Your vulnerability management program is the cornerstone of your cybersecurity initiative because you know that security vulnerabilities, if left unidentified and unaddressed, can bring your business down. But as your enterprise advances with new innovation in technology and growing employee numbers, your vulnerability management needs to evolve as well to continue to protect your enterprise against diverse threats.
To ensure that your vulnerability management initiative is not lagging behind, it is imperative to evaluate it from time-to-time. Are you stumbling on these 6 common barriers to successful vulnerability management?
#1: Not monitoring continuously and in real time
You have a huge number of assets including traditional IT and dynamic modern assets across all computing environments and each asset can be breached in a variety of different ways. The problem is that most vulnerability scanners do not work continuously. If you are not monitoring and analyzing your attack surface continuously and in real-time, you are setting yourself up for blind spots and delayed reaction time.
ASK YOURSELF: “Are new devices discovered with-in minutes of plugging into our environment and monitored across a broad range of attack vectors?”
Overcome it
Continuous, real-time monitoring and analysis of your entire attack surface gives you the ability to quickly identify potential breach risk and proactively fix security vulnerabilities. Consider investing in a risk-based vulnerability management system that offers continuous, real-time monitoring, instead of limited network scanning capabilities.
#2: Thinking vulnerabilities = CVEs
Vulnerability management scanners were designed to look for unpatched software flaws or CVEs (publicly known infosec vulnerabilities and exposures in publicly released software packages). However, if you consider the dictionary definition of a vulnerability, it is anything that exposes you and puts you at risk. So, bad password hygiene – using weak or default passwords, reusing passwords, and not storing passwords correctly – is also a vulnerability. And so are misconfigurations, encryption issues, and risky online behavior of employees.
Is your vulnerability management tool looking for vulnerabilities or flaws across other attack vectors also?
ASK YOURSELF: “Do we know our risk from weak or shared passwords, malware, phishing, encryption issues, online behavior of our admins and more?”
Overcome it
Vulnerabilities are not just CVEs. Any breach methods that put your enterprise at risk are dangerous. Invest in a risk-based vulnerability management system that goes beyond just monitoring unpatched software and covers a broad range of other attack vectors and vulnerabilities as well.
#3: Not inventorying all your assets
The traditional “scan-the-network” approach was aimed at enterprises with mostly static, on-premises systems like network infrastructures, servers etc. This does not work for the modern, multi-dimensional attack surface that hosts different types of assets including traditional IT (network infrastructure, servers, desktops) and dynamic modern assets (cloud instances, web apps, mobile, BYO, operational technology (OT), and IoT devices)
ASK YOURSELF: “Can we see all types of assets and devices – including unmanaged BYOD, IoT etc – that are on our network at any time?”
Overcome it
Broad asset coverage is a core capability that is required to discover all potential vulnerabilities. If your vulnerability management system only “sees” a few types of assets, your coverage is insufficient. Consider a risk-based vulnerability management system that identifies all types of assets, including BYOD, and empowers you to manage risk across the entire attack surface.
#4:Not having a searchable inventory of your IT assets
Having an automated, real-time, and accurate inventory of all your assets is a first – and critical – step, but if you are not able to search it and easily find what you need, that inventory is practically useless. You need to be able to craft complex queries like “iOS devices in Mountain View susceptible to Spectre” or “unpatched DNS servers in Texas” and get the answers quickly. Does your vulnerability management support that?
ASK YOURSELF: “If asked, how quickly and easily can we produce a list of all our assets susceptible to Wannacry? Can we even do it?”
Overcome it
Invest in a vulnerability management solution that offers the ability to perform natural language search and easily find answers to questions like “how many IoT devices do I have” or “where will the attack start” or “what is my risk from Poodle”. Being able to quickly find the needle(s) in the haystack is a huge advantage.
#5: Not prioritizing based on risk
The decision about what to fix and when to fix it has to be based on more than just a roll of the dice or generic vulnerability severity ratings. Risk-based prioritization must reflect numerous factors such as vulnerabilities across 100+ attack vectors, business value of the asset, active threats, exposure due to usage, and existing compensating controls. If your vulnerability management system not taking account all of these factors, the “prioritization” it may offer is of little to no value.
