What’s the rockstar CISO’s favorite song?
Smells like Team Spirit!

Cheesy jokes aside, if you are or wish to be a rockstar CISO you know that you can’t do it alone. You need a team that is completely aligned to your organization’s overarching security goals and works like a well-oiled machine to beat the bad guys. And of course, I know that one can’t really “hacker-proof” anything, but one can aspire, isn’t it?
In most organizations, security teams are usually siloed around buckets of technology, an artifact of the days of traditional IT workflows. But as the threat landscape has evolved and cybersecurity has become a topic for board-level conversations, the traditional make-up of the security team has to be rethought from scratch and organized around skill-levels to be fully resilient. After all, the adversary doesn’t care about your silos and is constantly looking to find a way to enter your networks, day-in and day-out.
So, what does this dream-team look like? What are some essential personas that must be a part of this team?
The Breaker
This is the persona that thinks like a hacker. Red teams, penetration testers, ethical hackers are all folks that take an offensive approach towards cybersecurity by emulating the behavior of an adversary. They are adept at all forms of digital attack, as well as social engineering and other methods to find ways to break into your systems and test the limits of your security posture. They are responsible for securing the organization’s digital assets through active hunting and identification of threats and vulnerabilities that are not detected by traditional vulnerability scanning. They possess a deep understanding of both information security and computer science and are comfortable with concepts such as networking, applications and operating system functionalities, application manipulation, exploit development, and stealthy operations.
Here’s a view of the enterprise a Breaker will typically look at:
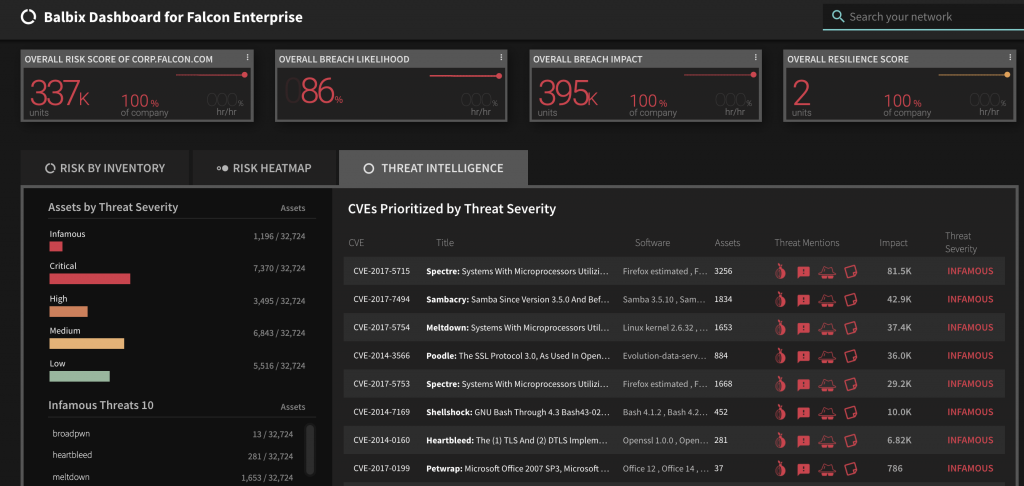
The Defender
This persona makes up the majority of your cybersecurity team. Folks in vulnerability and patch management, threat intelligence, security operations, network defense, security architecture roles are all defenders. Blue teams can also be classified as defenders. They continually monitor and endeavor to harden security around and within the company’s networks and data systems. The defenders provide technical expertise across the entire life cycle of vulnerability management including asset management, vulnerability scanning, threat intelligence, mitigating controls analysis, and reporting. They are also the ones to review vulnerabilities based upon footprint, threat intelligence and existing controls, in order to determine priority and risk ranking across the enterprise. In addition, they track and work with all support teams for patching and remediation reports on status of patching deployments to the CISO.
