

December 1, 2021
There is an expression: fiddle while Rome burns. It refers to the legend that Emperor Nero played his fiddle while watching the inferno that turned much of Rome to ashes in AD 64. The expression is used to describe the behavior of occupying oneself with unimportant matters and neglecting important ones during a crisis. Unfortunately, many security teams, vulnerability managers in particular, wittingly or unwittingly succumb to this behavior.
The Common Vulnerability Scoring System (a.k.a. CVSS scores) provides a numerical (0-10) representation of the severity of an information security vulnerability. Some argue that CVSS scores can provide a great starting point for evaluating how bad a particular vulnerability is as CVSS provides a metric that’s reasonably accurate and easy to understand. Instead, I’d argue that used in isolation, CVSS scores can be misleading and potentially increase an organization’s risk profile.
I’m not alone. Over the years, many have argued that CVSS scores are simply “not enough” to evaluate today’s threats properly. The solution has been to augment scoring by simply adding threat intelligence as a second factor in assessing risk. However, I believe this still provides vulnerability managers a false sense of security. This limited approach doesn’t take into account context about the affected asset and may therefore focus the security team on prioritizing the wrong vulnerabilities. Even worse, this approach could increase their organizational risk over time as more serious threats go unaddressed, and their digital ‘city’ burns.
So, how do vulnerability managers know which of your vulnerabilities are critical versus those that can wait? A good framework for thinking about this is to look at the overall risk of a breach to the organization. Risk is defined as the probability of a loss event occurring in a given unit of time (likelihood) multiplied by the expected magnitude of loss resulting from that loss event (impact). Cyber risk is the expected loss resulting from a cyberattack or data breach. (read my earlier blog on cyber risk quantification for more detail)

Calculating the risk for a specific CVE on an asset involves knowing five factors. Two factors affect the impact of a breach: the severity of the vulnerability and the business criticality of the underlying asset. The other three factors affect the likelihood of a breach: the real-time threat of the vulnerability being exploited, the exposure of the asset to the threat and whether mitigating security controls are in place to protect the asset.
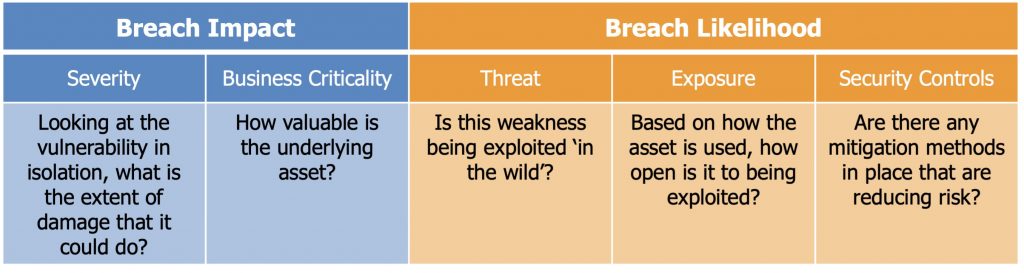
Severity provides a ranking of some of the qualities inherent to a vulnerability. These qualities do not change over time. Nor are they dependent on the environment the vulnerability appears in. As a result, some folks characterize severity as the hypothetical risk of a vulnerability.
The most common measure of severity is CVSS scores. As I mentioned earlier, CVSS scores provide a numerical (0-10) representation of the severity of an information security vulnerability. This infographic provides a good overview of CVSS scores. In short, the CVSS score for a vulnerability comes from “base factors” including exploitability, scope and impact, for which there are additional sub-components. CVSS is now on its third major version (v3.1), which was designed to address some of the shortcomings in its predecessor, v2. Most notably, v3 looks at the privileges required to exploit a vulnerability, as well as the ability for an attacker to propagate across systems (“scope”) after exploiting a vulnerability.
These base factors do not change over time, and are not dependent on real world exploitability or on compensating factors that an enterprise has put into place to prohibit an exploit. In other words, CVSS answers the question, “Is this dangerous?”, but not, “Is this dangerous to my organization?”
Vulnerability managers will often act to patch vulnerabilities with CVSS scores reaching nine or ten, the highest ranks, but only a small subset of vulnerabilities of any severity are associated with known and publicly documented attacks. Since security teams are invariably understaffed, there is always an opportunity cost to any action. In this case, some vulnerabilities being actively exploited in the wild may not be resolved as a priority.
In short, only looking at severity presents vulnerability managers with inadequate data to make decisions about how to best address the overwhelming volume of identified vulnerabilities, and it doesn’t tell them which ones pose the greatest risk to their enterprise.
CVSS does refer to temporal and environmental metrics, and this is an acknowledgement that there are more factors to consider. For organizations using only CVSS scores, it means those other aspects need to be specified and then manually scored. For example, to understand whether there is an active threat, vulnerability managers must have information about the current real-world exploitability of the vulnerability.
