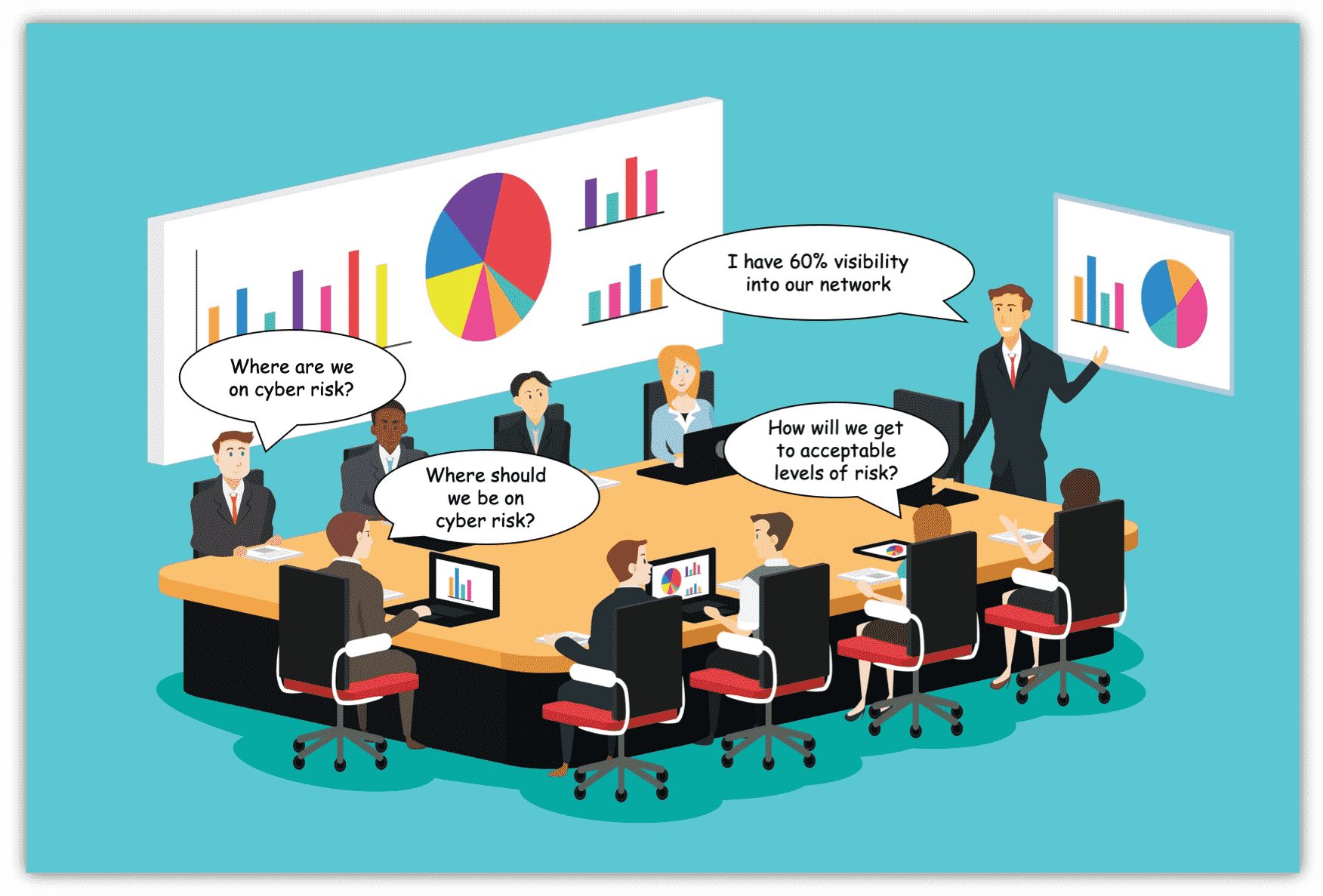
Visual imagery is an effective way to understand and communicate both abstract and concrete concepts. For CISOs and enterprise security teams, the ability to visualize your security posture and then use that imagery effectively while communicating your security posture to the board and other executives is of immense importance.