A defender might create a custom Balbix dashboard that looks like this:
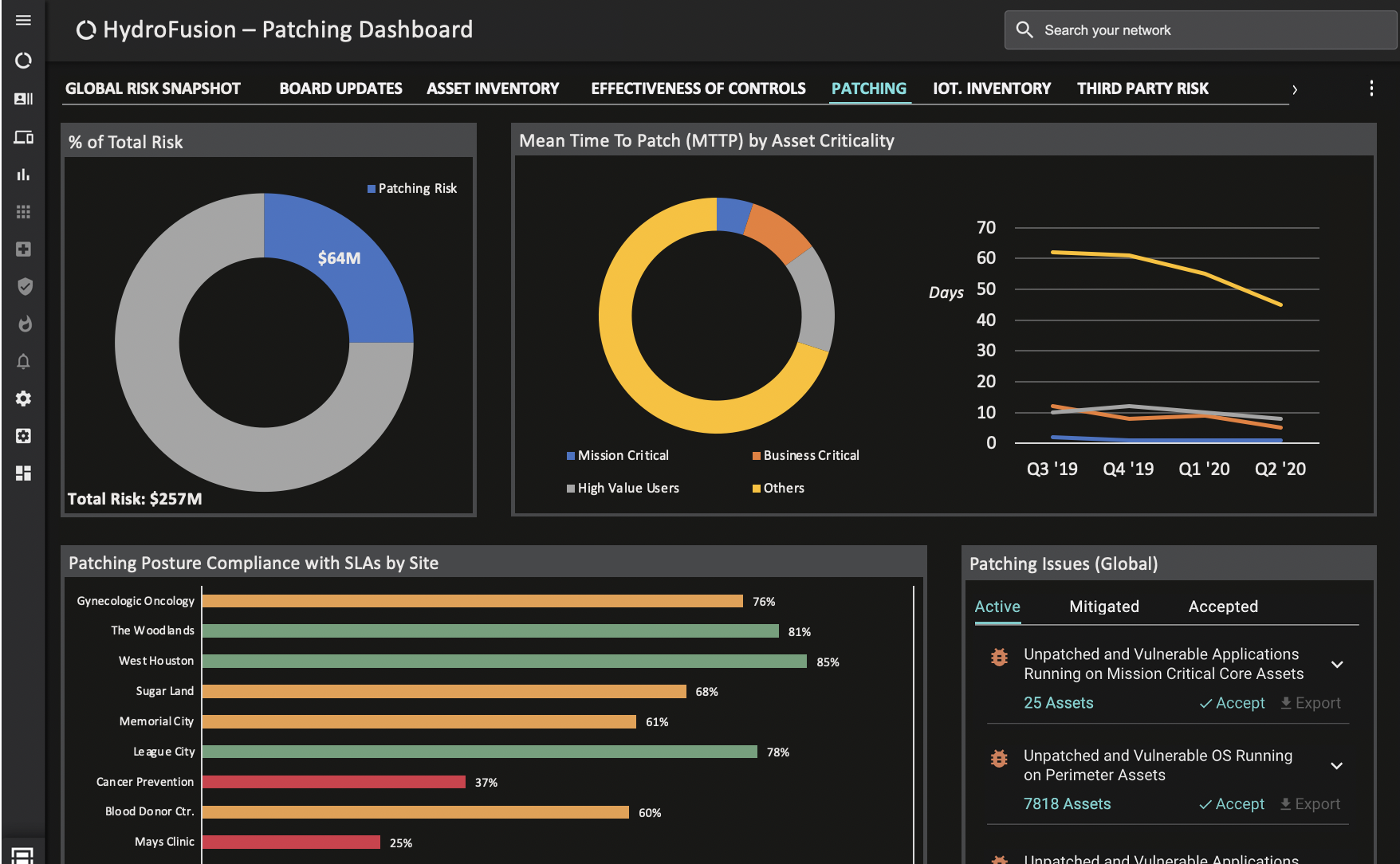
The Enforcer
This is the team member who is the policy and compliance expert. The person who is skeptical about who needs access to what and what rules can be relaxed. The Enforcer is also the person who says “no” to the employees (or admins) that have risky behavior – the tendency to click on phishing links and reuse passwords across accounts putting themselves at risk for credential stuffing. The enforcer takes the responsibility of ensuring that the organization is following all compliance best practices very seriously. A suitable view of the enterprise for the enforcer persona would be:
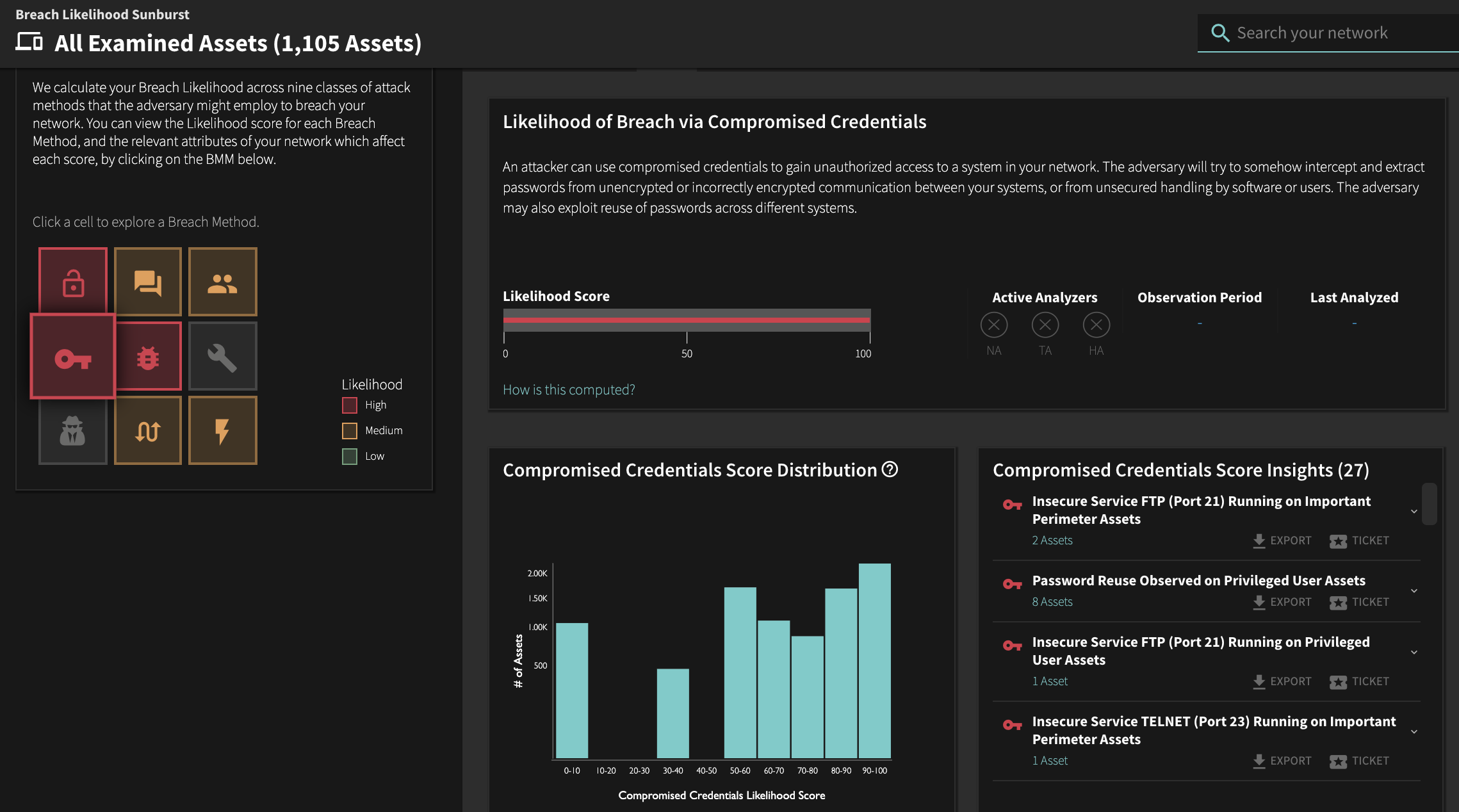
The Builder
As the name suggests, a builder (or software developer) brings key abilities to the team and having someone with secure software development skills on your team is a huge advantage. For example, you need coding skills to enable API based integrations of the various security products you have deployed. Also, security challenges are frequently solved by integrating third-party components and SDKs, so this is one area where developer skills can come in handy.
