In cybersecurity, there are a million things you can measure. Many infosec professionals have worked under a boss who requires that a certain number of patches be implemented every week. Others have spent months on end training employees in cyber hygiene, focused on the quantity of staff who view their presentation every month.
Legendary business mind Peter Drucker is known for his teaching on how to measure different areas of business and why measuring is so important. His writing on how to identify what you should be measuring, unfortunately, is often glossed over.
For infosec teams, the ultimate goal is to improve the company’s security posture. How then can this be measured? The answer is risk.
Measuring cyber risk can feel all but impossible. New devices and apps are constantly being added to the network. Adversaries are constantly updating attack vectors, or adding new ones. Luckily, AI-powered technologies are now able to continuously analyze the attack surface and automate these calculations. Balbix measures risk with a five-pronged approach and computes risk as a product of breach likelihood and impact using advanced AI algorithms and ML techniques.
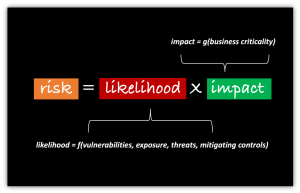
1. Vulnerabilities
How many vulnerabilities does your enterprise have? If you’re like most security leaders, your mind started counting up unpatched software issues that your team is currently working on. Unfortunately, this is just the beginning.
There are actually 9 types of security vulnerabilities. Your risk from weak or shared passwords, phishing, encryption issues, misconfigurations, and other vulnerabilities is a huge indicator of your overall security posture. Measuring this part of your security posture starts with having visibility into all vulnerabilities and the assets that are affected by them.
2. Threats
Do you know which weaknesses you have that are being exploited in the wild? The quantity and importance of assets that can be affected by real and emerging threats is central to your security posture.
If you’re able to observe how these threats are affecting your environment and prioritize them by business criticality then you are in good shape. Not all of the threats to your environment will be actual risk items and you should have visibility into this as well. In this respect, vulnerabilities and threats go hand in hand because threats require vulnerabilities in the target system to become successful attacks.
3. Exposure
Exploitation of a vulnerability is also dependent on an asset’s usage. Do you know what your exposure to particular vulnerabilities is based on how your vulnerable assets are being used? Does your vulnerability scanner account for this?
This factor of security posture is quite multi-dimensional. It takes into account the lifecycle of the asset, its availability, frequency of use, and type of use. Digging deeper, usage data is important and can become challengingly granular. Usage of specific software and applications, user profiles, and different credentials all play a role in every asset’s exposure.
4. Mitigating Controls
Much wasted effort can be exerted towards improving your security posture if you don’t know how your current security measures and impacting your risk items. Tools like firewalls, anti-phishing systems, and endpoint softwares can greatly reduce breach likelihood from certain vulnerabilities and threats. Knowing how these mitigating controls are cancelling out would-be risks is essential to getting an accurate read on your security posture.
5. Impact
The impact that a breach could have on your business is core to your security posture. Even if vulnerabilities and threats abound, exposure is high, and barely any mitigating controls are being used, your security posture may still be good enough. That is, if you’re adequately defending the right assets.
While the breach of a device like the CTO’s laptop will probably have a severe impact on the business, the breach of a receptionist’s smartphone would likely have small consequences.
Knowing the importance or business value of each asset dictates is crucial to understanding your security posture. The most business critical assets in your enterprise are what you should focus on when measuring your security posture.
Automating Cyber Risk Measurements
Implementing a certain number of weekly patches or conducting a certain number of monthly training sessions are not inherently meaningless metrics to be evaluated by. In fact, they are good goals for managers to set if they tie directly into quantifiable risk goals. Balbix automates risk calculations and measurements in real-time, across every asset and type of vulnerability. This allows CISOs to align their teams on cybersecurity objectives and measure their security posture accurately as they spearhead risk reduction initiatives.

