

September 13, 2021
If you’re a sports fan, you know that home-field advantage is the tendency of athletes to win more often when competing at their home facility. And this is not just a belief, but is supported by a number of research studies.
In cybersecurity, the infosec teams should have the home field advantage against the (unwelcome) visitors – the cyber criminals. After all, the cyber criminals are coming into your turf, trying to find that one chink in your defenses. You should know your landscape better than them. You should know where your critical assets are, you should know what protections you have in place, and you should know where you are vulnerable…but do you?
More and more, infosec teams are beginning to realize that while they should have the home turf advantage theoretically, there are instances where blindness on several fronts, and a lack of agility are letting them down.
First, there is a lack of an accurate and comprehensive asset inventory. The number and types of assets in an enterprise is dynamic and the inventory changes constantly, especially in the cloud. Keeping track of your inventory using manual methods or point-in-time snapshots leads to gaps in your visibility. This allows attackers to take advantage of your blind-spots and makes compliance and cyber-risk management very difficult.
Inadequate coverage of various types of security risks and vulnerabilities is another challenge. Most monitoring tools only cover one type of exposure – typically unpatched software or cloud misconfigurations – but leave you blind to additional unseen risks like weak and reused passwords, encryption issues, and expired certificates that can be easily exploited by attackers and put you on your heels.
Then there is the challenge of alerts popping up faster than you can fix them. This deluge of alerts coupled with a lack of accurate and customized prioritization can lead to your team constantly chasing low impact items, while neglecting truly critical, high impact vulnerabilities.
So, what are 3 quick actions that you can take right now to recapture your home field advantage?
This may seem like a tall order, but the first step towards gaining home field advantage is to have visibility across the entire field of play. All your IT and cybersecurity tools – like CMDB, firewalls, vulnerability tools, EDR, SIEM, MDM systems, Active Directory, IoT/OT management systems, cloud infrastructure APIs etc. – generate data. This data typically ends up in silos. One option is to consolidate this data in a data lake. Yet, it can be problematic to find what you are looking for in a data lake.
Instead, Balbix provides our customers with a single, comprehensive and organized view of their asset inventory. In addition, Balbix continuously discovers and monitors your devices, apps, and users across 100+ attack vectors by analyzing the data from your cybersecurity tools (and optionally via our sensors).
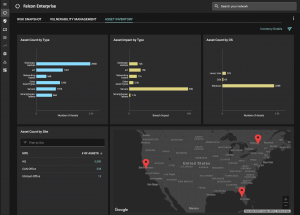
A sure way to improve your advantage is to lessen your opponent’s ability to strike. In cybersecurity, that means reducing your attack surface by defending where you are most exposed. It’s not uncommon for a large enterprise to have thousands or even tens of thousands of vulnerabilities at any time. Figuring out which vulnerabilities to prioritize is a daunting task.
Balbix allows you to use your cybersecurity data and tilt the field in your favor. The Balbix platform uses specialized AI to predict likely breach scenarios, prioritize vulnerabilities to fix, and prescribe necessary risk mitigation actions.
The risk of a breach to an organization is a function of the likelihood of an asset being breached and the business impact of that breach. For Balbix customers, likelihood of an asset being breached is calculated as a weighted sum of the likelihood of a breach from individual attack vectors by considering vulnerability severity, exposure, threat level, and security controls.
Breach impact is first estimated using automation, and then refined with input from the CISO and various risk owners. Balbix denominates risk metrics in monetary terms which enables everyone involved to have a common language and make better decisions faster.
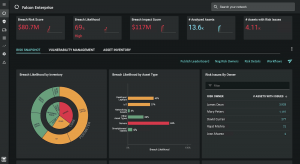
In most organizations, folks outside the security team don’t really understand cybersecurity issues, and often don’t take them seriously. Attackers exploit this lack of teamwork. The way to get around it is to enable all stakeholders to own their cyber risk by assigning risk to owners. Risk owners can then act to mitigate risk.
Balbix also provides risk dashboards and reports to enable you to gamify cyber risk reduction and demonstrate the value of your security program to senior leadership and the board. And to enable all stakeholders to participate in cyber risk reduction and improvement of the security posture, Balbix provides out-of-the-box and customizable breach risk reporting built around your organizational structure and processes.
Home-field advantage is real. Balbix has allowed many global 1000 companies to take back the home-field advantage. We can help. Get in touch to see a 15 min demo.