The Number Cruncher
The CFO or the Number Cruncher as a part of the security team may come as a surprise to you. But security really is everyone’s responsibility and building relationships across the enterprise has never been more pertinent. Cybersecurity is a critical financial risk to an organization and the cost of cybersecurity is not only related to purchasing tools and hiring resources to avert cyberattacks, but also the potential cost of a breach.
Because The Number Cruncher needs to have visibility into the financial aspect of cyber risk that the organization takes on, their Balbix dashboard view might look like this:
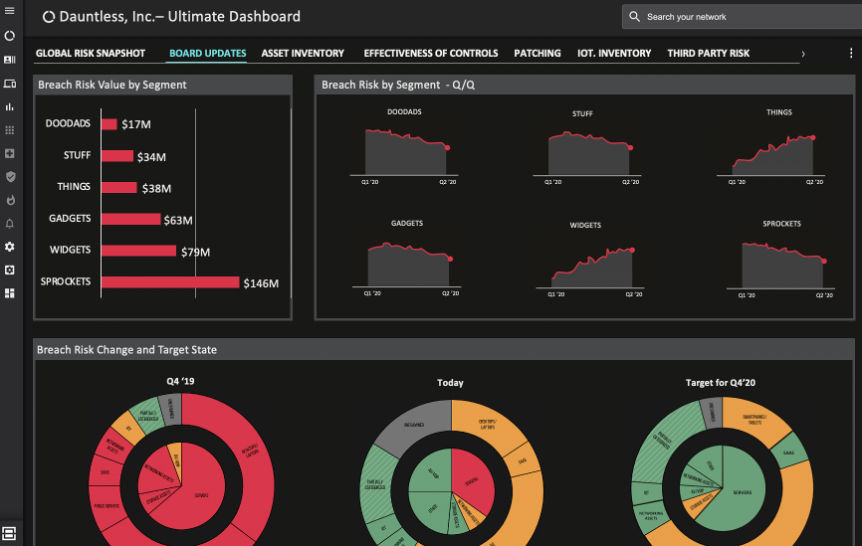
Balbix – An Extension of Your Security Team
The Intelligence
With the number of cybersecurity threats growing every day and increased digitization of assets and processes that could be vulnerable to those threats, it is mathematically impossible for humans to monitor for threats and sift through hundreds of thousands of vulnerabilities to determine which to prioritize and how to address your cyber-risk. You need AI for that.
