

February 1, 2022
The World Economic Forum, in collaboration with Accenture, recently published their 2022 Global Cybersecurity Outlook. It is based on a survey of 120 security and business leaders. The news for security leaders isn’t good. According to Jeremy Jurgens, managing director, World Economic Forum: “despite the growing cognizance of cyber risks, decision-makers and cyber experts are often not on the same page in terms of prioritizing cybersecurity, integrating cyber risk into business strategy and integrating cyber leaders into business processes.” While these issues are not new, what is surprising is, according to the report, the gap between cyber leaders and business leaders is widening.
The report identifies three critical gaps between security-focused executives (CISOs, CIOs, etc.) and business executives (CEOs, Board of Directors, etc.):
Fortunately, there are some known actions security leaders can take to bridge these gaps:.
Let’s look at what underlies each of these three gaps and the ways CISOs can get on the same page as organizations’ leadership in a bit more detail:
The key challenge is that business leaders and security leaders have different perceptions of the status quo. CEOs and CISOs see the prioritization of cyber in business decisions very differently: “while 92% of business executives surveyed agree that cyber resilience is integrated into enterprise risk-management strategies, only 55% of security-focused leaders surveyed agree with this statement.” CISOs don’t see cyber risk being given due consideration.
A common reason for the disconnect is the lack of a common language for discussing cyber. Security leaders almost always have operational metrics to measure their team’s performance such as mean time to patch (MTTP) and service level agreements (SLAs) with stakeholders. When reporting to leadership they often repurpose these metrics. Unfortunately, for their CFO, CEO and the board of directors, these metrics don’t resonate. When a CEO doesn’t have a way of judging the impact on the business when told that 100 patches were completed that week.
The report recommends that CISOs “translate cyber risk into business impact.” The way to do that is to use the common language of money. CISOs should discuss cyber risk in monetary terms with their leadership. A CEO will understand the implication of reducing $5 million in risk.
The journey to cyber risk quantification starts with security teams developing a deep understanding of critical business operations. In the coming year, having visibility of the organizations’ assets is of paramount importance. There is alignment amongst the report’s respondents, both security and business leaders, that digital transformation will have the greatest influence on their organizations’ approach to cybersecurity in 2022. One reason is the resulting proliferation of assets – traditional devices and cloud infrastructure.
With an inventory in place, security teams then need to measure the business impact in monetary terms of each asset should it be breached, including factors such as productivity loss, response costs, replacement costs, competitive advantage loss, fines and judgements and reputation damage.
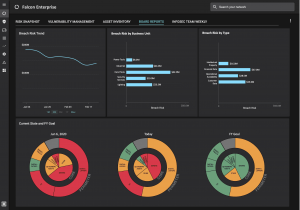
The second challenge outlined in the report is the lack of support for cybersecurity programs. Despite growing cyber threats to organizations’, the report noted that only 68% of survey respondents, “see cyber resilience as a major part of their overall risk management.”
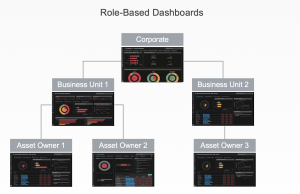
To improve support for cyber programs, the report encourages security leaders to “ensure regular communication between cyber and business operations teams”. One of the most effective ways to do so is to operationalize cybersecurity as part of business leaders’ day-to-day habits. At Balbix we have found that dashboards aligned to their area of responsibility provide business leaders with both visibility and a shared sense of accountability for security risks for those business areas.
In fact, role-based dashboards are effective at all levels of the organization. For example, dashboards can be set up so the windows admin sees Window tasks and the endpoint admin sees endpoint tasks, and so on. One of our customers has set up over 100 custom dashboards for its security team and their business stakeholders.
Recent trends like the “great resignation” are affecting staffing in all parts of the economy. Unfortunately for cyber security teams, these trends are only compounding a longer term skills shortage. So it’s no surprise that the challenges that organizations face to recruit and retain cybersecurity talent was highlighted in the report, where the authors found that: “59% of all respondents would find it challenging to respond to a cybersecurity incident due to the shortage of skills within their team”
In parallel with efforts to improve staffing levels, organizations can look to make the staff they do have more productive. According to the report, respondents expect automation and machine learning to have the greatest influence on transforming cybersecurity in 2022-2023. From my seat at Balbix it’s easy to see why. We provide cybersecurity posture automation, a large portion of which is due to using machine learning to provide our customers with a unified risk model. In so doing, we allow our customers to more efficiently inventory their assets, prioritize and remediate vulnerabilities and measure their cyber risk in monetary terms.
The contrast to other methods of security posture management and cyber risk quantification can be striking. I recently reviewed another vendor’s cyber risk quantification solution. Based on the FAIR model, it requires security analysts to manually input data for each asset in their environment. In contrast, Balbix automatically ingests data from our customers existing IT, security and business tools; and continuously maps over 400 attributes to each asset while simultaneously identifying risk issues for those assets and determining the business impact in monetary terms should they be breached. Security analysts can manually override the automated Balbix but what we have found is that they only need to do so on an exception-level basis. The model is aligned with their own risk estimates. The contrast in how security teams are spending their time using Balbix versus common approaches is magnified when you consider that the largest environments include 100,000s, if not millions, of assets.
Advocating for investment in solutions based on automation and machine learning is just one more way that security leaders can close the gap with their organizations’ business leaders.
Balbix provides an innovative cybersecurity posture automation solution that helps security executives to: