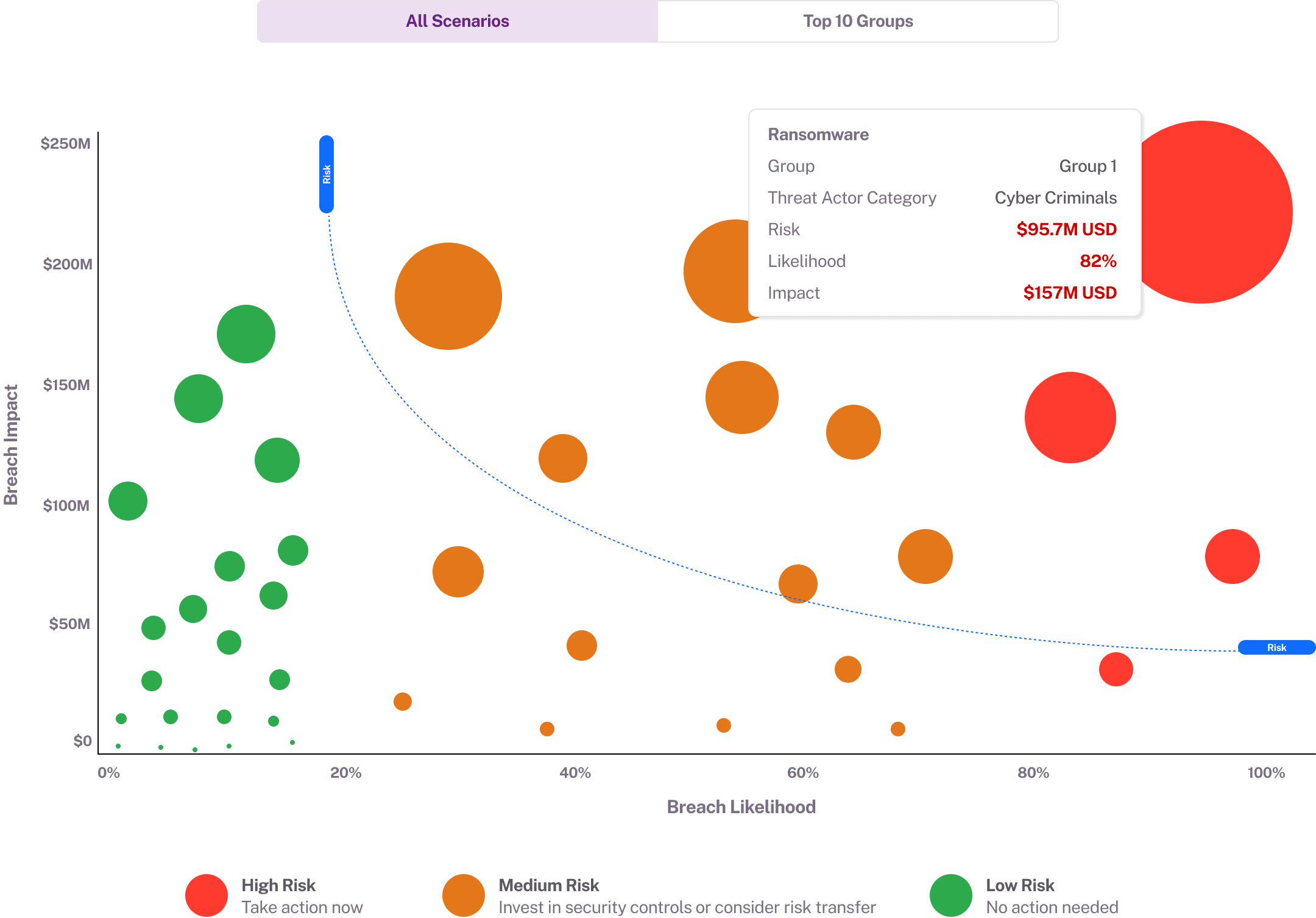
Financial risk insights
Balbix translates technical vulnerabilities into financial terms, quantifying the potential business impact of specific risks. Balbix enables CISOs to prioritize mitigation efforts based on financial exposure and ROI.
