

November 23, 2021
The queen stands on her castle wall, keen to defend her people and valuables against the gathering hordes. She wonders, has she left herself vulnerable? She assesses her defenses. First, there is the castle itself: it has a wide moat, a strong gate, and high walls. She knows that the better her defences, the less likely the enemy is to get in. But she also knows the enemy is crafty. Her second layer of defence is to monitor inside the walls looking for spies and enemy forces that may have slipped by (hint: view large wooden horses with suspicion).
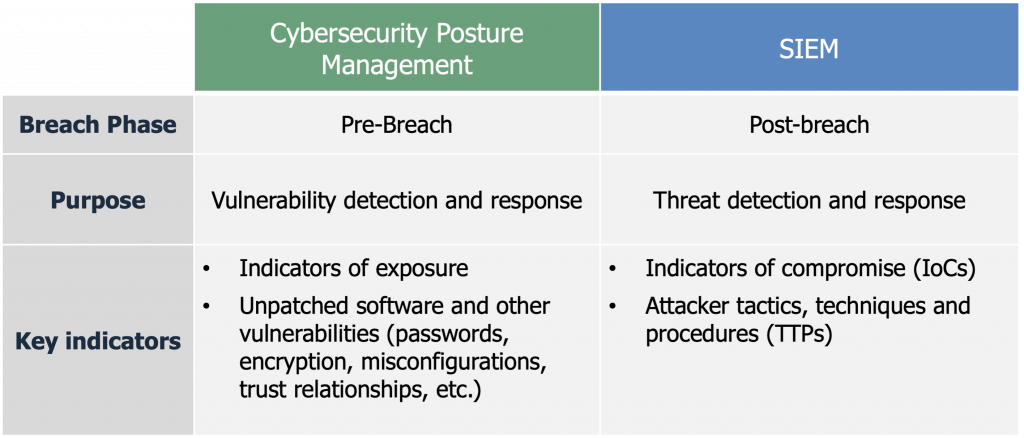
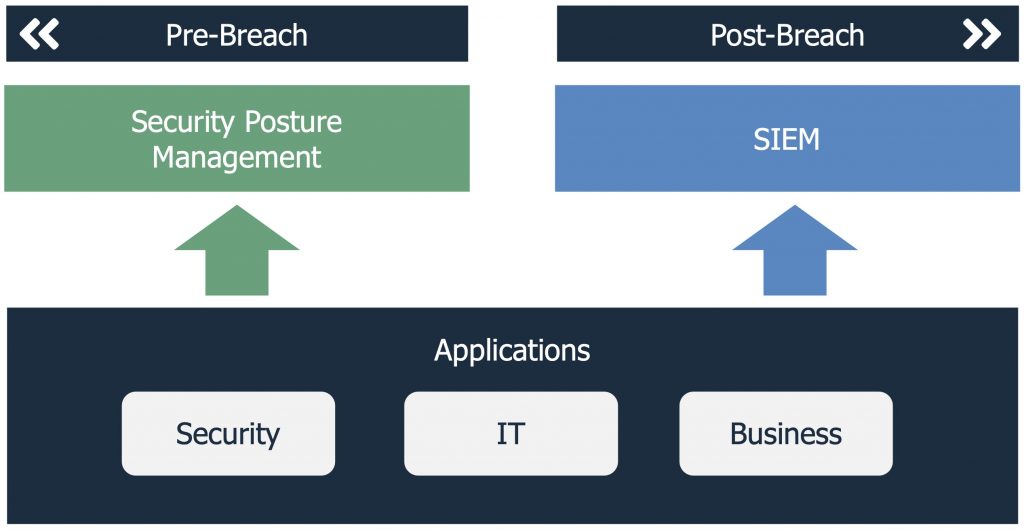
As it was in medieval times for our queen, it is now for digital enterprises. Albeit with a few changes. Our queen has been replaced by the chief information security officer (CISO). Monitoring of the castle defences has been replaced by cybersecurity posture management, and monitoring inside the walls has been replaced by security incident and event management (SIEM). The former for monitoring and managing exposures to prevent a breach, and the latter for monitoring and managing attacks in the event of a breach. Both though, ultimately to reduce risk due to cyber attacks.