Let’s say you have two vulnerabilities: vulnerability A has a moderate CVSS score, but does have malware associated with it and is being reported on social media as being actively exploited. Vulnerability B has a CVSS of 10, the highest score, but has no known attacker tools and is not being actively exploited. Do you rely on CVSS alone? You probably don’t want to waste resources worrying about theoretical issues when you have open security issues that present immediate danger. This is where adding threat intelligence comes in.
Legacy risk-based vulnerability management (RBVM) tools and independent threat intelligence providers can provide much more detailed information about how vulnerabilities are actually being exploited “in the wild.” A number of security vendors helpfully provide this information in the form of scores and statistics. Some inputs may include ranking vulnerabilities based on criminal adoption, patterns in exploit sharing, and numbers of links to malware. These vendors also provide context and a deeper understanding of how and why threat actors are targeting certain vulnerabilities and ignoring others.
Legacy RBVM vendors combine severity with threat intelligence to produce scores that are often drastically different from the base score provided by CVSS base score alone. This is helpful in that threat metrics are a consideration for how likely a breach is to occur, while severity scores simply measure impact. However, these solutions still miss the underlying business context of the vulnerable asset. At best, completing the model using a legacy RBVM tool entails a lot of manual effort, at worst, ignoring the underlying asset steers prioritization in the wrong direction and may lead to an increased breach risk.
There is a way to automatically include context about the underlying assets. As the table below illustrates, Balbix provides a risk prioritization model that automatically incorporates all five factors for determining risk. Balbix is able to analyze a broader range of risk factors because we have knowledge of not only the vulnerabilities but also the underlying assets.
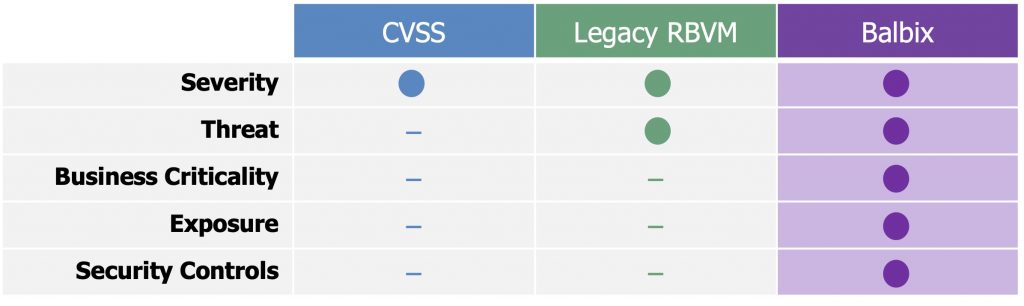
The Balbix risk model is able to incorporate additional context because Balbix also provides a continuously updated asset inventory that includes over 400 attributes for each asset. In doing so, Balbix is able to look at risk at different levels of granularity across the organization. Severity and threat level are analyzed by CVE. Business criticality and security controls are analyzed asset-by-asset. Exposure, especially to issues like network placement and risky users, is assessed for groups of assets with common traits.
Balbix uses CVSS scores to measure severity. This allows Balbix to display severity ratings directly to users but also provides severity as an input to the broader risk prioritization model.
Threat intelligence for each CVE is also provided to users, but users have two options. For users who have invested in a legacy RBVM tool, Balbix can ingest data from that tool into its risk prioritization model. For other users, Balbix provides threat scores directly.
To properly estimate the adverse effect to the organization if an asset were to be breached, risk prioritization should take into account both inherent properties and contextual properties of the asset. This can only be done by having access to information about the asset itself, not the vulnerability.
Balbix tracks inherent attributes like asset category (laptop, server, storage, etc.), business unit and geography. Balbix also tracks a number of contextual properties such as the asset type (mission critical, privileged, etc.), the risk inherent in the role of the asset (including a risk to intellectual property, a risk to customer data, or a risk of operational disruption, for example), user privileges and an asset’s interaction with other assets.
Vulnerability managers can then search for, analyze, prioritize and remediate vulnerable assets that have these attributes, for example they can search for “intellectual property”. Users may choose to focus on reducing risk for a specific attribute during a month or quarter, and show real progress.
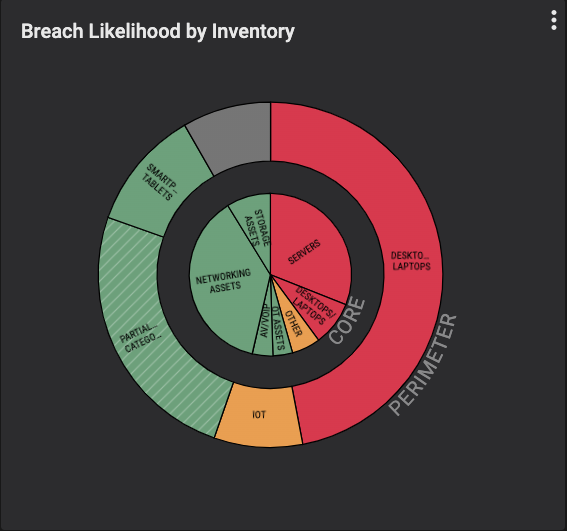
Exposure also requires knowledge about how an asset is being used, as exposure is tied to the asset not the vulnerability. Balbix calculates exposure due to asset usage by analyzing multiple properties such as duration for which the asset has been present on the network, availability and frequency of use, as well as type of use. Another source of exposure is the asset’s placement no the network, as seen in the image below.