ASK YOURSELF: “Is my vulnerability management system really prioritizing vulnerabilities for me or is it just pseudo or incomplete prioritization?”
Overcome it
Moving from a vulnerability-focused mindset to a risk-based prioritization approach requires a vulnerability management platform that understands and learns your business context, considers the value of each asset to your business and takes into account vulnerabilities, active threats, exposure due to software usage and any mitigating controls already implemented in your enterprise to calculated risk. This risk-based prioritization helps you first focus on actions that are critical and make smarter decisions to reduce your risk, both strategically and tactically.
#6: Not having the right tools
With the number of cybersecurity threats growing every day and increased digitization of assets/processes that could be vulnerable to those threats, it is mathematically impossible for humans to monitor for threats, analyze the attack surface, and determine the actions to take and in what order to reduce breach risk. You need artificial intelligence (AI) for that. Legacy approaches and tools designed to protect traditional IT assets such as servers and network infrastructure aren’t robust enough to defend the modern attack surface and digital landscape.
ASK YOURSELF: “Does my vulnerability management system make it easy for me to see where my security gaps are? Does it prescribe the necessary tactical and strategic mitigations to address them and minimize risk?”
Overcome it
An AI-powered platform that continuously monitors all assets and proactively predict what vulnerabilities are most likely to be exploited is necessary just to keep up with the constantly evolving attack methods employed by cyber criminals, as well as the ongoing digital transformation of enterprises.
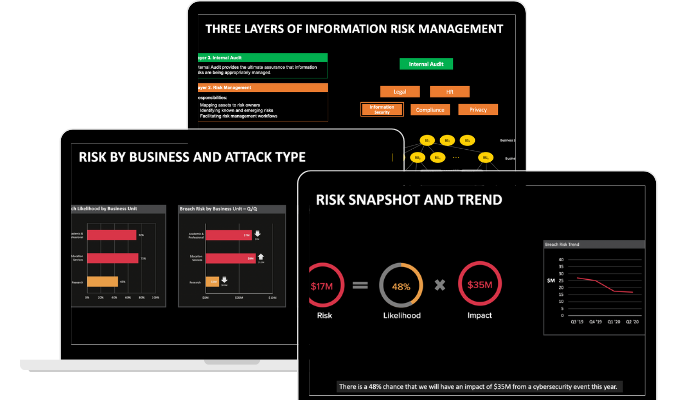
Risk-Based Vulnerability Management with Balbix
Balbix uses deep learning and advanced AI algorithms to enable you to:
- Understand your attack surface
Balbix continuously observes your extended enterprise network inside-out and outside-in, to discover the attack surface and analyze the hundreds of millions (or more) of data points that impact your risk. It monitors all your enterprise assets across 100+ attack vectors (such as such as phishing, credential exposure, weak/shared passwords, and malicious behavior and not just unpatched software vulnerabilities) continuously and in real-time.
- Get an accurate read on your risk
Balbix calculates your enterprise’s real-time risk, taking into account open vulnerabilities, business criticality, applicable threats and the impact of compensating controls. Analysis of all possible breach scenarios – the various combinations of attack starting points, target systems and propagation paths – and precise determination of the riskiest scenarios is key. This real-time risk model is surfaced to relevant stakeholders in the form of highly visual drill-down risk heatmaps and Google-like natural-language search. You can ask questions like “where will attacks start” or “what is the risk to customer data”, get a relevant, highly visual answer within milliseconds, and then drill-down into the details.
- Obtain prioritized action items with prescriptive fixes
Balbix generates a prioritized list of actions that will affirmably reduce risk. Security posture issues with the greatest risk are addressed first before working down the list of smaller contributors. For each issue, responsible owners for the corresponding assets are identified and then prioritized tickets containing all relevant context are generated and assigned to these owners. Progress is closely tracked and fed back to relevant stakeholders.