On August 5, 2018, a malware sample, now known as Glueball (CVE-2020-1464), targeting Microsoft Windows was uploaded to VirusTotal. Upon investigating the issue, the sample was forwarded to Microsoft for further investigation. In January, 2019, VirusTotal published a blog post about the issue, wrapping up by stating that, “Microsoft has decided that it will not be fixing this issue in the current versions of Windows.” 734 days later, after extensive confirmation that the issue was being exploited in the wild, Microsoft finally issued a patch as part of its August, 2020 Patch Tuesday release.
The facts on CVE-2020-1464
- Patch released 734 days after Microsoft was notified
- The vulnerability was known to be exploited in the wild
- Exploitation allows for installation of arbitrary malicious code
- Impacts all major versions of Microsoft Windows
This amounts to some sort of breakdown in the patching process for Microsoft.
What is Glueball, how dangerous is it, and why did it take so long for a patch to be released?
About CVE-2020-1464 (Glueball)
This CVE exploits a vulnerability in Microsoft’s Authenticode Digital Signing of software packages. Authenticode is a code signing technology meant to identify software publishers, while also prohibiting tampering of the software packages. Authenticode technology operates in a fashion very similar to digital certificates – “the software publisher signs the driver or driver package, tagging it with a digital certificate that verifies the identity of the publisher and also provides the recipient of the code with the ability to verify the integrity of the code.” Authenticode is used widely as a security mechanism, primarily by preventing altered or improperly signed software packages from being installed.
The flaw in relates to the fact that Microsoft allows content to be appended to the end of Windows MSI package without invalidating the Authenticode signature. Attackers have leveraged this behavior to append their own malicious code, such as JAR files that can be executed directly. Since many operating systems and security products rely on the signature to decide whether or not to trust a file, the malicious code inserted by the adversary will be trusted since it’s part of the signed package.
According to VirusTotal, “in short, an attacker can append a malicious JAR to a MSI file signed by a trusted software developer (like Microsoft Corporation, Google Inc. or any other well-known developer), and the resulting file can be renamed with the .jar extension and will have a valid signature according Microsoft Windows.”
Interestingly,
The Dangers of CVSS-based Prioritization
The issue as described above, combined with the fact that the vulnerability is being exploited in the wild, might lead one to believe that Glueball would have a high CVSS score. In fact, the CVSSv3 Base Score for Glueball is 5.3, or medium severity. This means that many vulnerability management programs that prioritize based on severity might miss this vulnerability in favor of those rated “High” or “Critical.” This is a great example of how CVSS scores can be misleading.
Risk-based vulnerability management can ensure that priority issues like this CVE are prioritized based on risk to the organization, rather than based on severity scores which might or might not have any bearing on the risk that the CVE poses to the enterprise.
Operating Systems Vulnerable to CVE-2020-1464
Basically, every modern version of Microsoft Windows and Microsoft Windows Server:
- Windows 7
- Windows 8.1
- Windows 10
- Windows Server 2008
- Windows Server 2012
- Windows Server 2016
- Windows Server 2019
A full listing of impacted operating system versions can be found here.
Balbix Customers: Identifying CVE-2020-1464
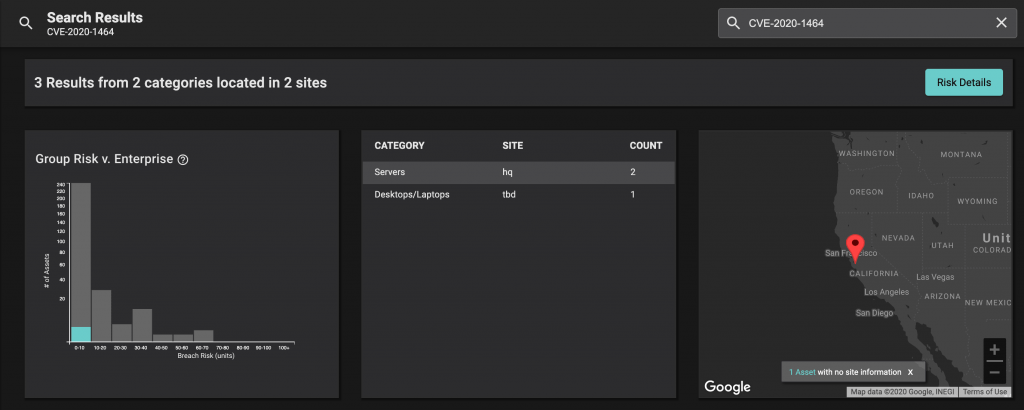
Balbix customers can quickly and easily identify all systems vulnerable to Glueball using the platform’s natural language search capability. Simply type “CVE-2020-1464” in the search and all vulnerable machines will be identified:
Non-Balbix Customers: Identifying CVE-2020-1464
Request a demo today to learn how you can quickly identify CVEs like Glueball, as well as dramatically improve the efficiency and effectiveness of your Infosec team.