Gartner noted in a 2005 report under the broad umbrella of vulnerability management that: “the monitoring step of the vulnerability management process can be automated by regular execution of deployed VA [Vulnerability Assessment] and security configuration management technologies and through the use of SIEM technology.”¹
It was the SIEM market that matured first, with Gartner coining the term in this same 2005 report. Gartner now defines the SIEM market as, “analyzing event data in real time for early detection of targeted attacks and data breaches, and to collect, store, investigate and report on log data for incident response, forensics and regulatory compliance.” According to Gartner, the SIEM market grew to $3.58 billion in 2020², the third largest market in cybersecurity.
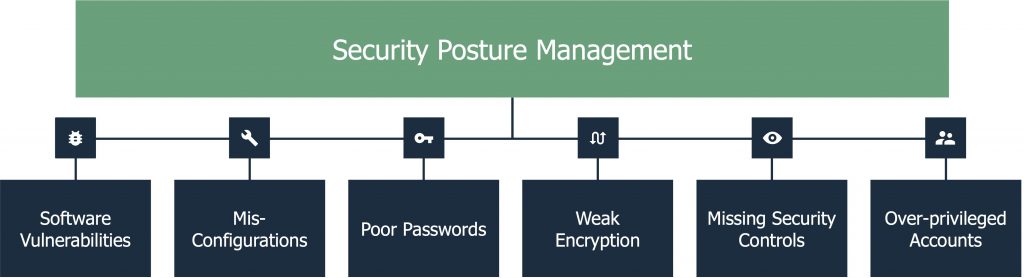
Cybersecurity posture management, on the other hand, helps organizations reduce their attack surface to decrease the likelihood and impact of a breach. To do so, vulnerability assessment, security configuration management, and the monitoring of a host of other potential breach methods including poor passwords, weak encryption, and over-privileged admins has recently combined under the auspices of security posture management, facilitated by the evolution of technology.
In fact, it is not a coincidence that both SIEM and cybersecurity posture management went through huge changes starting 5-7 years ago. Both solutions were able to take advantage of technology advances including data analytics, specifically machine learning; cloud infrastructure; API-based integrations; and big data technology that usurped the scale and processing power of traditional software. For SIEM, these changes led to the emergence of new user and entity based analytics (UEBA)-based SIEM vendors, like Exabeam and Securonix, and the addition of analytics-based offerings from larger players like IBM and Microsoft. For cybersecurity posture management, these technology advances have allowed the management of the disparate breach methods discussed above to be combined into a unified risk model by a vendor like Balbix.
Both solutions ingest data from a similar range of IT, security and business applications. In doing so, they significantly reduce the burden of managing separate tools. They also intelligently aggregate data about a customer’s environment and unveil meaningful insights from previously siloed systems across their security stack – all without the need to replace existing tools.
Previously, security teams monitored and managed each security application in isolation. This became increasingly difficult as they added security tools to adapt to the breadth and dynamic nature of attacks, and due to constant changes in their underlying technology stack. The fragmentation allowed security analysts to look at unique breach methods, but failed to bring together a bigger and higher fidelity picture.
Now, a modern SIEM and a cybersecurity posture management tool like Balbix allow organizations to integrate their tools, a non-trivial effort, as anyone who has attempted to do this manually can attest. See for example our recent post on the challenge of managing cybersecurity data lakes.
Collecting and correlating multiple data sources has allowed for real-time analysis and faster detection. On top of that, users of both solutions benefit from the inclusion of automation and artificial intelligence to ingest and understand vast amounts of data, and then normalize the data and make it available for analysis through a single console. As such, both modern SIEMs and Balbix eliminate the need to weed through an endless stream of events, alerts or notifications located across many separate tools.