The Balbix platform is powered by AI, a smart system of automated breach risk assessment, which discovers and continuously analyzes your complete attack surface with little or no human effort, learns the context of your business, identifies and categorizes your assets, and monitors them for security vulnerabilities in real-time. Balbix then prescribes the necessary tactical and strategic mitigations to minimize risk.
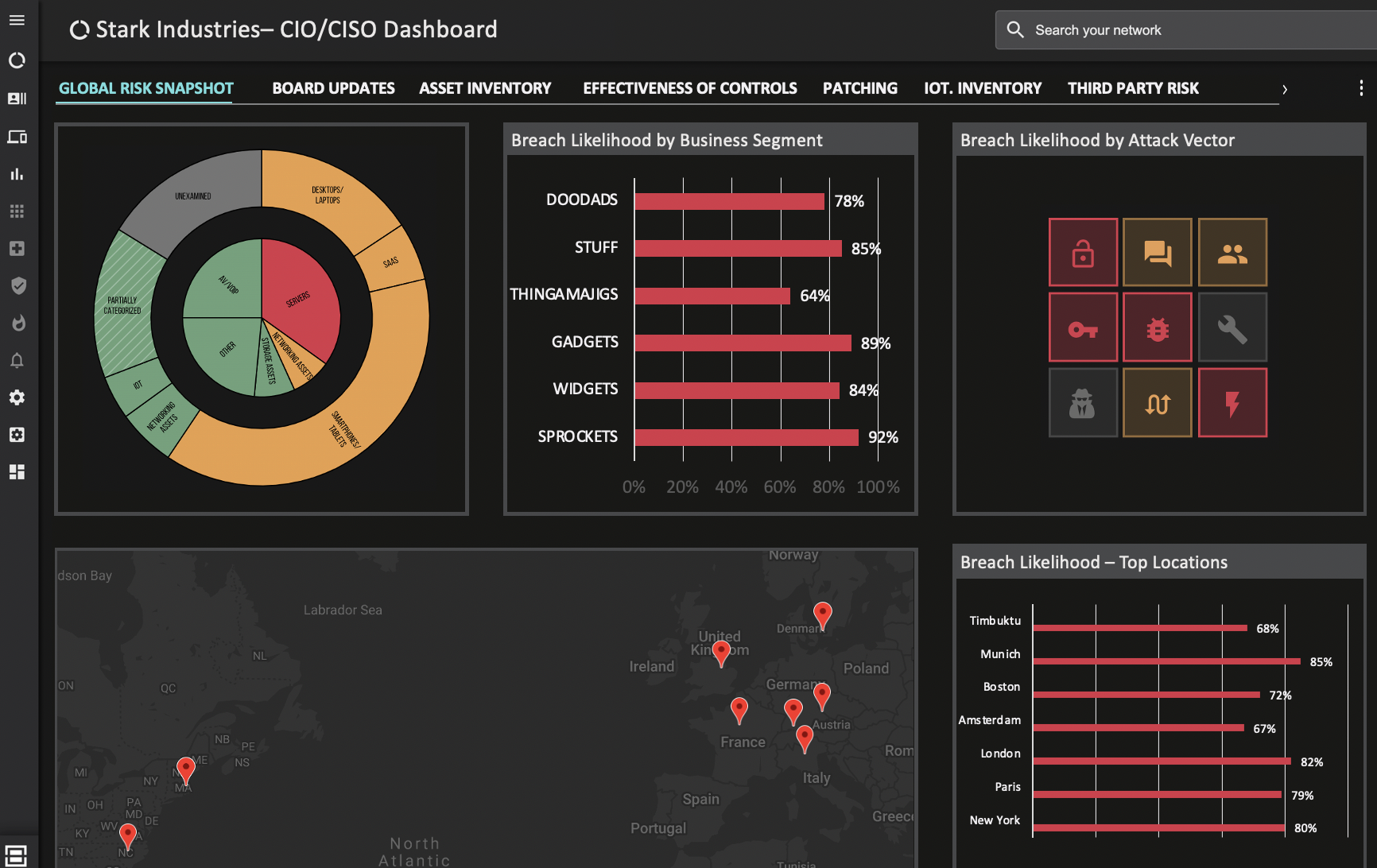
The Balbix dashboard most used by CISOs and CIOs to get a high-level view of where risk lies in their organization looks like this:
Let us show you how Balbix can be an extension of your security team and enable other members to do their jobs even more effectively and efficiently.