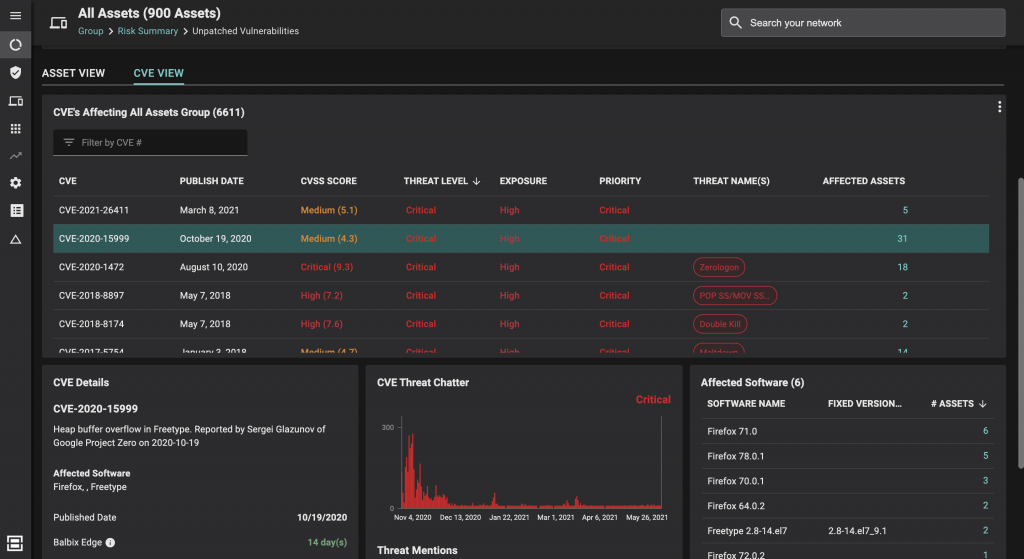
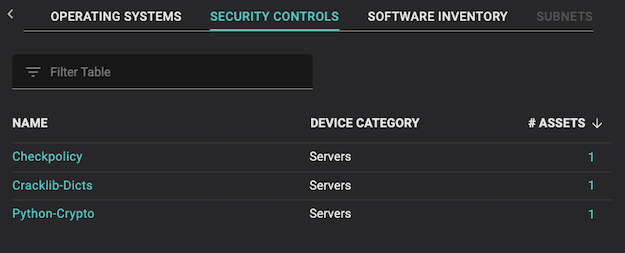
Balbix provides vulnerability managers with the ability to monitor and manage risk using both a CVE-centric view (see immediately below) and an asset-centric view (see Security Controls, below).
The final risk factor that Balbix tracks is whether mitigating controls like investments into firewalls, anti-phishing systems, and endpoint detection and response solutions are in place.
Ultimately, vulnerability management is about reducing risk. By automatically incorporating five factors in their vulnerability management practice (severity, threat, business criticality, exposure, and security controls), vulnerability managers can not only prioritize individual CVEs, but can also get a clear understanding of the likelihood and impact of an asset being breached. Having the bigger picture ensures that vulnerability managers and other stakeholders aren’t overlooking a blazing fire.
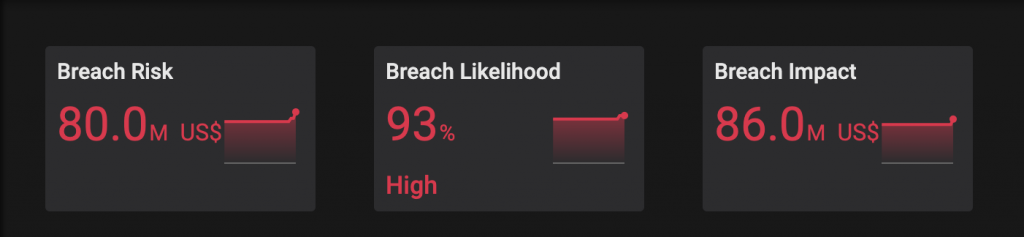
As shown in the image below, Balbix provides security team members at any level of the organization with an assessment of the organization’s breach risk. Vulnerability managers can use these measurements to tie their vulnerability prioritization and remediation efforts to quantifiable reductions in risk to specific assets and to their organization’s overall cybersecurity posture.
No one wants to be caught fiddling while their digital ‘city’ is on fire!