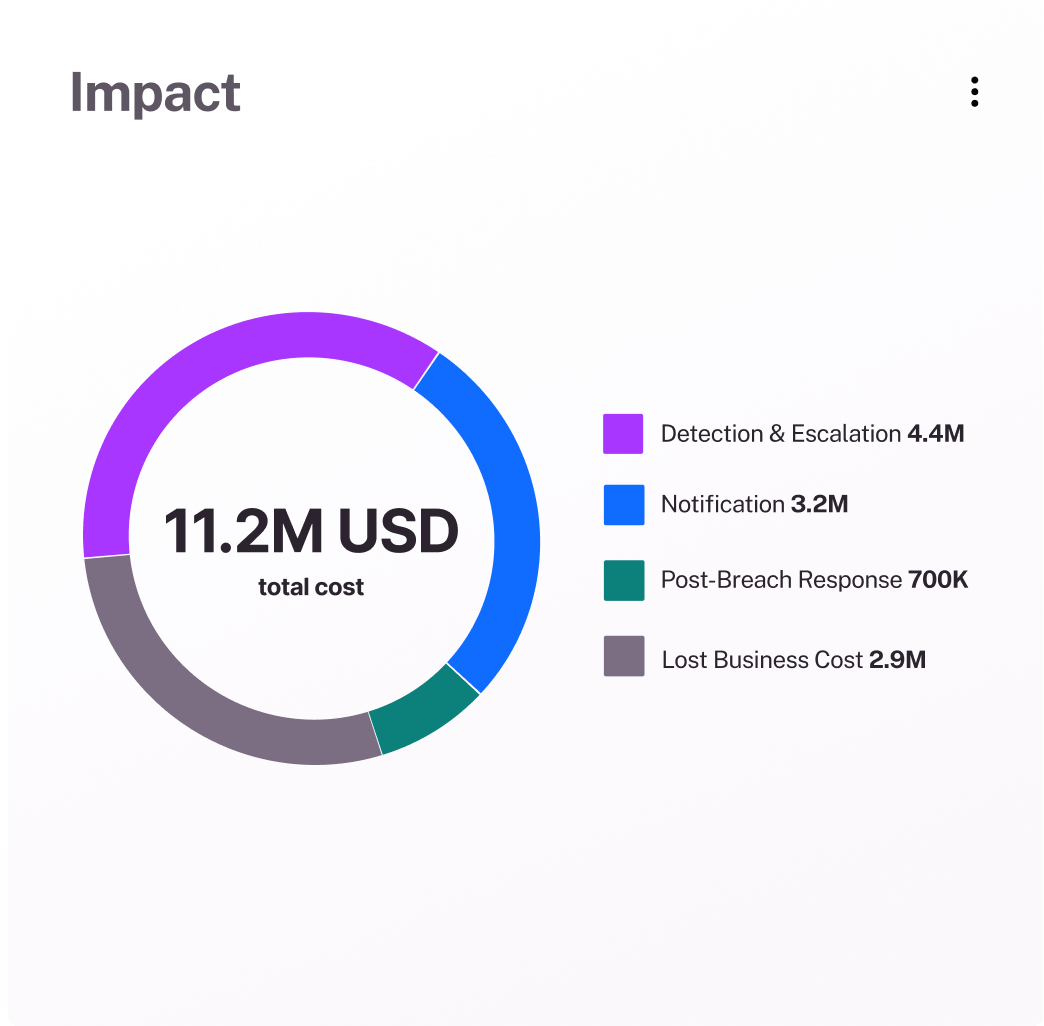
ROI of cybersecurity investments
Highlight the effectiveness of your cybersecurity program by showing measurable cyber risk reduction in monetary terms. Report on the impact of security investments with clear, quantifiable metrics.
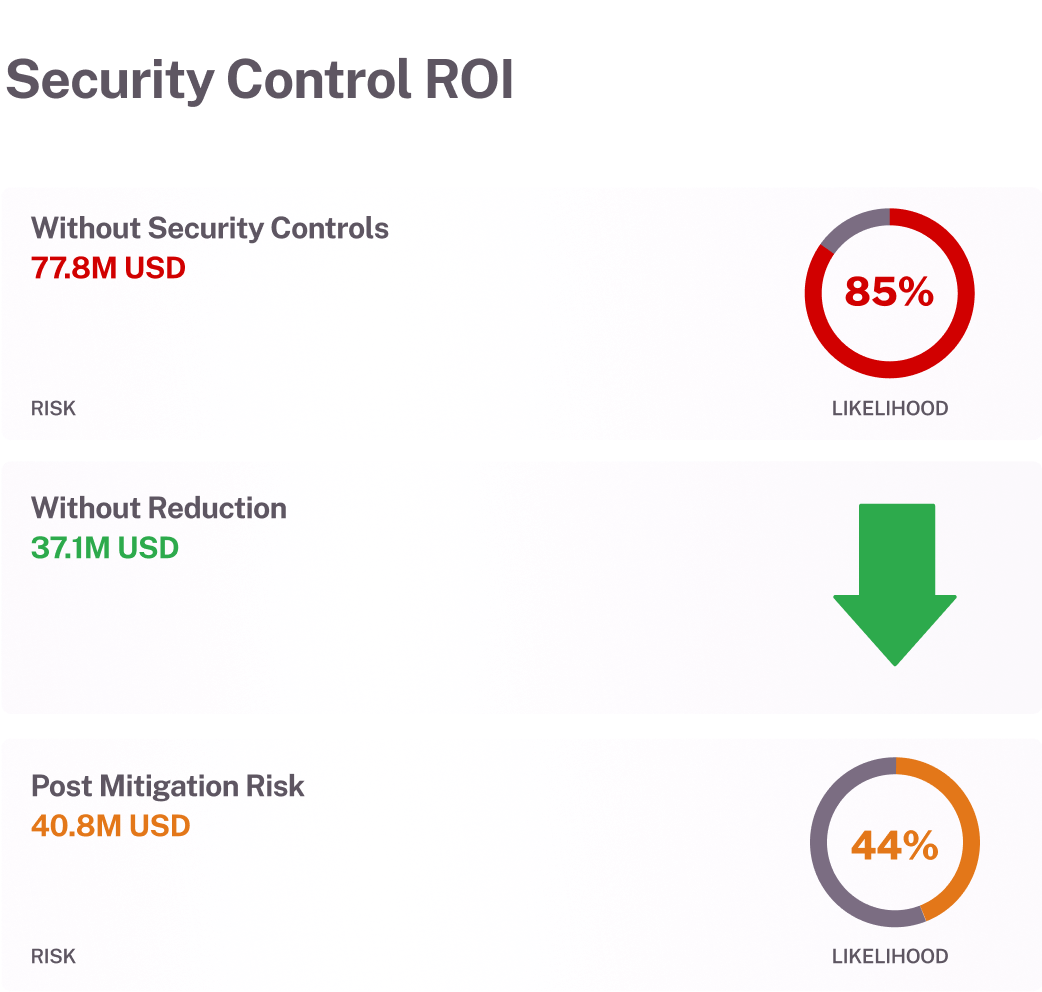
Rapid materiality assessments
Achieve unified visibility into all assets and applications. Quantify cyber risks in monetary terms to determine material impact quickly and accurately, ensuring compliance with SEC cyber disclosure requirements.
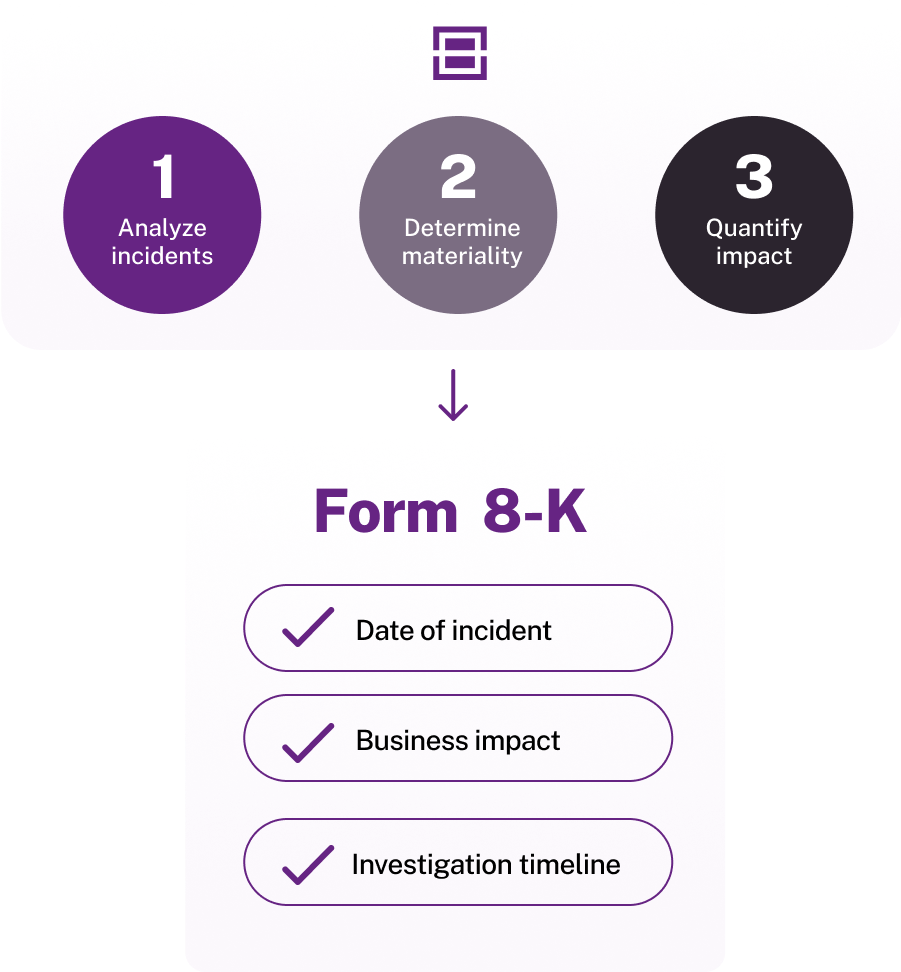
Enhance compliance efficiency
Simplify SEC cyber rule compliance by eliminating data retrieval bottlenecks. Instantly access the insights you need, reducing manual effort and ensuring teams can focus on risk mitigation and regulatory readiness.
“Balbix is an industry-leading platform that consolidates cyber risks into a single reportable model. This technology enables us to scorecard our risk remediation performance and gain continuous visibility into open security issues.”

Rhonda Gass
Stanley Black & Decker
Get a demo and discover how the world’s leading CISOs use Balbix as the brain of their cybersecurity programs.