Your security posture is the overall security status of all your software and hardware assets, networks, services, and information. It also includes the controls and measure you have in place to protect your enterprise from cyber-attacks, your ability to manage your defenses, and your ability to react to and recover from security events.
A conceptual diagram representing your security posture would look something like this:
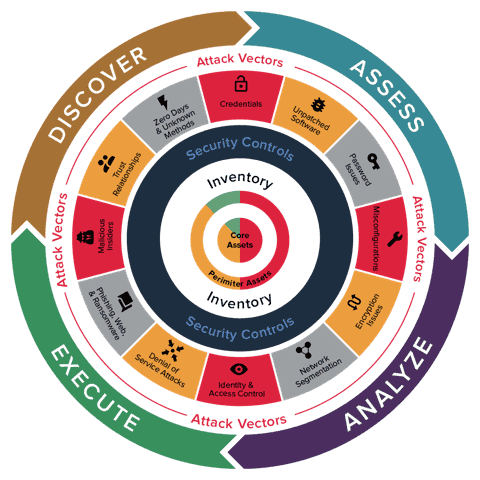
Let’s look at this diagram, starting from the center and going outwards to discuss the concentric circles.
At the very center of your security posture is an inventory of all your assets, including core and perimeter assets, categorized into on-prem, cloud, mobile, and 3rd party assets; managed and unmanaged assets; applications and infrastructure, catalogued based on geographic location.
Surrounding this core is an enumeration of your existing security controls, deployed to manage your defenses. Inherent in this enumeration is also an understanding of how effective these controls are in reducing your cyber risk.
Outside of that circle are the various risk items and attack vectors. Attack vectors are the methods that adversaries use to breach or infiltrate your network. Attack vectors take many different forms, ranging from malware and ransomware, to man-in-the-middle attacks, compromised credentials, and phishing. Some attack vectors target weaknesses in your security and overall infrastructure, others target weaknesses in the humans that have access to your network.
This combination of your inventory, surrounded by the security controls, defending against the numerous attack vectors makes up your attack surface. Your attack surface is represented by all of the points on your network where an adversary can attempt to gain entry to your information systems. Basically, any technique that a human can use to gain unauthorized access to your company’s data via any asset.
Your ability to monitor your assets in risk areas such as unpatched software, password issues, misconfigurations, encryption issues, phishing, web and ransomware, denial of service attacks and many others is the mainstay of your security posture.
The stronger and more resilient your security posture, the lower your cyber risk is and the greater your cyber-resilience is. Therefore, understanding the full scope of your security posture and correctly prioritizing areas of relevant risk is essential to protecting your organization against breaches.
This is where the outer most circle denoting your actions comes in. You need to continuously and cyclically:
- Discover and inventory assets in real time to know what needs to be protected
- Assess and understand the threat landscape and effectiveness of your security controls
- Analyze and develop risk insights and prioritize vulnerabilities
- Execute on assigning owners, setting goals, and showing outcomes
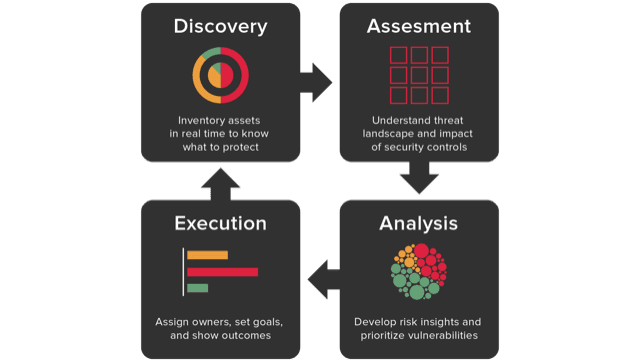
Balbix helps enterprises get visibility into their security posture
Balbix customers are able to:
- Achieve cybersecurity posture visibility by identifying all that needs to be protected and prioritizing areas of greatest risk.
- Transform cybersecurity posture by enhancing current security measures and investing in new areas
- Optimize cybersecurity posture continuously as conditions change
- Communicate breach risk and cybersecurity posture accurately to the board of directors
Learn more about getting visibility into your security posture and the various elements of security posture transformation.