The advanced analytics and modeling provides fidelity and detection quality, while the inclusion of additional IT and security telemetry provides additional contextualized insights. SIEMs can thus be used to detect advanced persistent threats (ATPs) and insider threats. Balbix can be used to detect and protect against potential breaches by proactively identifying and eliminating common vulnerabilities and exposures (CVEs) and non-obvious vulnerabilities like re-used passwords or over-privileged administrators.
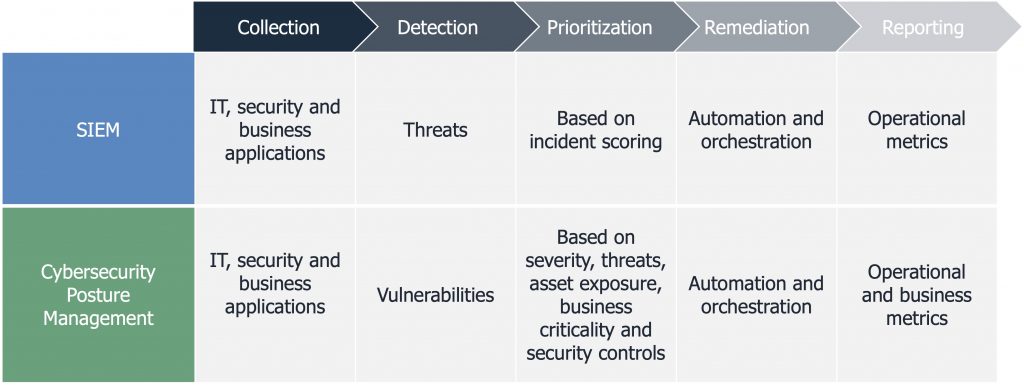
The addition of advanced analytics to these solutions since the mid-2010s, has allowed for automated prioritization. SIEMs provide prioritization using incident scoring, while a cybersecurity posture management solution like Balbix provides prioritization of vulnerabilities based on 5 factors: severity, threats, asset exposure, business criticality and security controls. Prioritization of risk allows analysts to focus on threats and vulnerabilities that matter. Even better, prioritization for both types of solutions is accompanied by context to make human analysis faster and more accurate.
Automation is pervasive across the entire lifecycle, and throughout the workflow of both solutions – from collection to detection, and from prioritization to remediation. The automated workflows lead to faster response and recovery times when critical issues are detected: whether they be an attacker in the midst (in the case of a SIEM), or an actively exploited vulnerability requiring an immediate fix (in the case of cybersecurity posture management). Automation also makes it easier for under-resourced security analysts and SOC teams to manage the large volume of issues on their plate.
Finally, both modern SIEMs and Balbix provide reporting. And while it is outside of the detection and response workflow, reporting is a key management tool. In this regard, both solutions provide reporting on key operational metrics. Notably, managers will be able to review mean time to respond (MTTR) in a SIEM and mean time to patch (MTTP) in a security management tool.
This is also an area where the tools diverge, as a cybersecurity posture management solution like Balbix also provides key business metrics. Specifically, security leaders are able to quantify and manage their cyber risk in monetary terms, allowing them to speak to their CFO, CEO and board of directors in a language that they readily understand: dollars and cents.
If you have unified your post-breach threat detection and response workflow using a SIEM, ask yourself, why haven’t you done the same for your pre-breach exposure to unpatched software and other vulnerabilities? View this 5-minute demo video to see how Balbix can help you reduce the likelihood and impact of a breach.
¹Gartner, Improve IT Security with Vulnerability Management, Amrit T. Williams, Mark Nicolett, May 2, 2005.
²Gartner, Magic Quadrant for Security Incident and Event Management, Kelly Kavanaugh, Toby Bussa, John Collins, 29 June 2021.