Less than 10% of vulnerabilities will ever be exploited in the wild. That’s the good news.
The bad news? Of those that are weaponized, it will only take 7-14 days after CVE disclosure for an exploit to be made available, but it will take your organization (yes, yours) 85-100 days to patch that vulnerability. Some vulnerabilities are successfully exploited within hours.
Even more troubling is that only half of exploited vulnerabilities have a CVSS score of 9 or 10 (critical).
Something is seriously wrong with vulnerability management.
The Problem with Vulnerability Management Programs
Most organizations are still prioritizing based on severity, as indicated by CVSS Base Scores published in the NIST NVD. Using such a simple scheme results in much effort wasted on high severity vulnerabilities that will never be exploited, while simultaneously ignoring lower severity vulnerabilities that already are being exploited.
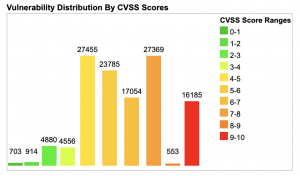
Take for example an organization focused on closing all critical vulnerabilities as quickly as possible. Of the 16,185 critical vulnerabilities, only around 2,000 of them have been weaponized with publicly available exploit code. Even assuming this organization can patch those vulnerabilities within days, they are still ignoring half of the attacker’s arsenal by leaving lower severity vulnerabilities unpatched (not to mention the 8 other types of security vulnerabilities).
The organization’s focus on the 14,000 critical vulnerabilities that haven’t been exploited means less time and resources to spend on the other exploited vulnerabilities. This is a major contributing factor in why it takes so long to patch these vulnerabilities. Other factors include inability or lack of willingness to patch by risk owners, lack of availability of patches from vendors, and overall poor patching processes.
Switch to Risk-Based Vulnerability Management
Modern, risk-based approaches to vulnerability management (such as Balbix) have been designed to eliminate these inefficiencies and get security teams focused on mitigating risk, as opposed to mitigation of anything deemed “severe.” These approaches look at severity as just one component of a much more comprehensive risk picture.
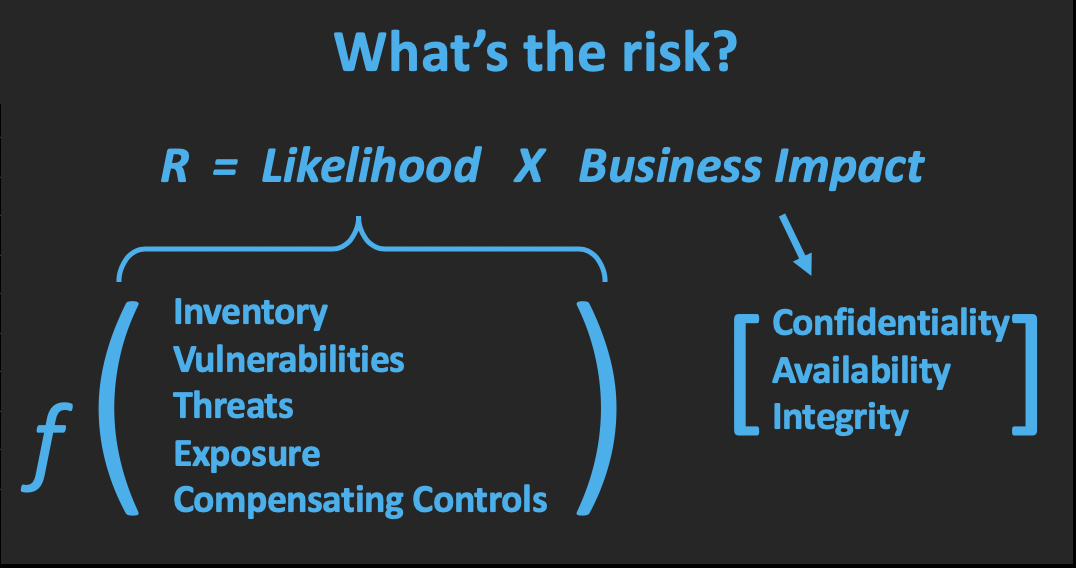
Risk is a function of both Likelihood of Breach and Business Impact.
Business Impact is the same whether you use a traditional approach to vulnerability management or a risk-based approach. After all, a mission critical asset means big losses if breached regardless of how you try to protect it.
Likelihood of Breach, however, is where these two approaches really diverge. In traditional vulnerability management, prioritization mostly relies on base CVSS score severity. Risk-based vulnerability management takes into account several risk-driving factors, including:
- Inventory – you can’t improve what you can’t measure, so you need to have an accurate, real-time view of your entire asset inventory.
- Vulnerabilities – this is where CVSS scores come into play. But it’s important to remember that vulnerabilities are not just CVEs. You could have a weak password, an easy to phish user, some misconfiguration, and so on, in addition to unpatched software.
- Threats – this is where active threats come into play. Identifying that 5.5% of vulnerabilities that are actually being exploited in the wild as opposed to the 94.5% that are purely theoretical.
- Exposure – 37% of enterprise software is unused. If there is a vulnerability targeting a piece of software, but that software is not used, is there much risk? If a tree falls in the woods, does it make a noise?
- Compensating Controls – you’ve probably spent a ton of money (and time) on building a best-in-class security stack. For a given CVE, there’s some likelihood that one or more of the controls in that stack can mitigate either the severity of the vulnerability, or the ability for it to be exploited
With these factors in mind, you can shift your organization to focus on those vulnerabilities that are most likely to impact your organization, resulting in massive breach risk reduction with no incremental resource allocation towards your vulnerability management program. This will dramatically improve your ability to shrink your mean-time-to-patch, eliminating the advantage that attackers have before vulnerabilities are patched.